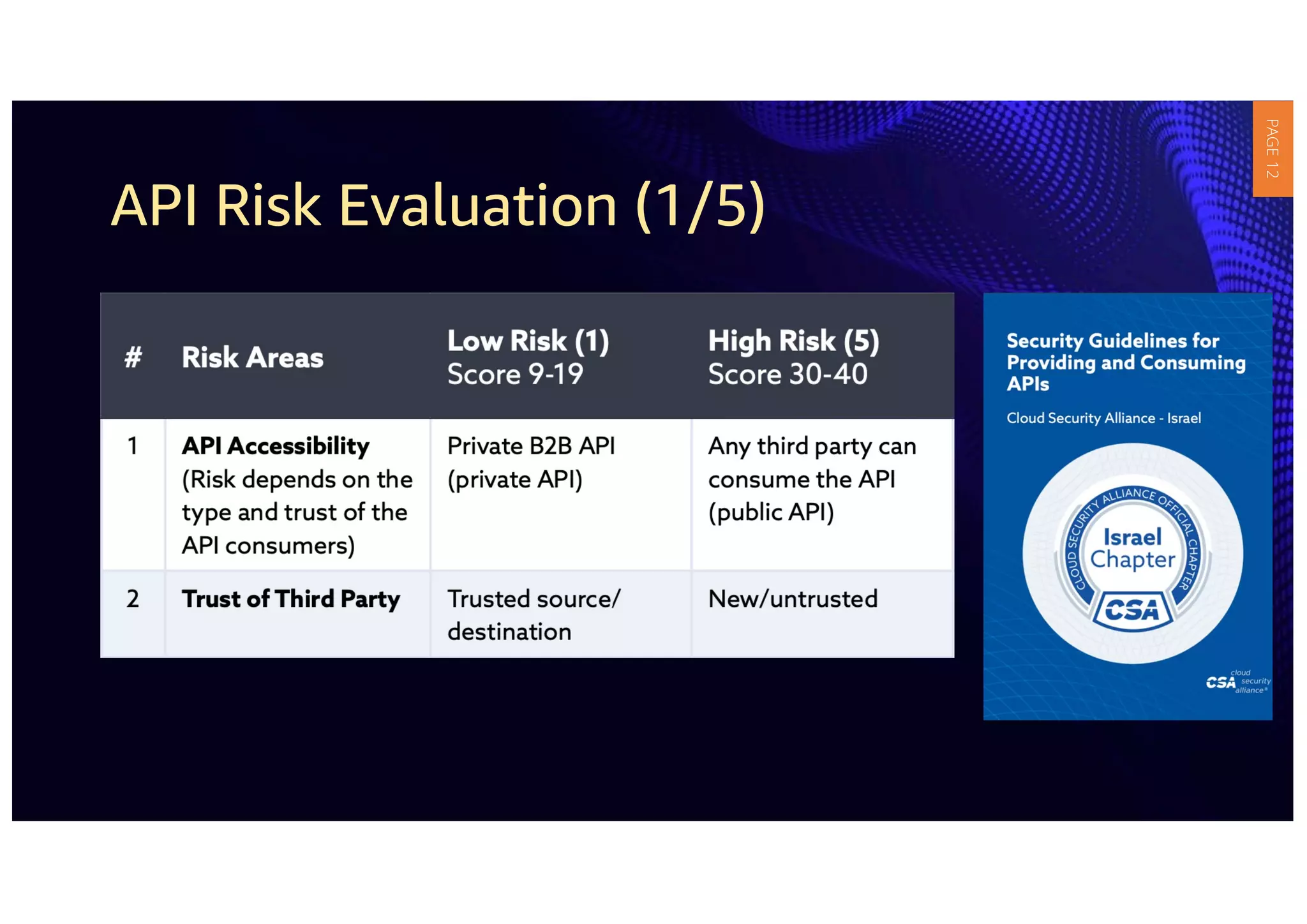
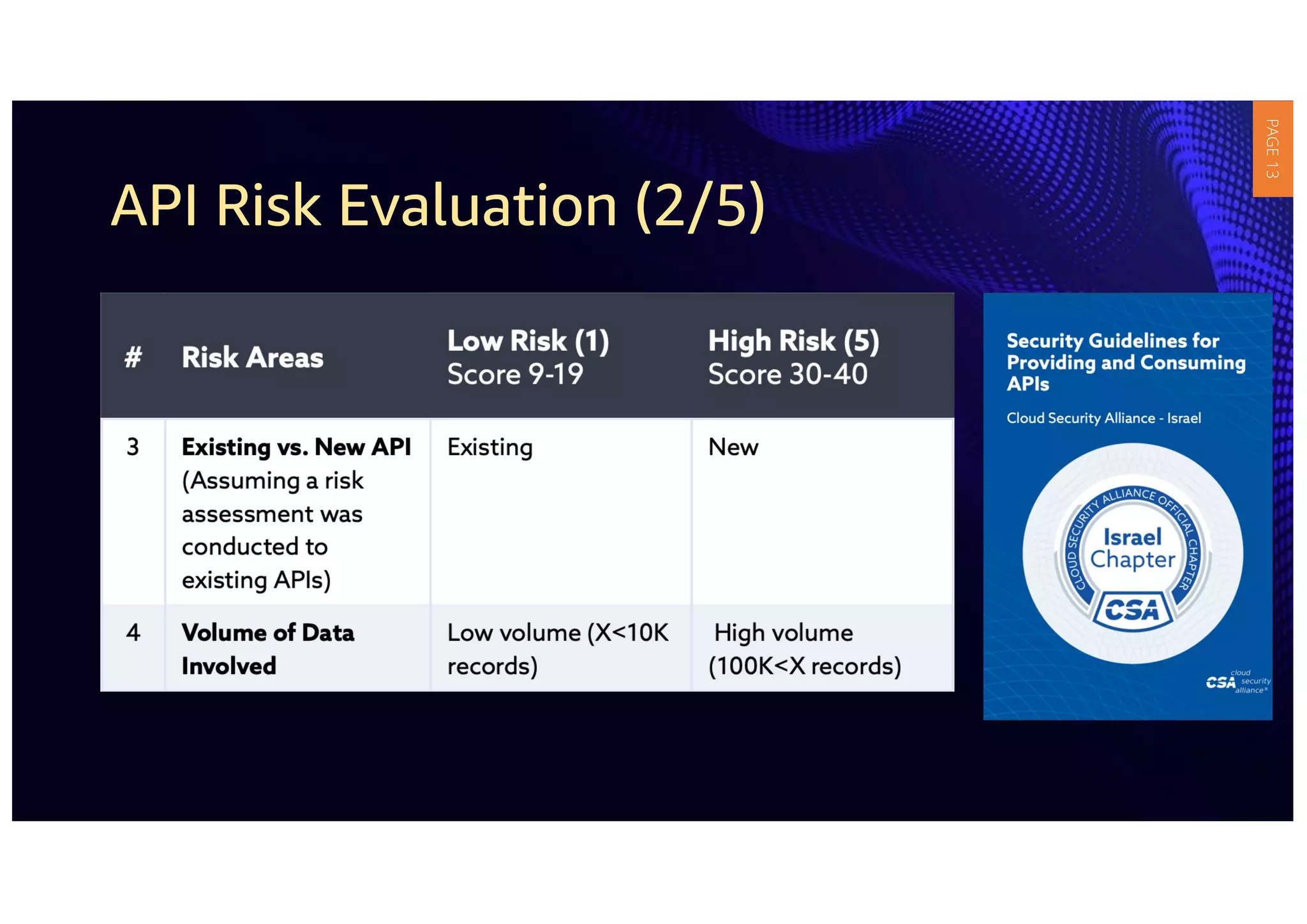
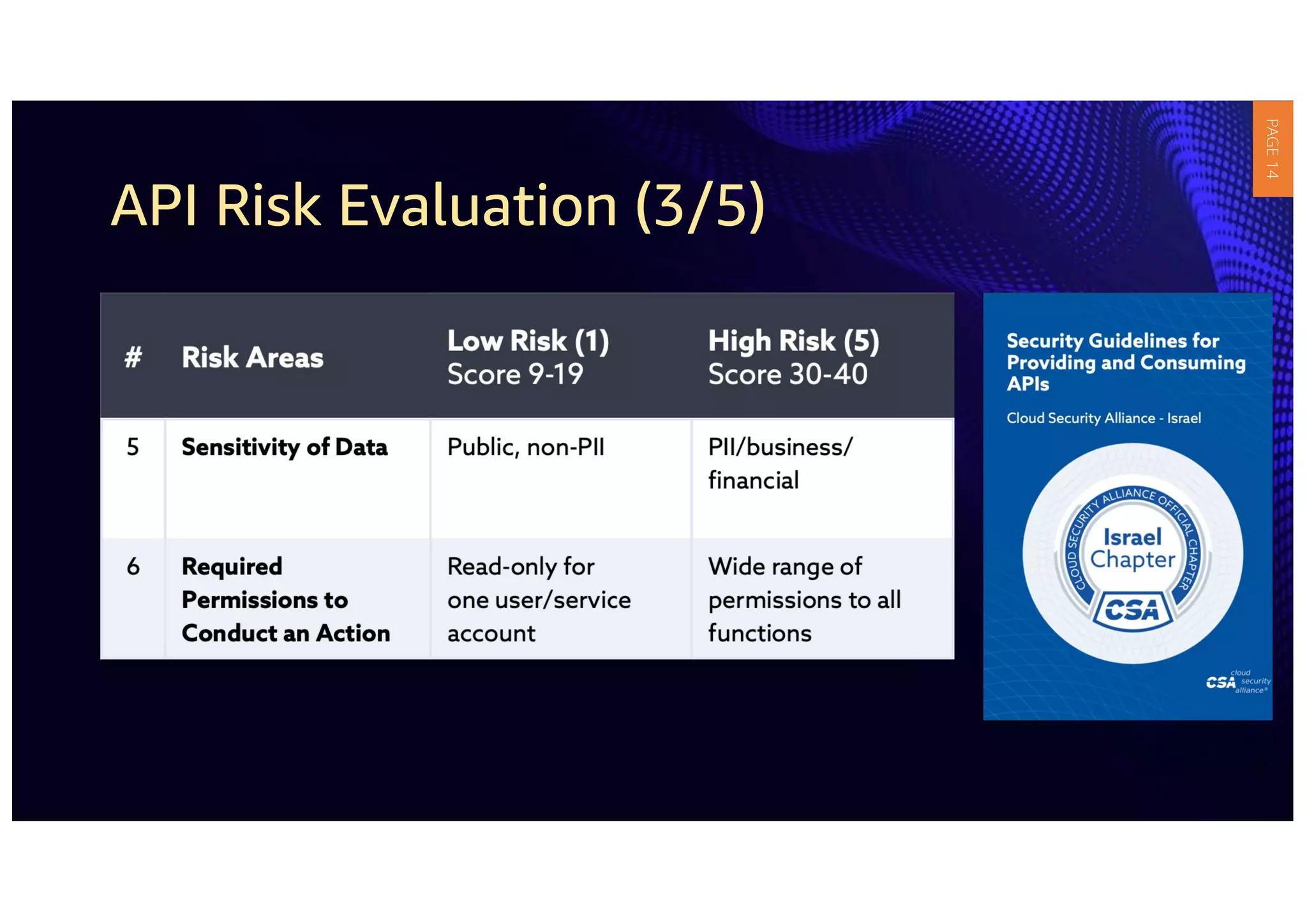
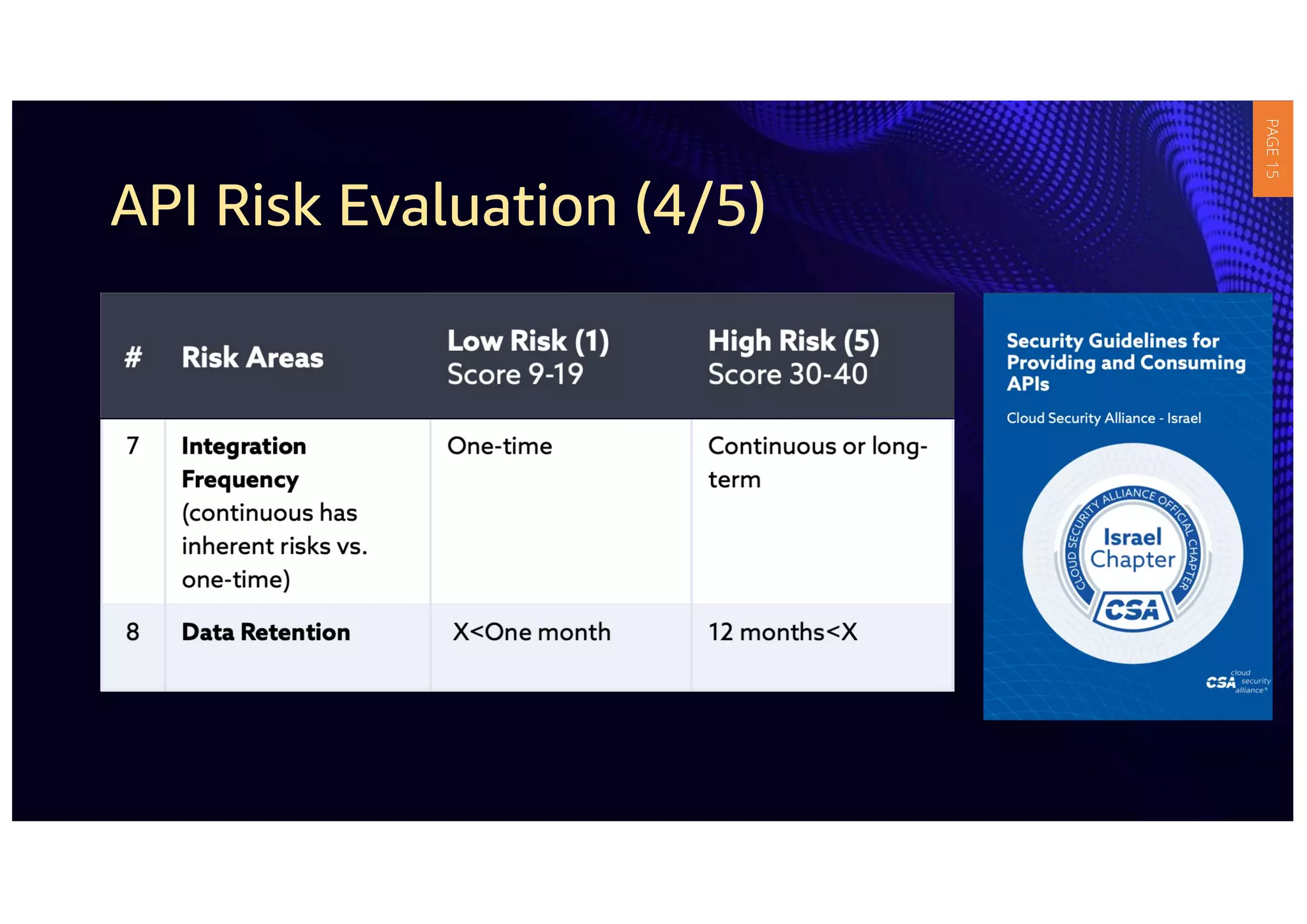
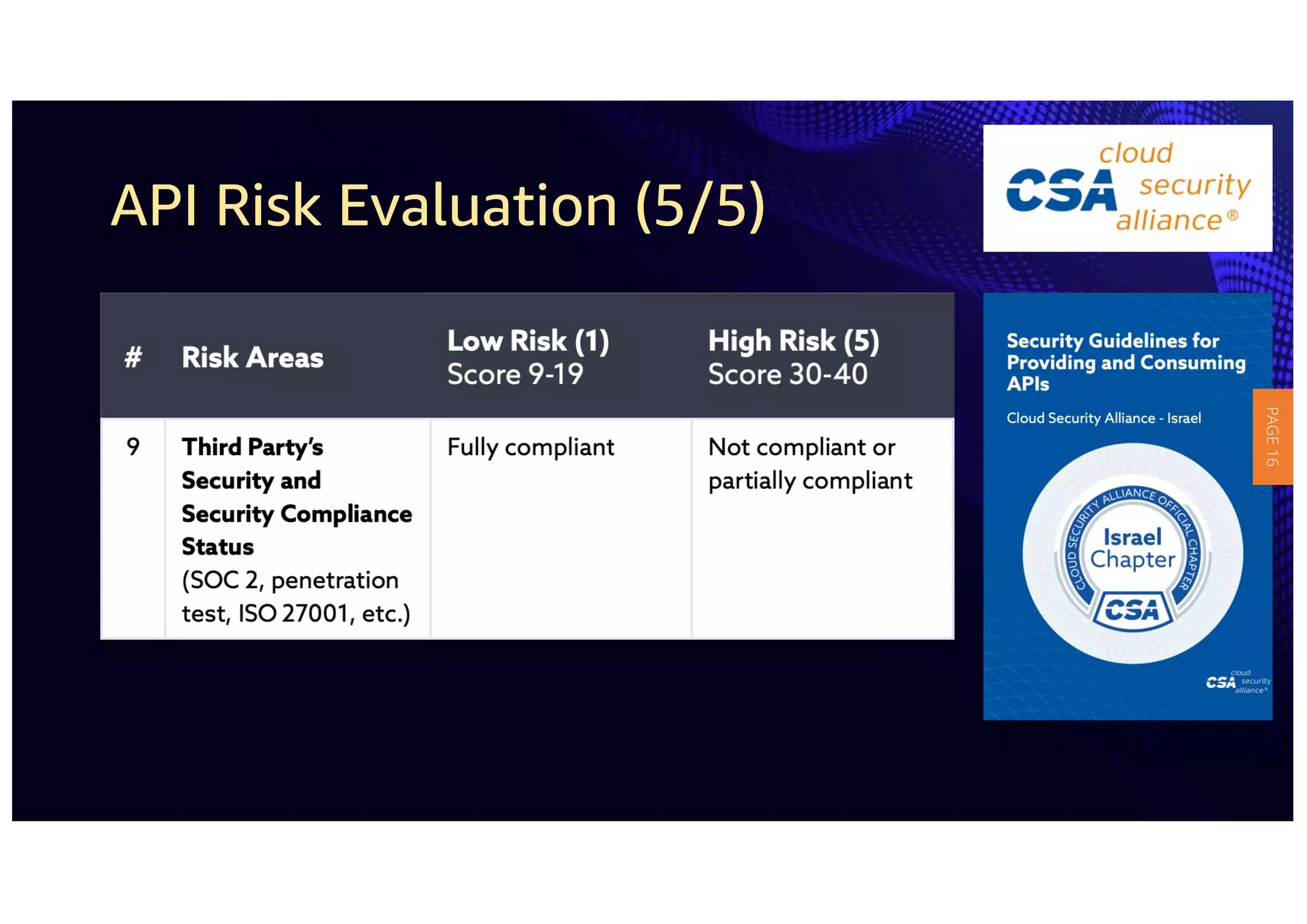
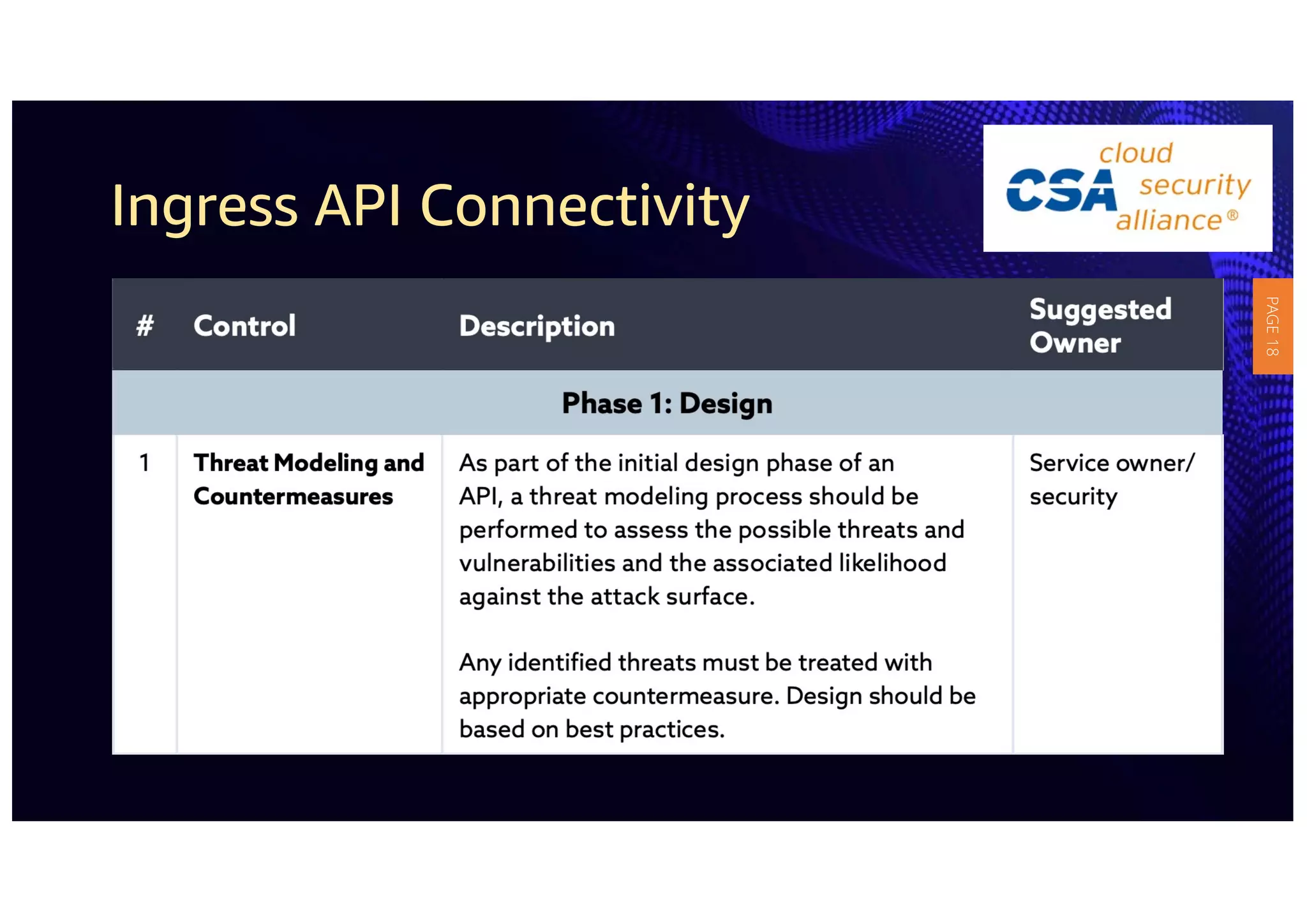
