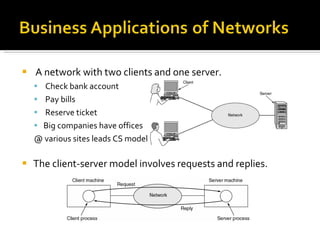
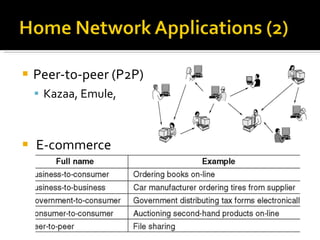
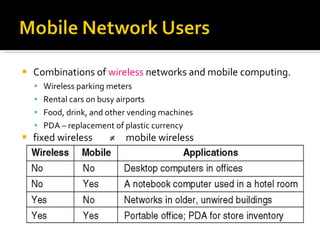
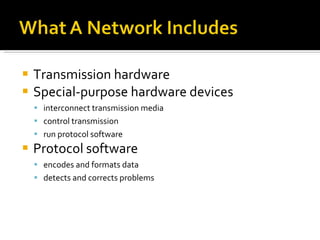
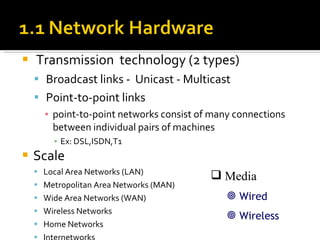
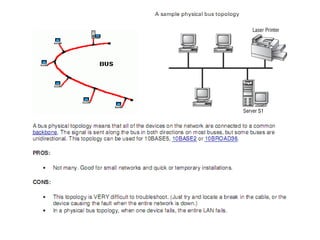
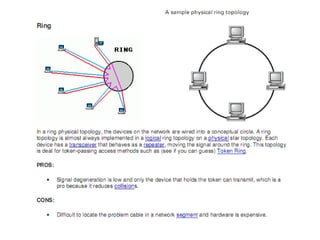
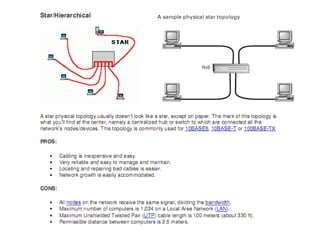
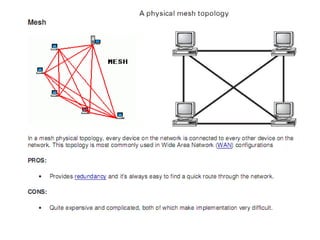
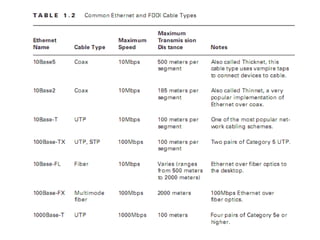
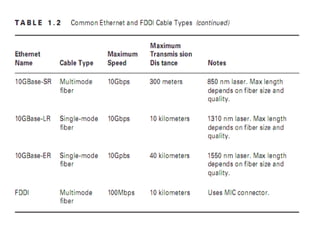
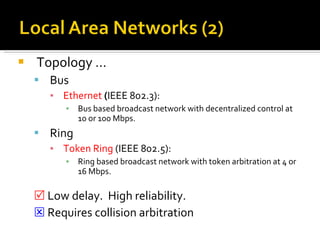
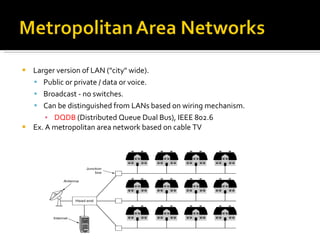
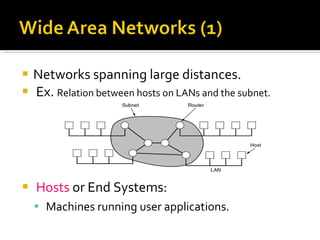
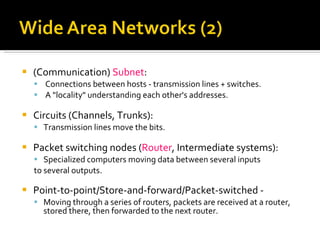
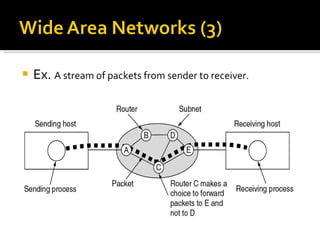
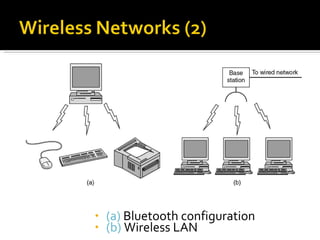
