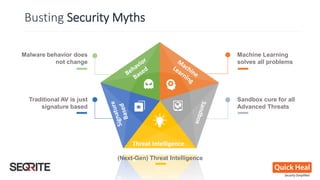
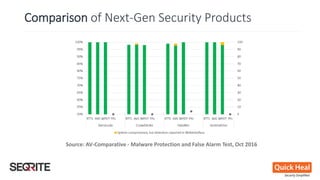
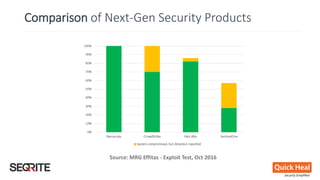
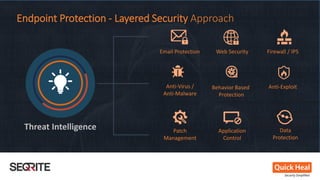
This document discusses whether antivirus (AV) software is dead or just missing in action. It begins by comparing traditional, signature-based AV to next-generation security products that use techniques like machine learning and threat intelligence. The document then debunks common myths about AV and security technologies. It analyzes results from tests of next-generation security products on services like VirusTotal. The document concludes that while no single product can stop all threats, security defenses continue to evolve beyond traditional AV through layered approaches.