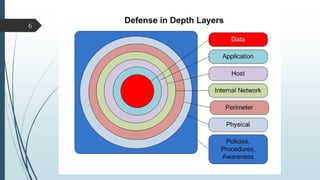
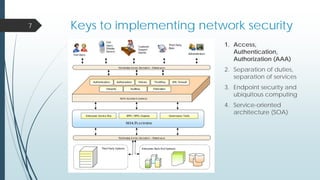
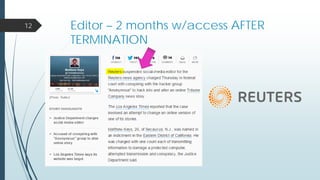
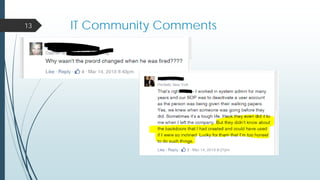
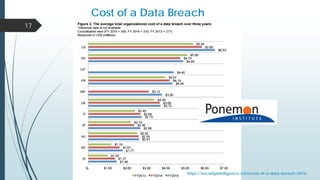
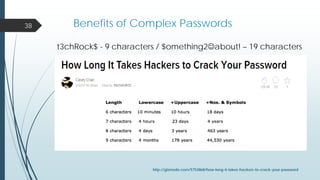
This document provides an overview of a presentation on cyber security user access pitfalls. It discusses why user access is an important topic, highlighting that insider threats can pose a big risk. It also covers IT security standards, the high costs of data breaches, principles of least privilege access and problems with passwords. Specific examples of data breaches at Cox Communications and Sony Pictures are also summarized, highlighting lessons learned about securing systems and user access.