1) The document provides guidelines for securing APIs when providing and consuming services. It outlines evaluating API risks, securing ingress API connectivity, and mapping the OWASP API security risks to the ingress API development lifecycle.
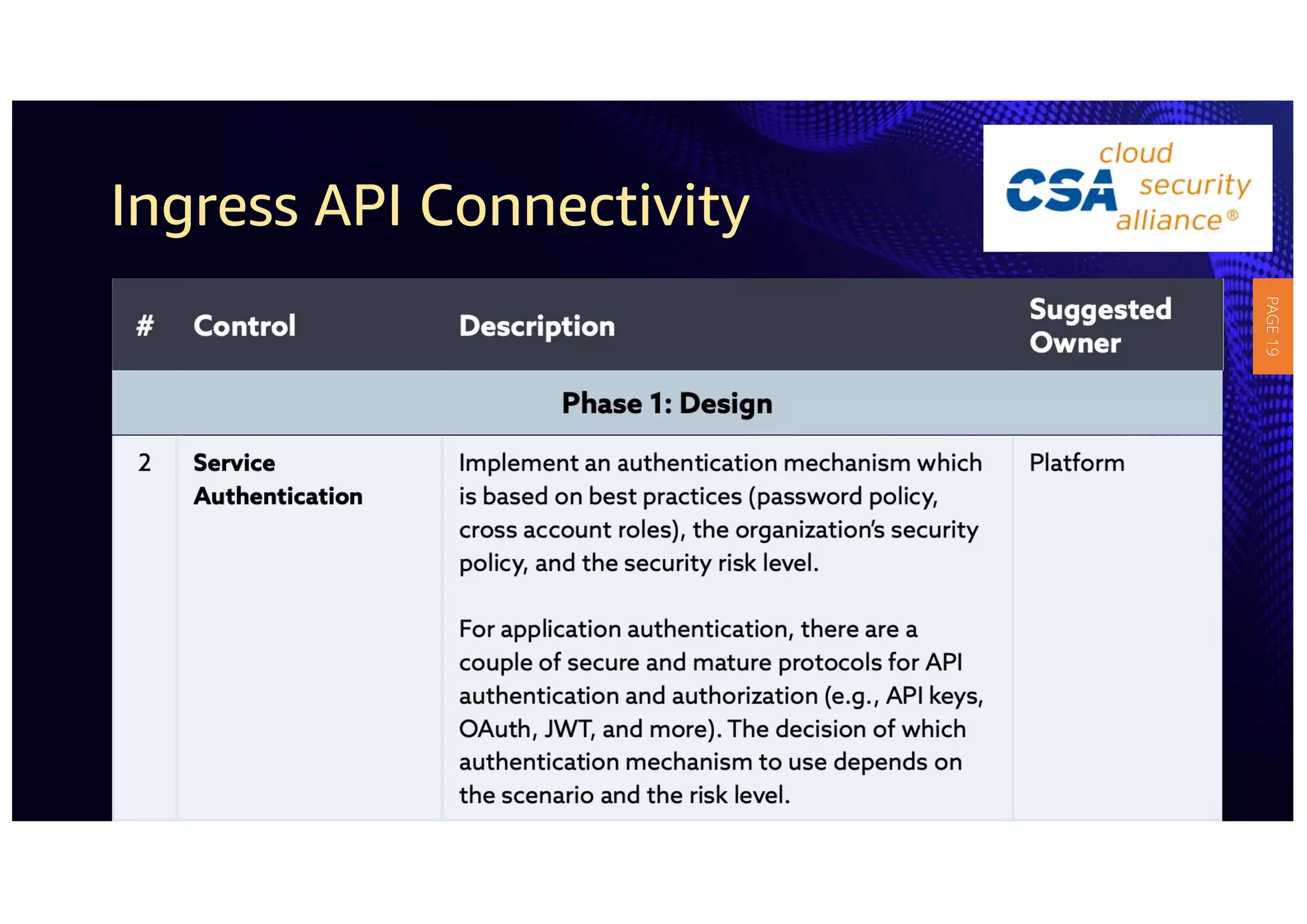
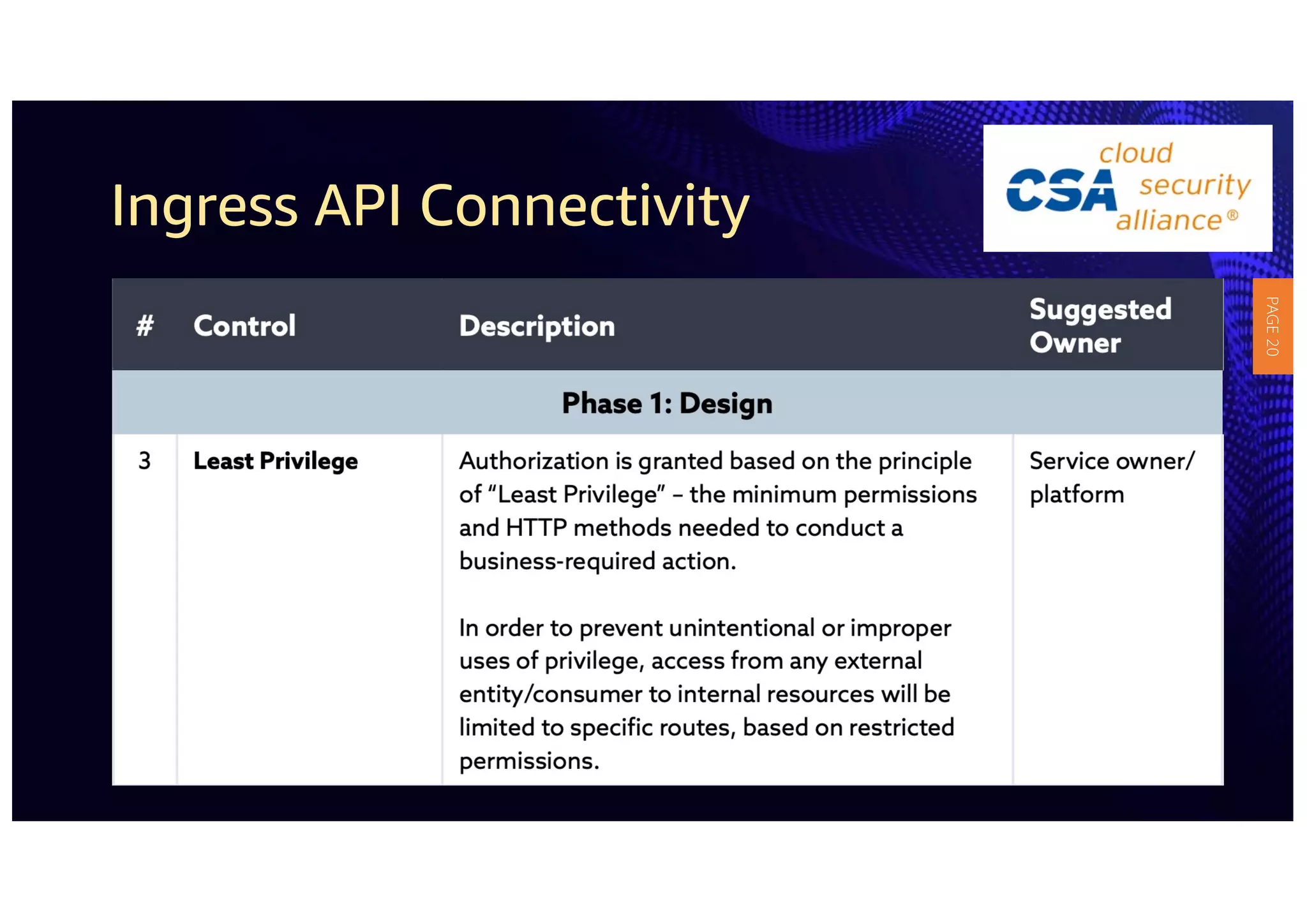
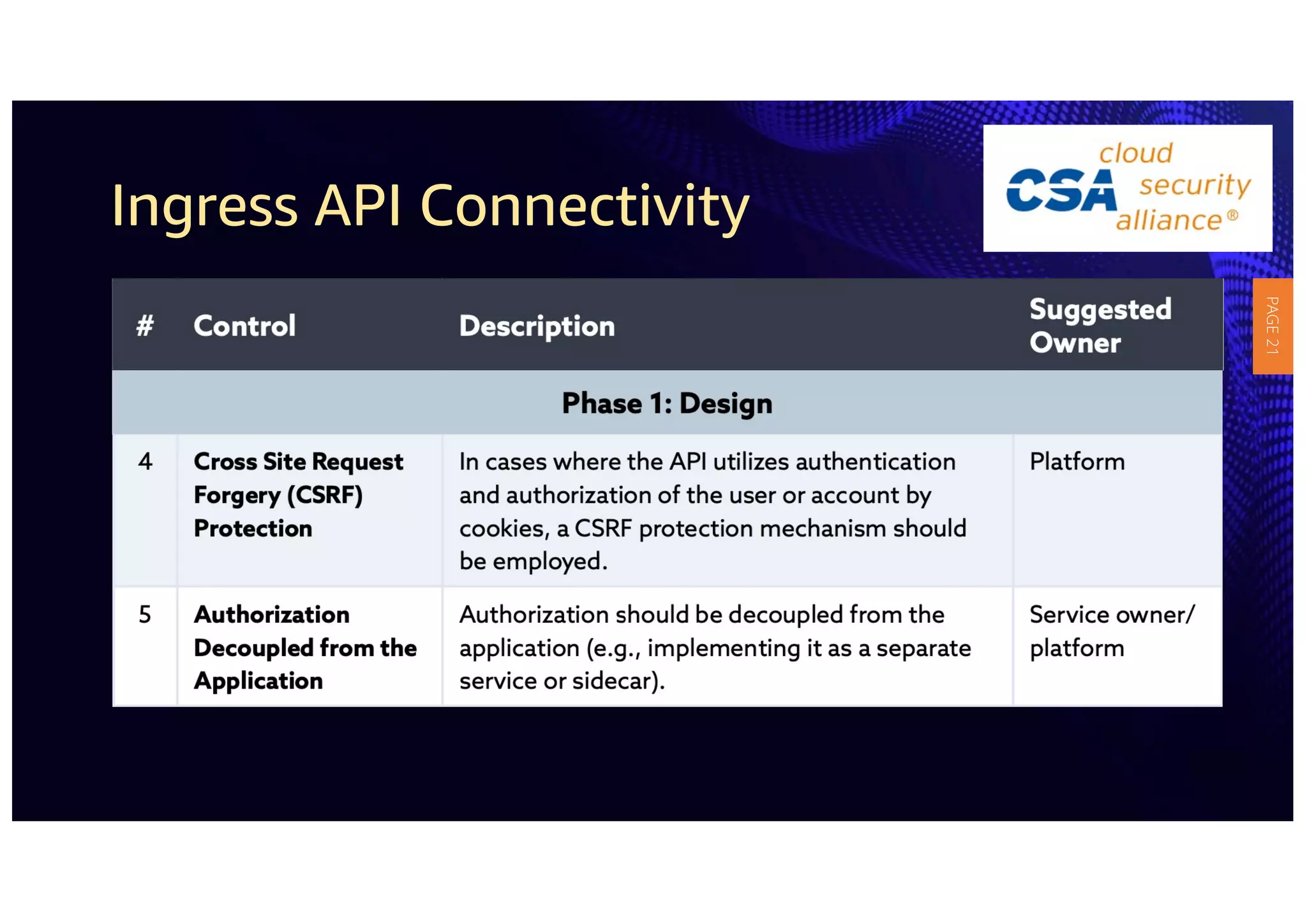
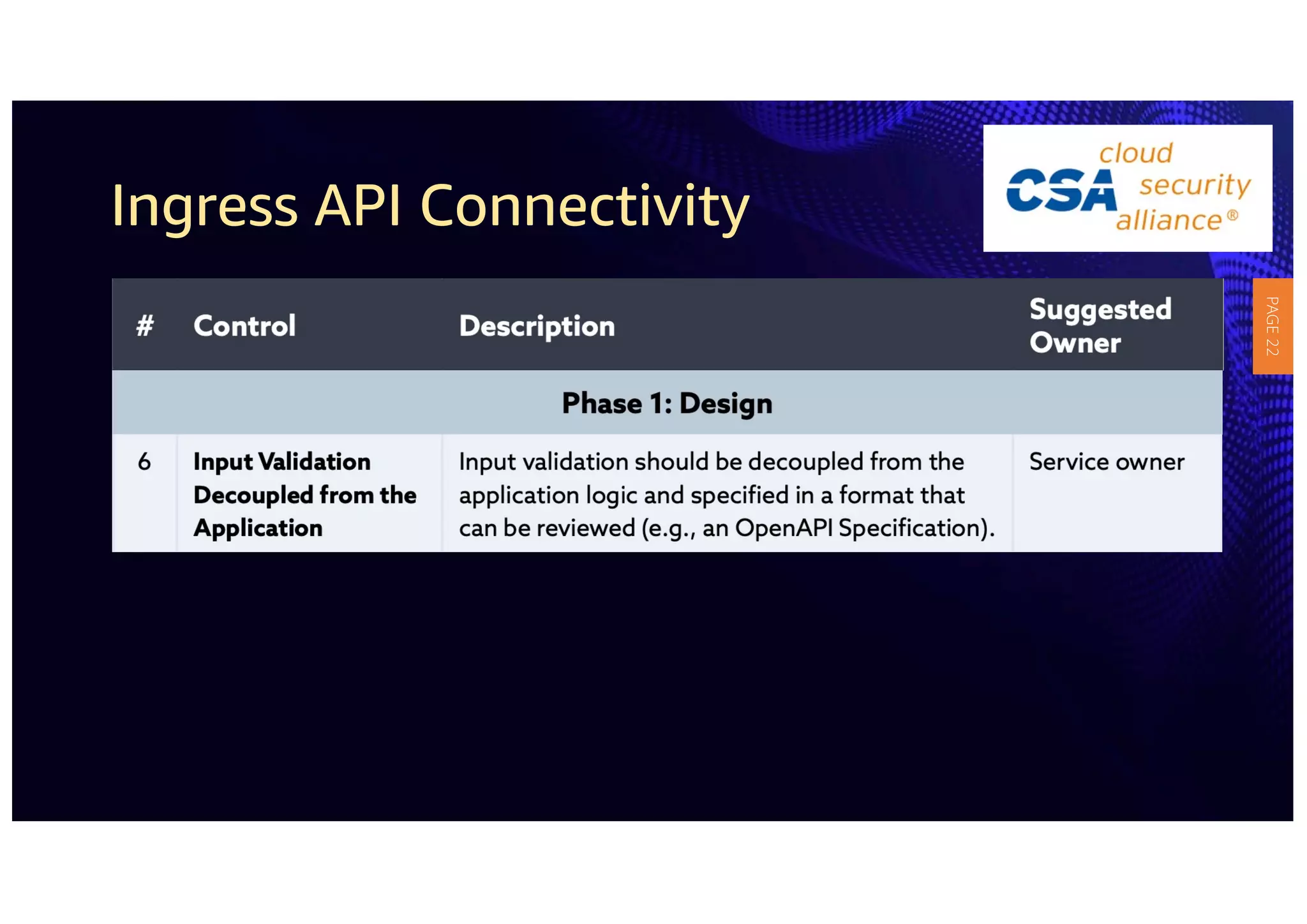
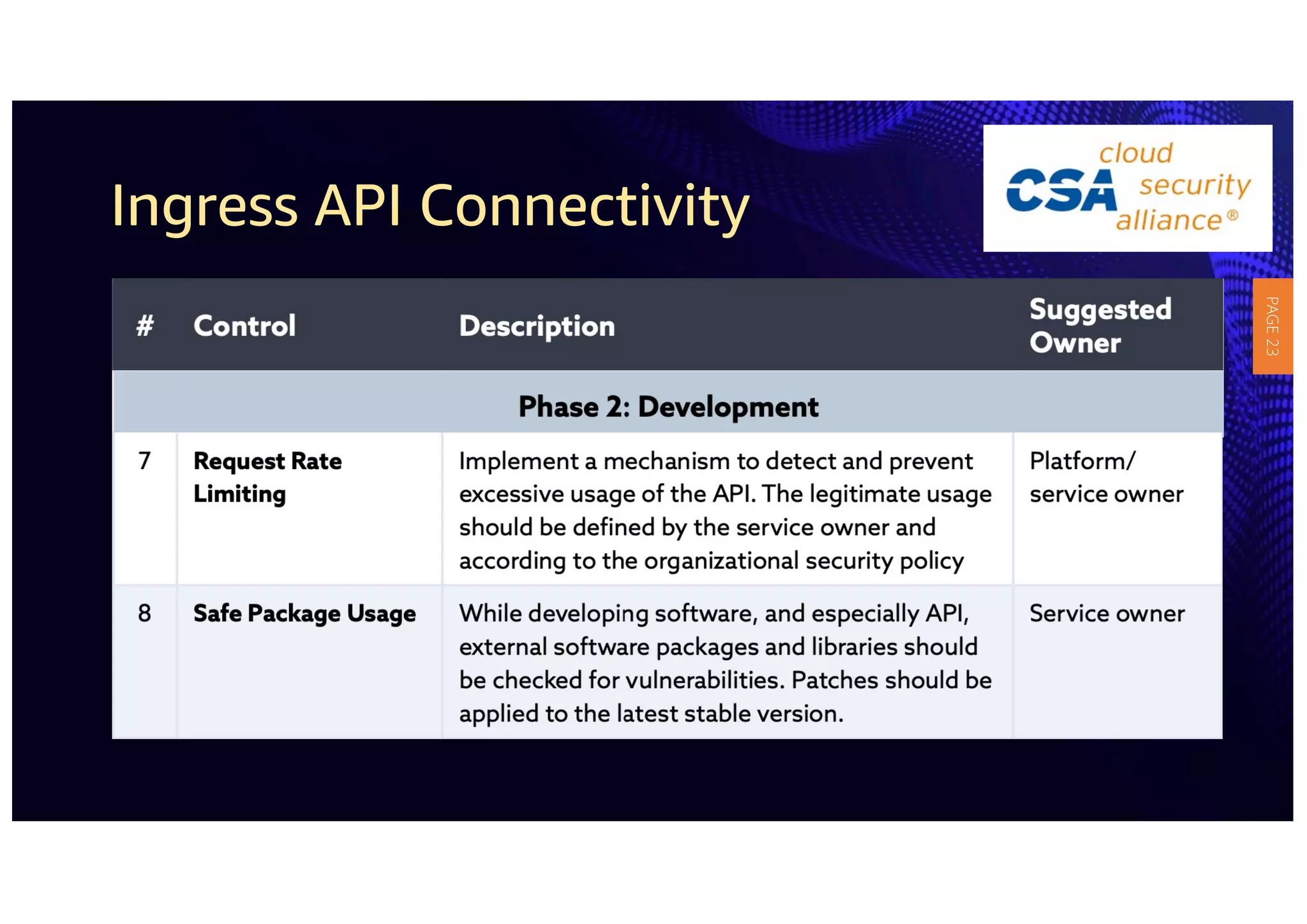
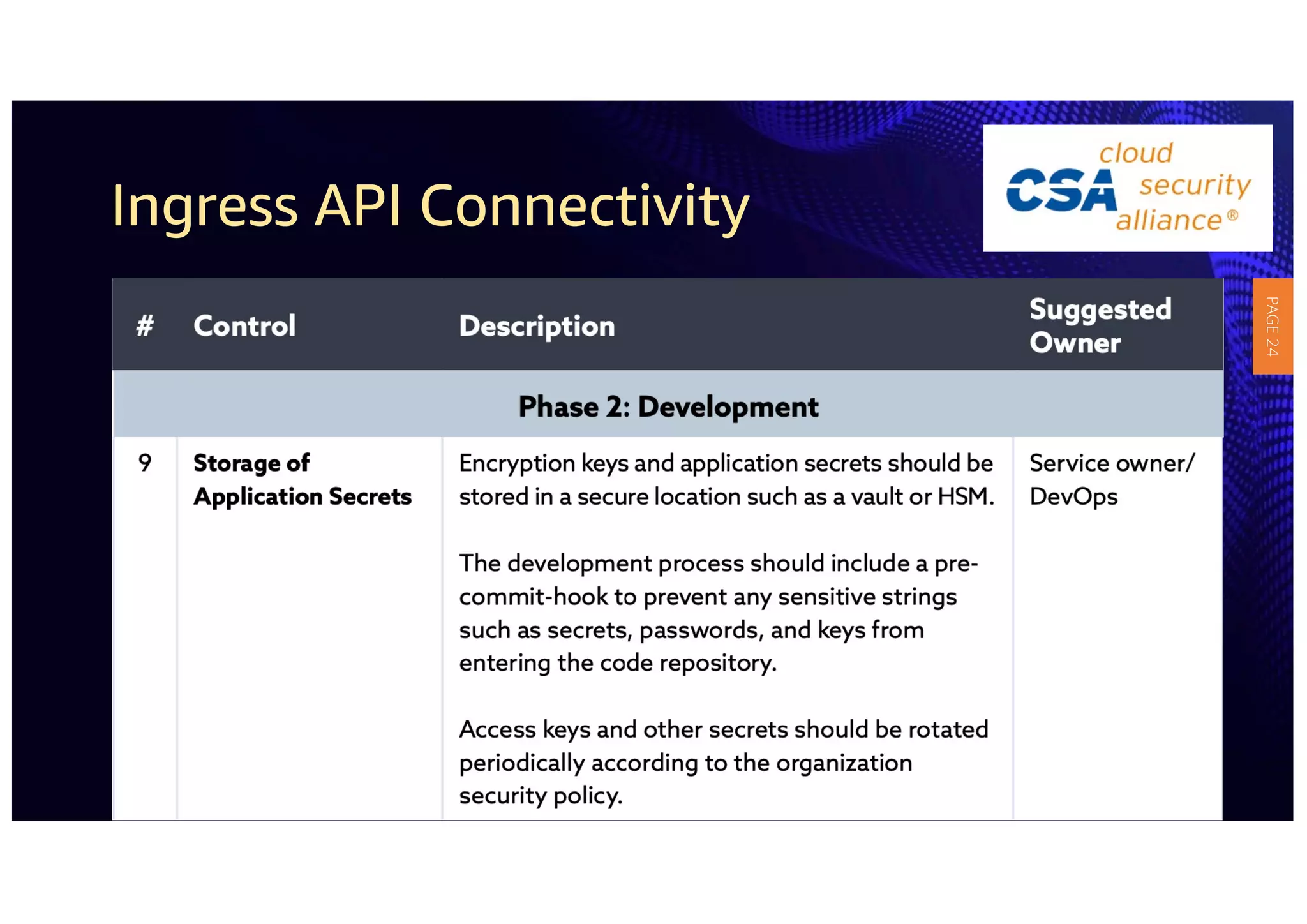
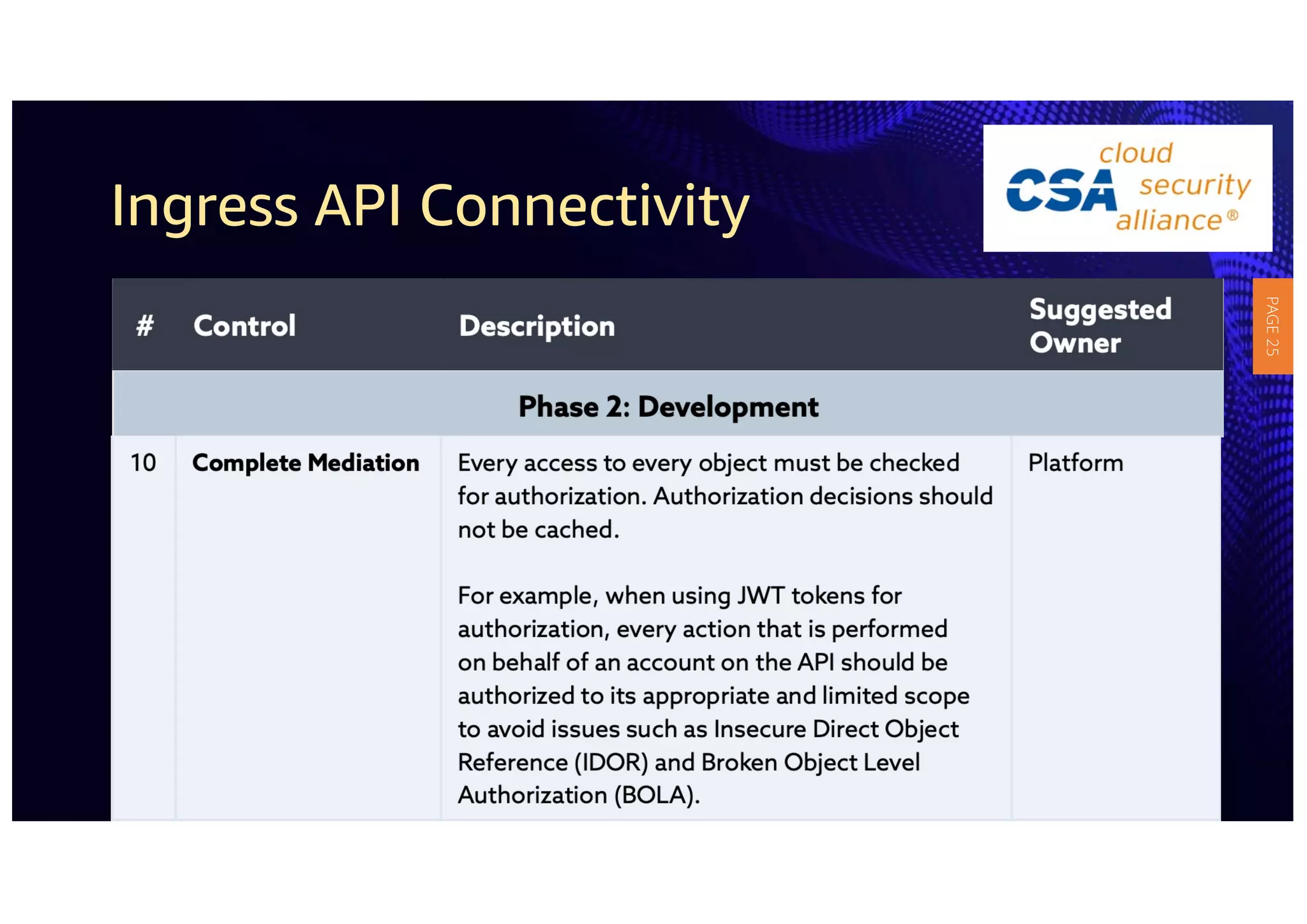
