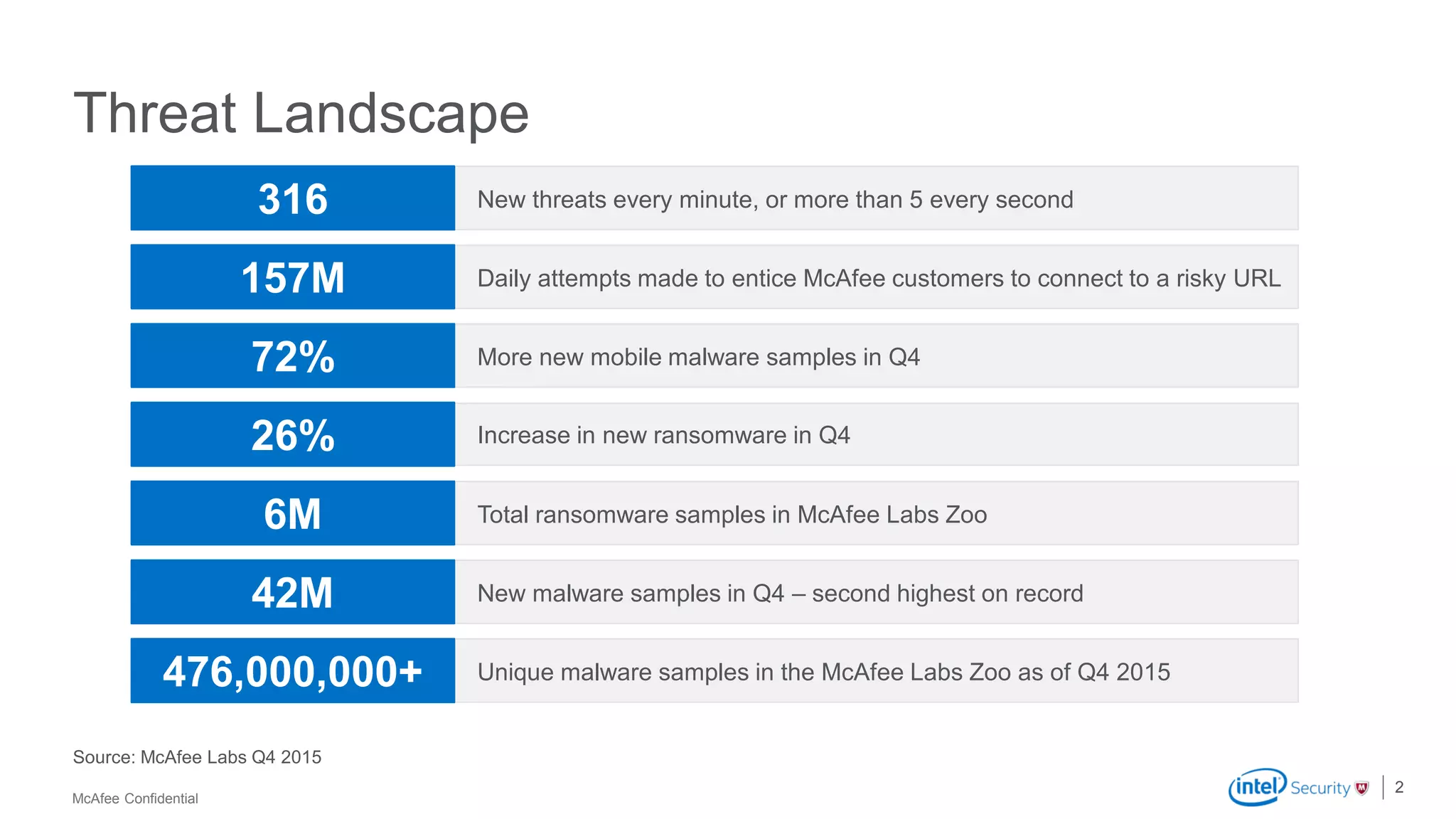
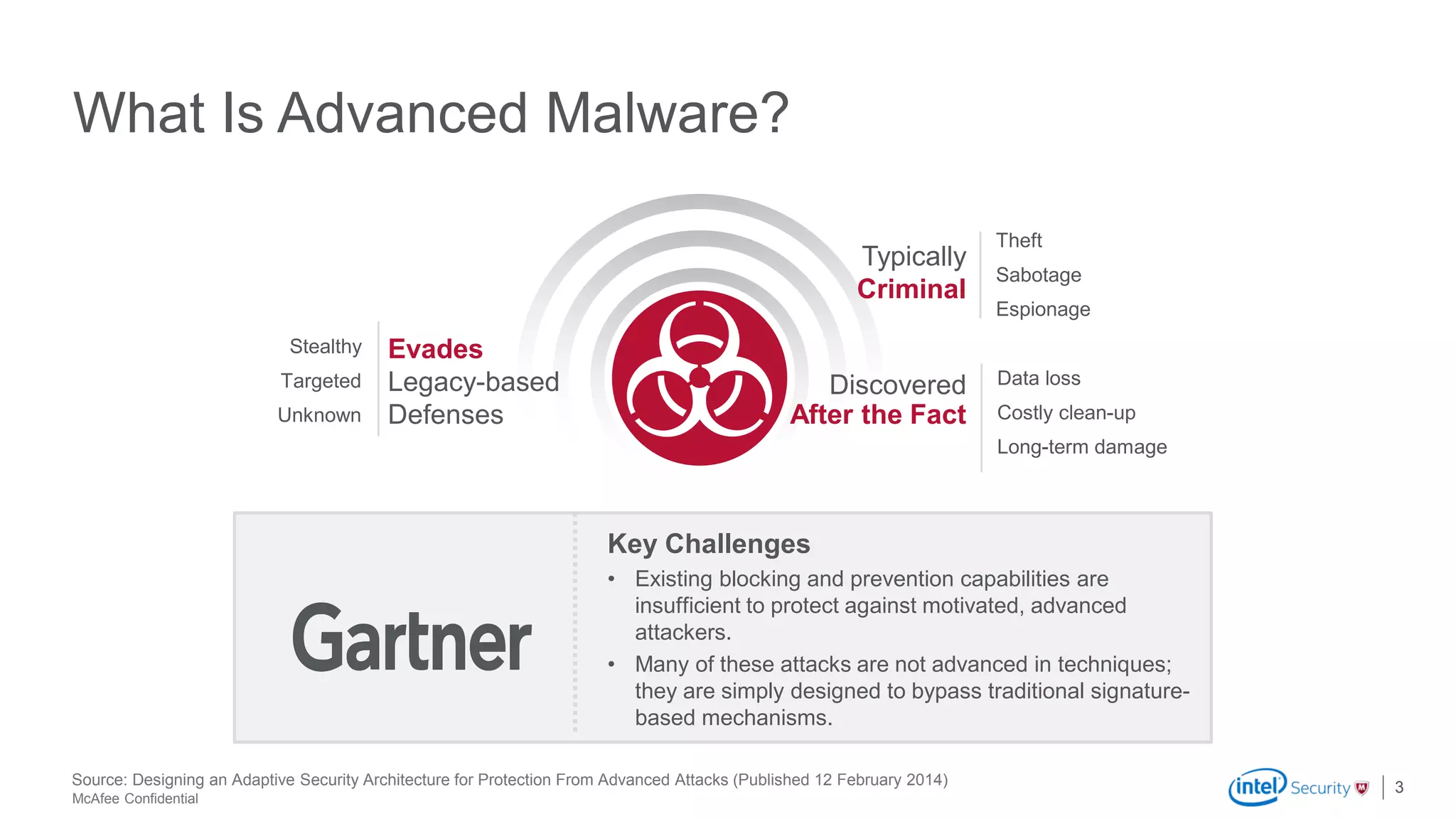
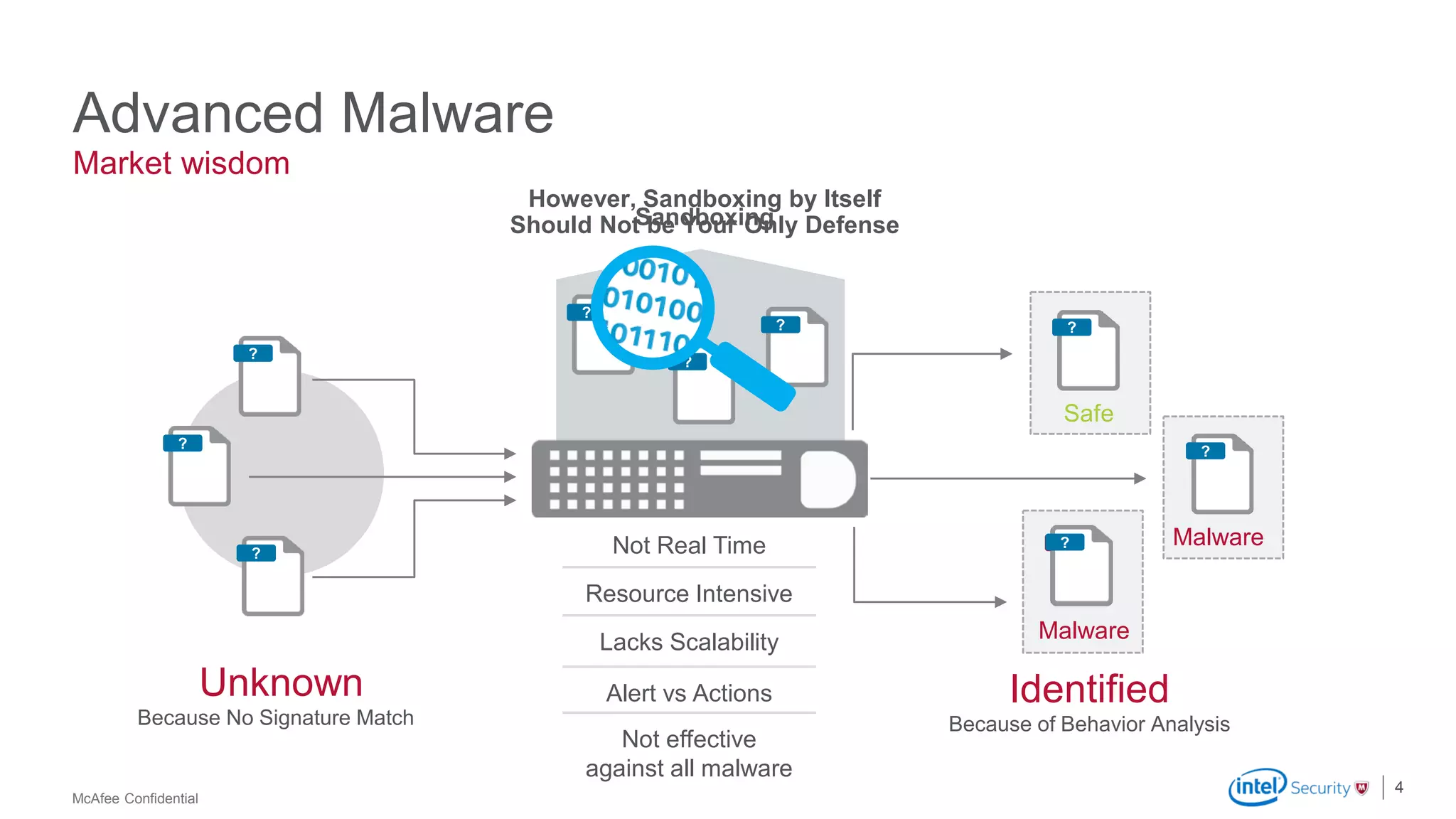
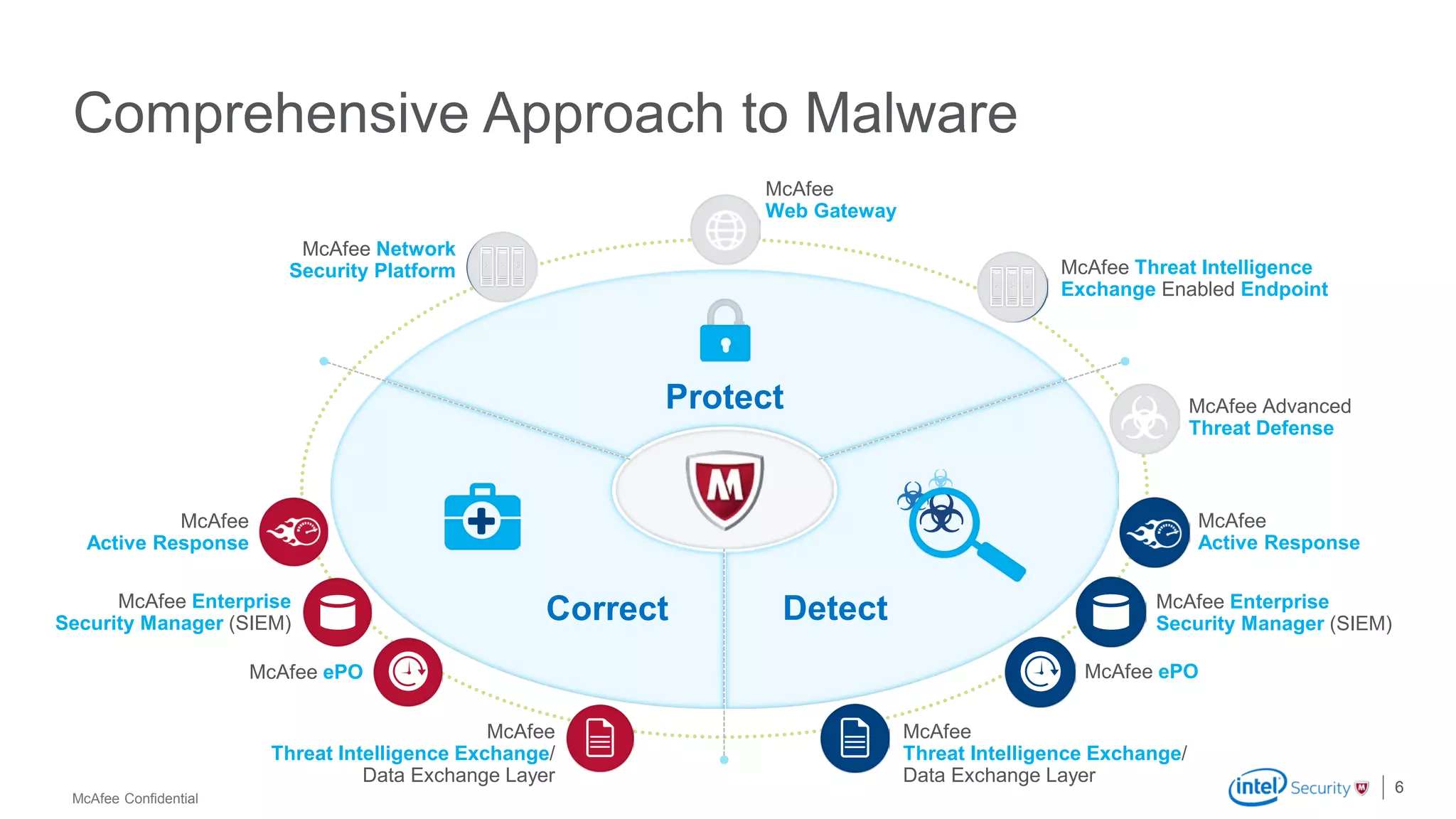
