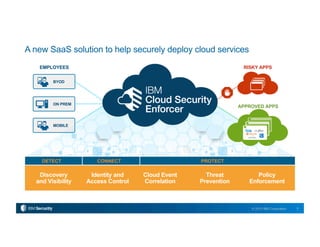
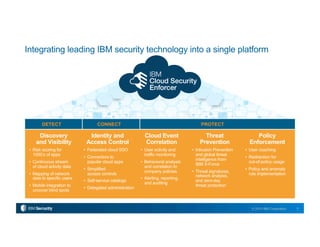
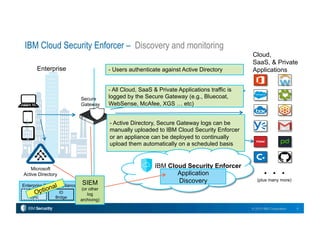
This document describes IBM's Cloud Security Enforcer, a new SaaS solution that integrates identity and access control, threat prevention, policy enforcement, and discovery/visibility capabilities into a single platform. It consolidates leading IBM security technologies to help organizations securely adopt cloud services. Key features include risk scoring for thousands of apps, continuous monitoring of cloud activity, mapping network data to users, mobile integration, single sign-on, connectors to popular apps, access controls, activity monitoring, behavioral analysis, alerting/reporting, intrusion prevention, and threat protection from IBM X-Force. The solution aims to help customers securely deploy cloud services for their employees.

![5© 2015 IBM Corporation
IBM Cloud Security Enforcer – World Wide Mobile Cloud Proxy
Home WiFi /
Cellular Data
Network
Cloud,
SaaS, & Private
Applications
. . .(plus many more)
- Users use mobile device at the office and out of
the office via their home WiFi or cellular data
networks.
- This creates a ‘mobile blind spot’ for most
corporations.
- Without a secure gateway or IPS there is a risk of
malware being downloaded or other threats.
- Leveraging the built-in mobile VPN clients we will
direct traffic to our WW deployments of Cloud
Proxies to inspect, monitor, and provide controls on
the traffic.
IBM Cloud Security Enforcer
World Wide Mobile Cloud Proxy
Client Gateway
[VPN]
Intrusion Prevention
System](https://image.slidesharecdn.com/10-7-15arecloudappstheinvisibleman-151008145929-lva1-app6892/85/Are-Cloud-Apps-the-Invisible-Man-5-320.jpg)

![7© 2015 IBM Corporation
IBM Cloud Security Enforcer – Single Sign-On & Launchpad
Microsoft
Active Directory
Enterprise
Cloud,
SaaS, & Private
Applications
Secure
Gateway
. . .(plus many more)
- SSO from either the Enterprise Bridge Identity
Bridge component or via a federation product
(TFIM, ADFS or Ping)
- User arrives at launch pad and can single click on
an entitled application or browser application
catalog
Enterprise Bridge Appliance
Log
Collection
ID
Bridge
Directory
Sync
IBM Cloud Security Enforcer
Launchpad &
Catalog
SSO
[Service
Provider]
SSO
[Identity
Provider]
FIM
(or
federation
product)
Optional](https://image.slidesharecdn.com/10-7-15arecloudappstheinvisibleman-151008145929-lva1-app6892/85/Are-Cloud-Apps-the-Invisible-Man-7-320.jpg)