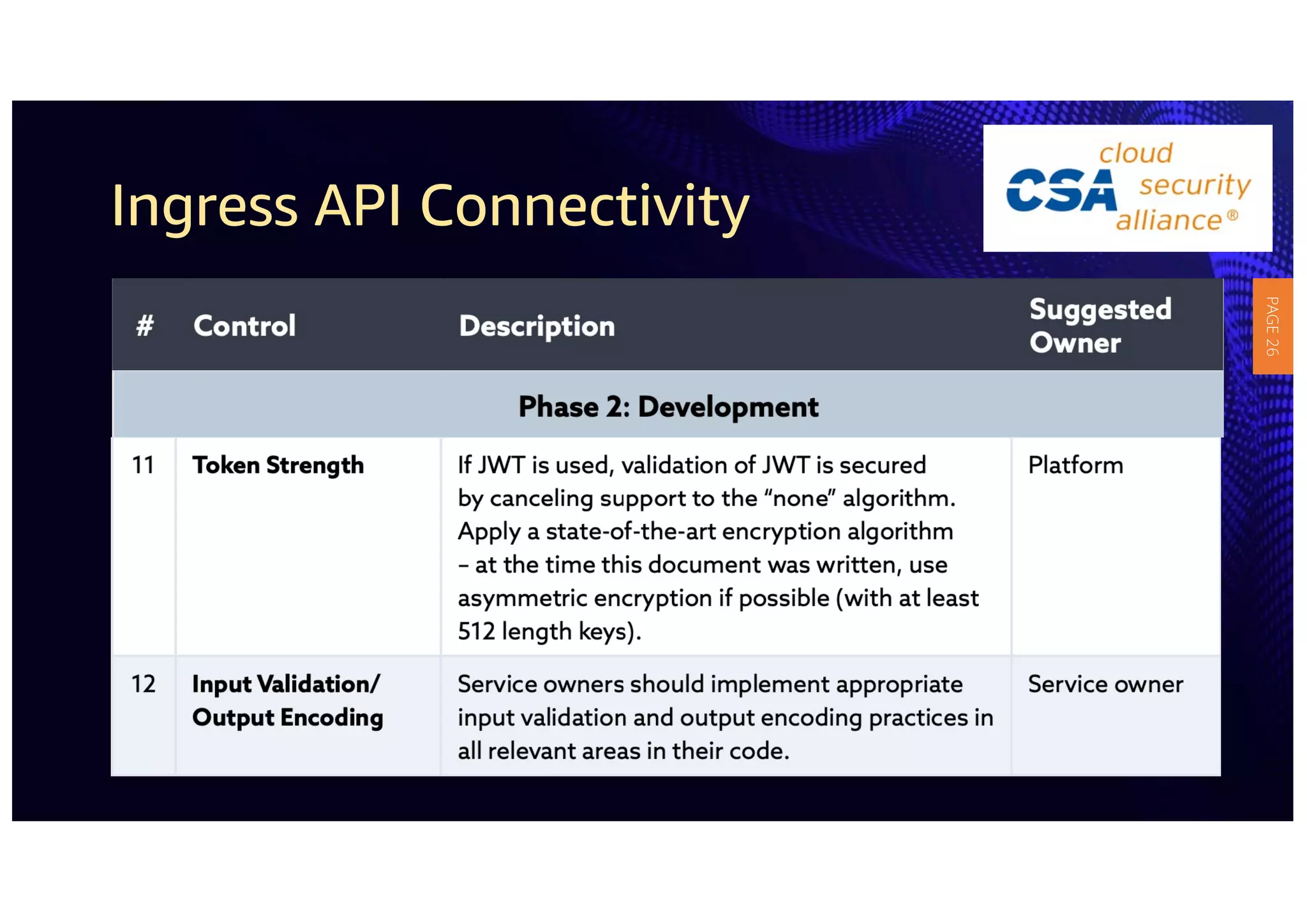
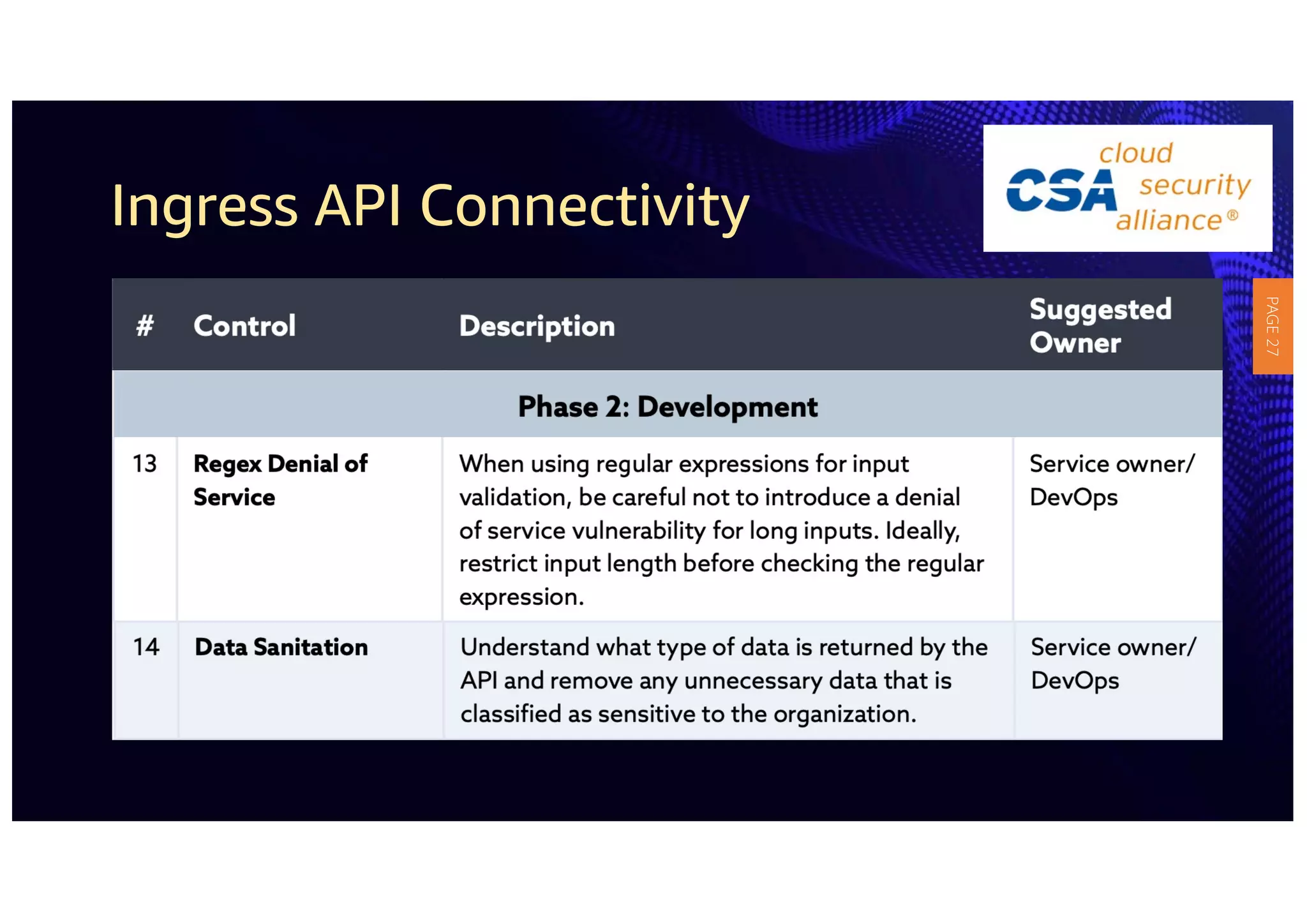
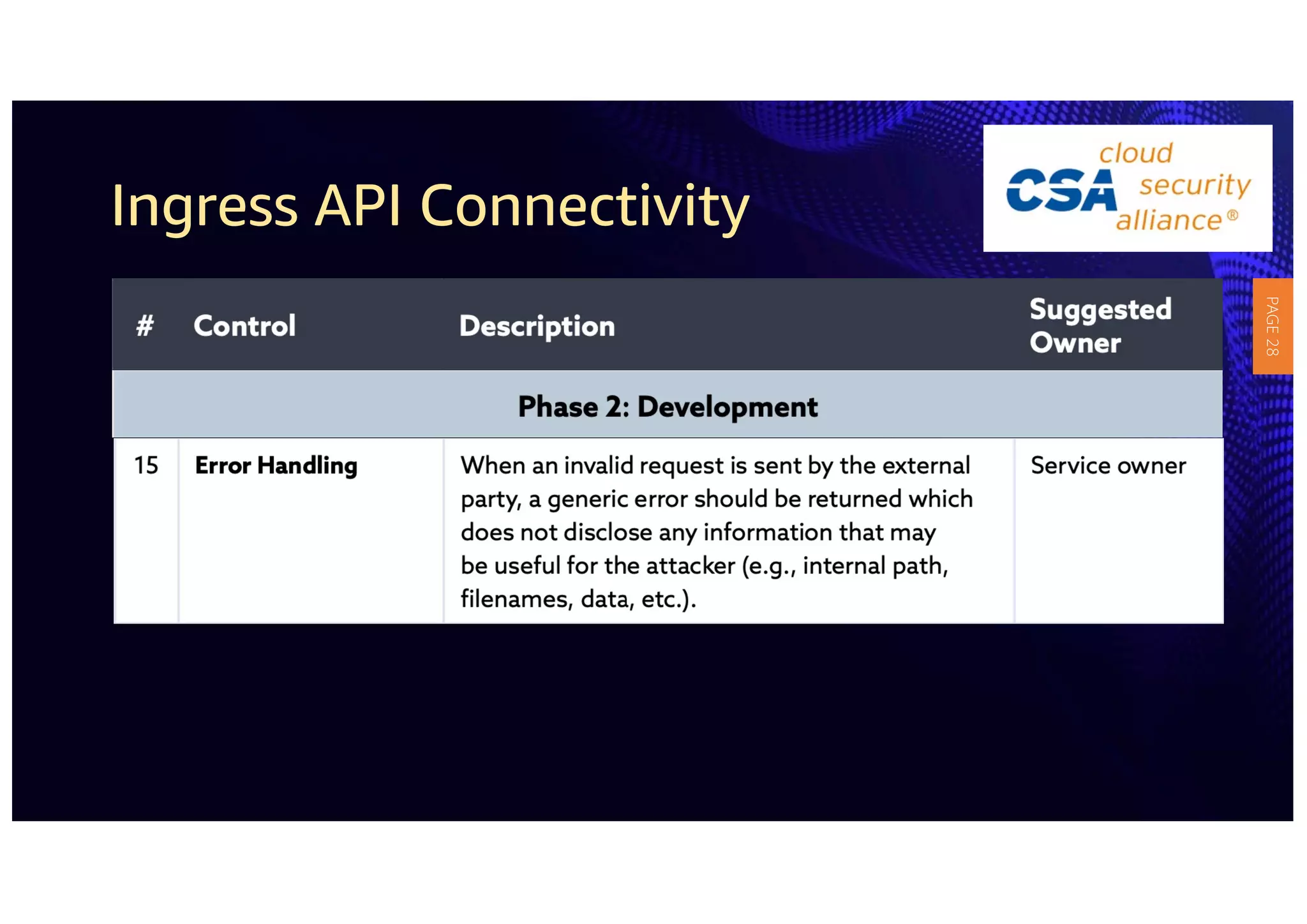
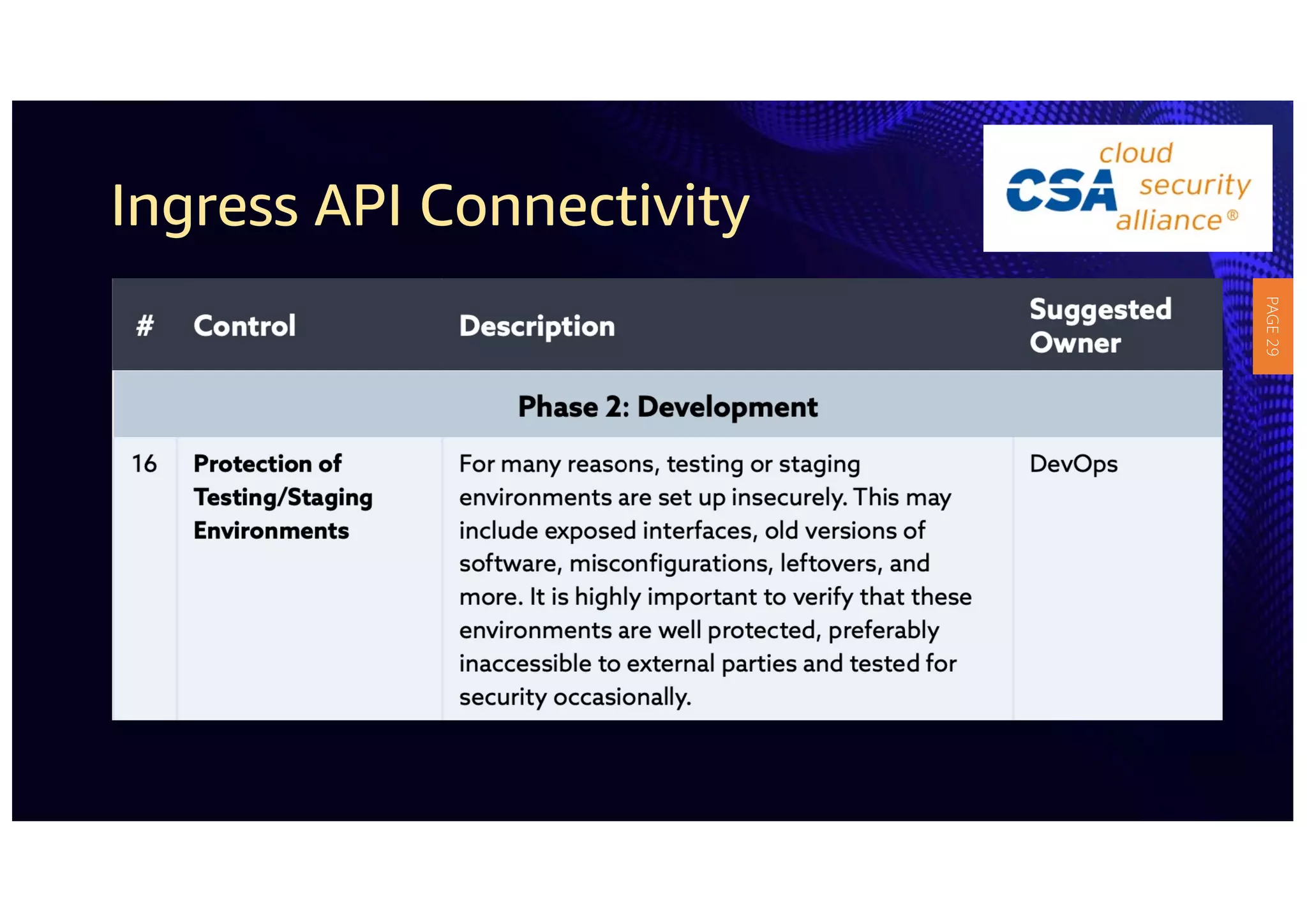
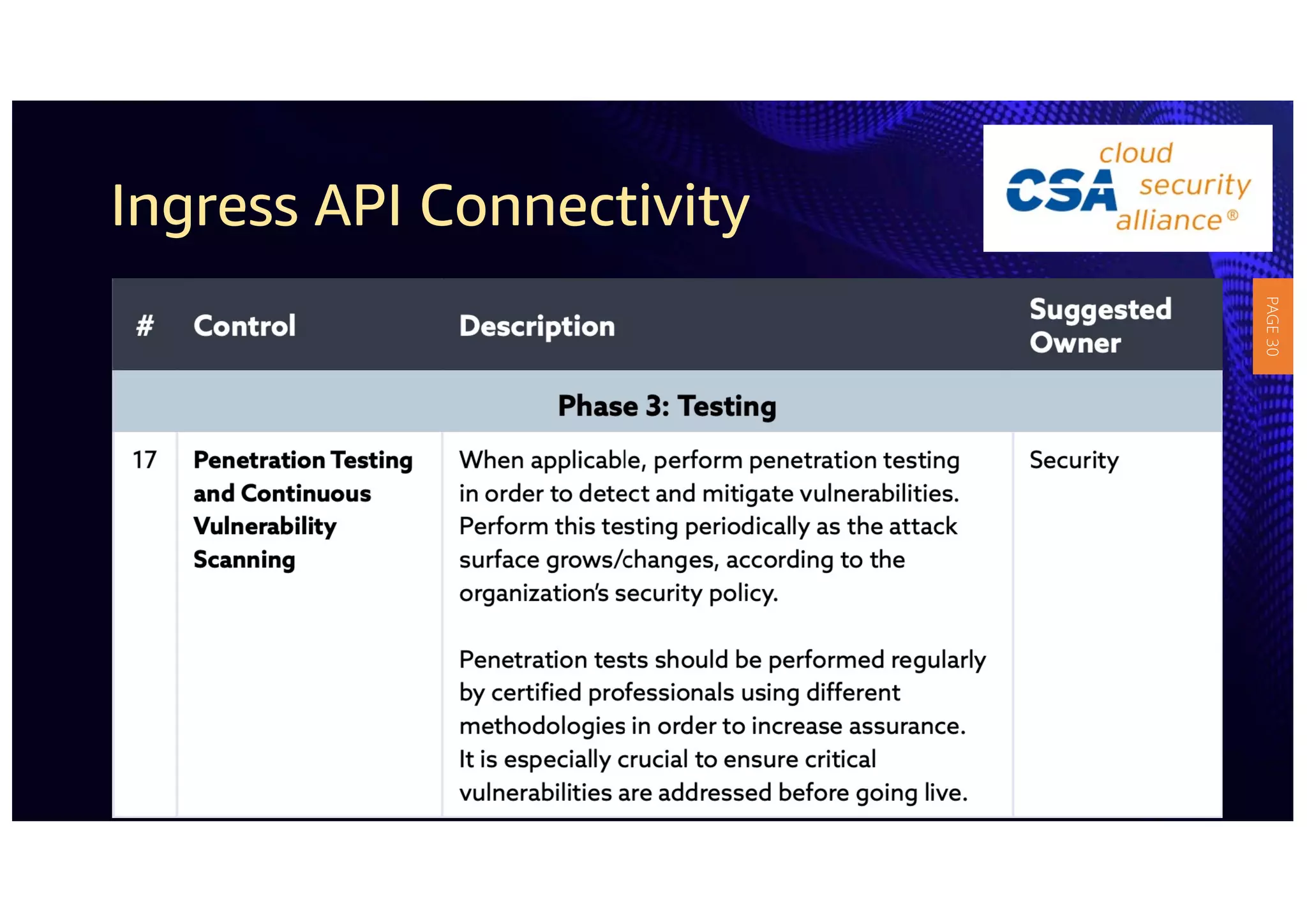
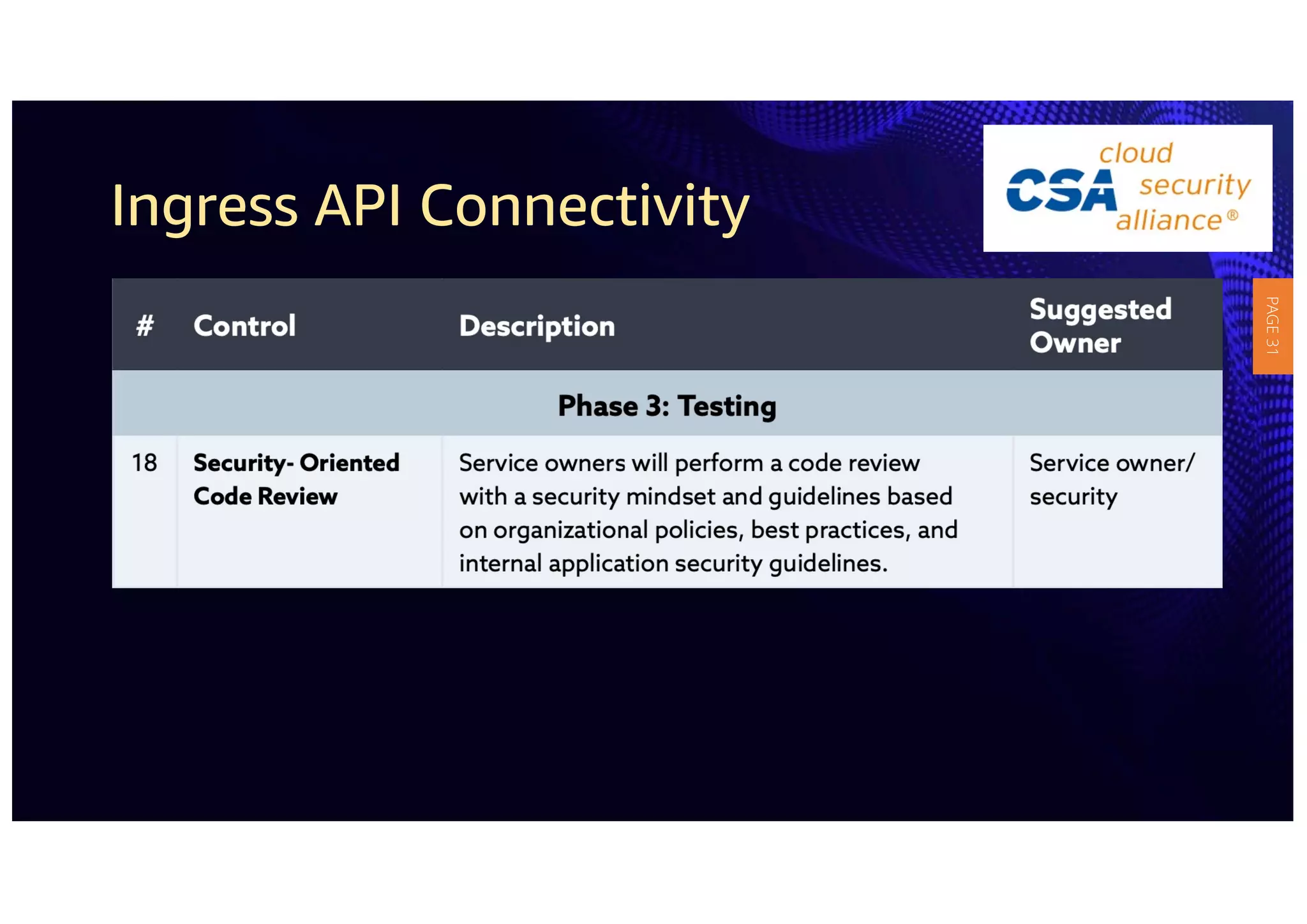