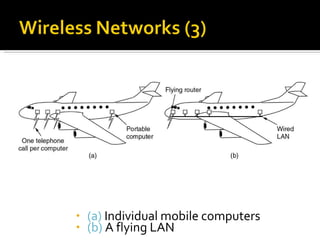
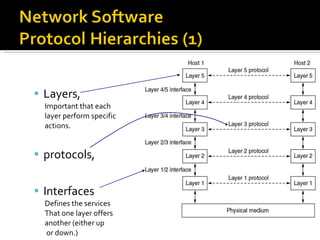
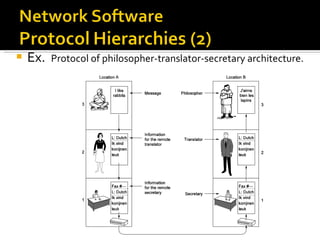
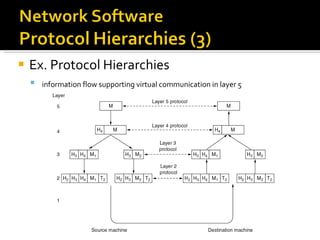
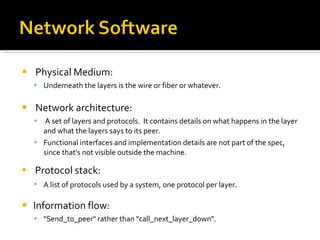
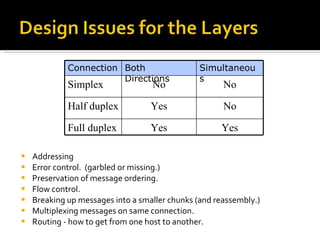
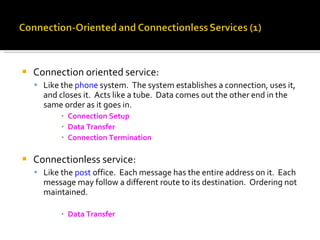
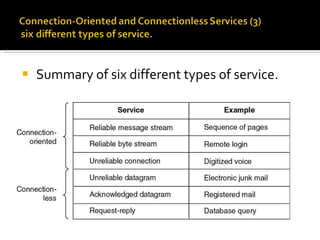
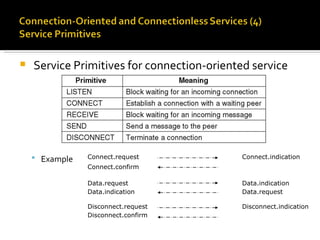
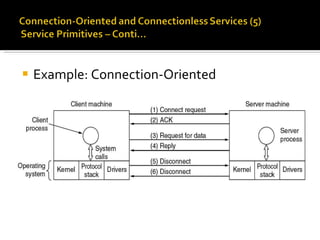
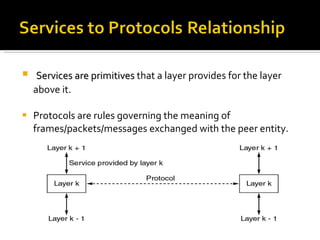
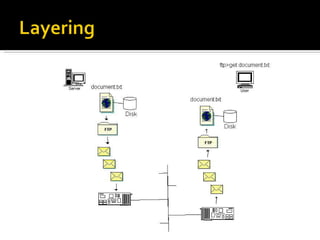
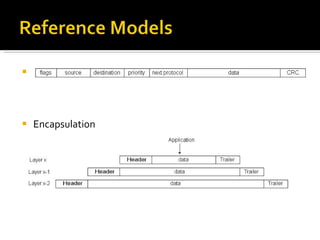
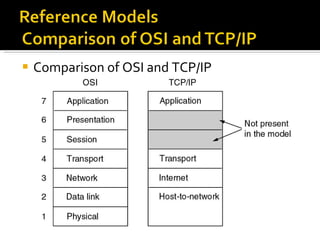
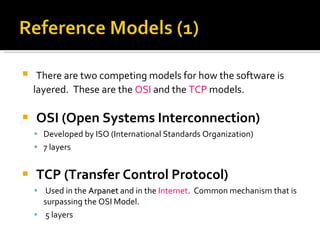
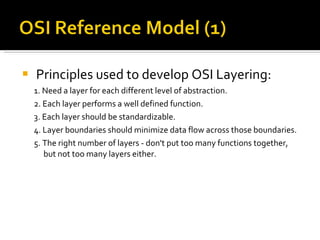
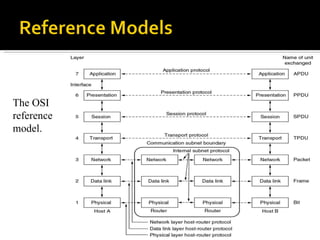
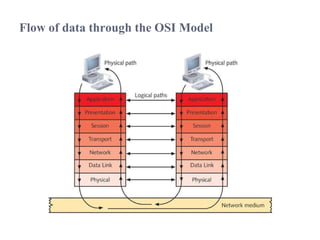
