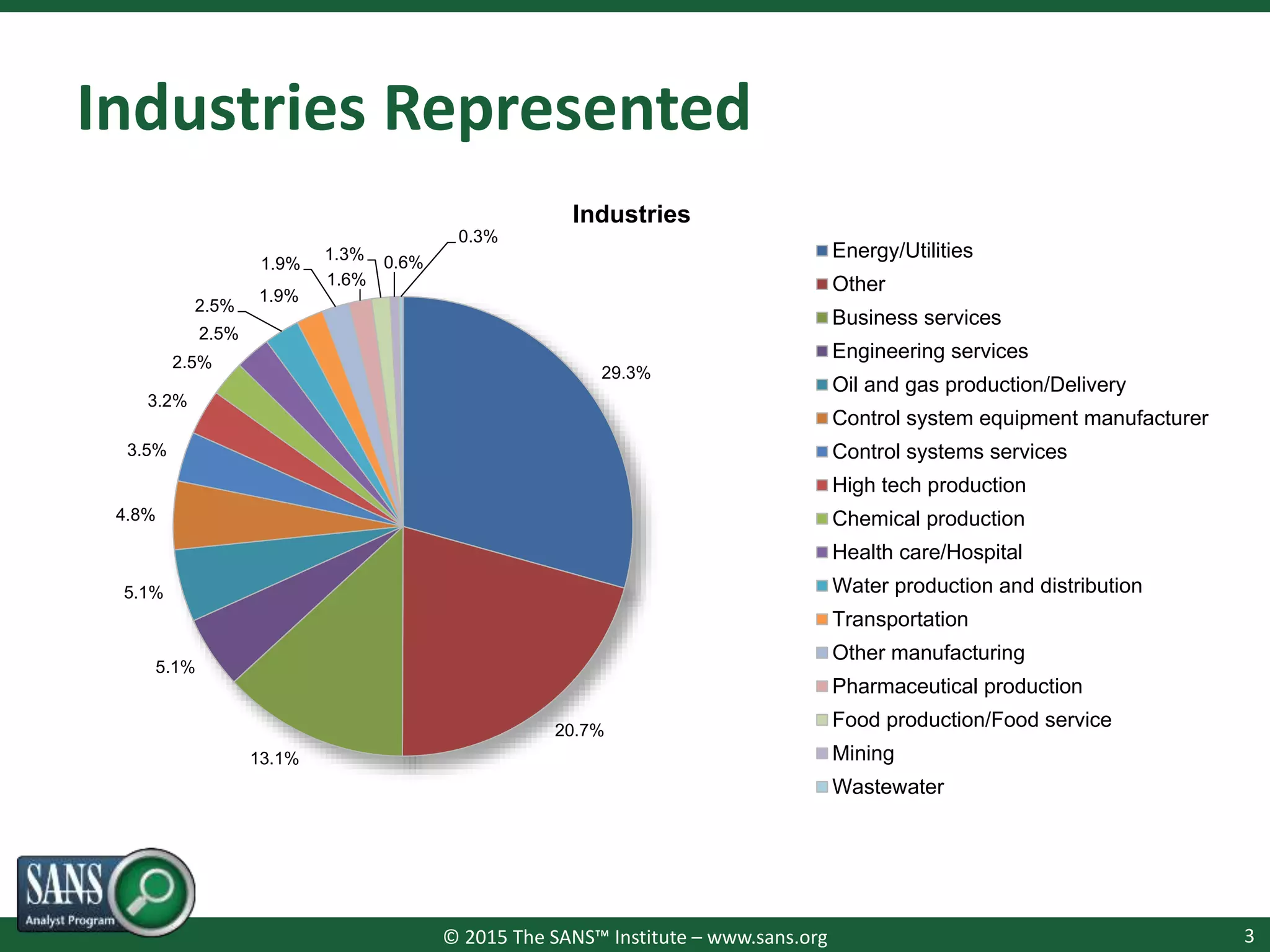
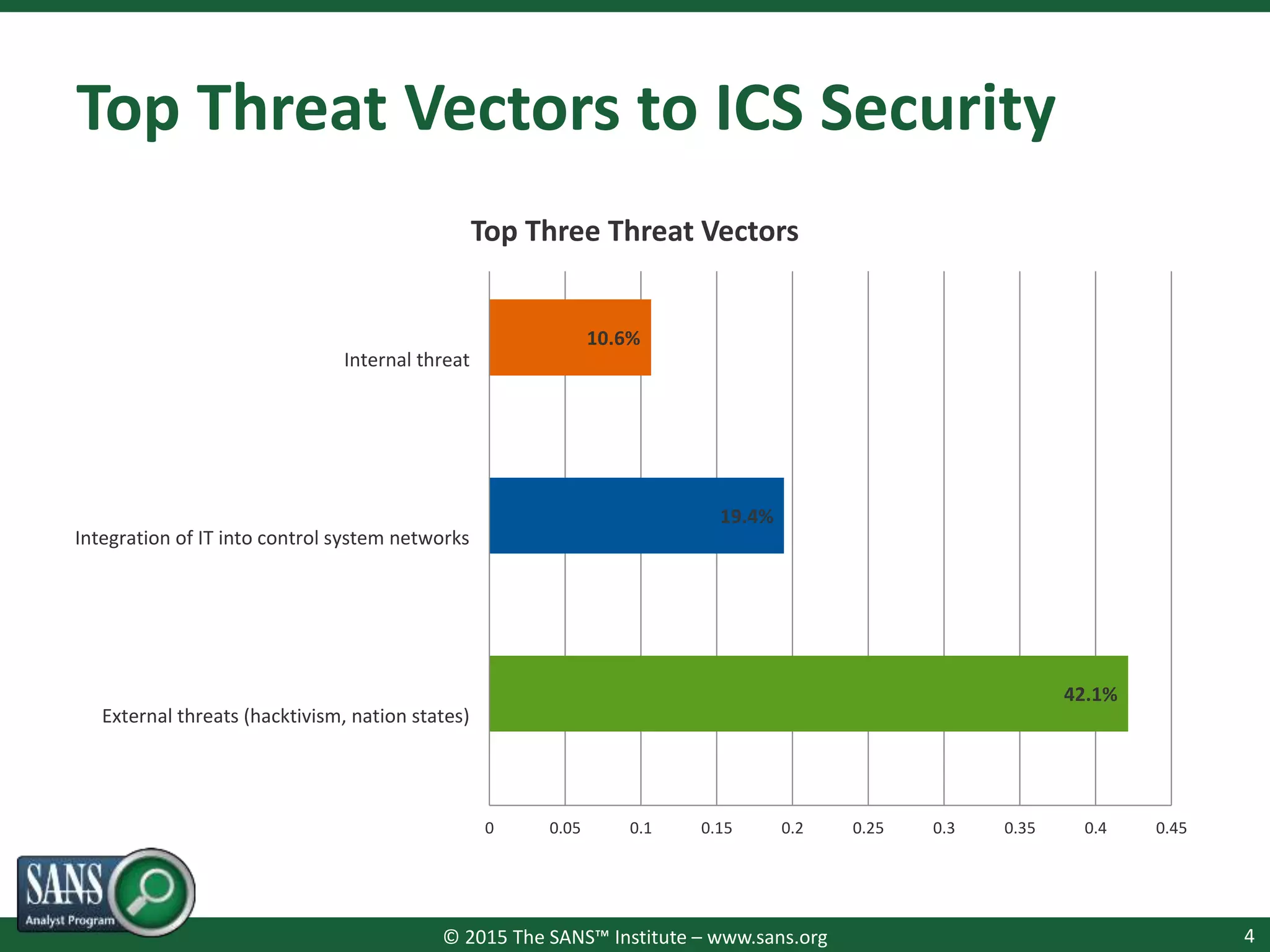
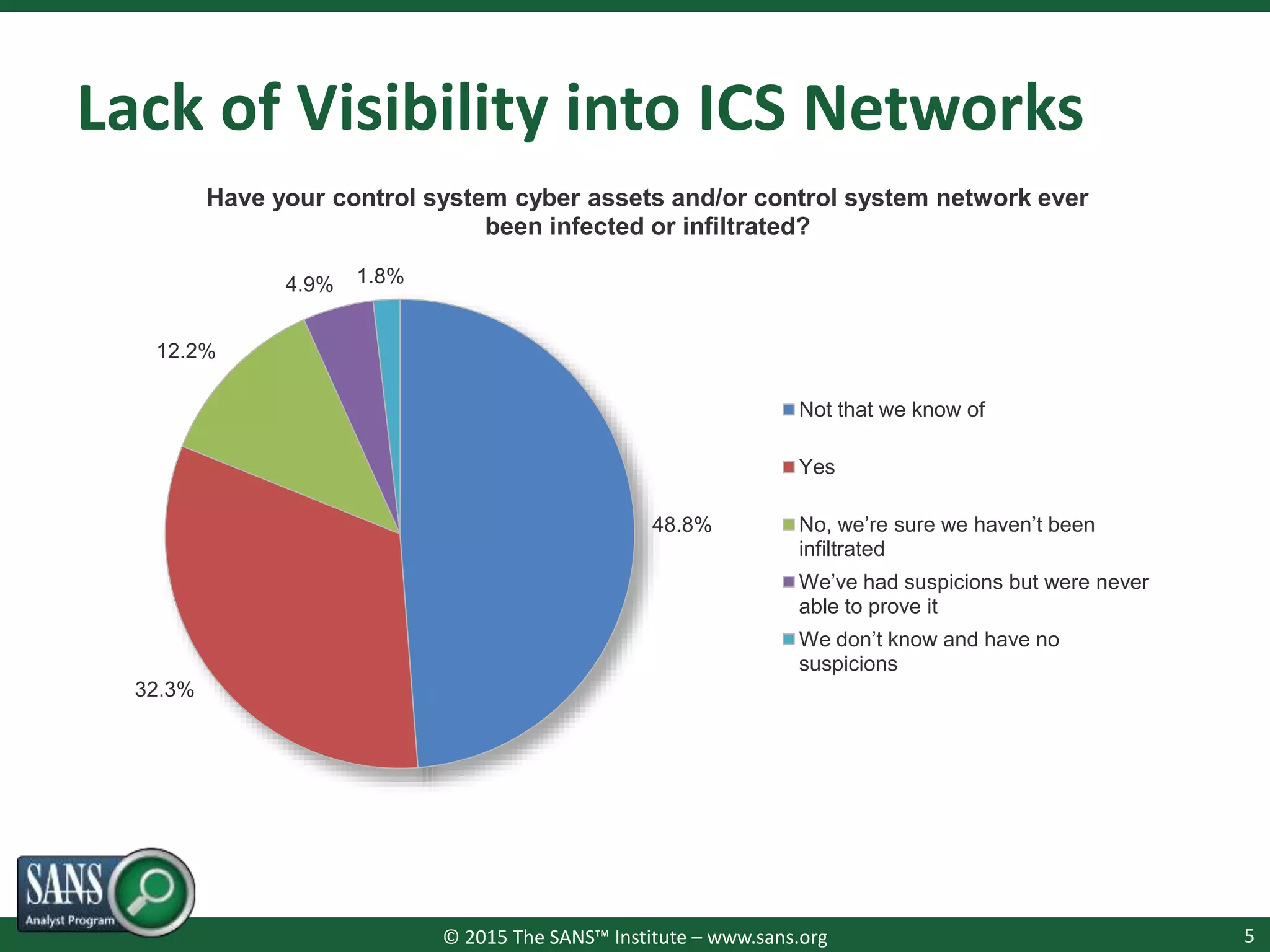
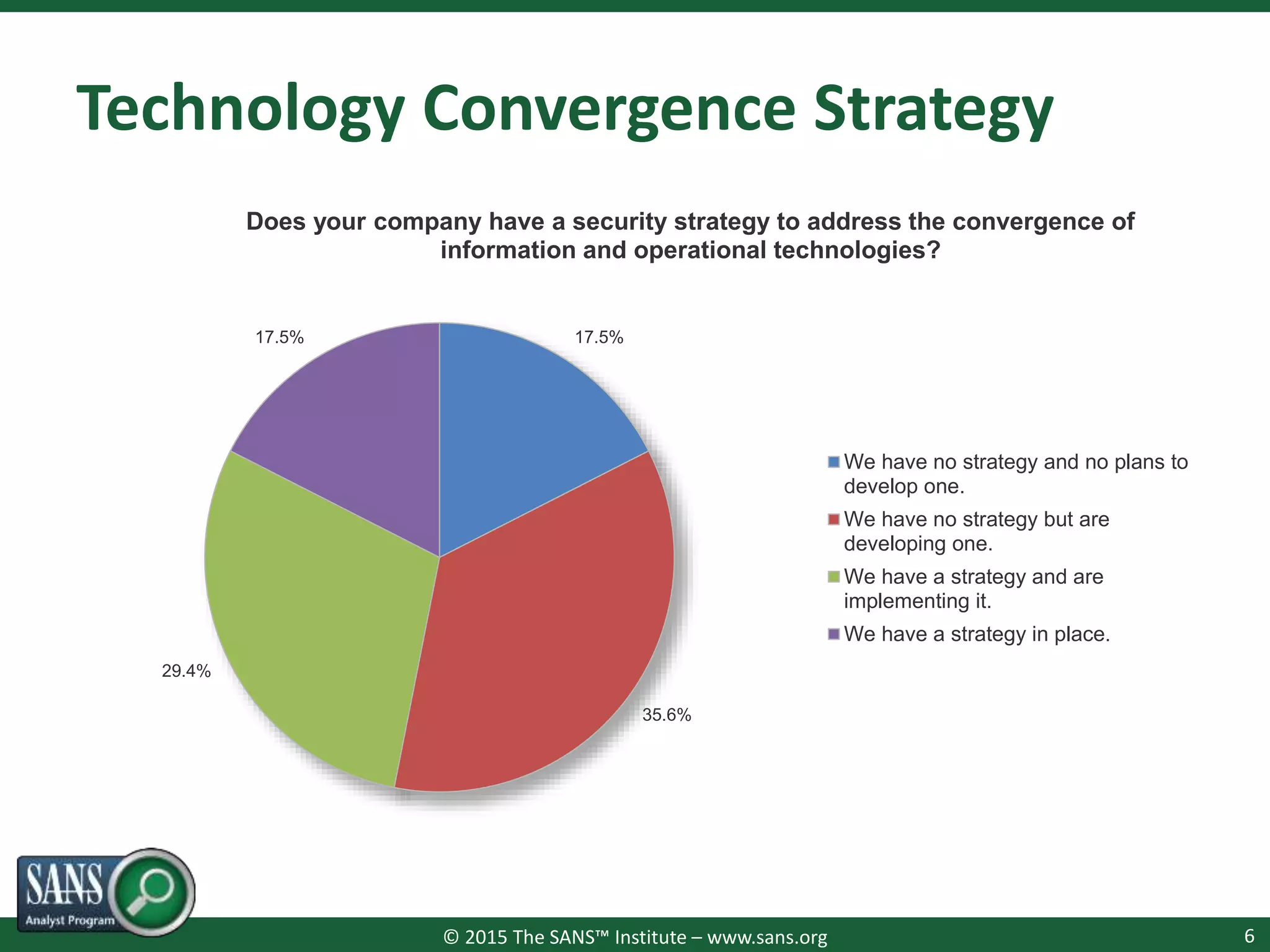