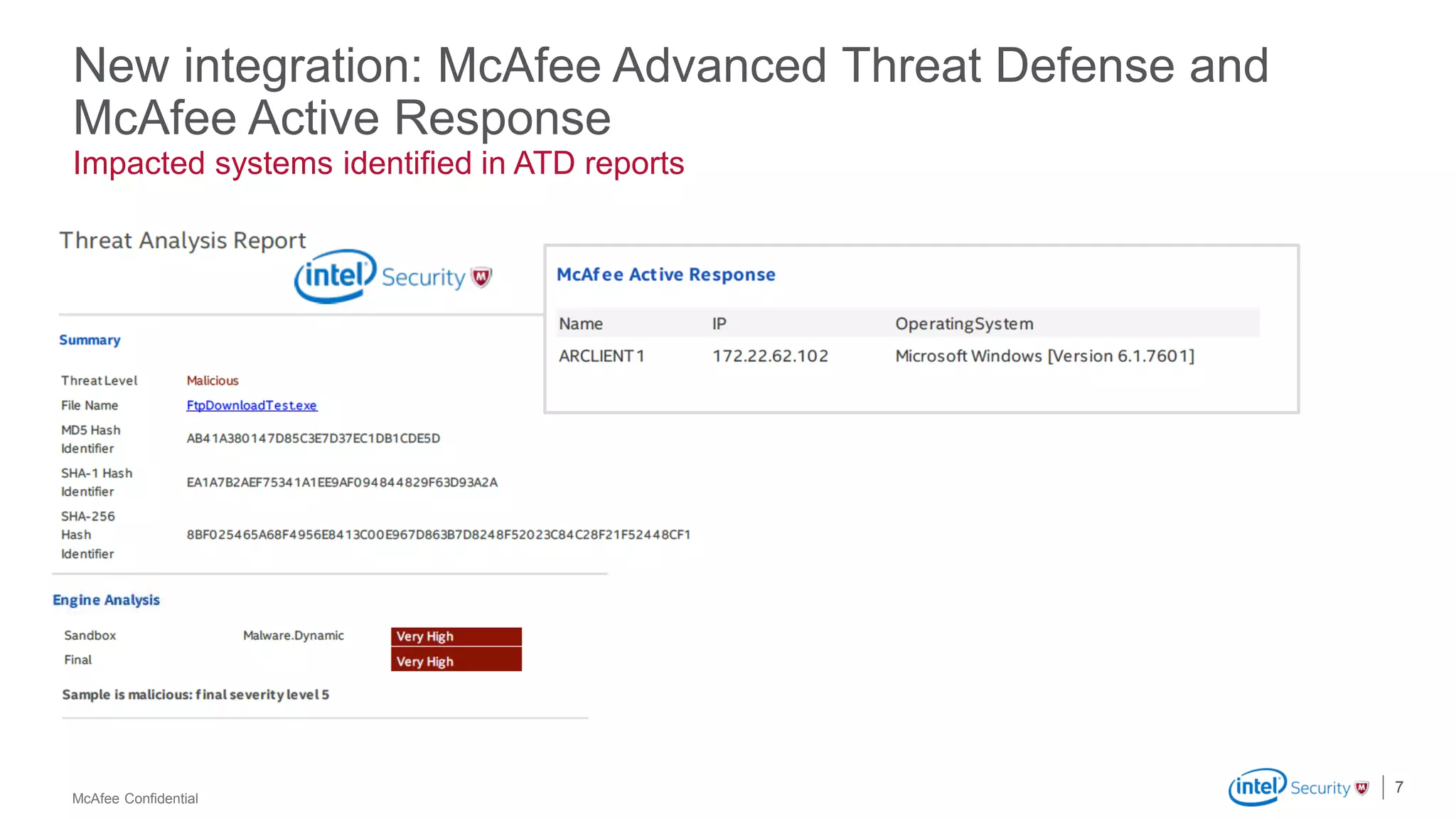
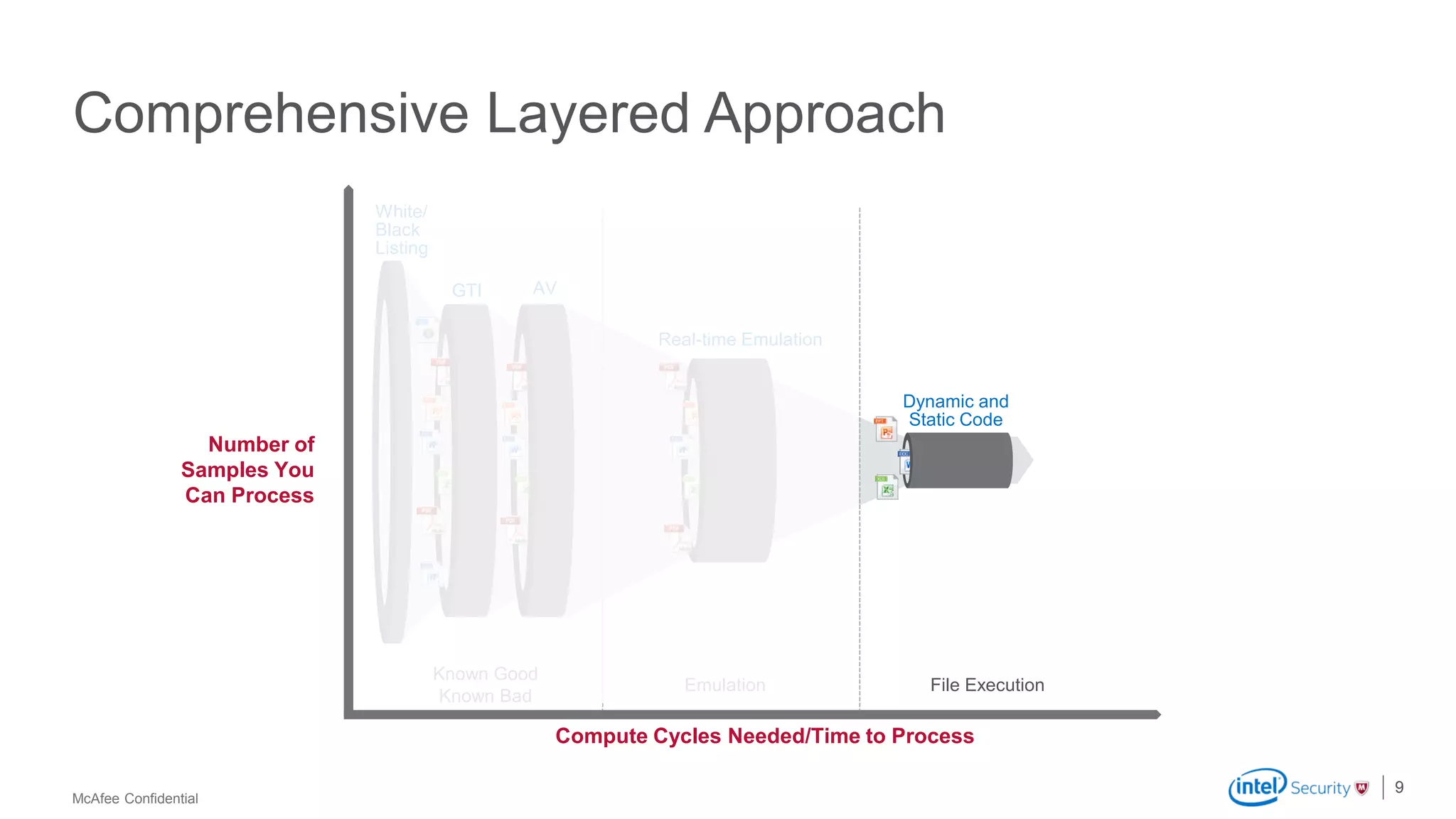
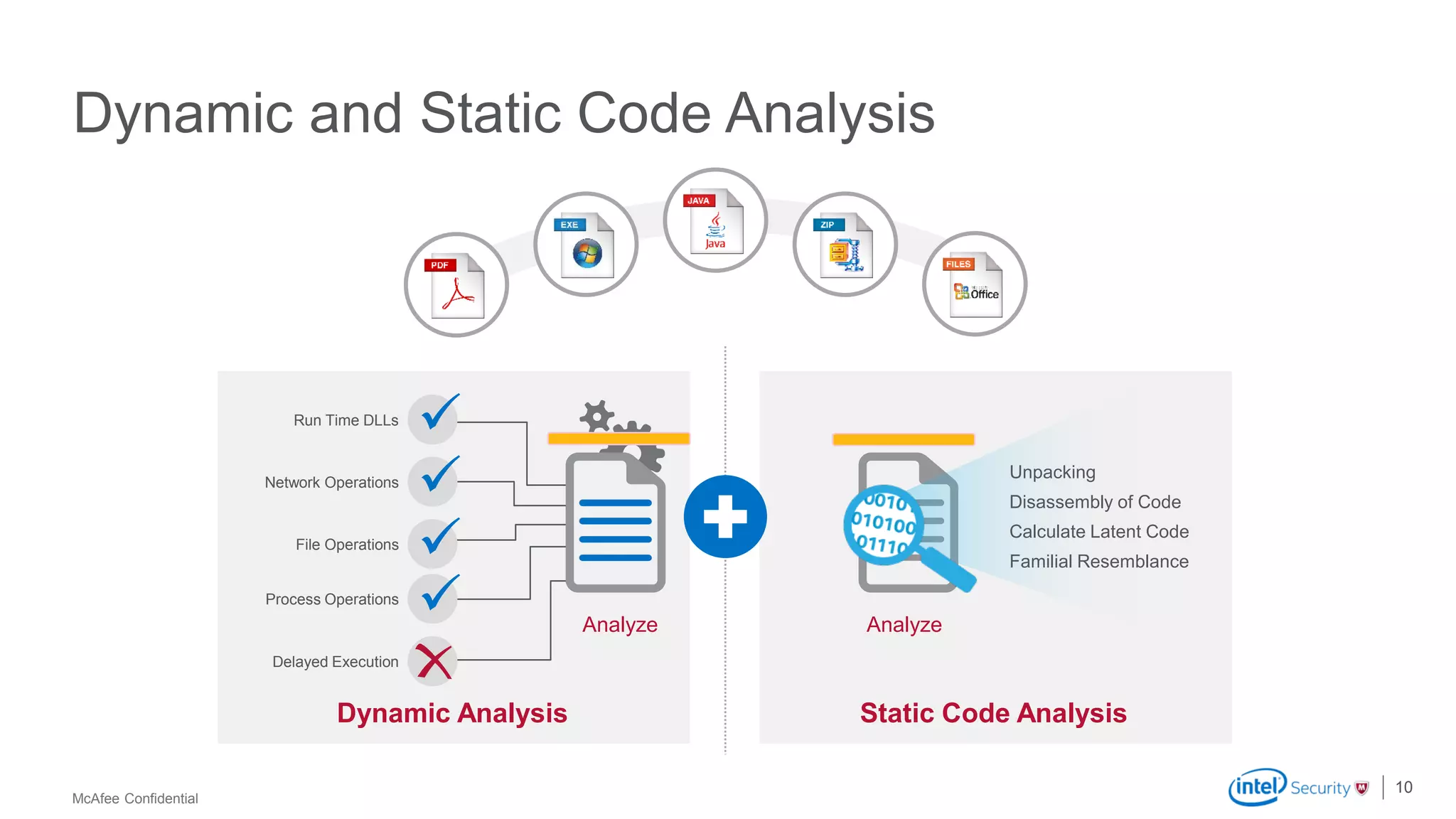