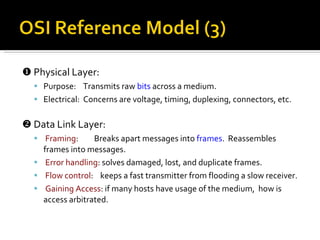
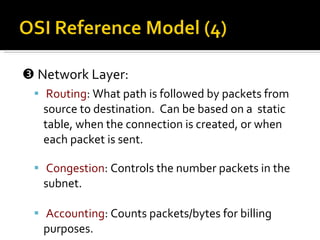
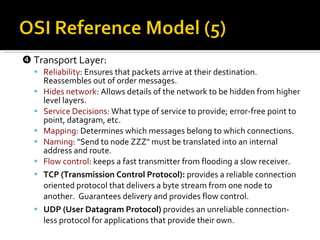
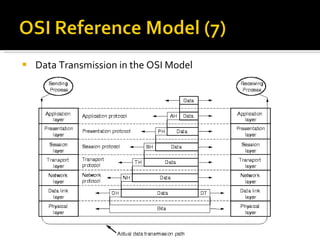
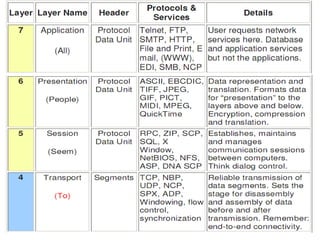
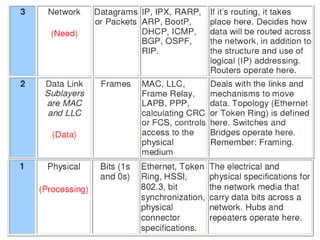
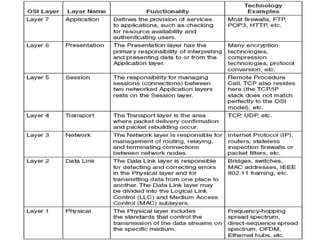
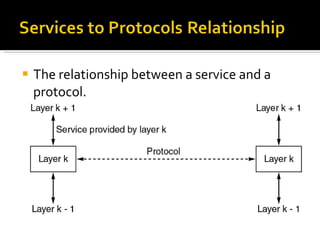
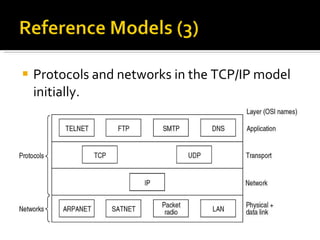
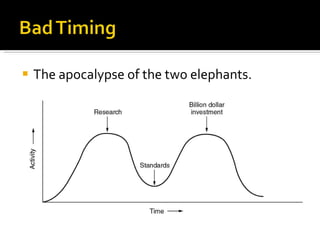
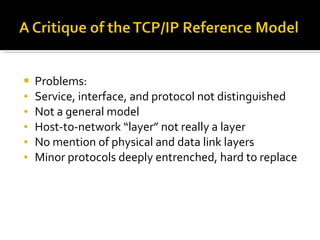
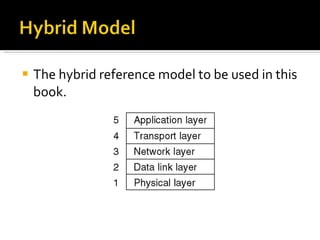
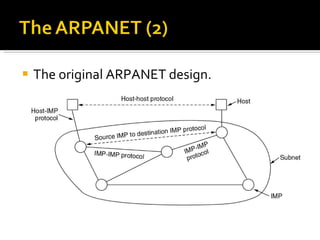
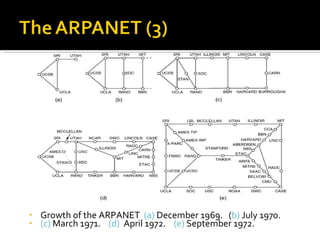
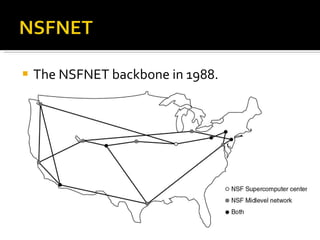
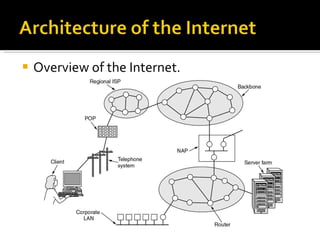
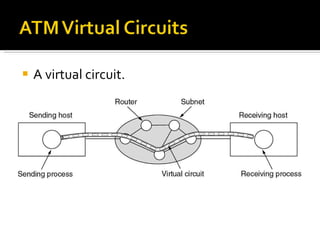
