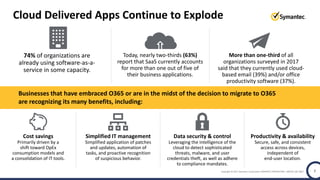
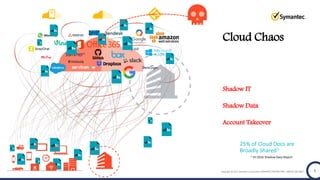
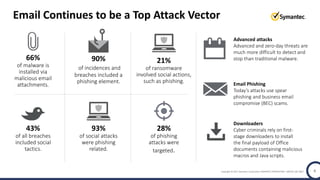
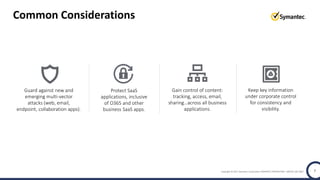
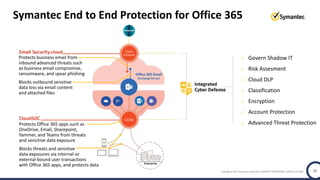
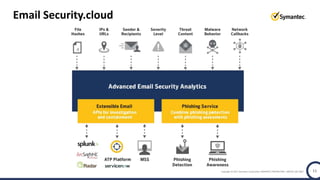
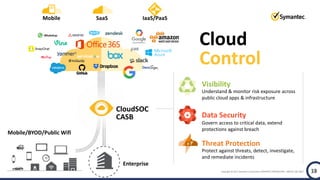
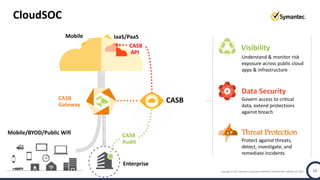
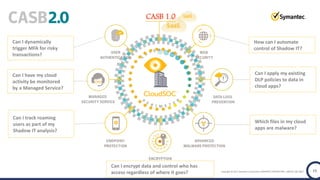
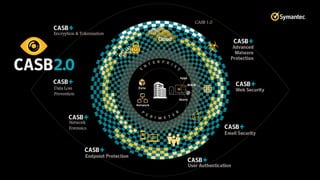
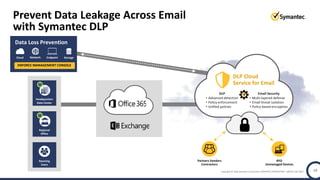
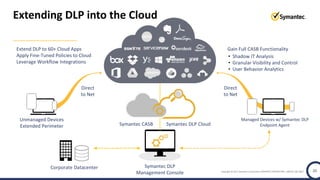
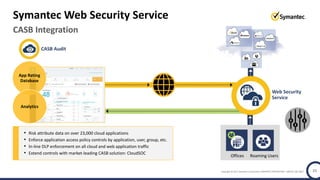
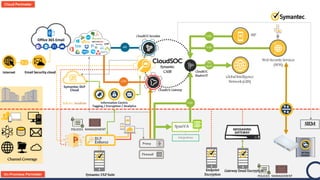
The document discusses the security challenges and considerations surrounding the adoption of Office 365, highlighting the benefits of cloud migration such as cost savings and simplified IT management. It emphasizes the need for robust security measures against evolving threats, particularly in email security, and the importance of implementing third-party tools to enhance protection. Additionally, it outlines strategies for data loss prevention and securing corporate data across various cloud applications.