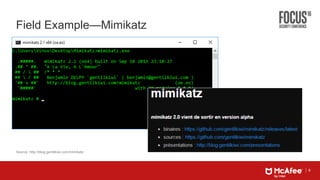
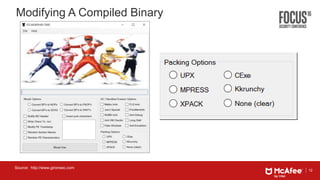
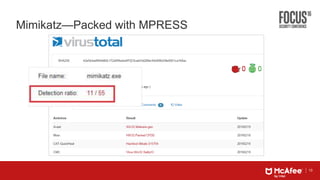
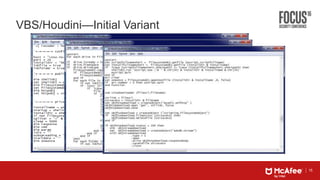
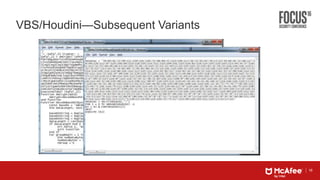
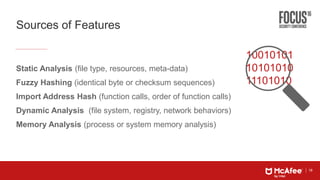
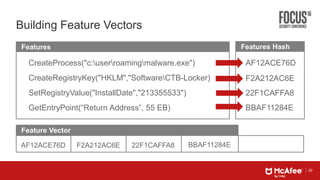
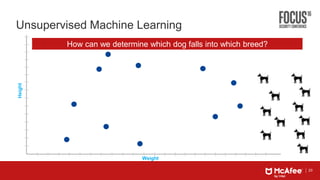
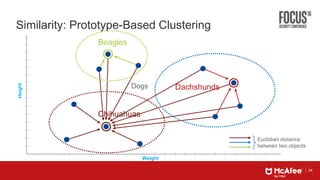
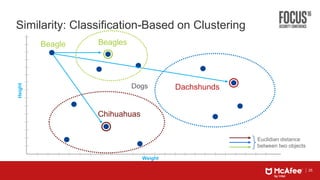
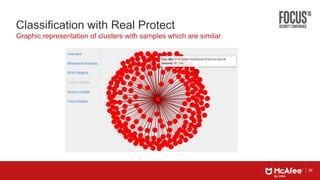
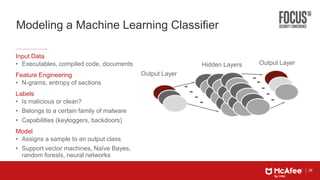
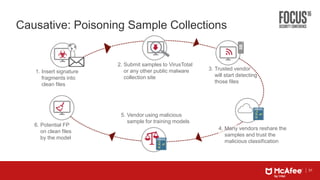
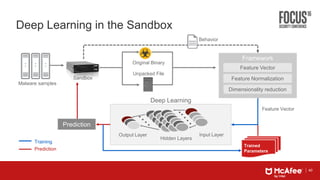
This document discusses machine learning approaches for defending against zero-day threats. It begins with an overview of the challenges of signature-based detection as malware variants increase. It then covers extracting static and behavioral features from files to build feature vectors for machine learning models. Unsupervised and classification-based clustering are examined for grouping similar objects. The document outlines attacks against machine learning defenses, such as obfuscating files to evade detection or poisoning training data. Defenses include preventing access to training data and making models resilient to poisoning. The document introduces Real Protect, a product from Intel Security that uses machine learning including deep learning in sandboxes to detect malware.