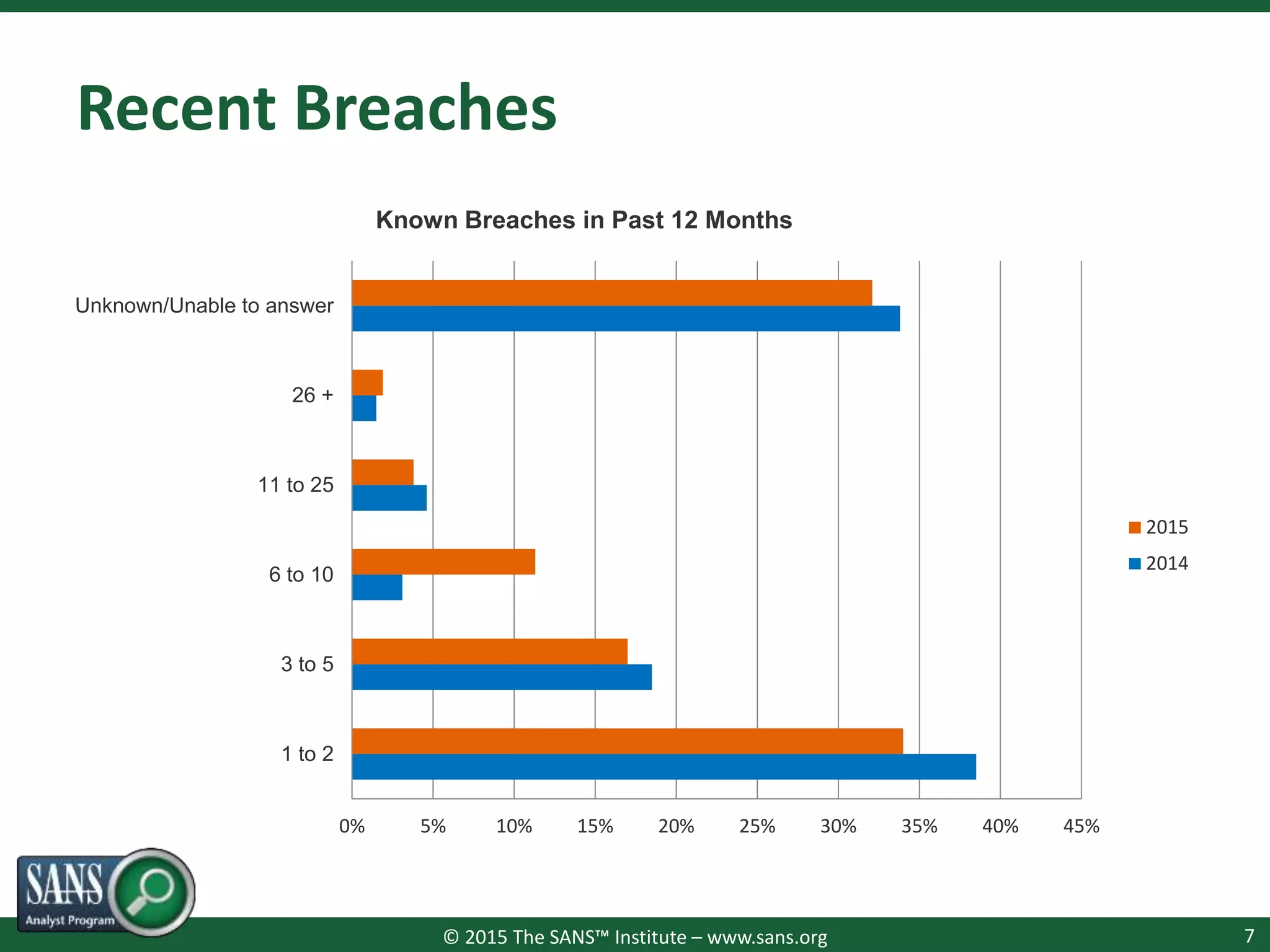
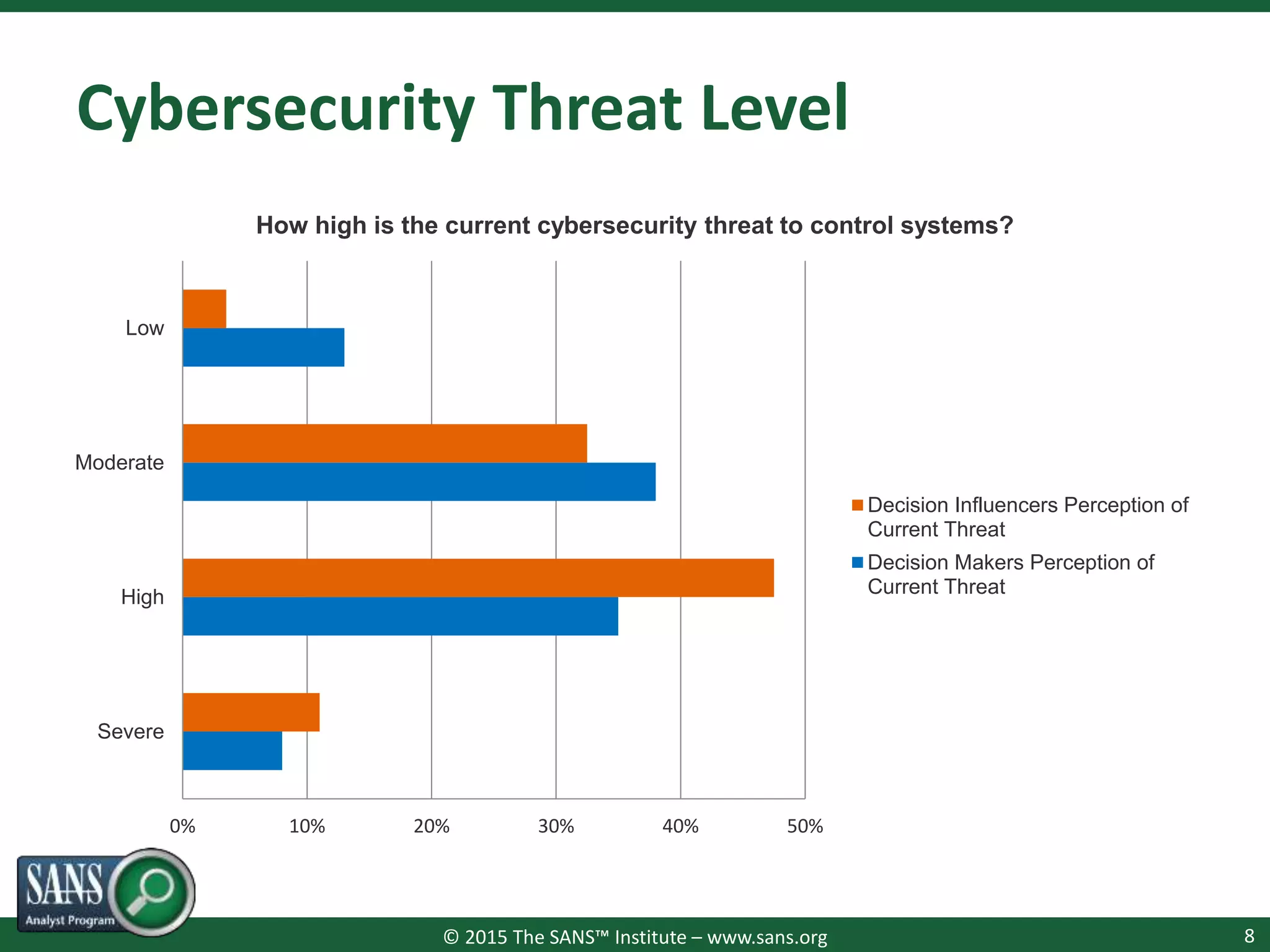
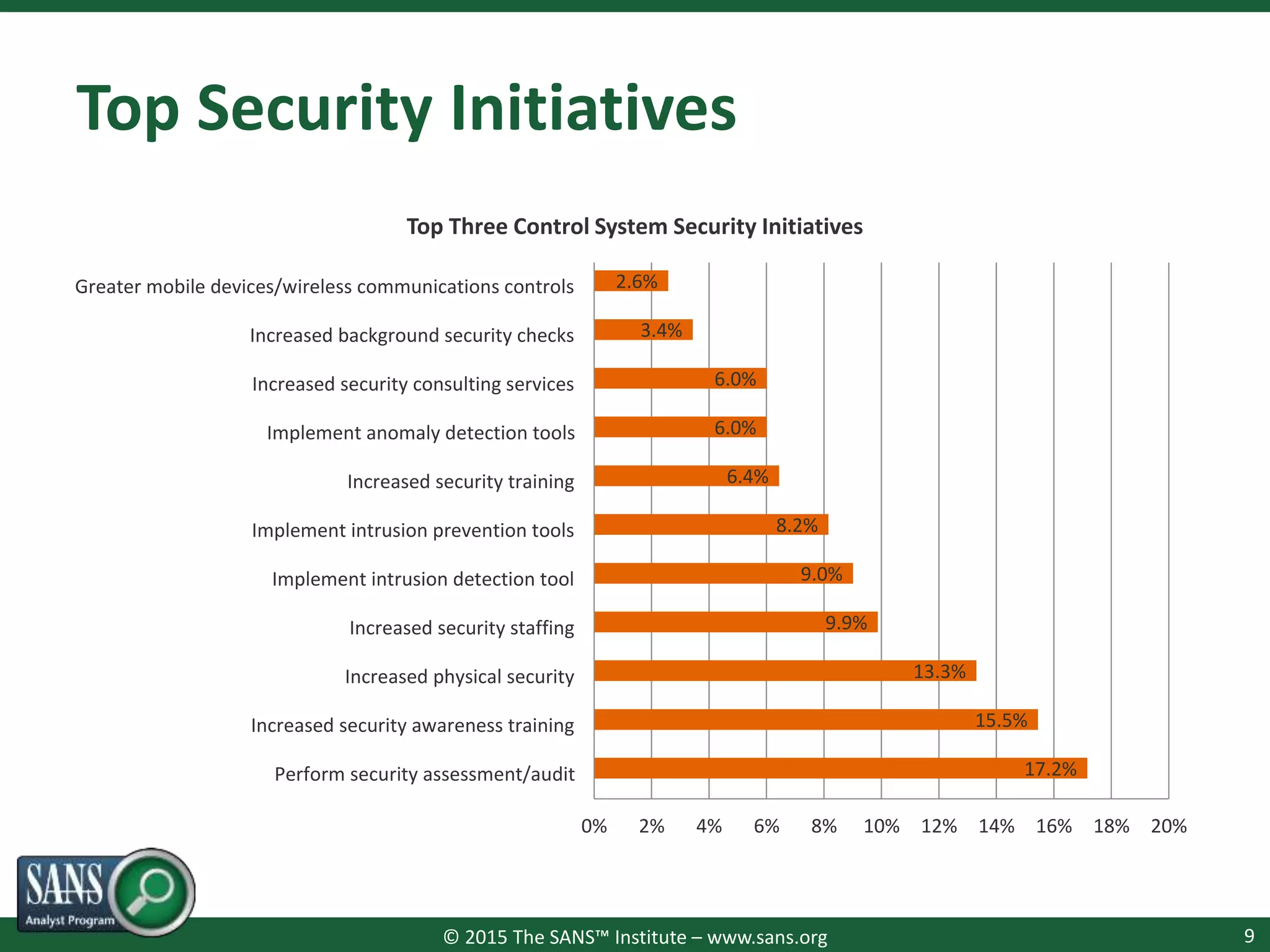
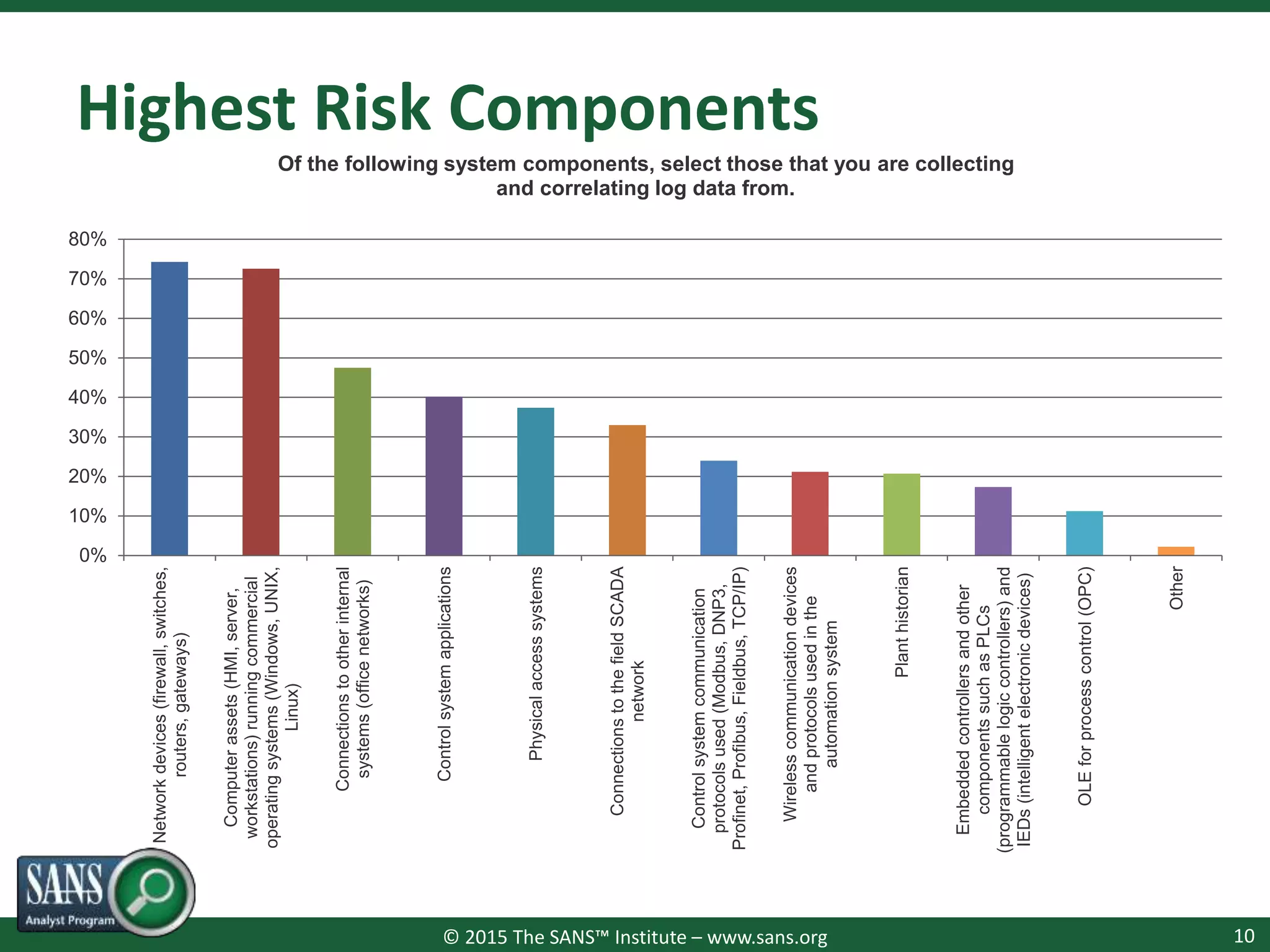