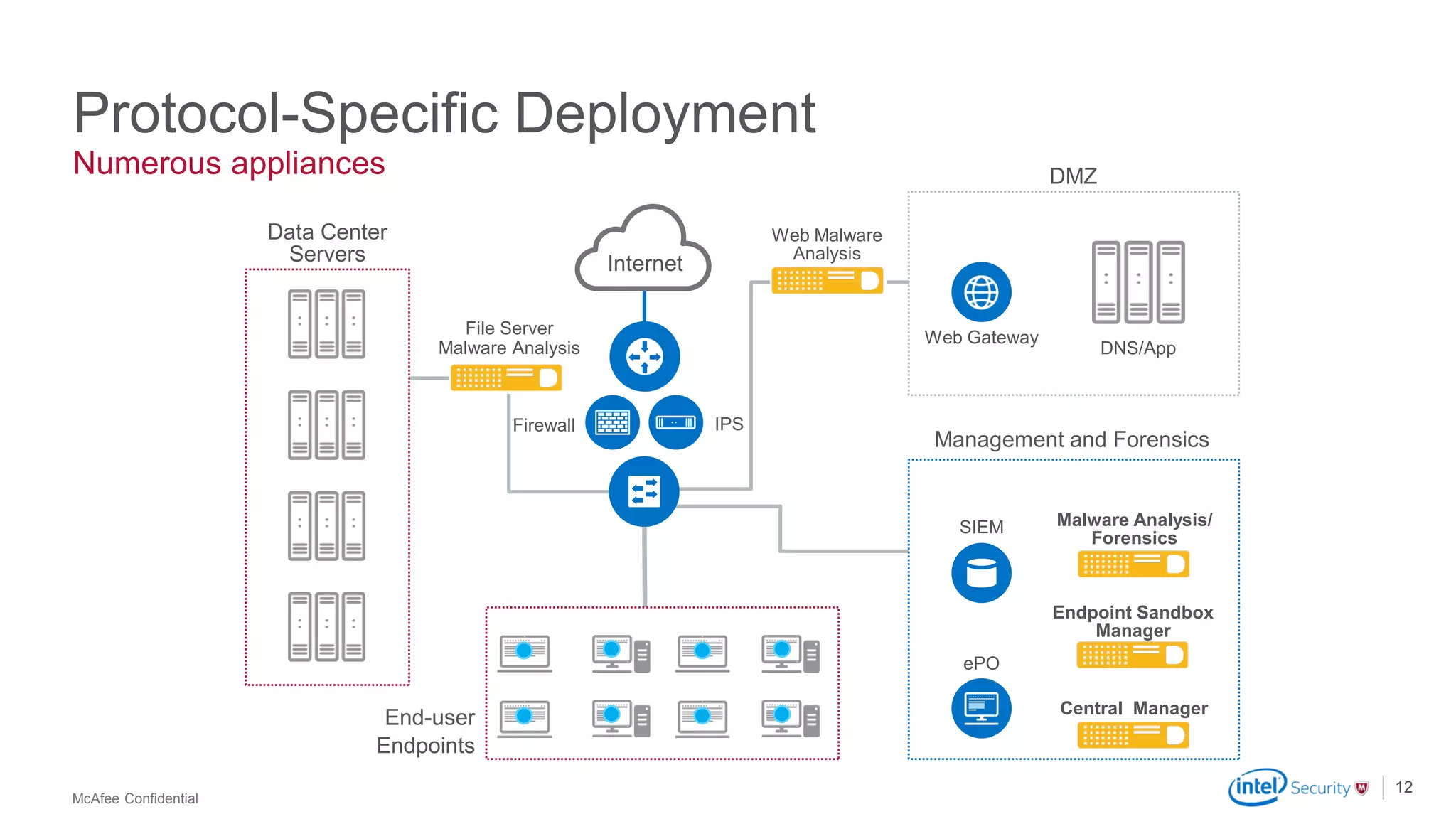
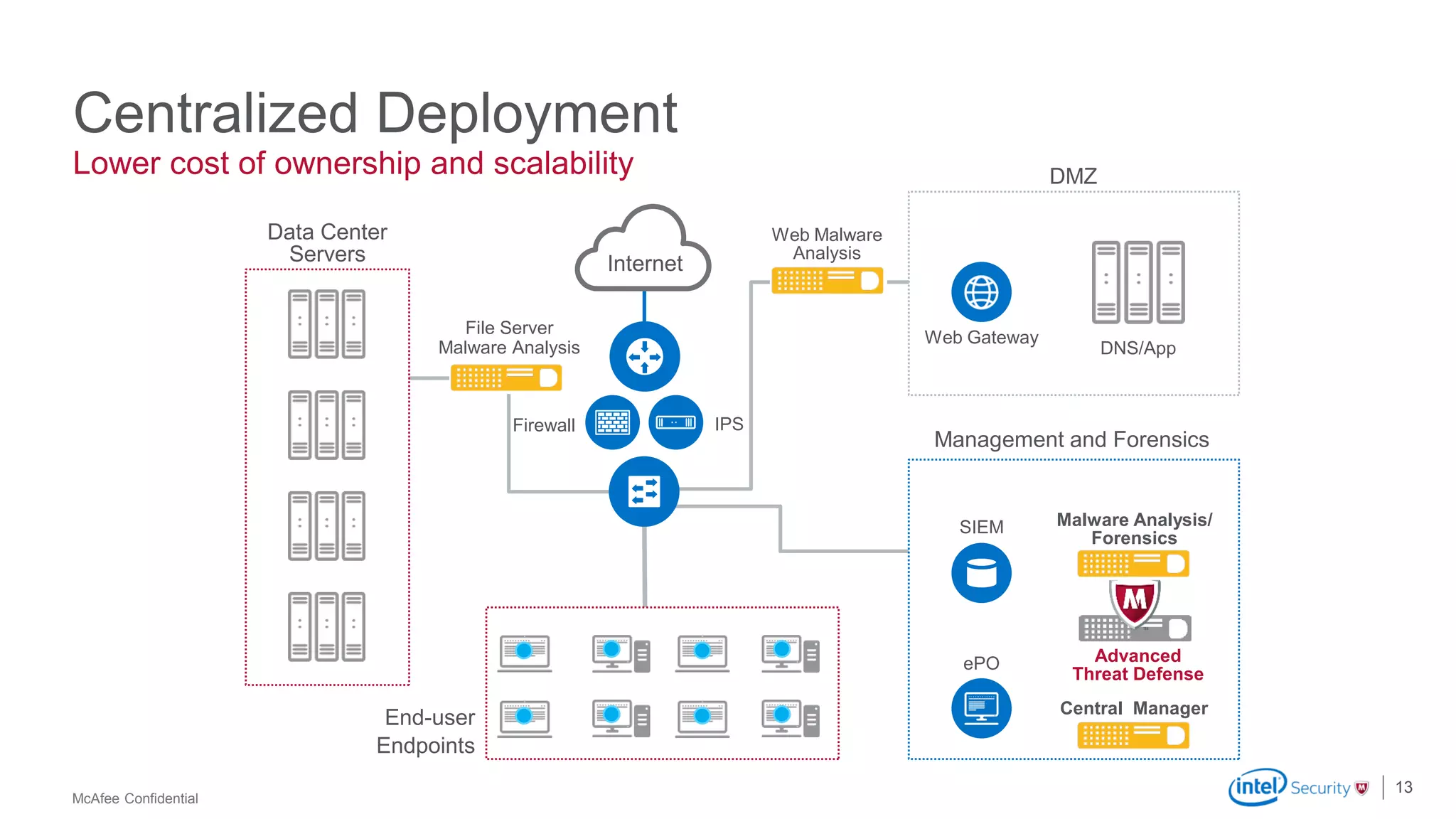
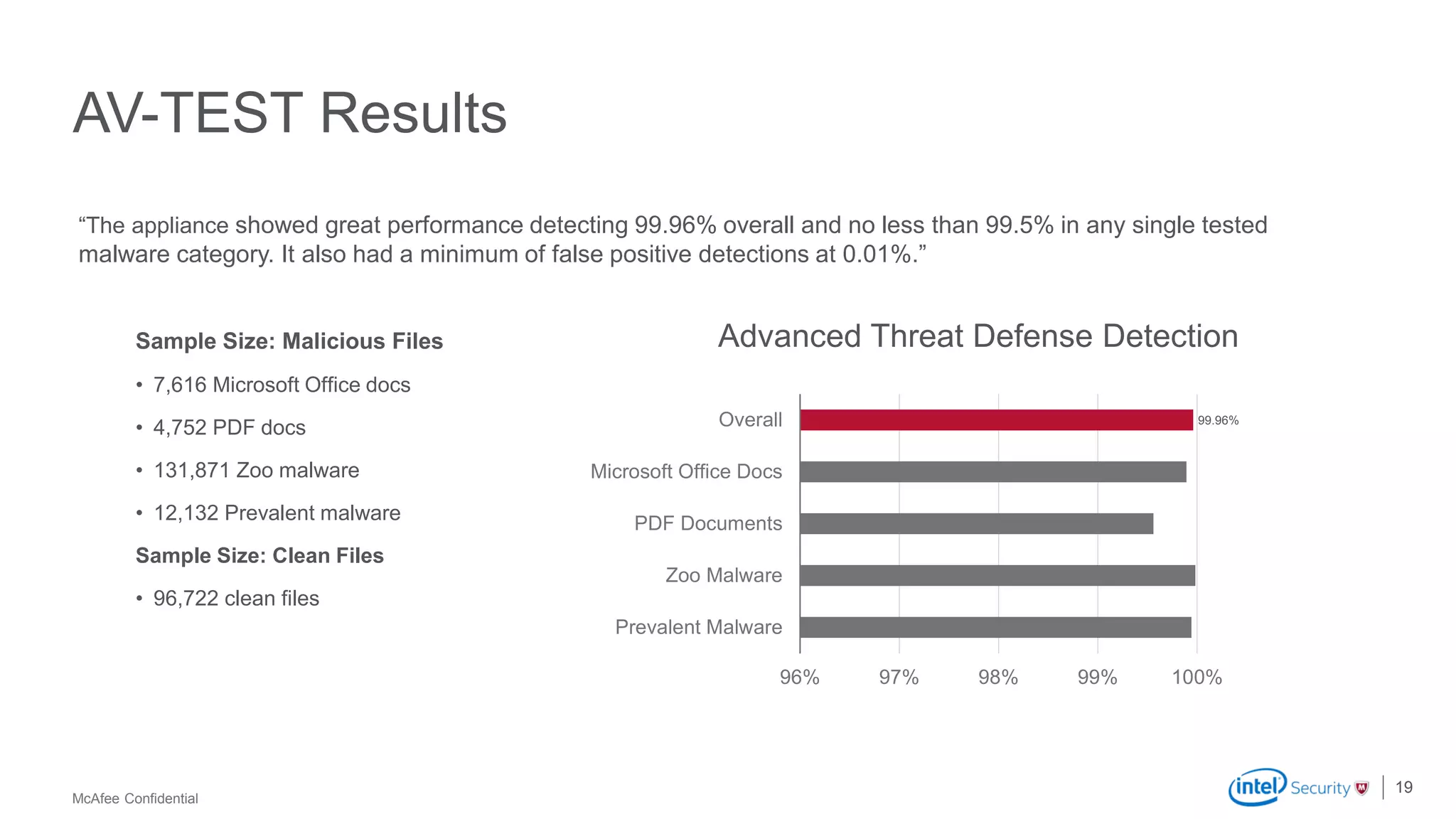
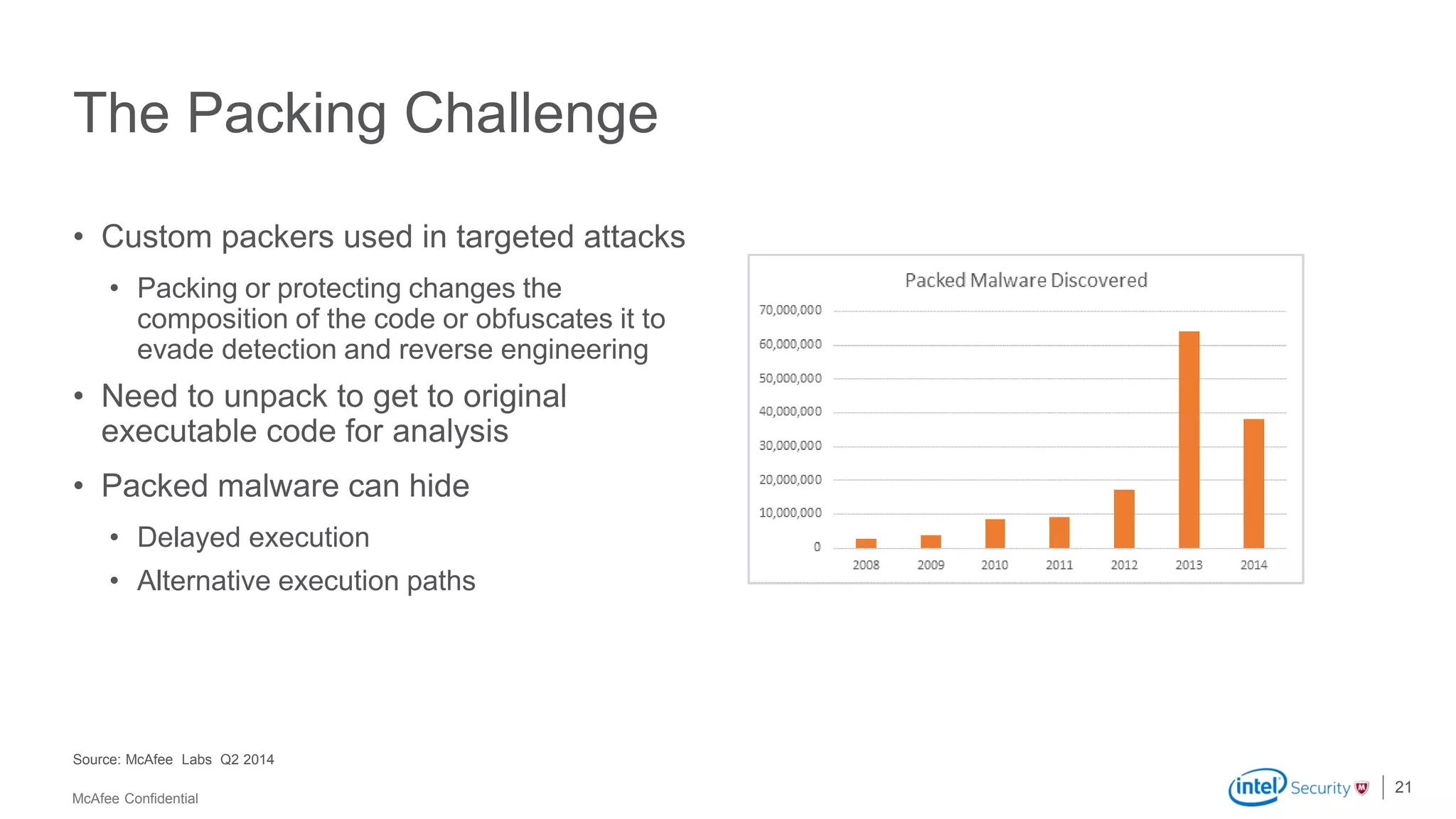
