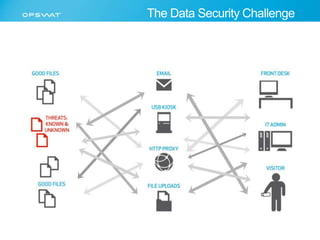
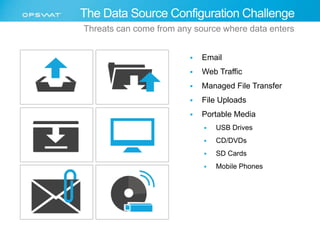
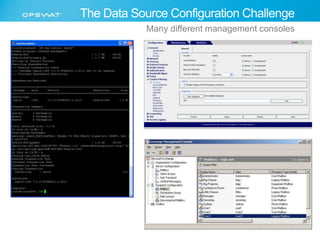
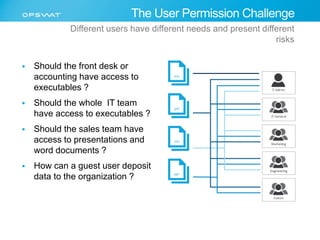
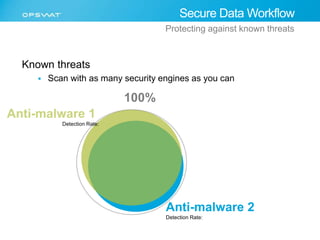
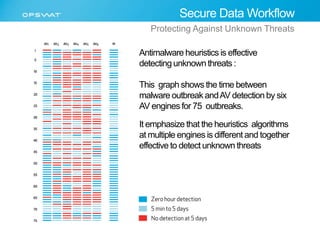
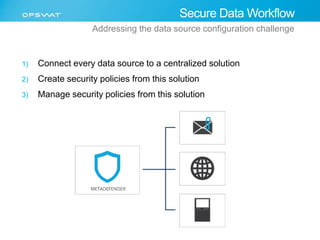
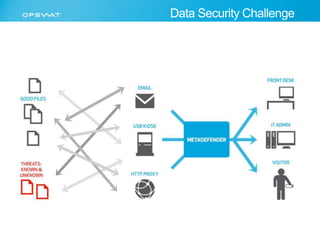
The document discusses the multifaceted challenges of data security, outlining various threats from both known and unknown sources, including keyloggers, zero-day vulnerabilities, and configuration issues. It emphasizes the importance of tailored user permission policies and securing data workflows through measures like data sanitization and the use of multiple antivirus engines. Strategies for mitigating these risks are suggested, including centralized management of data sources and comprehensive security protocols for different user groups.