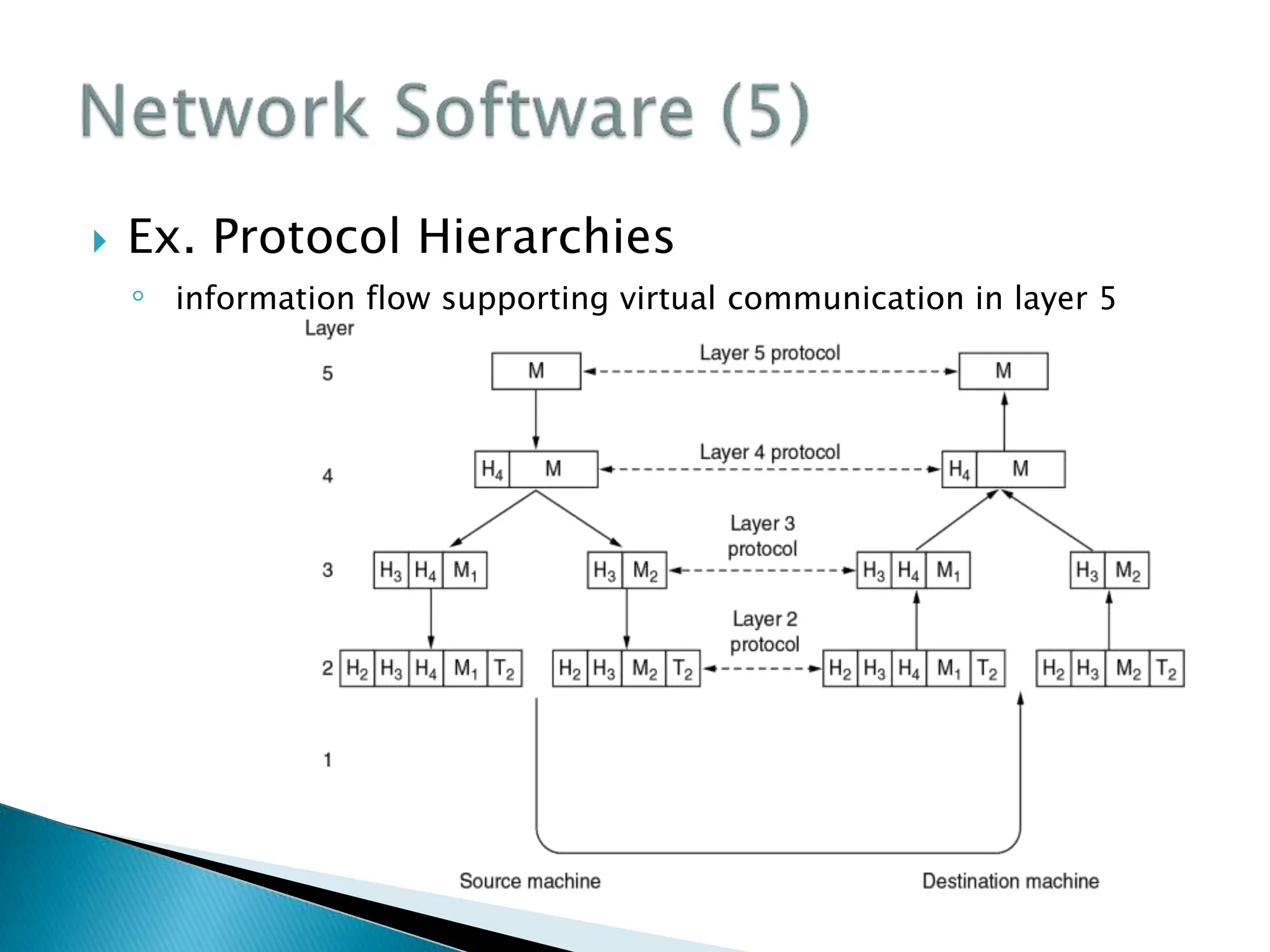
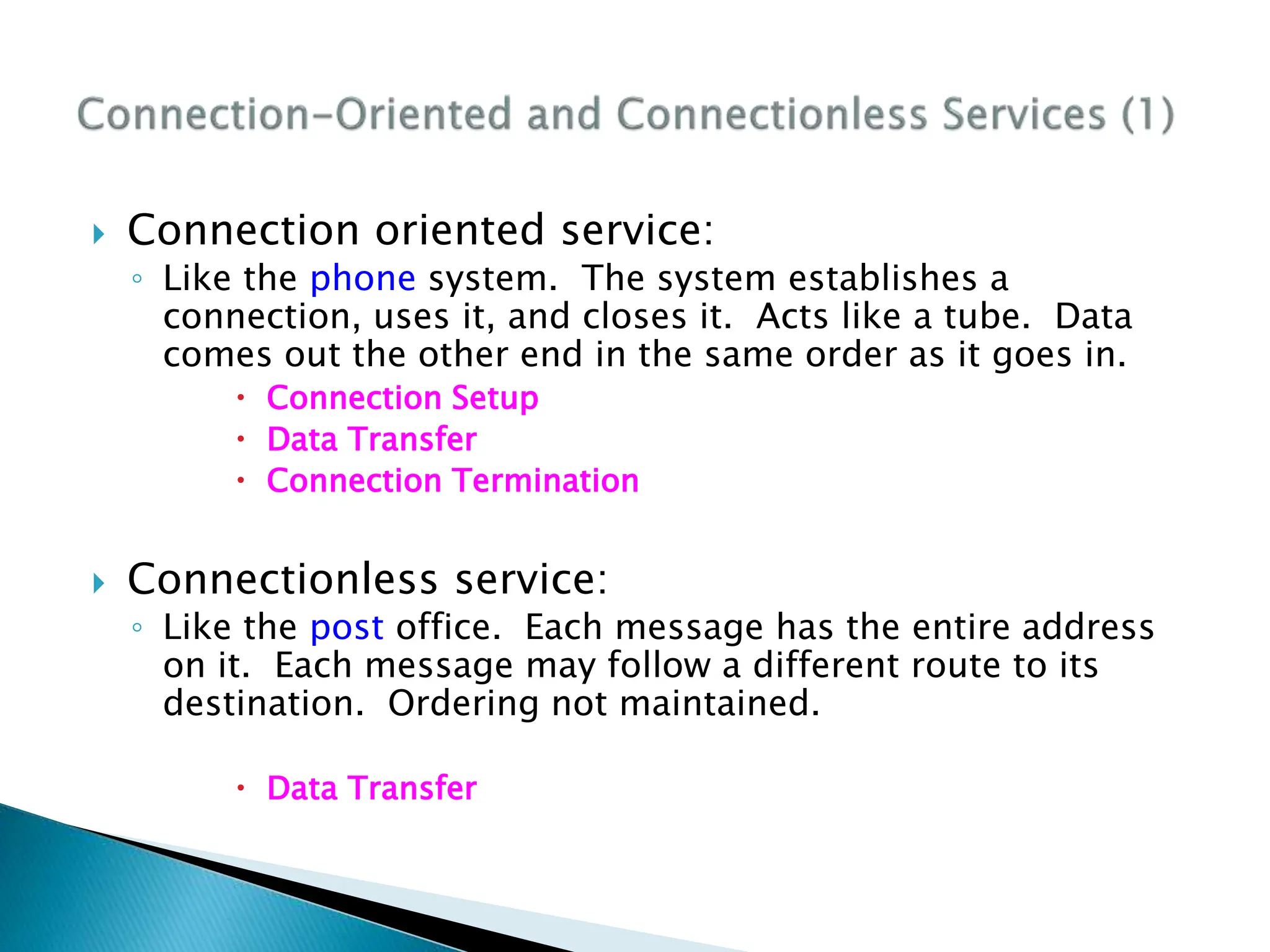
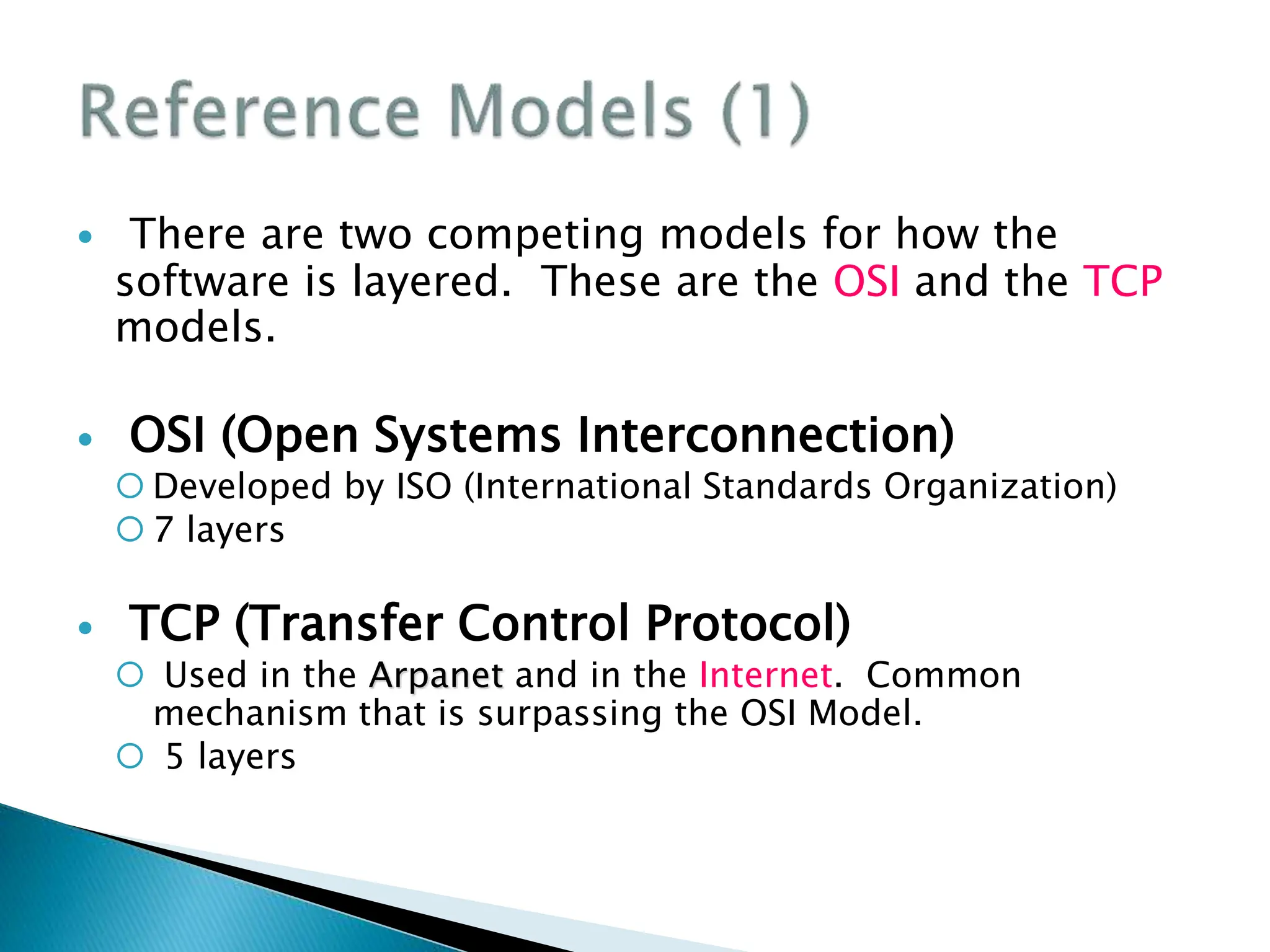
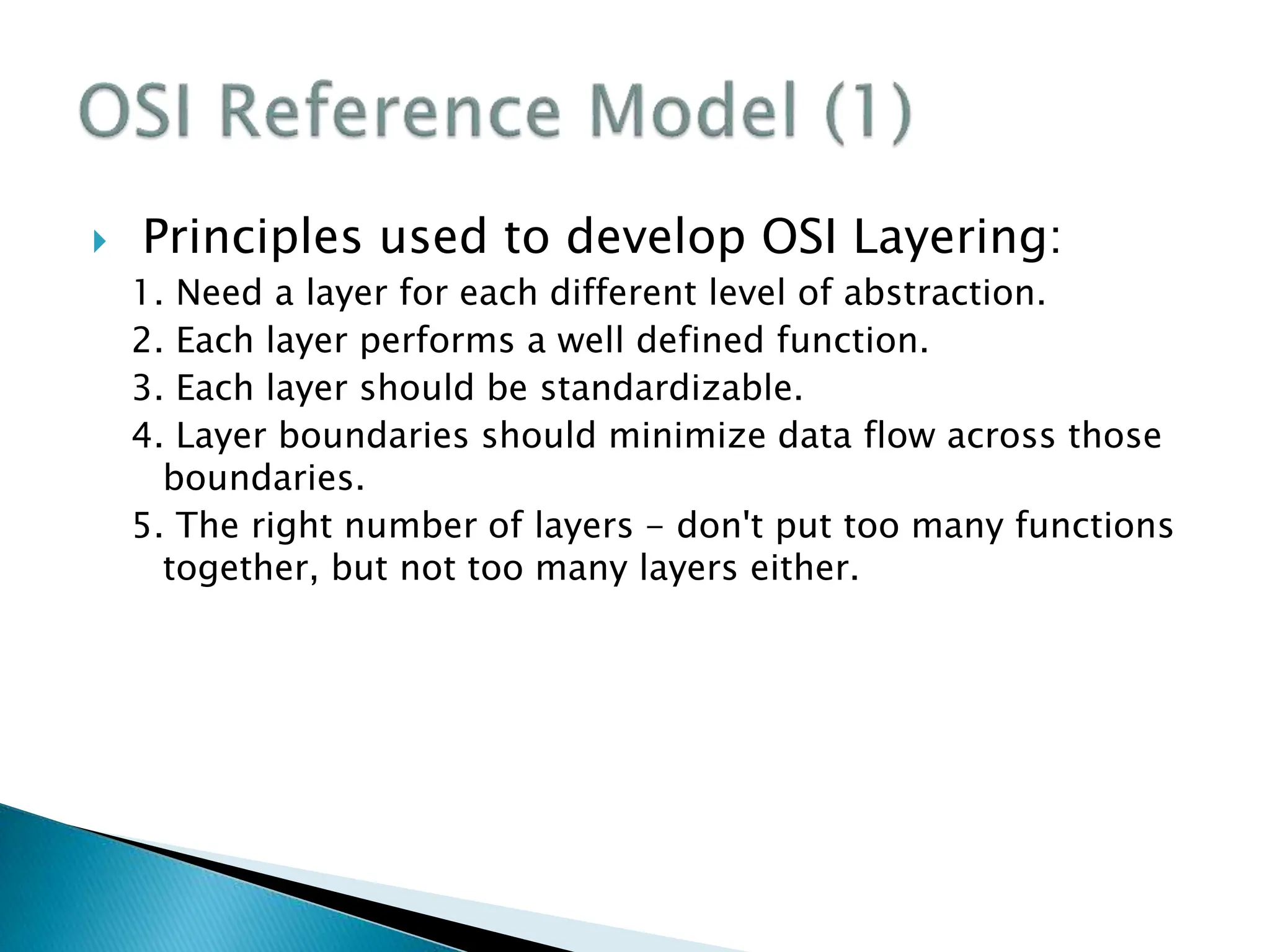
The document provides an overview of computer networking concepts including recommended textbooks, basics of networking terminology and principles, network hardware, protocols and layering, network addressing, and applications of computer networks. It discusses key topics like transmission technologies, local and wide area networks, wireless networks, protocol hierarchies, network services, and the OSI and TCP network models. The goal is to teach students the fundamentals of how networks work rather than specific configuration skills.

![Text book
Andrew Tanenbaum, “Computer Networks, 3rd Edition”,
1996. [4th edition is available]
◦ Recommended
James F. Kurose and Keith W. Ross, “Computer
Networking , A Top-Down Approach Featuring the
Internet”, 2001.
Stallings, William, “Data and Computer
Communications, 6th Edition”, 2000.](https://image.slidesharecdn.com/cnchapter1-231223151419-41549d5d/75/CN-chapter1-ppt-2-2048.jpg)