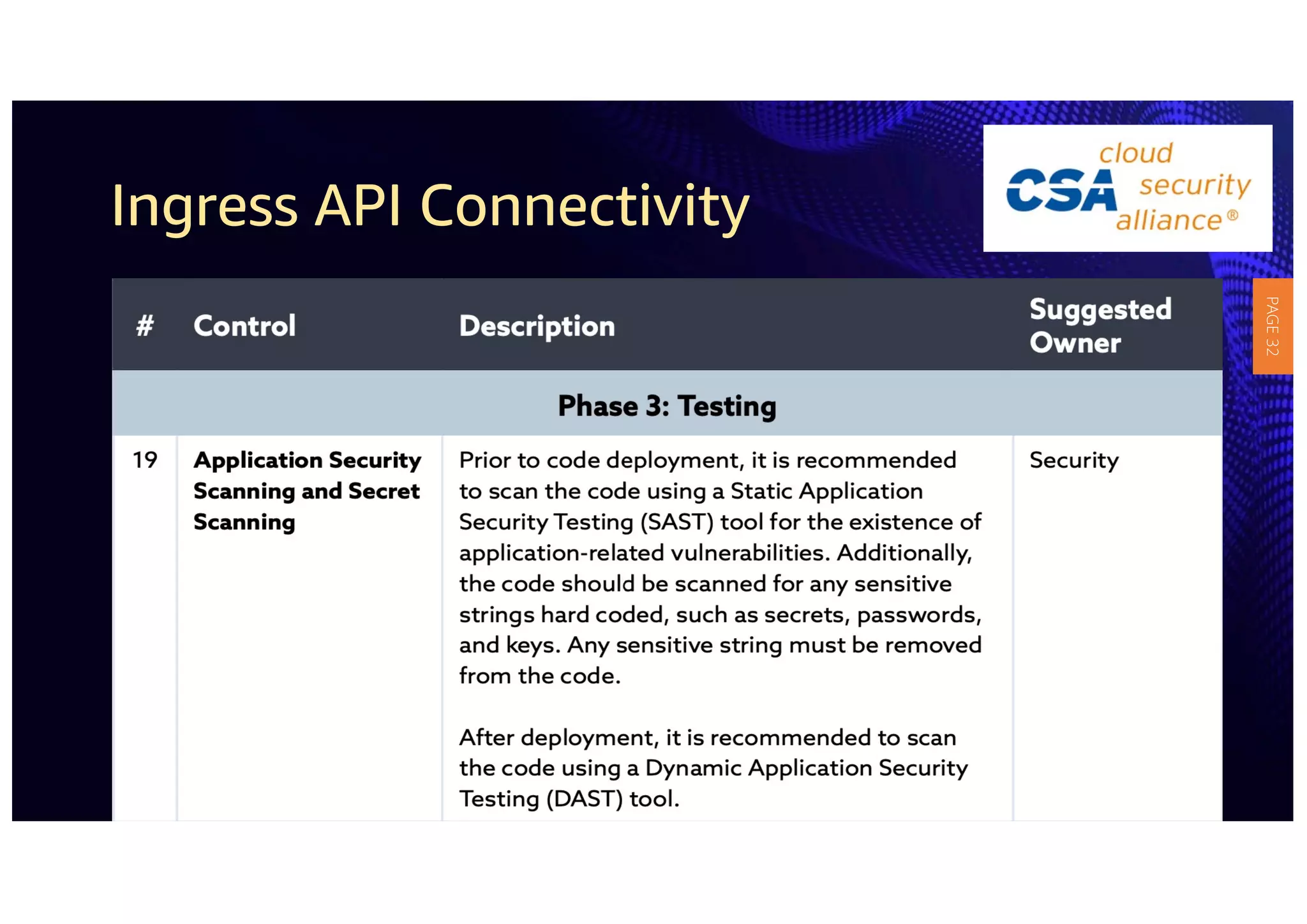
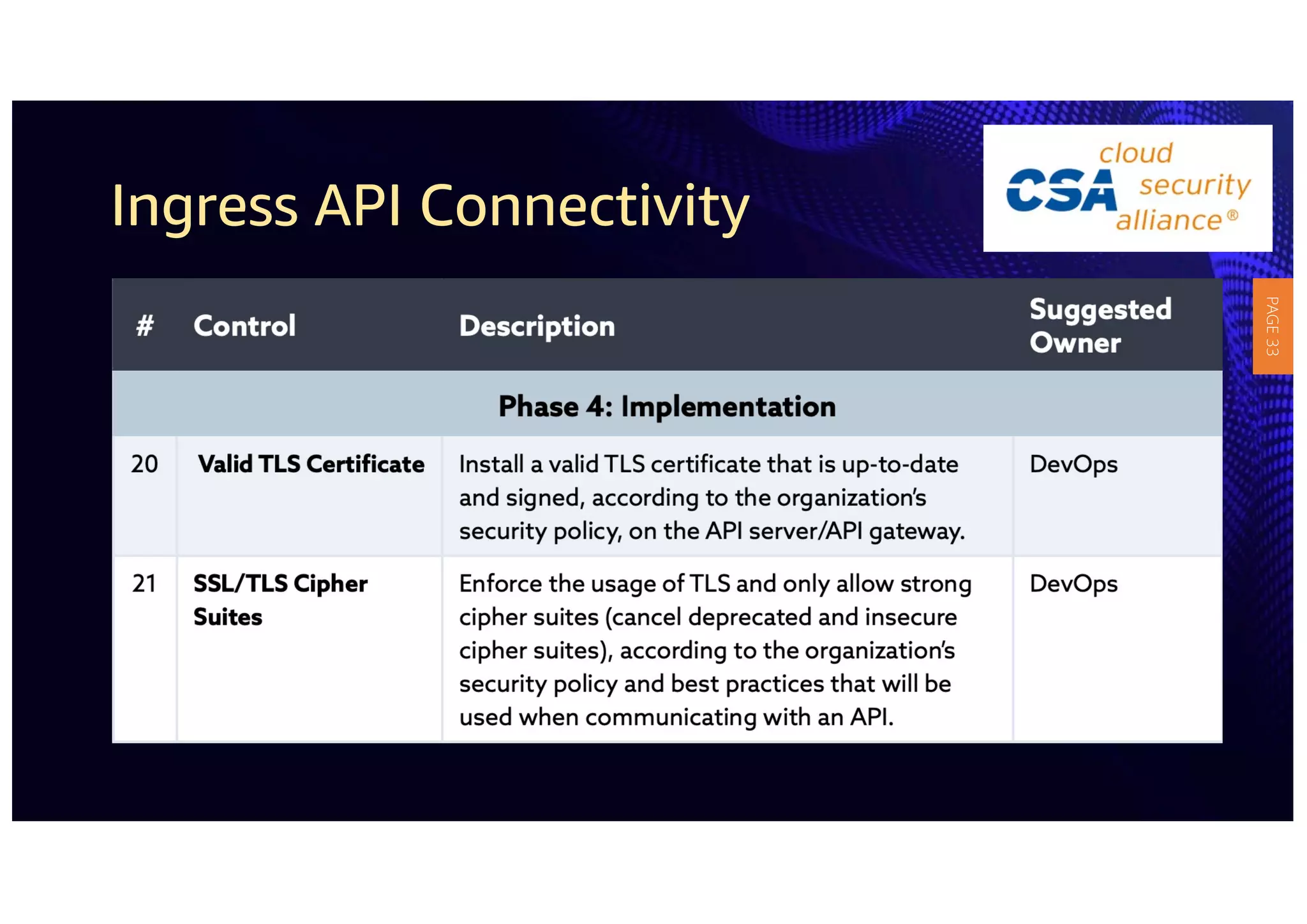
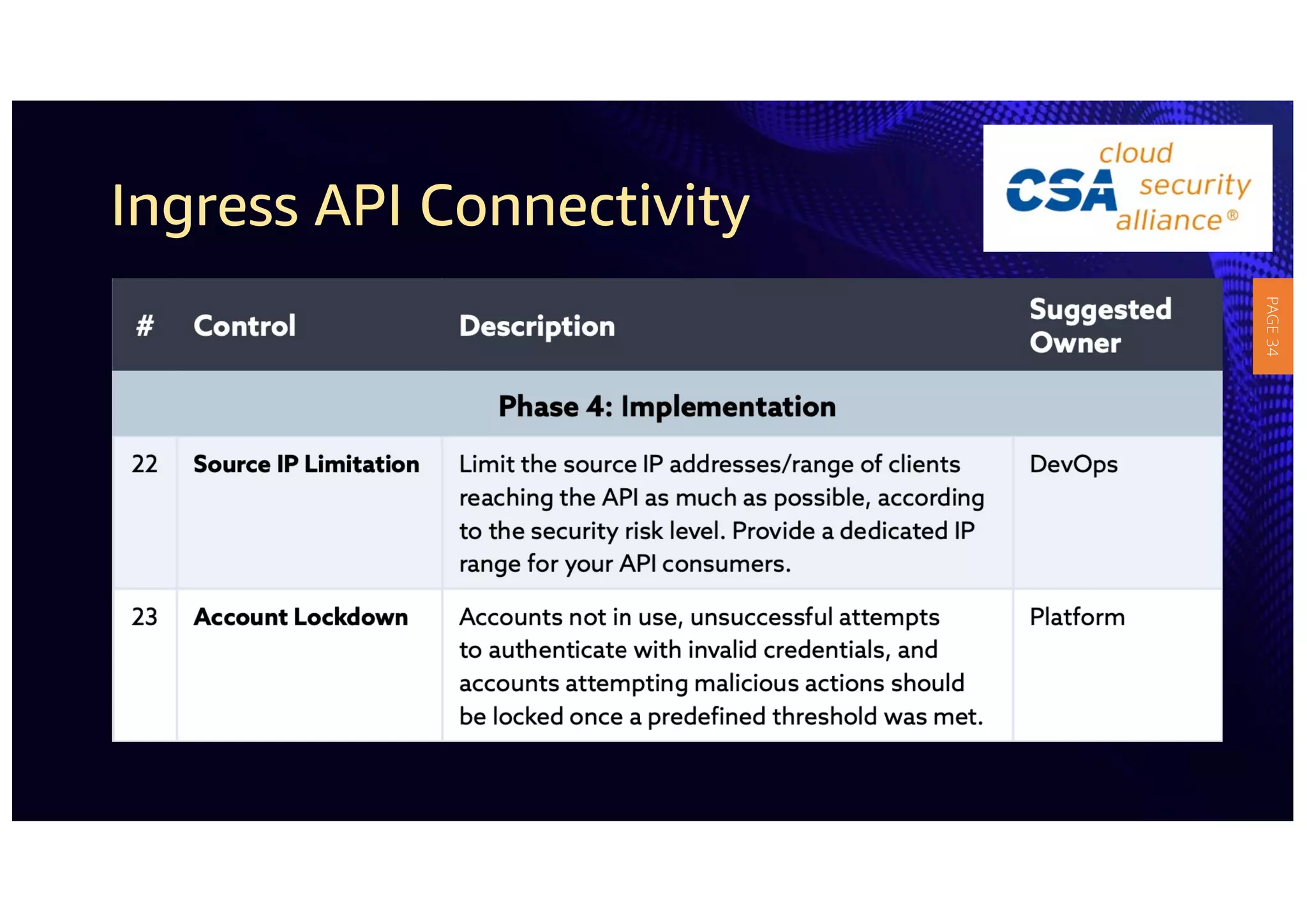
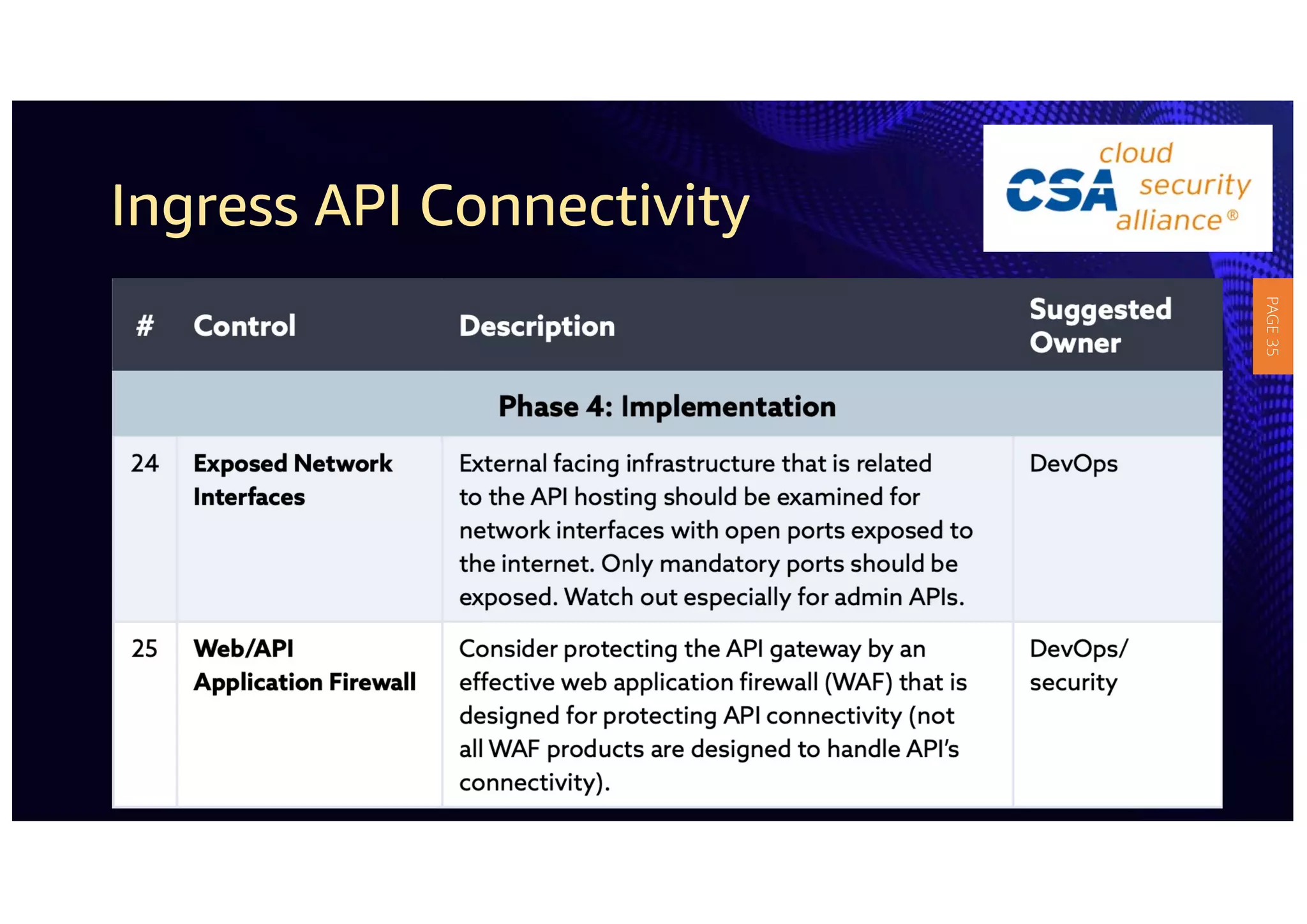
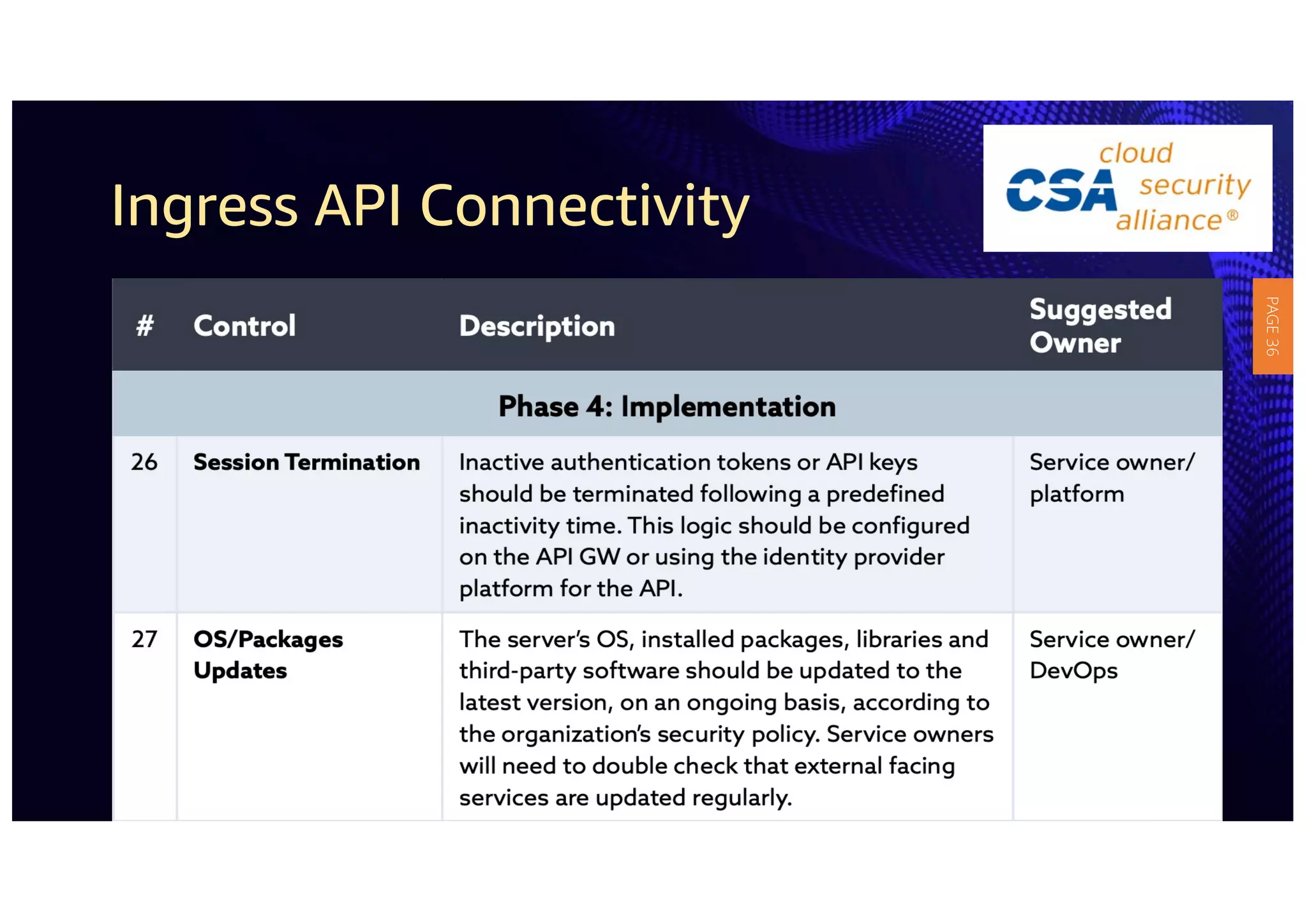
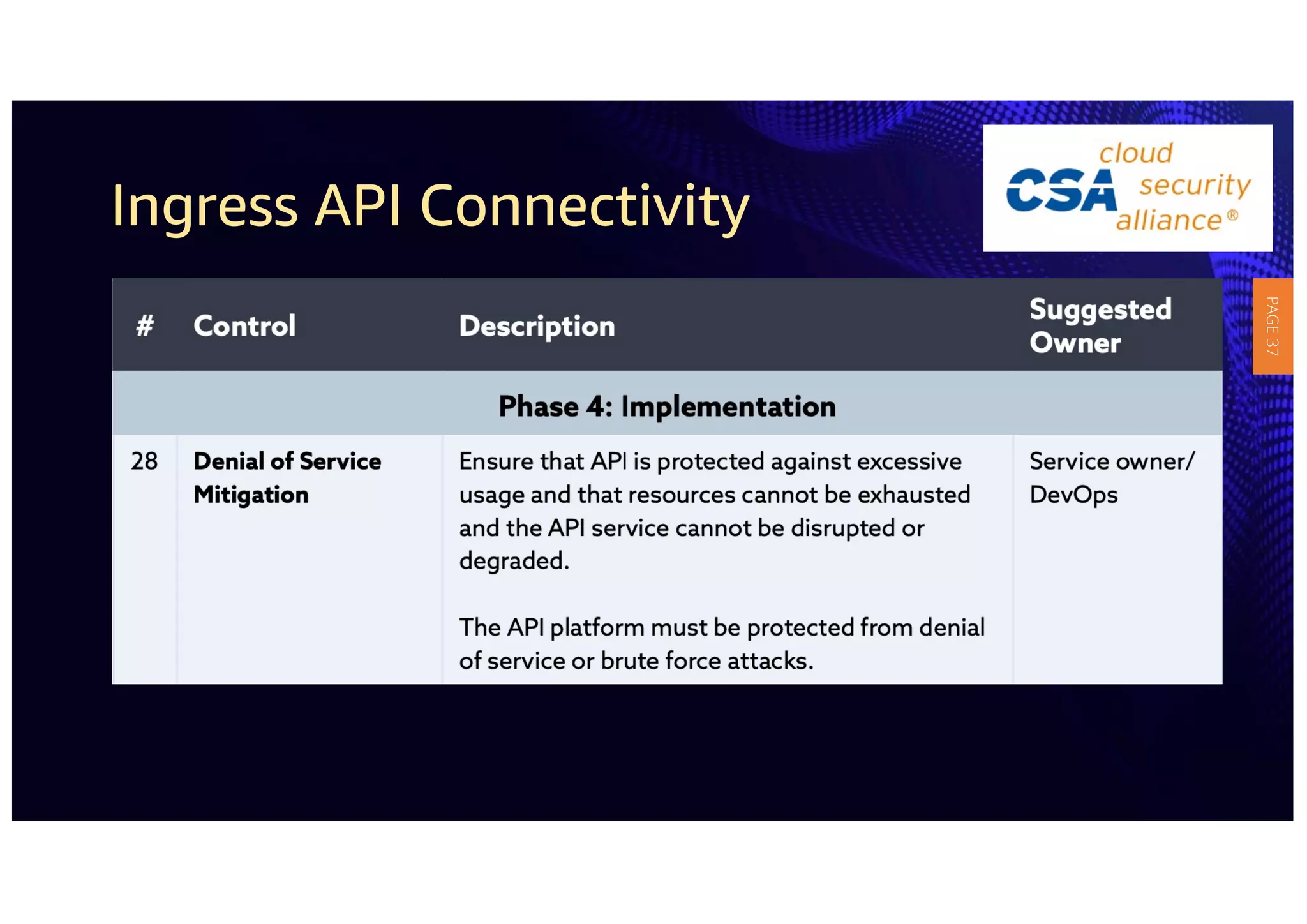
