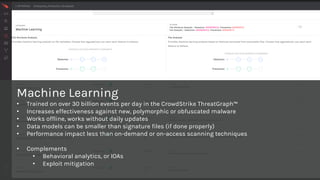
This document summarizes CrowdStrike's endpoint security product Falcon and argues that it provides more effective protection than legacy antivirus solutions. It notes that antivirus has an efficacy rate of only 45% against modern threats and is ineffective at stopping sophisticated attacks. CrowdStrike's Falcon uses techniques like machine learning, IOAs, and threat intelligence to prevent a wider range of attacks while having a smaller system footprint than antivirus. It also provides detection capabilities like endpoint detection and response to eliminate attack dwell time. The document aims to convince readers to replace their legacy antivirus with CrowdStrike's Falcon.