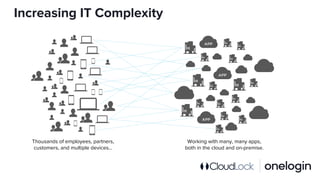
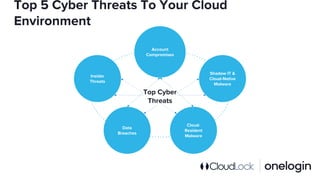
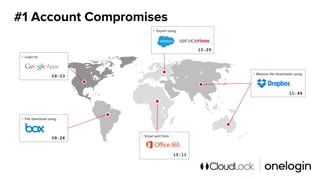
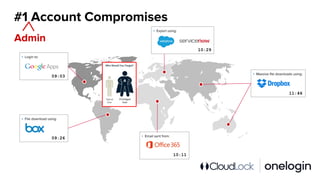
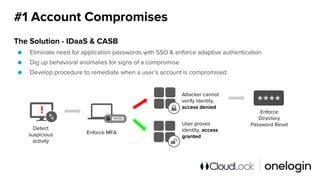
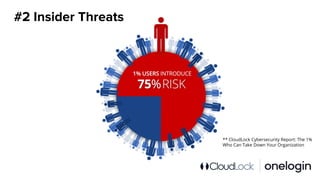
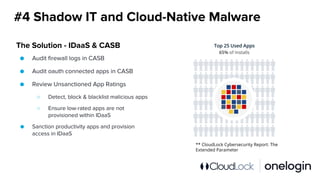
The document outlines the complexity of IT security in organizations and identifies the top five cyber threats to cloud environments, including account compromises, insider threats, cloud-resident malware, shadow IT, and data breaches. It discusses integrated solutions using Identity as a Service (IDaaS) and Cloud Access Security Broker (CASB) to mitigate these threats through measures like multi-factor authentication, monitoring for unauthorized activities, and proper access control. The document emphasizes the importance of proactive measures and coordination among IT stakeholders to secure sensitive data and applications.