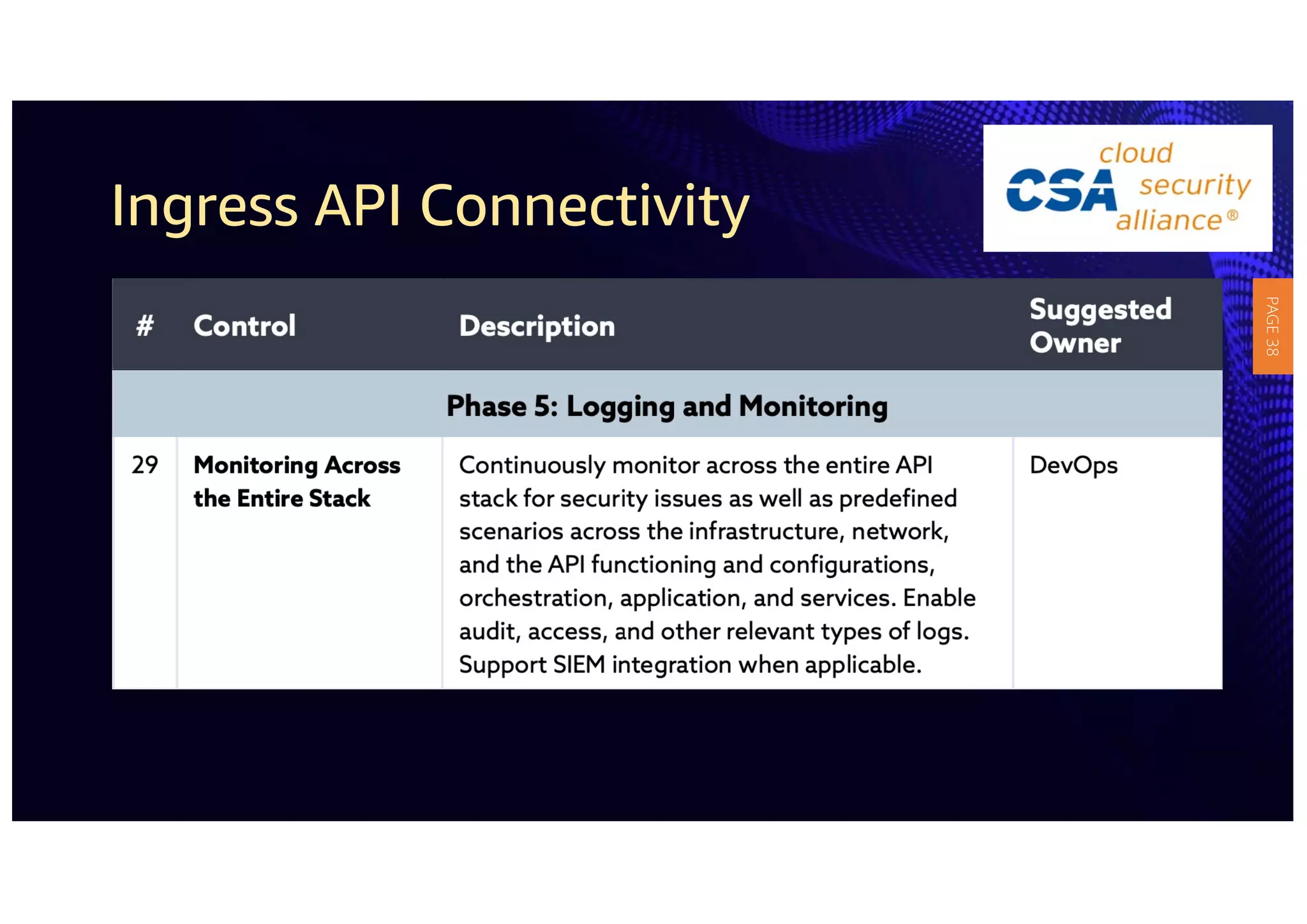
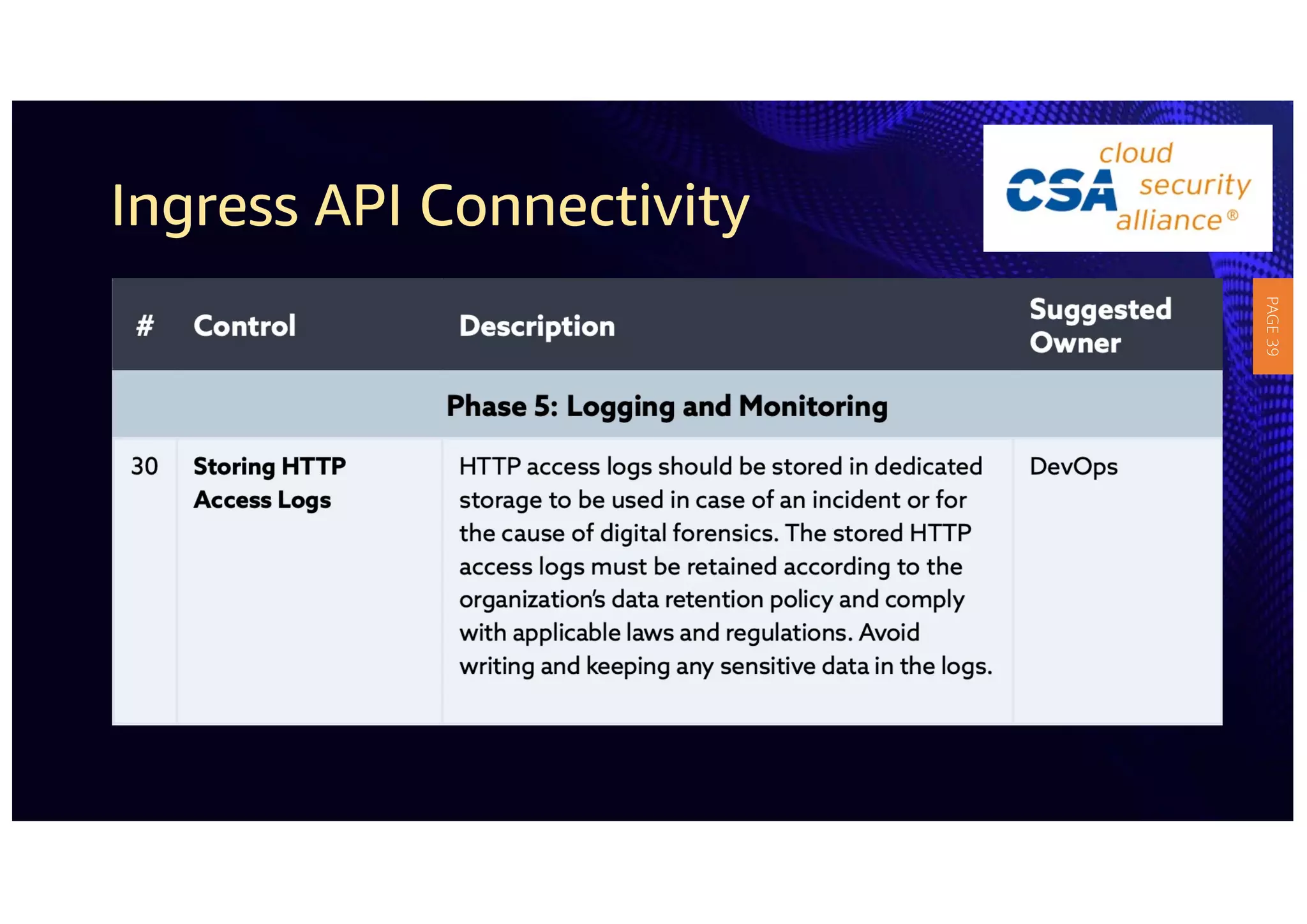
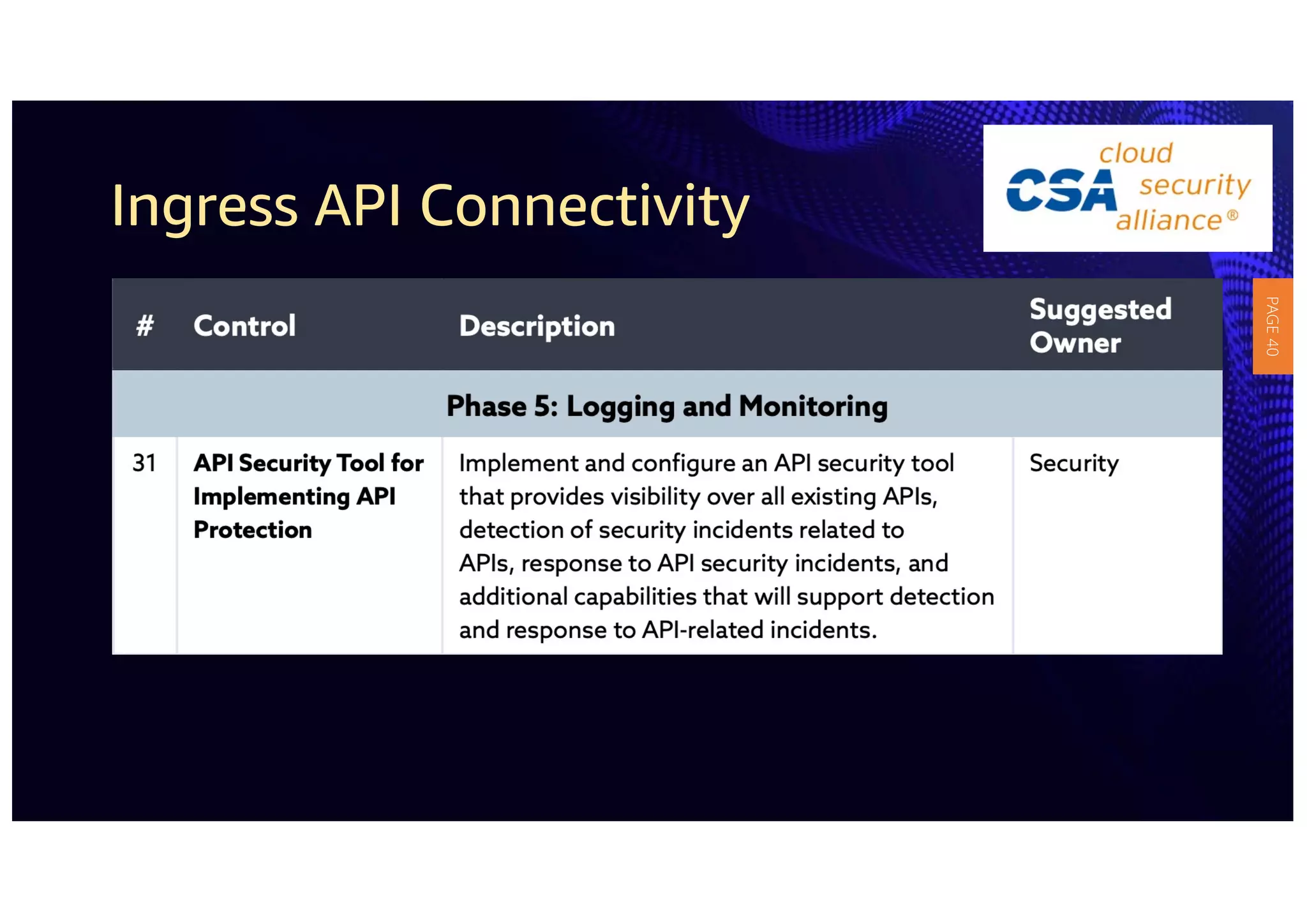
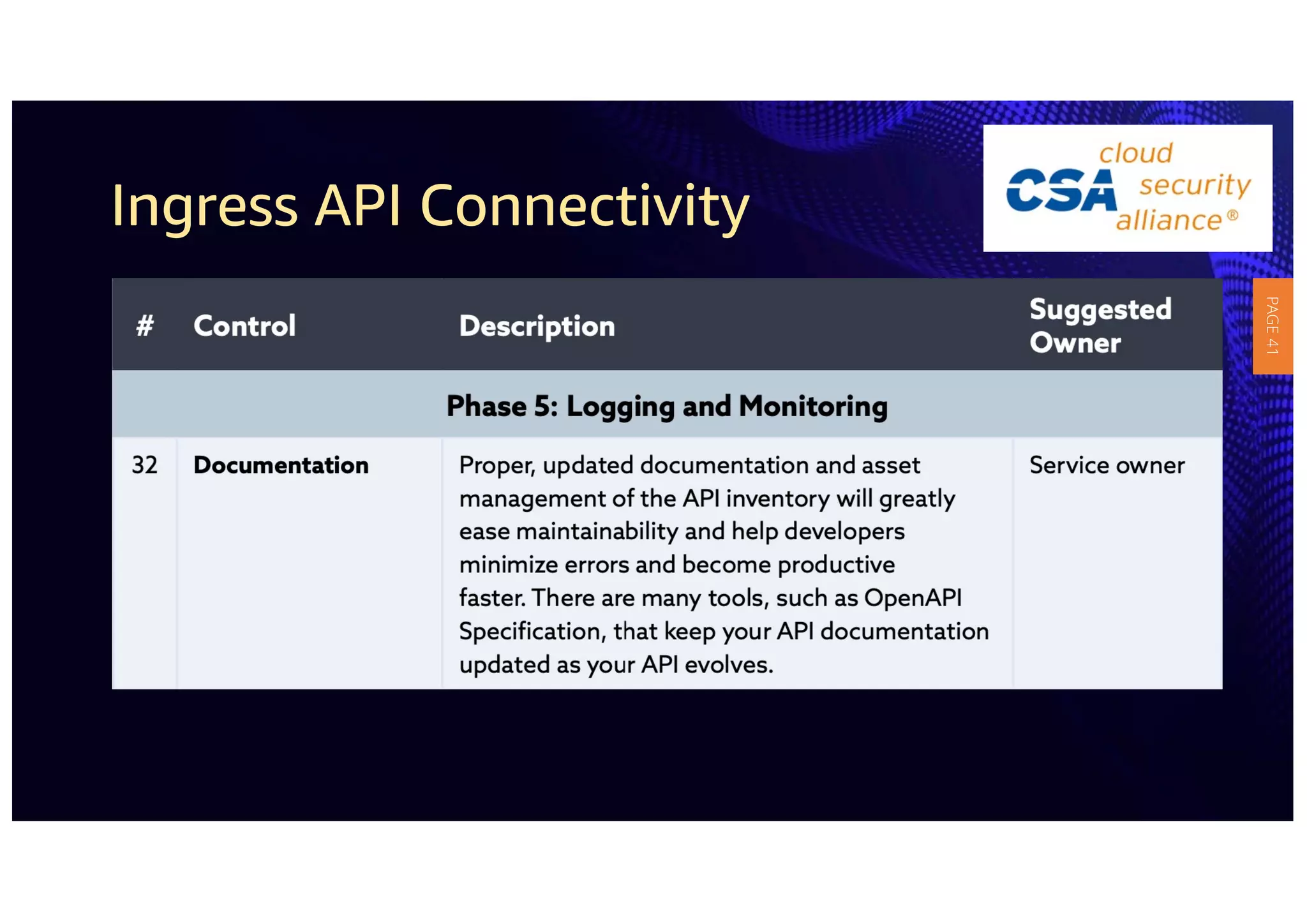
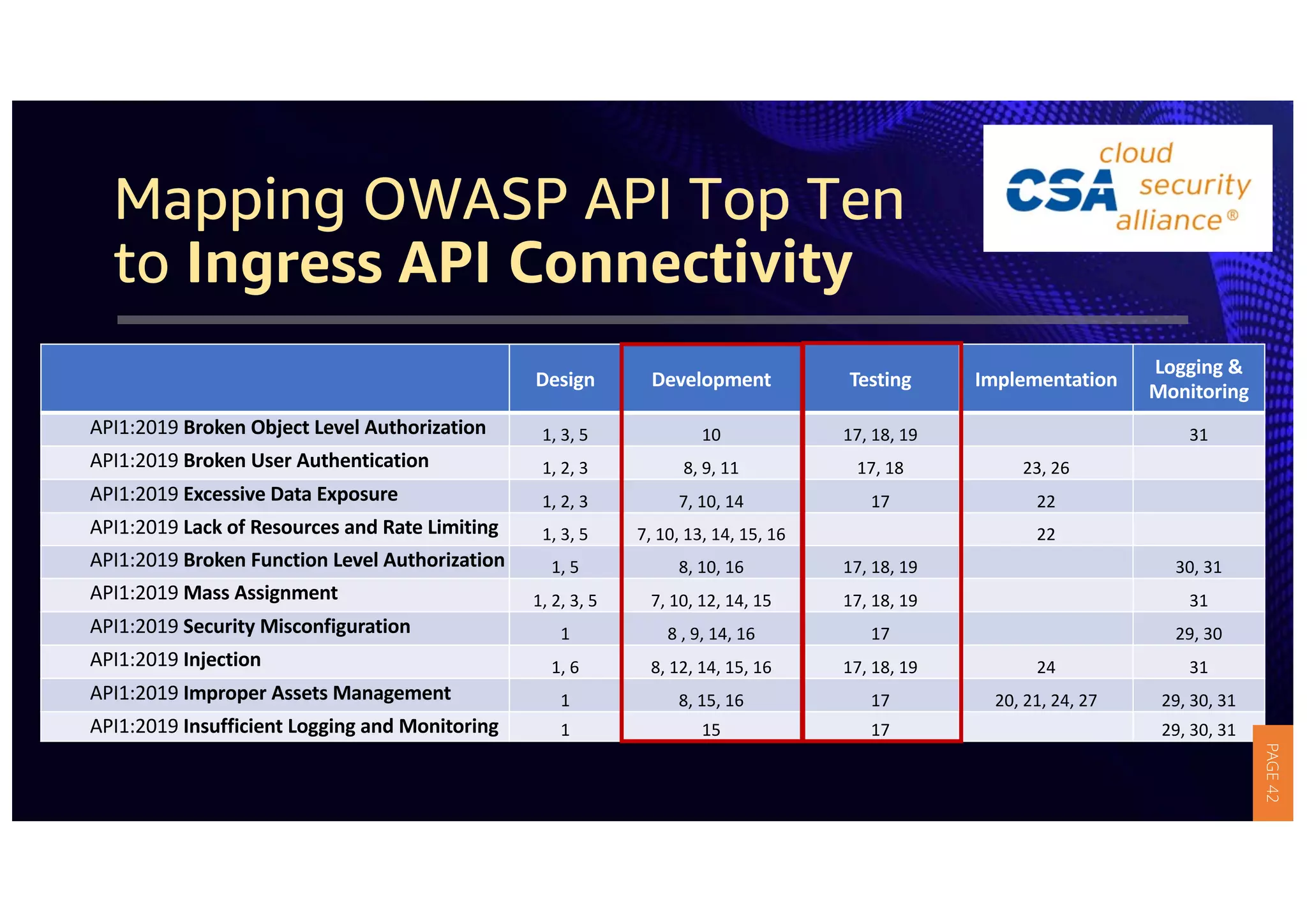
2) The guidelines include five phases for