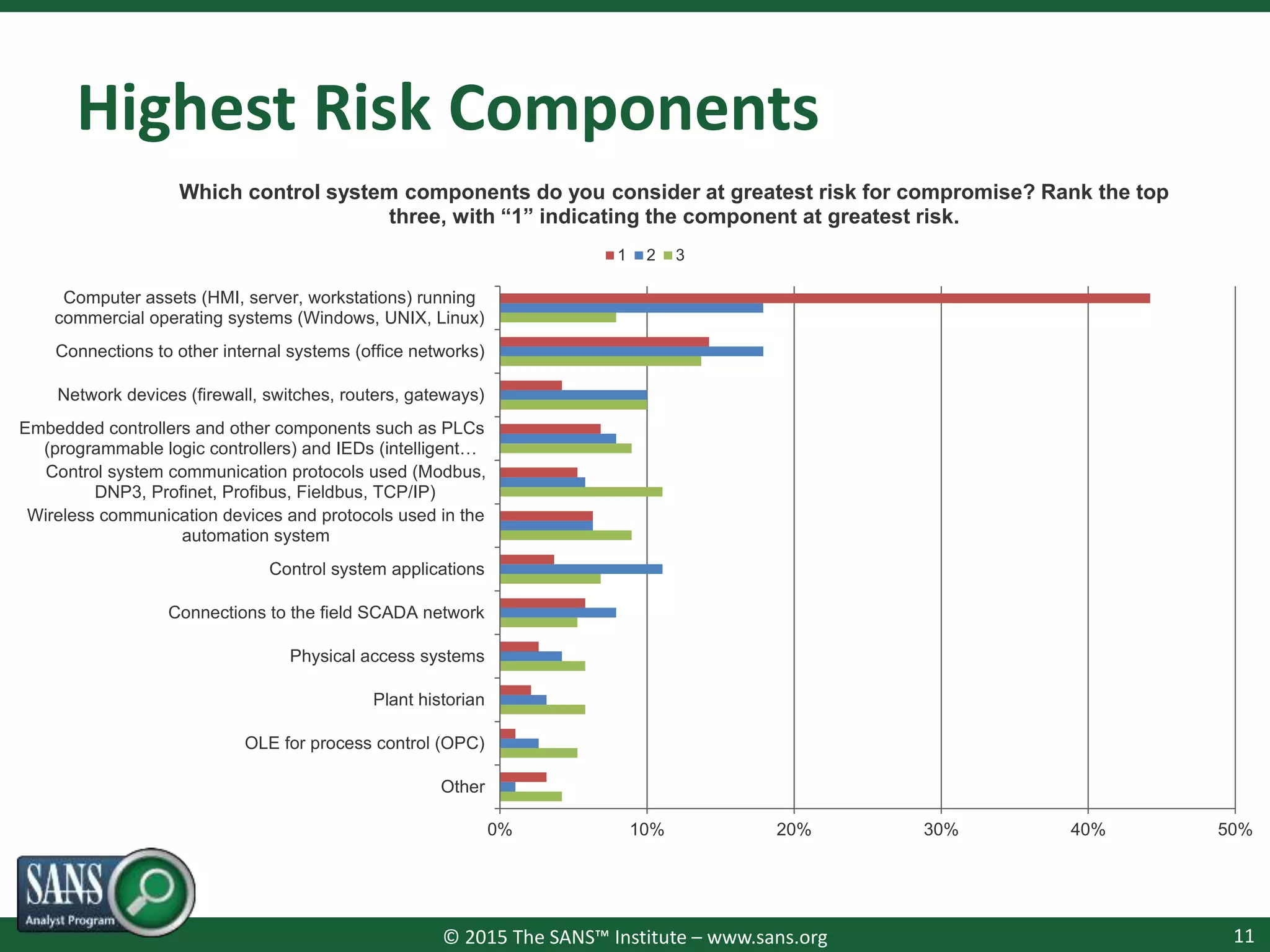
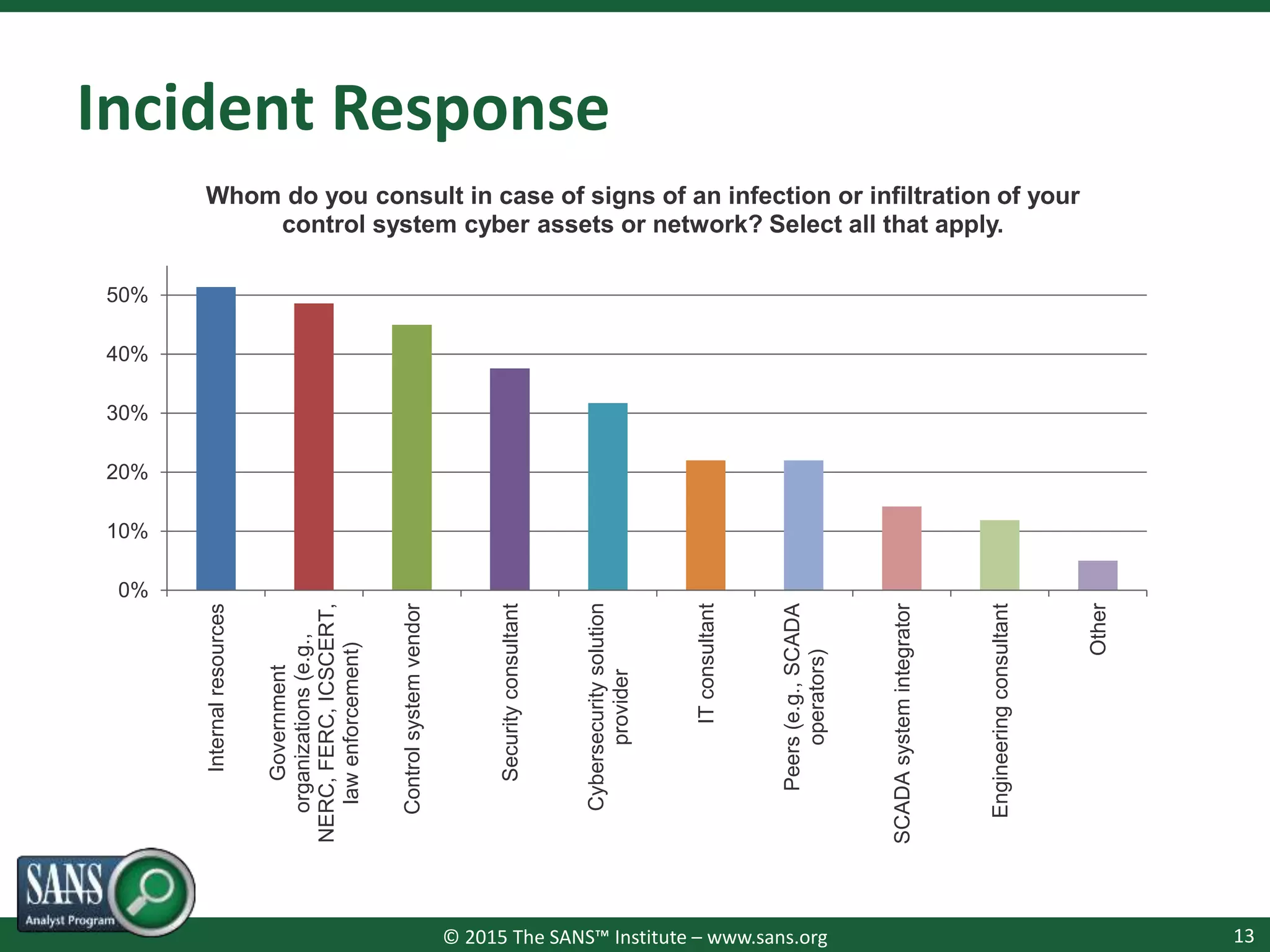
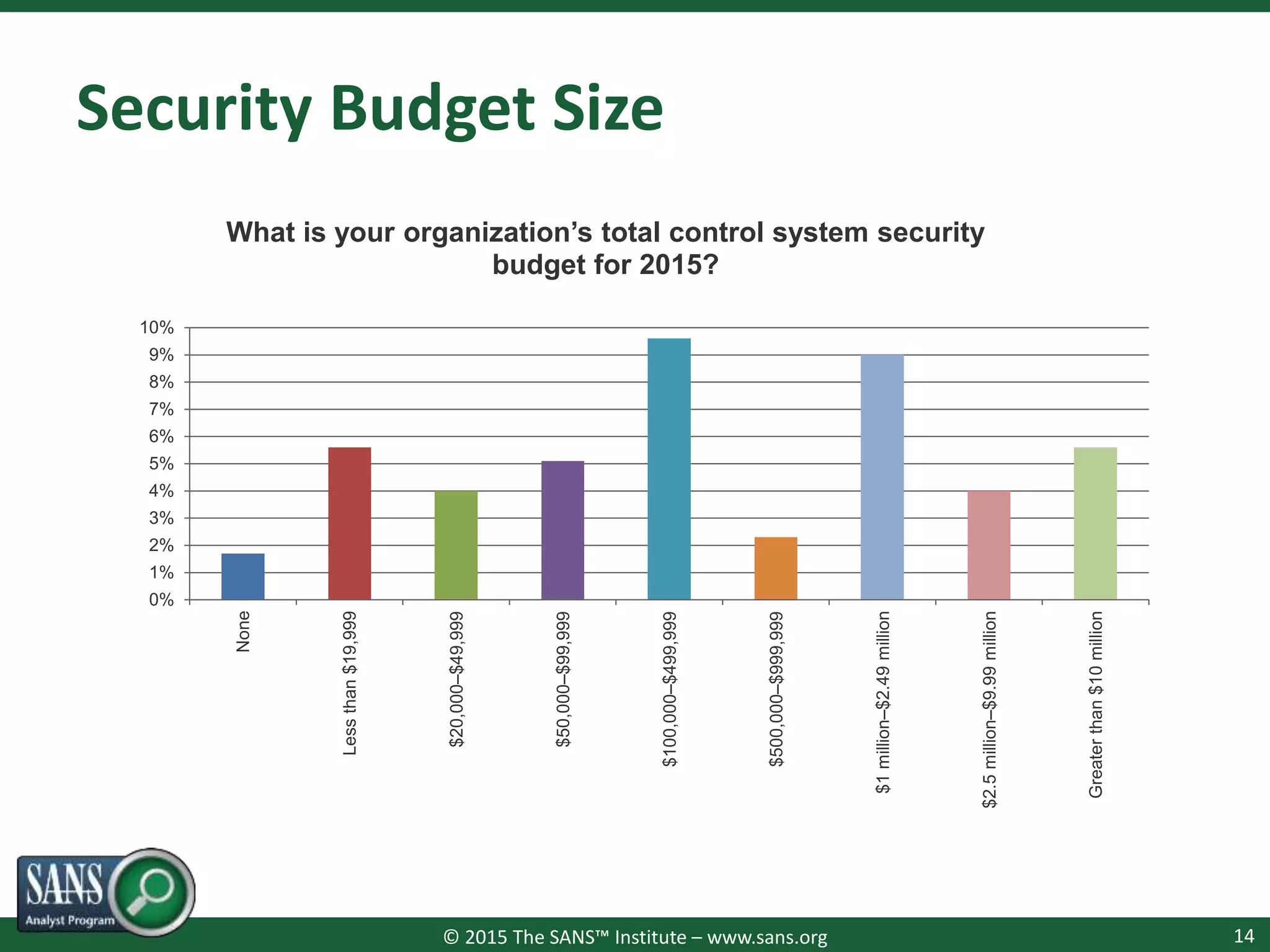