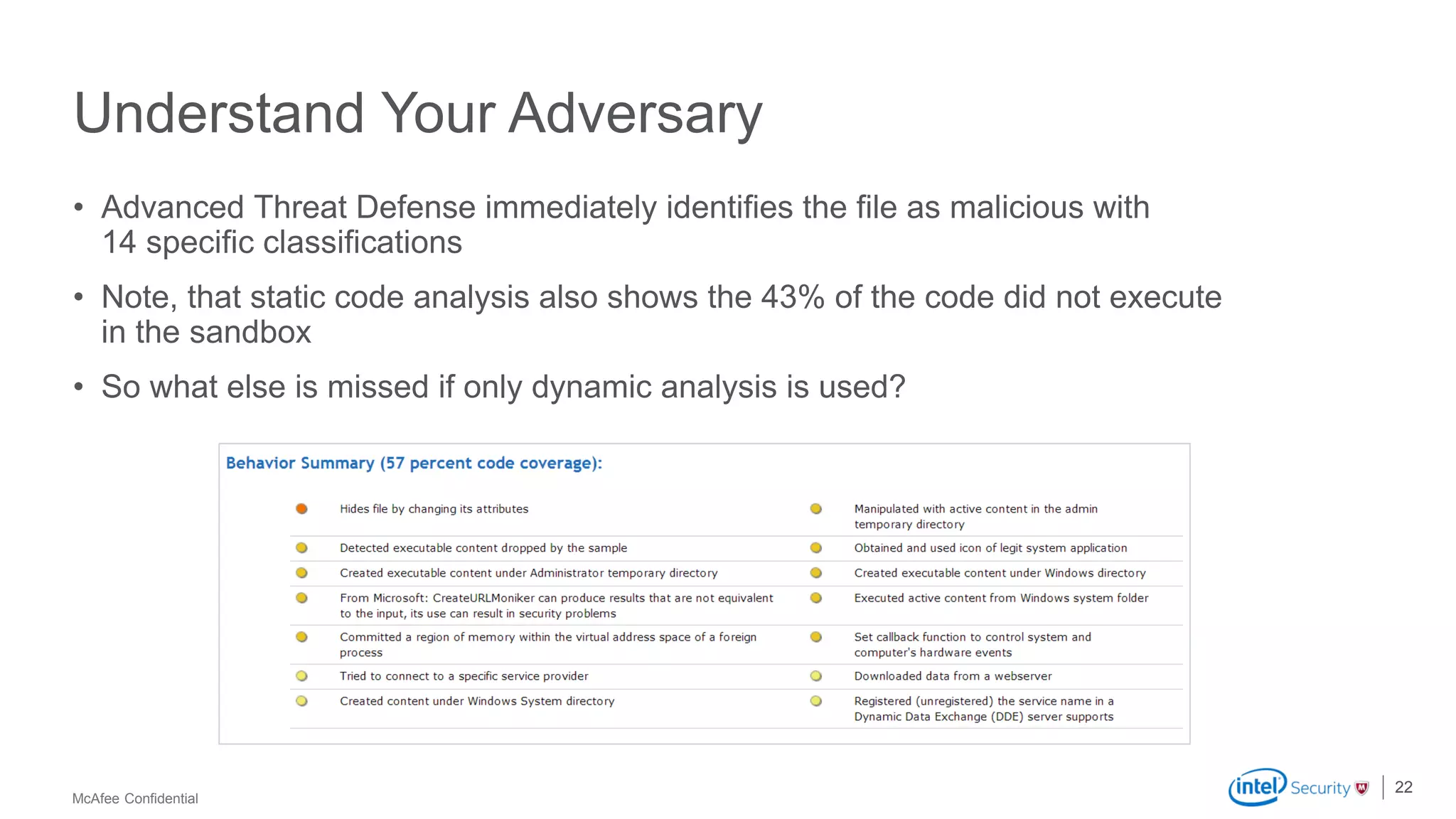
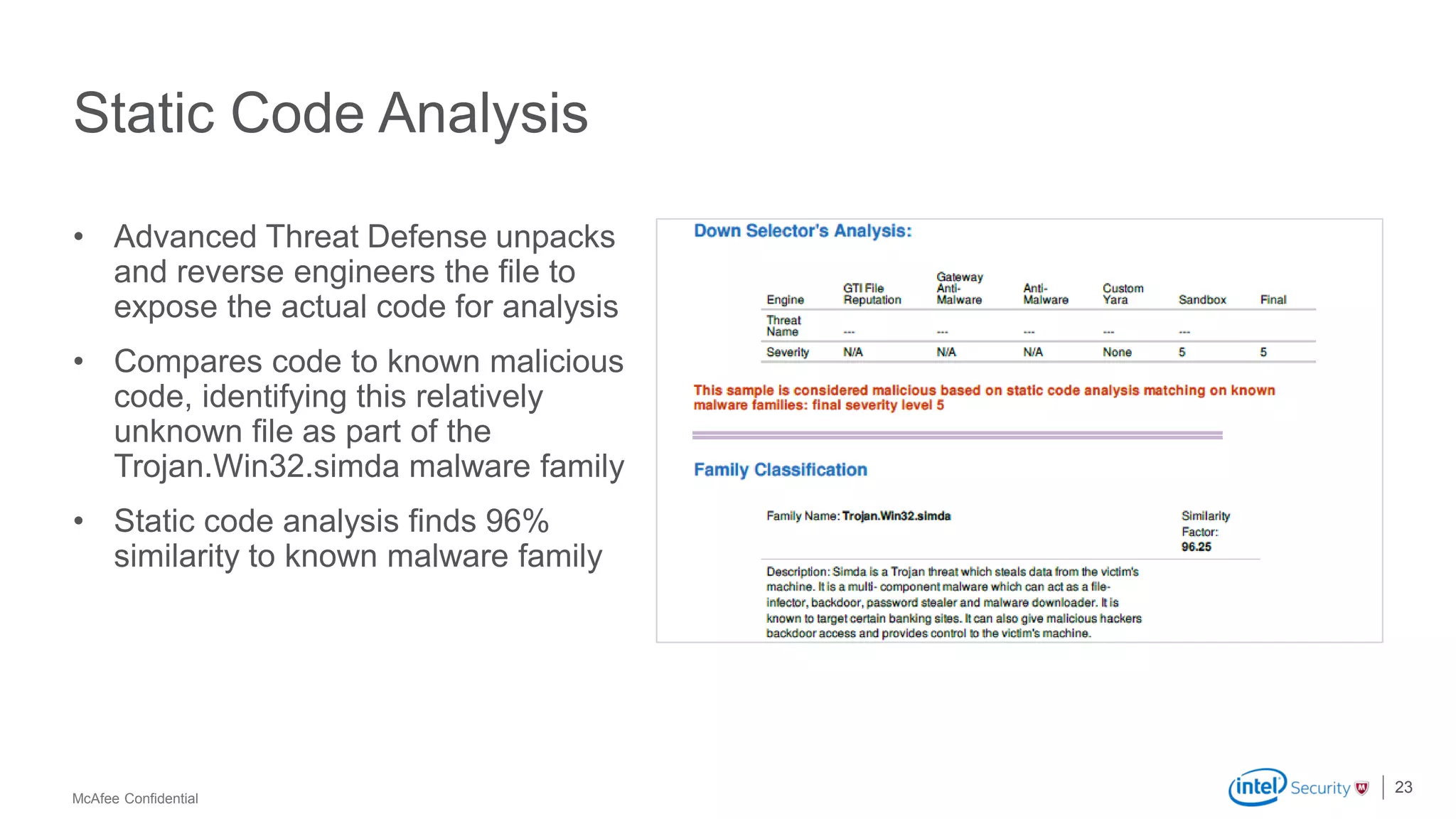
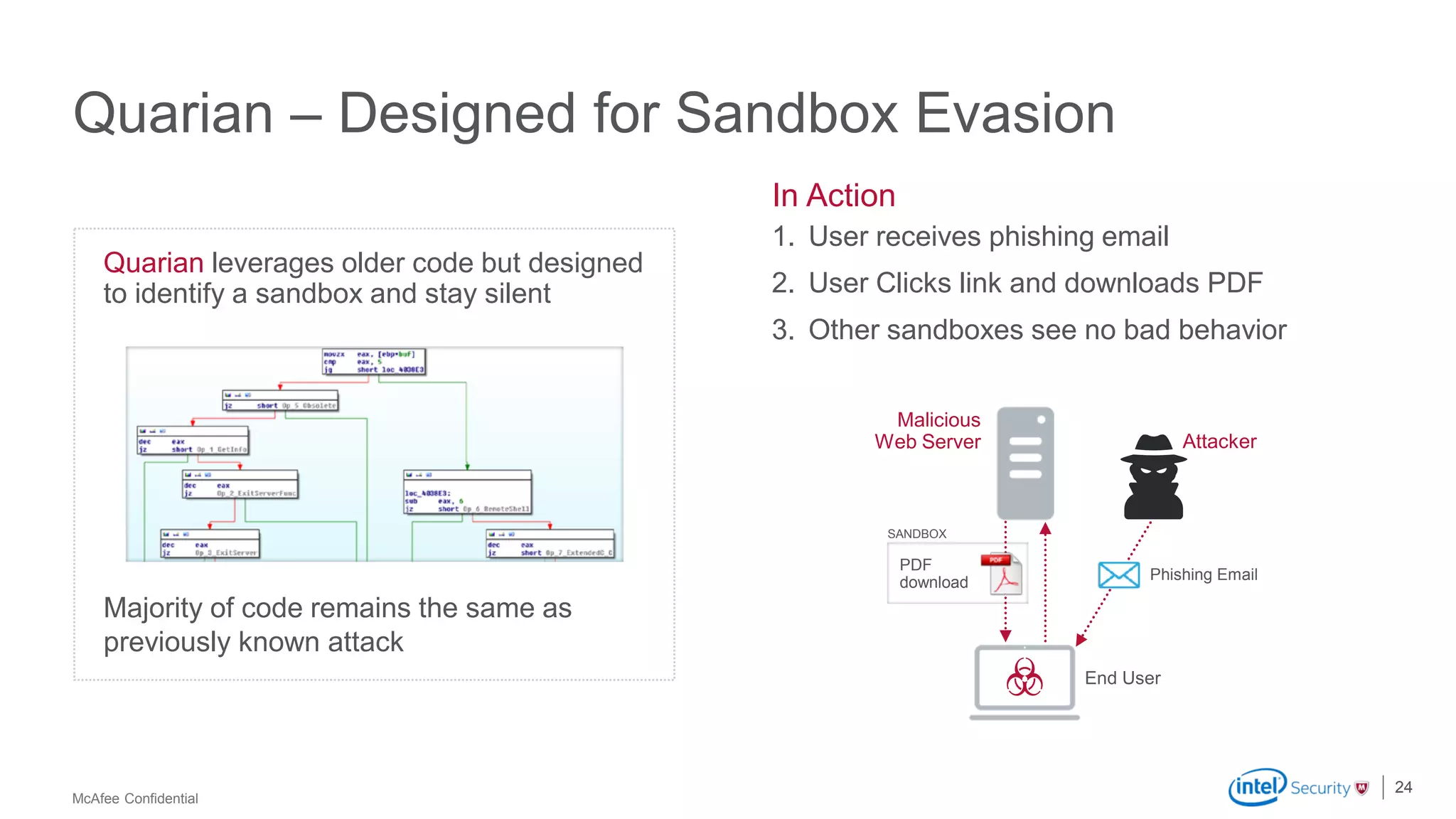
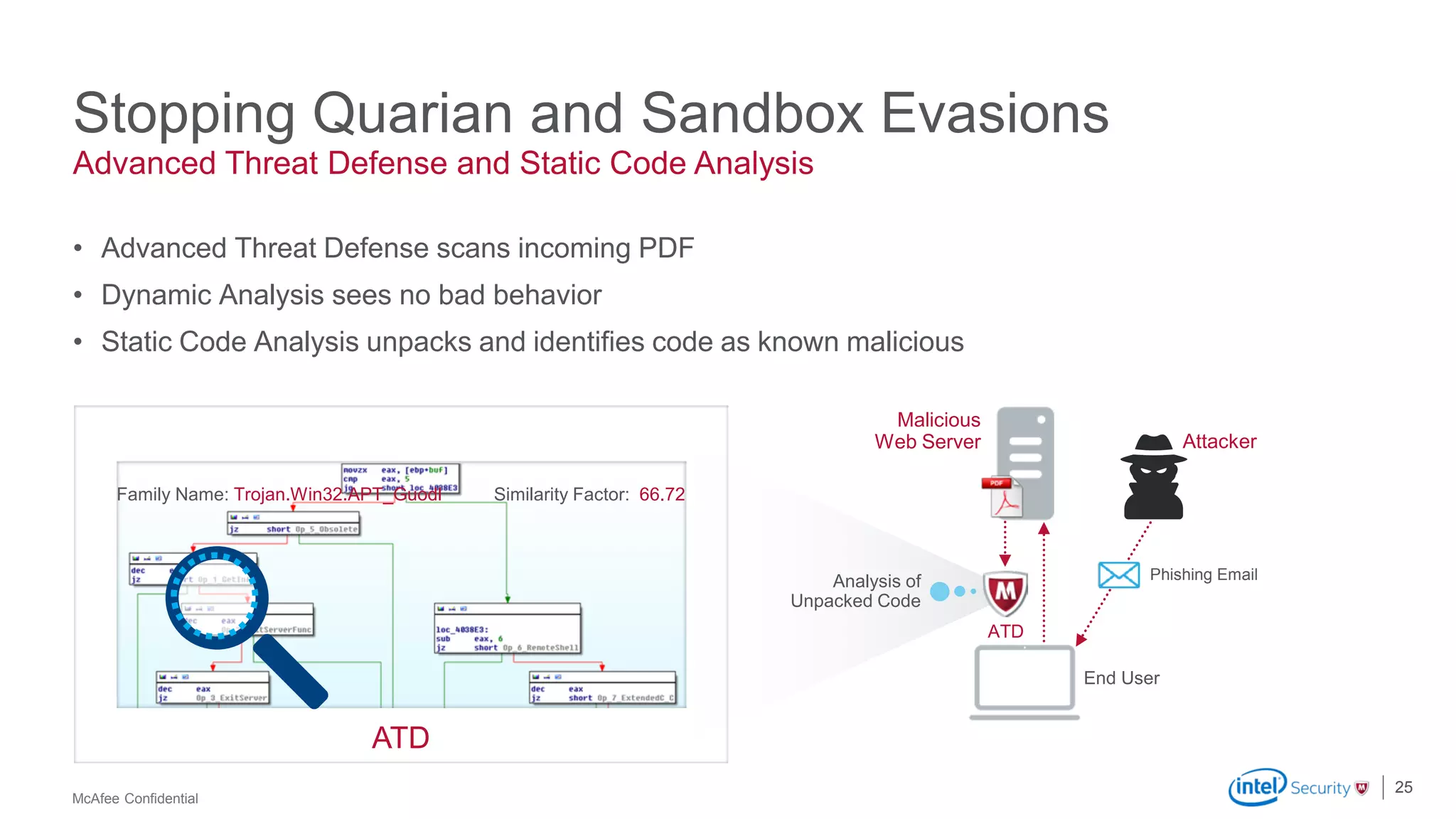