ingress API connectivity: design, development, testing, implementation, and logging/monitoring. Each OWASP API security risk is mapped to elements within these phases.
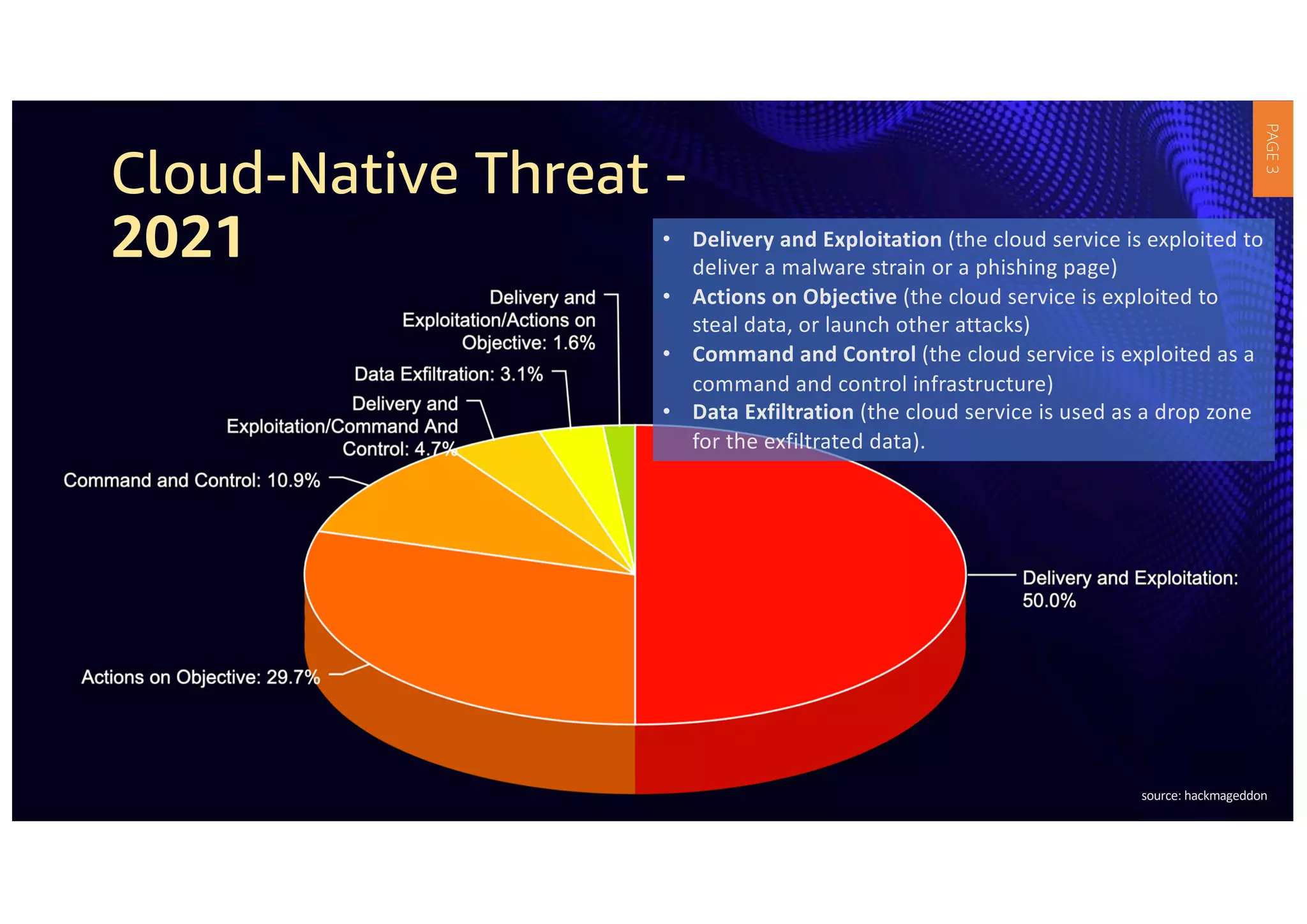
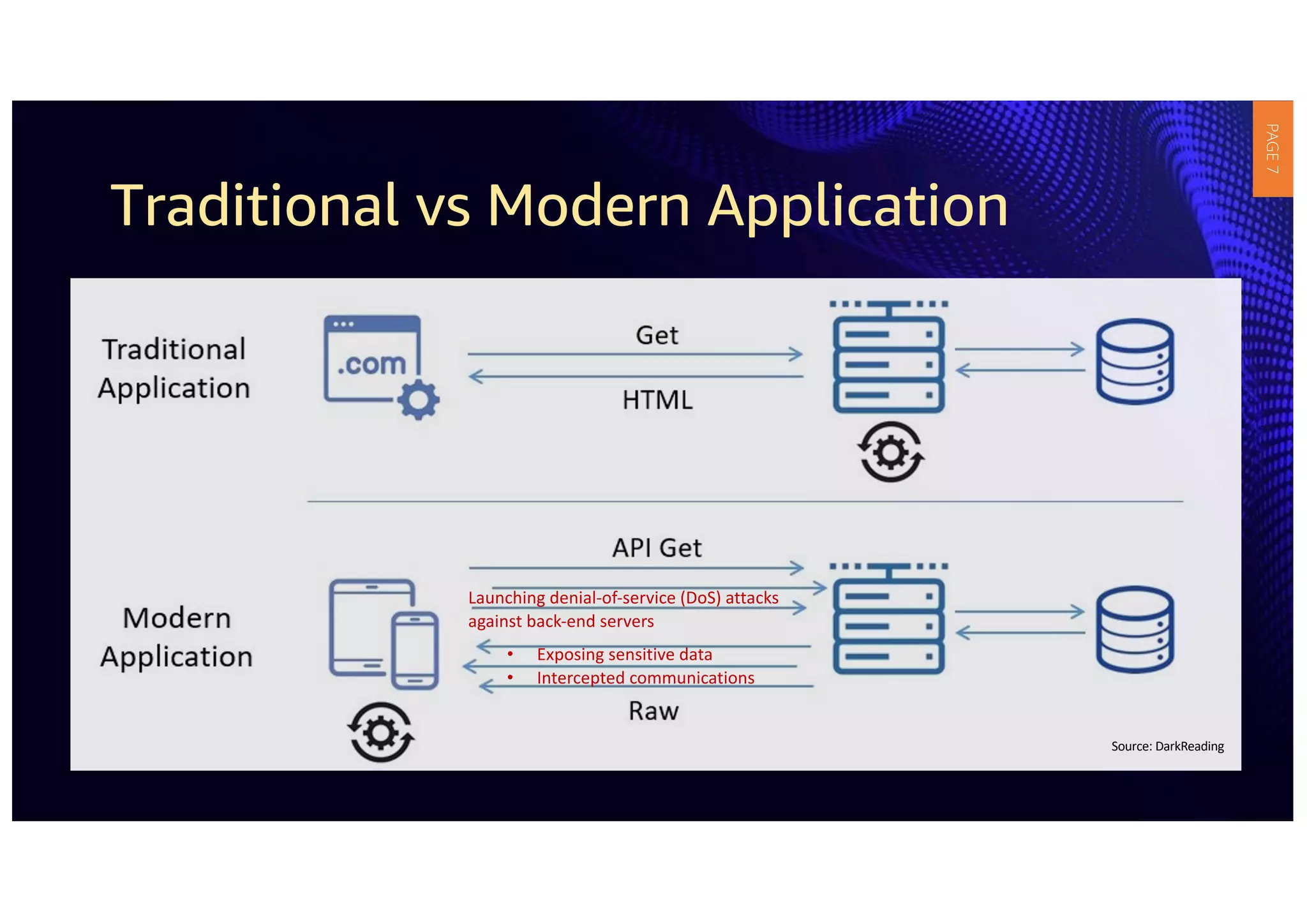
3) APIs have become critical to modern applications, but many organizations' security measures have not kept up with requirements. Robust API security policies that span the entire development lifecycle are needed to securely provide and consume services.