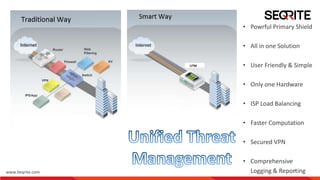
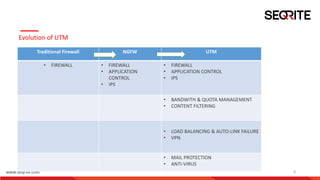
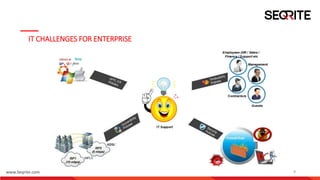
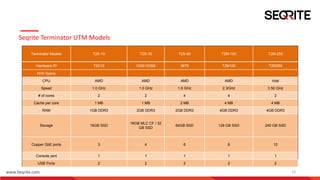
The document discusses gateway-level protection and the importance of Unified Threat Management (UTM) in enhancing network security for enterprises. It outlines the functions of firewalls, the advantages of UTM, and how Seqrite's solutions, including the Seqrite Terminator, offer comprehensive protection against various cyber threats. Additionally, it details the features, models, and management capabilities of UTM systems.