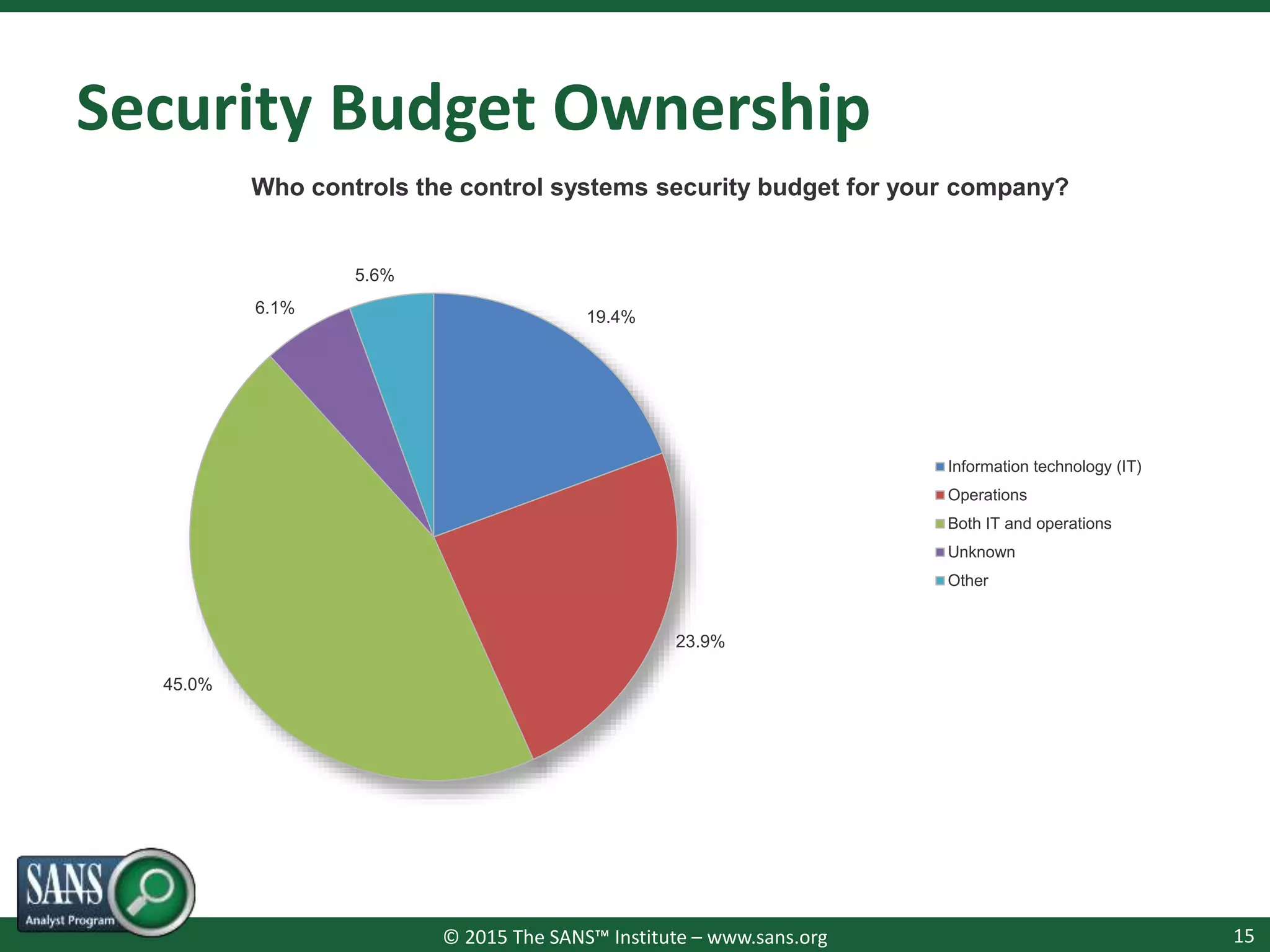
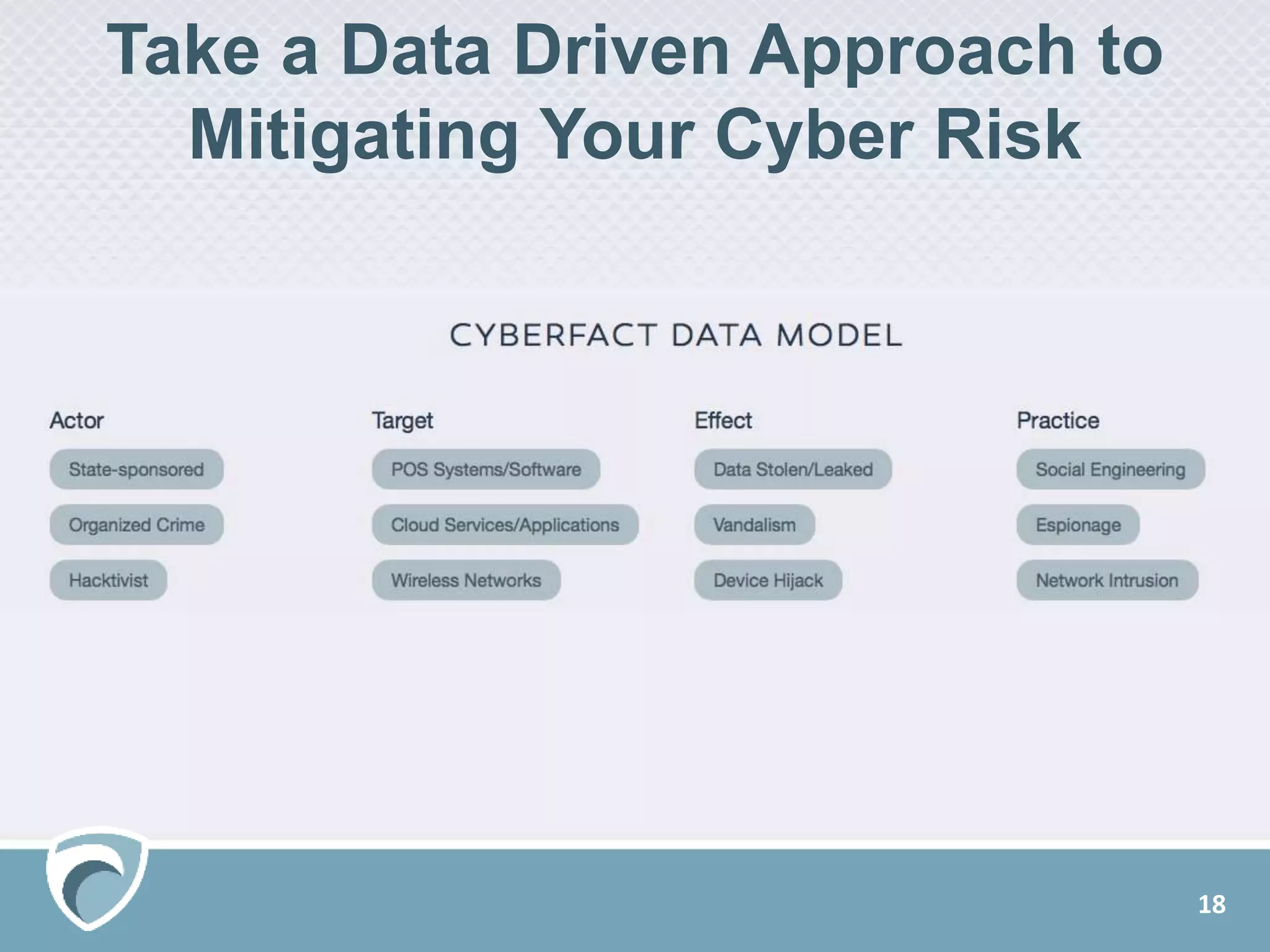
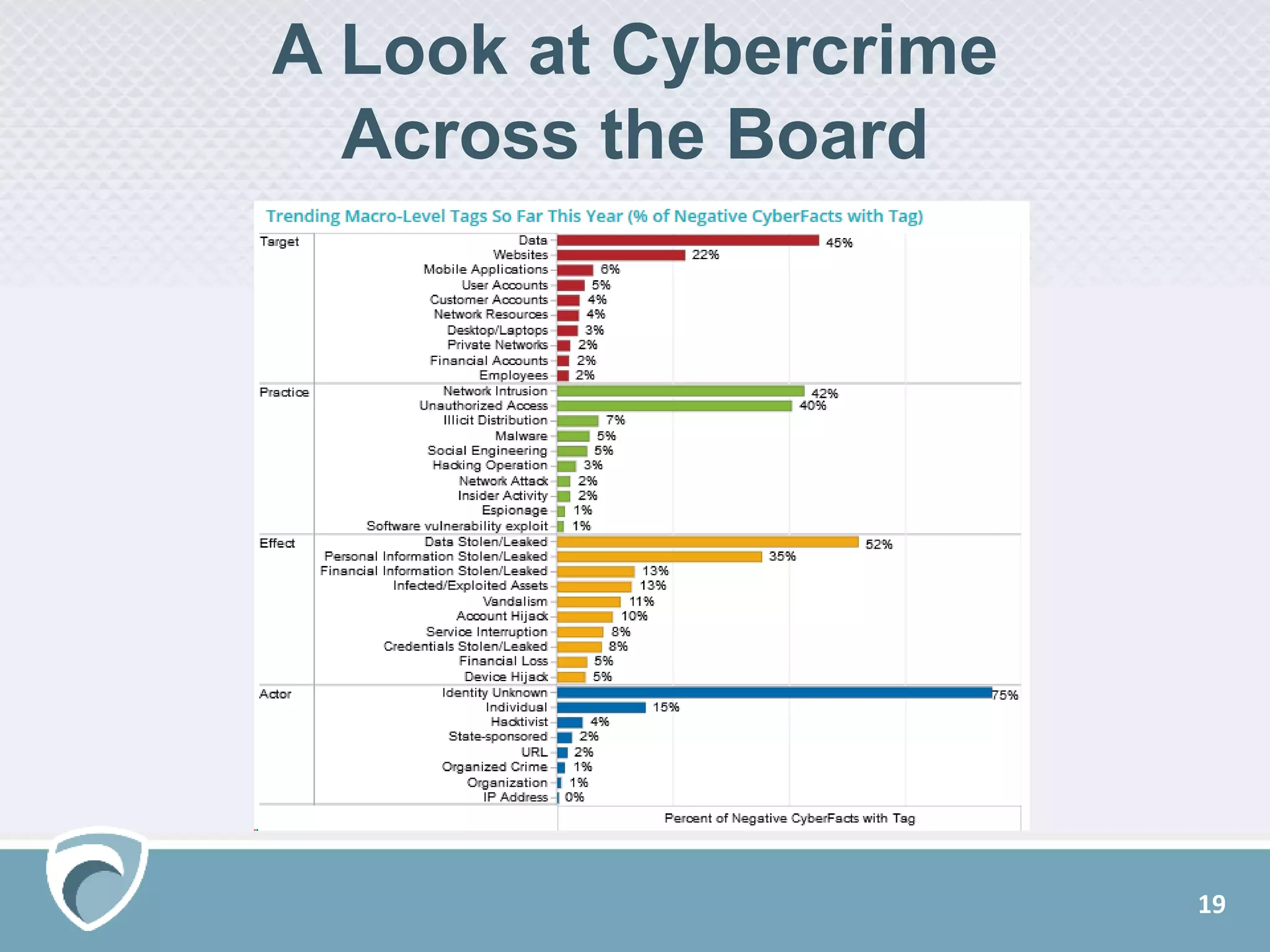
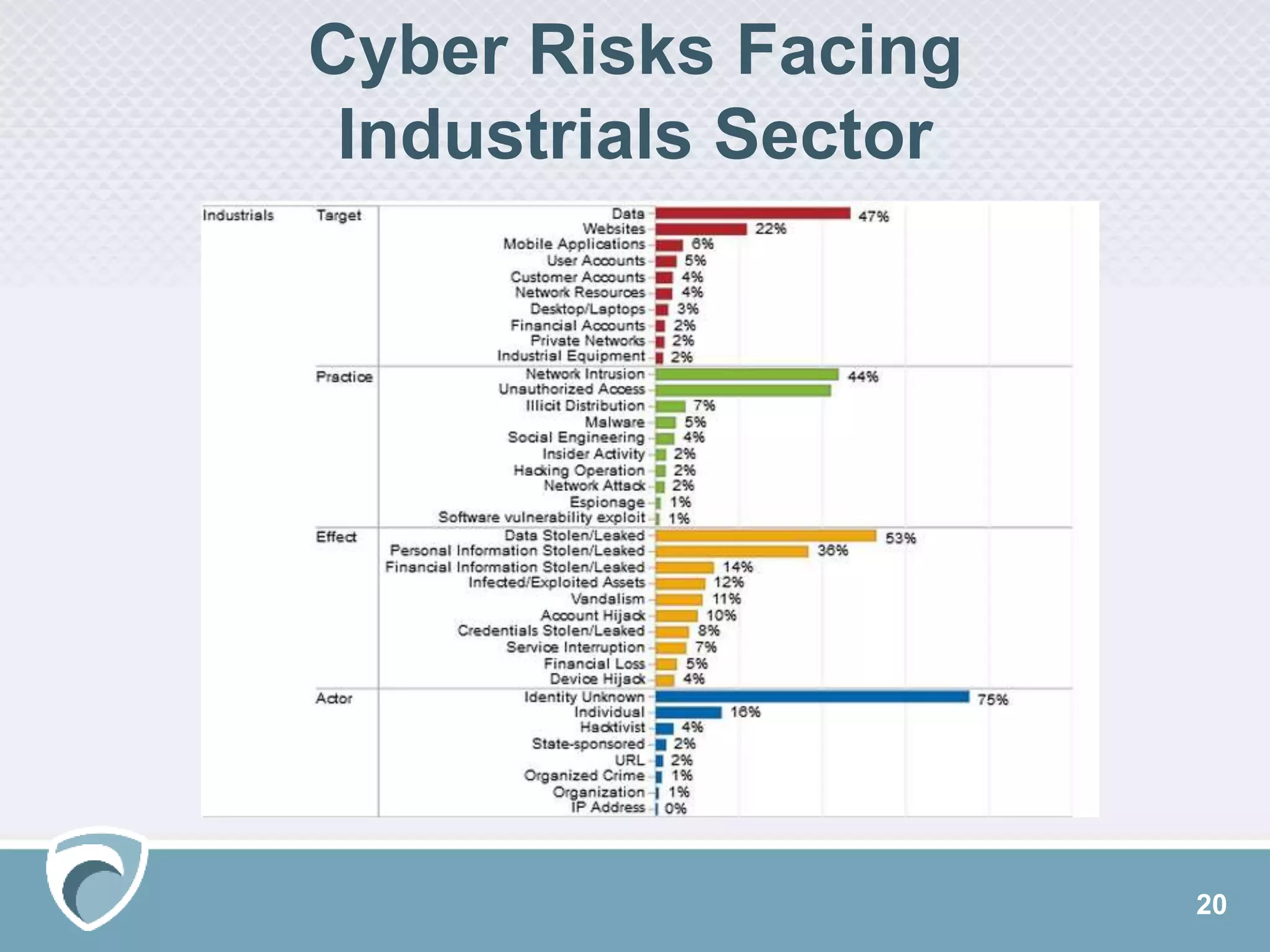
