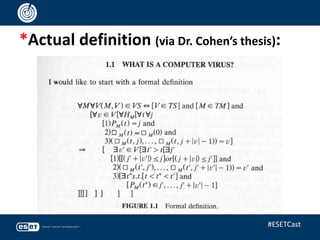
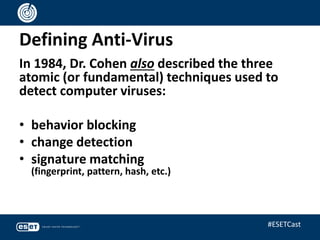
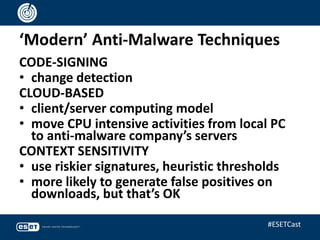
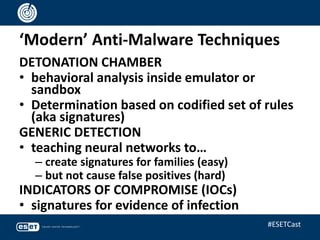
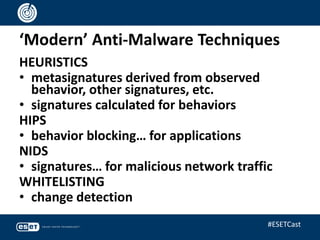
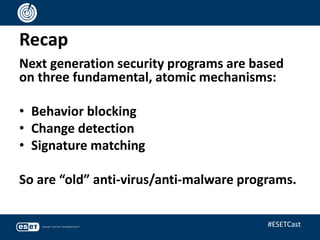
The document discusses the relevance of anti-virus (AV) software from the 1980s to the present, highlighting the evolving landscape of malware and the ongoing debate about whether antivirus is 'dead.' It emphasizes that while traditional viruses represent a small percentage of current threats, the field of anti-malware has adapted to include a variety of sophisticated techniques beyond simple signature matching. Ultimately, the presentation argues for the continued importance of anti-malware technologies and the need for ongoing innovation in the fight against increasingly complex cyber threats.