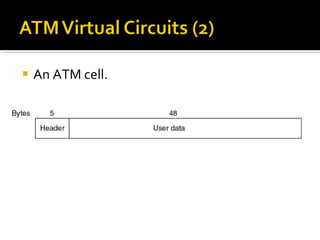
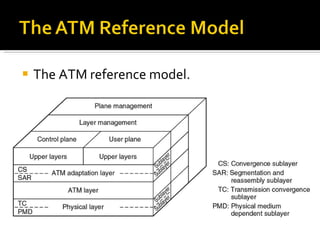
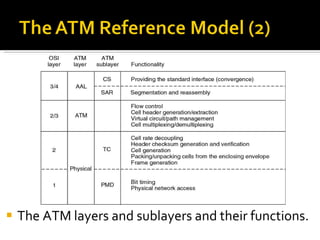
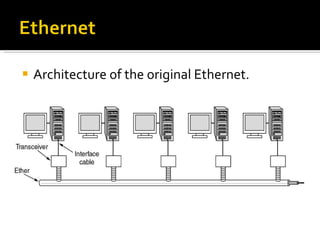
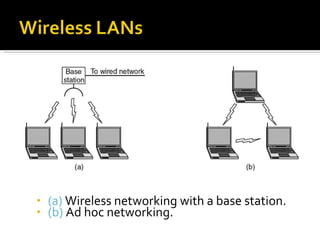
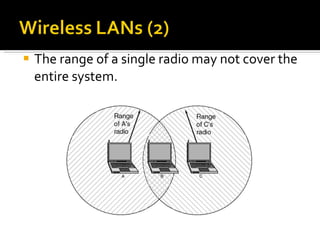
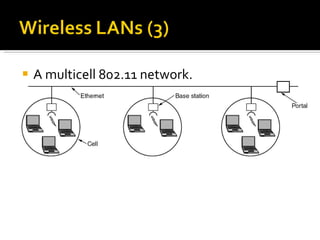
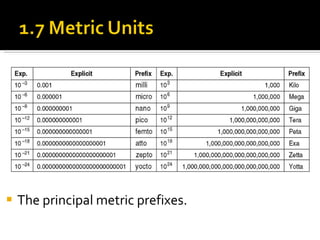
The document summarizes the key topics covered in Chapter 1 of the book "Computer Networks, Fourth Edition" by Andrew S. Tanenbaum. It discusses the seven-layer OSI reference model and the five-layer TCP/IP reference model as the two main models for organizing computer network software. It also briefly describes the different layers of each model and compares the OSI and TCP/IP models.