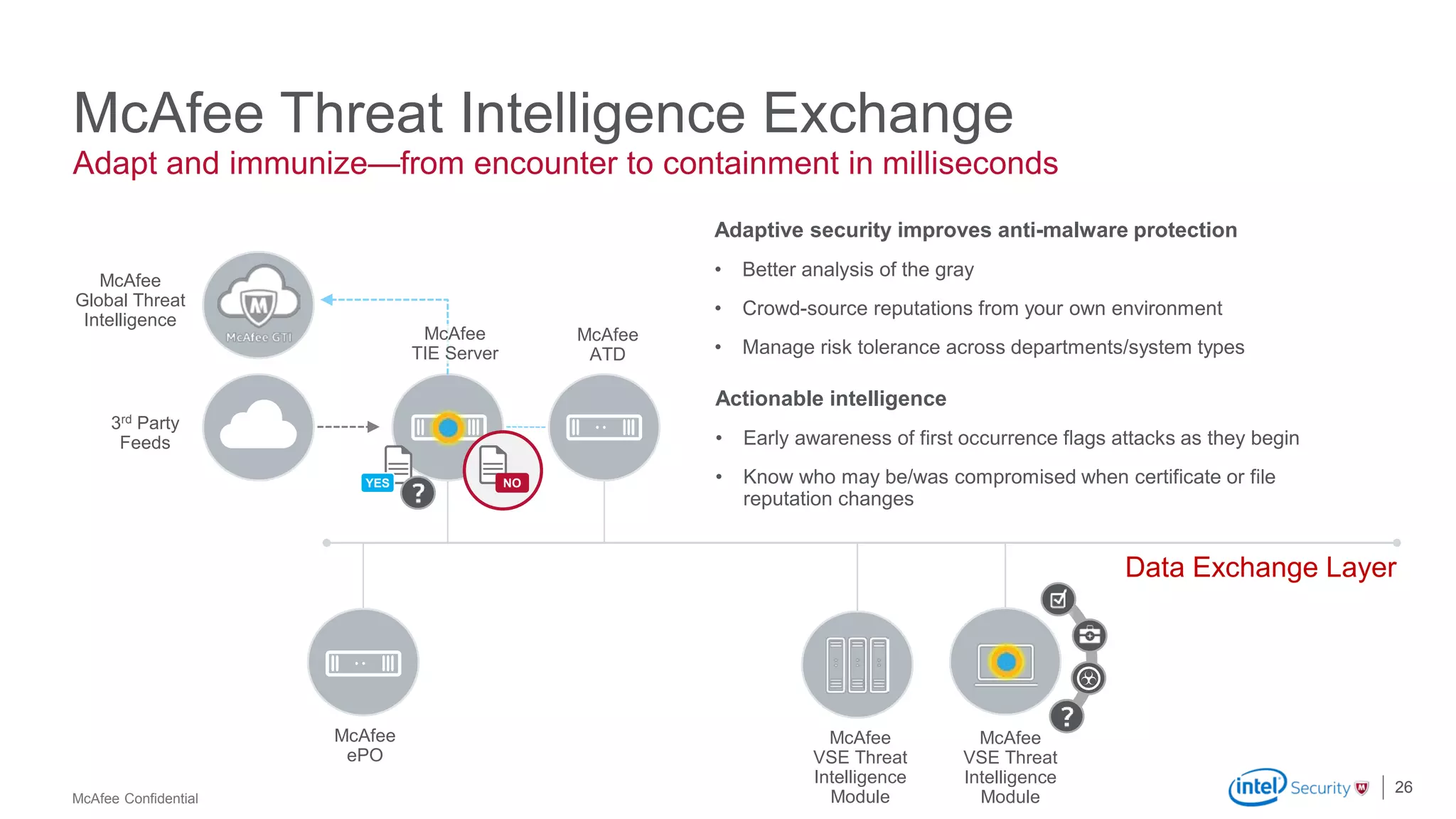
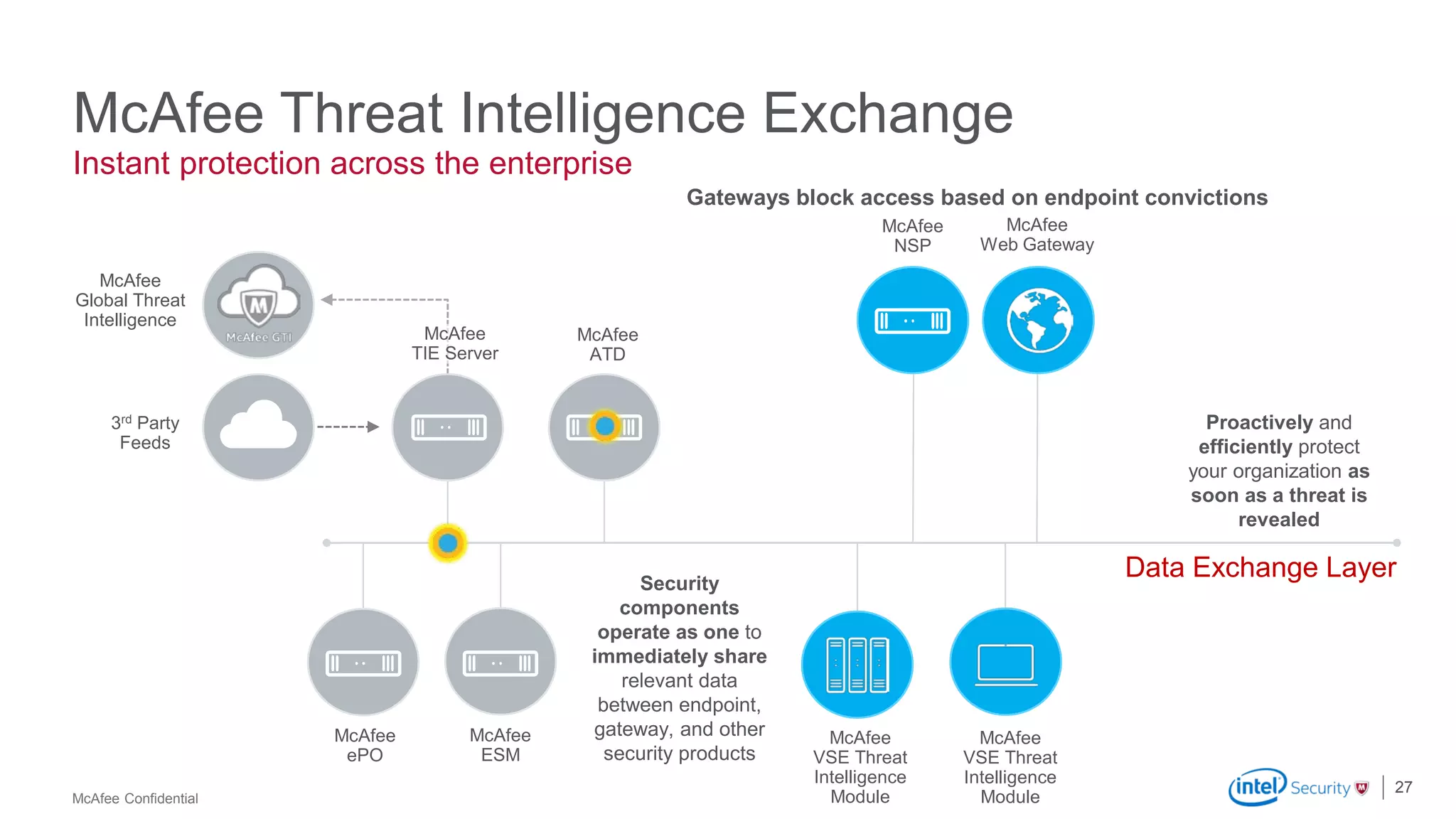
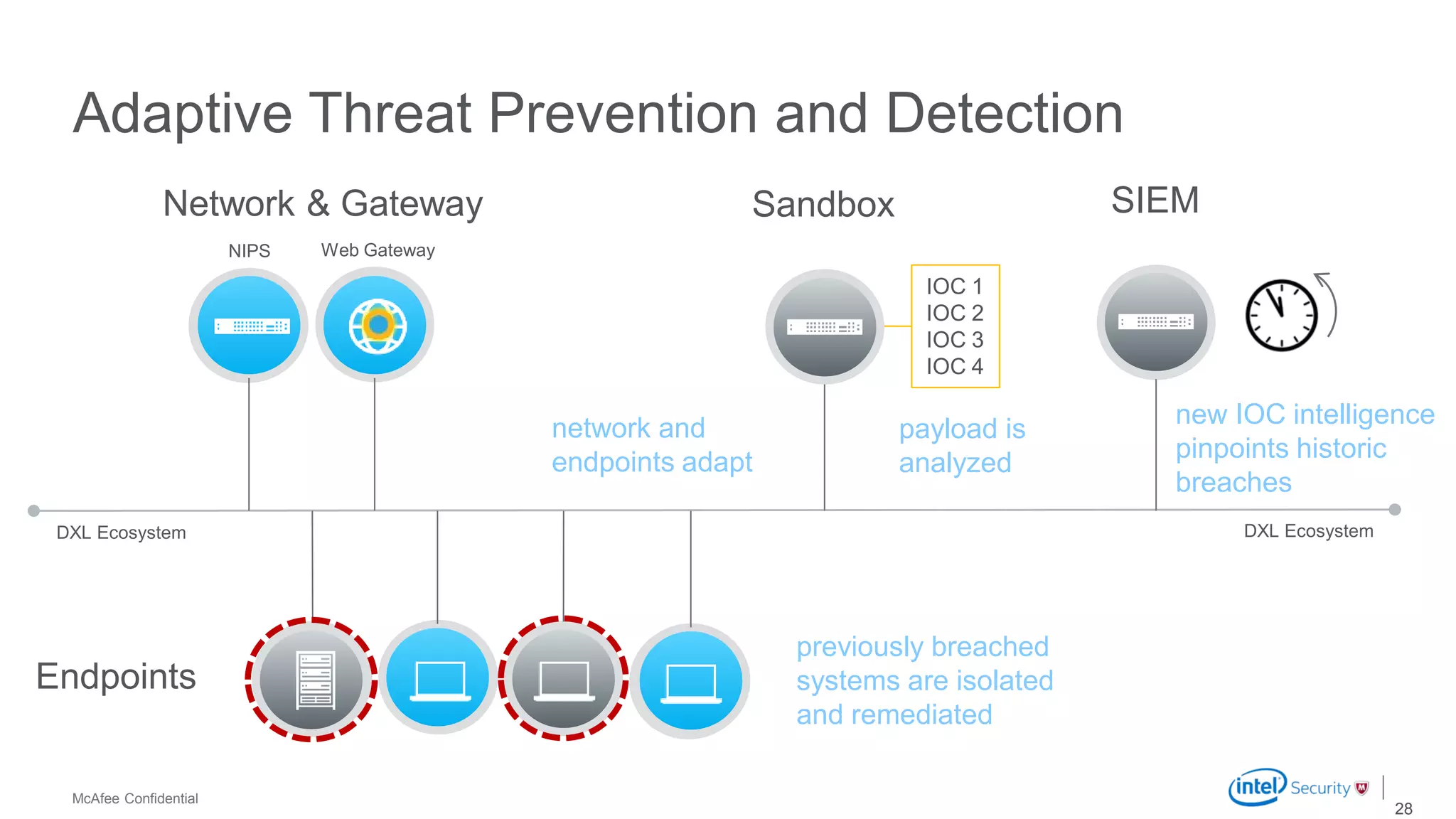
McAfee Advanced Threat Defense is a comprehensive solution that uses dynamic analysis, static code analysis, and machine learning to detect advanced malware. It analyzes malware behavior in real-time using emulation and deploys centrally to provide high detection accuracy and lower costs compared to other solutions. The solution integrates with other McAfee products to form a coordinated defense that rapidly shares threat intelligence across the enterprise to immediately block threats.