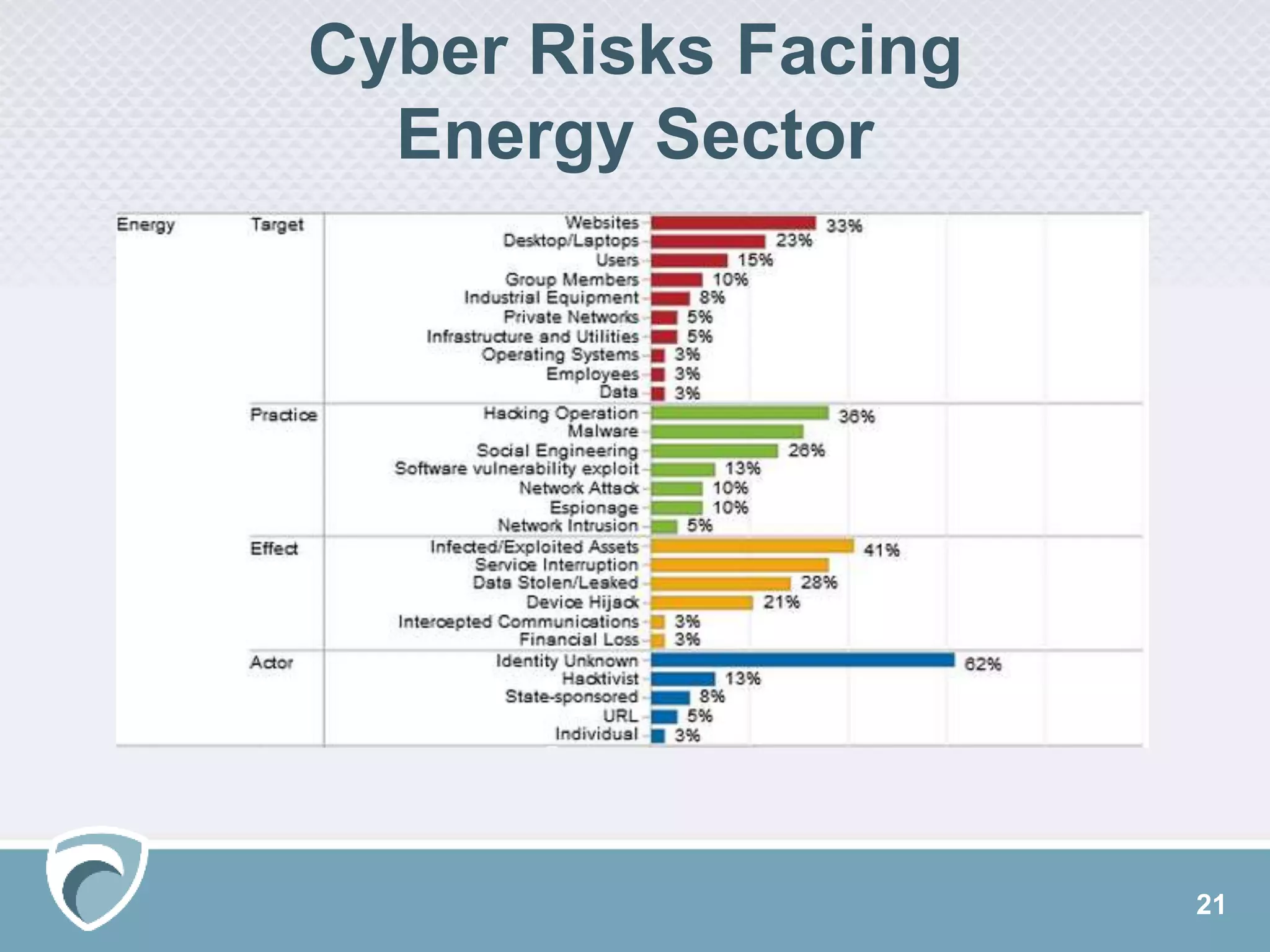
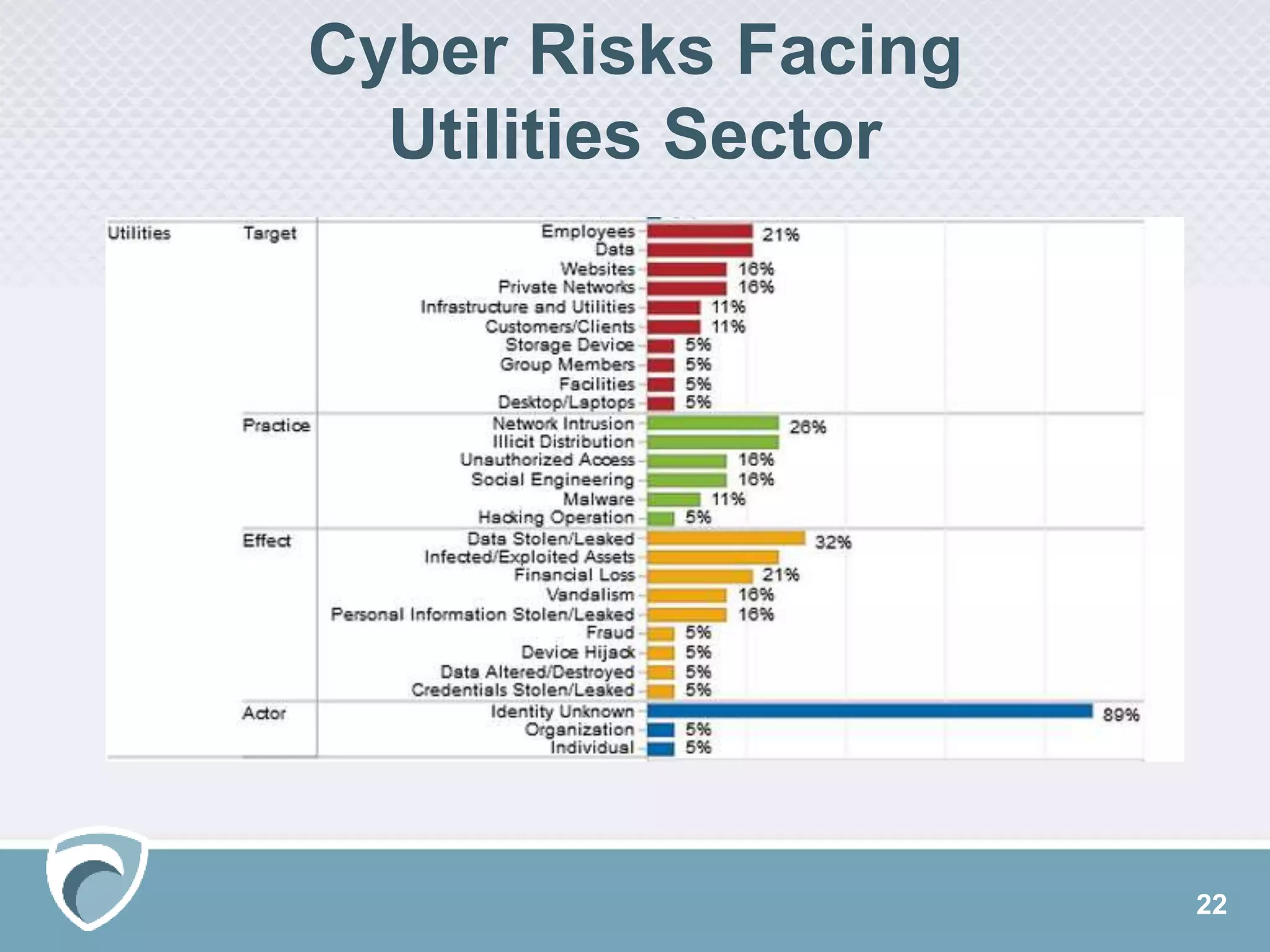
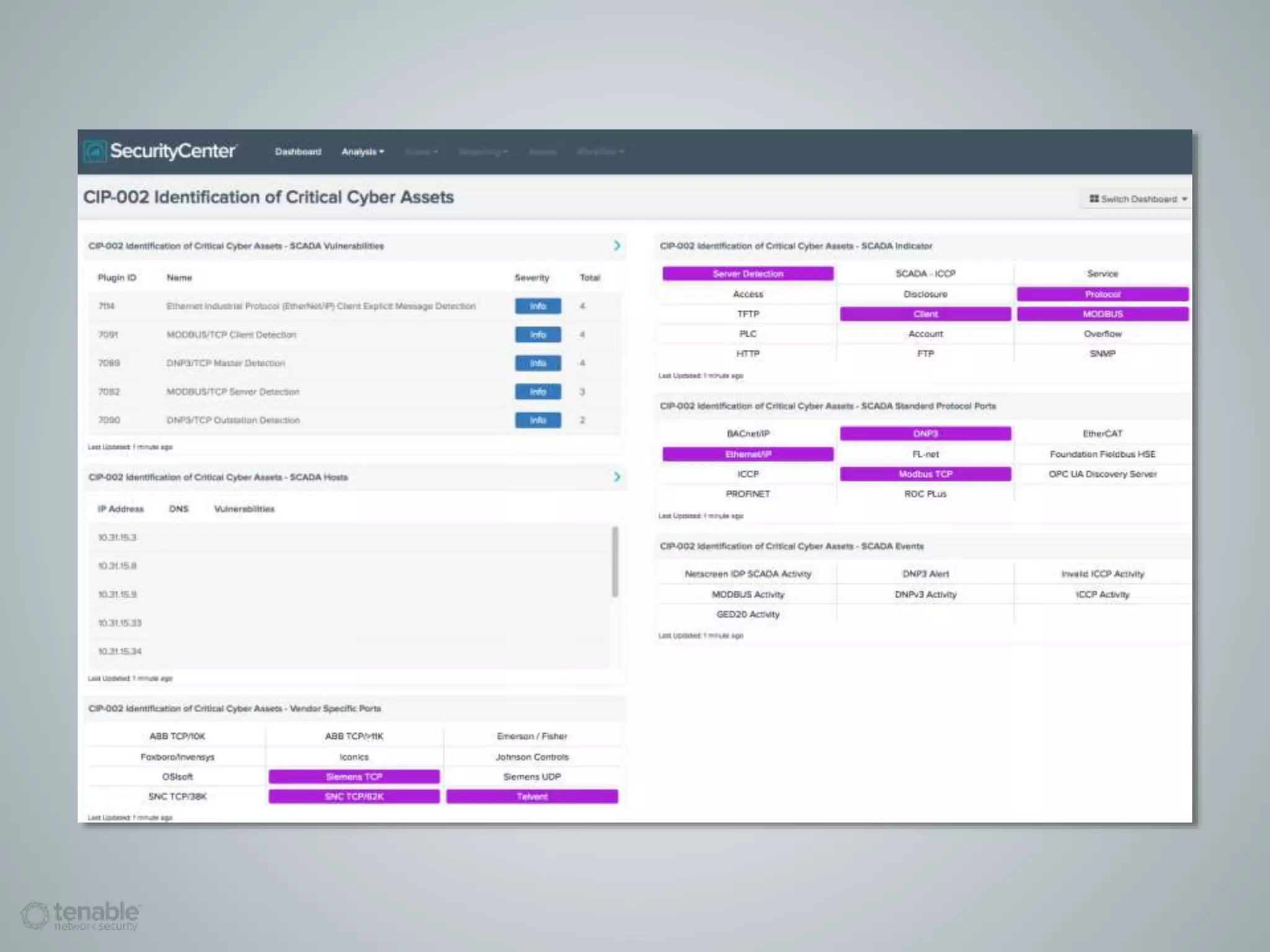
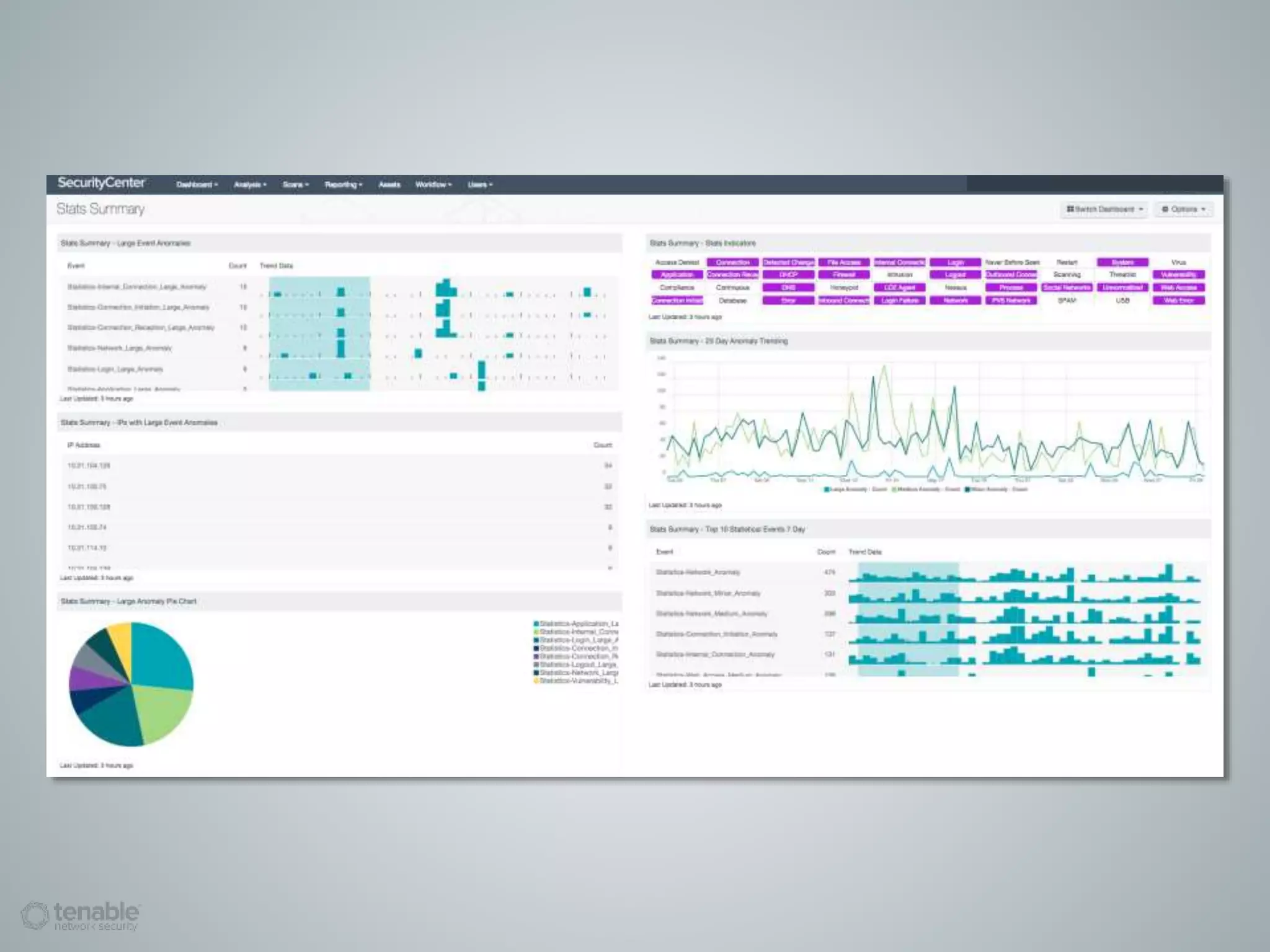
The document presents a survey webcast discussing the current state of security in industrial control systems, highlighting top threat vectors and security initiatives. It reveals that external threats and lack of visibility are significant challenges for organizations, and many do not have a comprehensive security strategy. Additionally, it touches on cybersecurity budgets, recent breaches, and the importance of continuous network monitoring to enhance security.