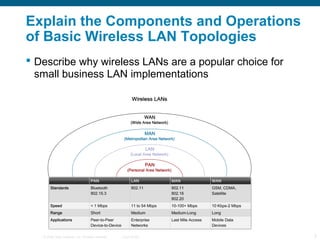
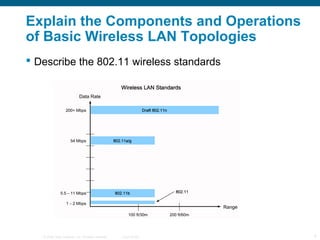
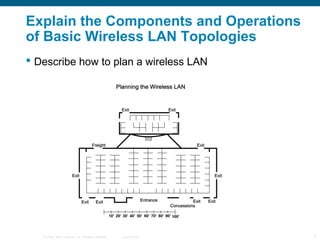
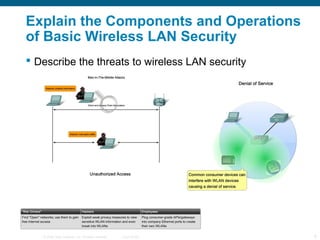
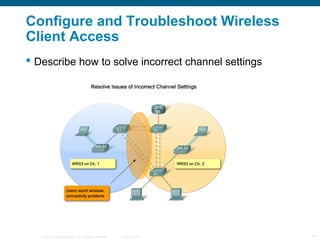
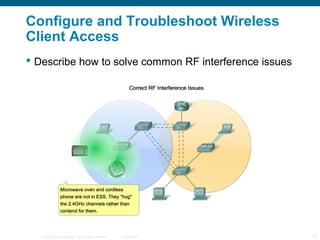
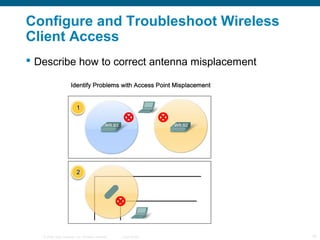
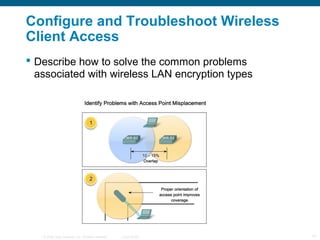
The document discusses configuring and troubleshooting wireless local area networks (WLANs). It covers wireless LAN topologies and components, security protocols and practices, and how to configure a wireless access point and network interface card. Troubleshooting techniques for wireless client access issues are also examined, including solving problems related to access point firmware, radio frequency interference, encryption settings, and authentication.