Embed presentation
Download to read offline


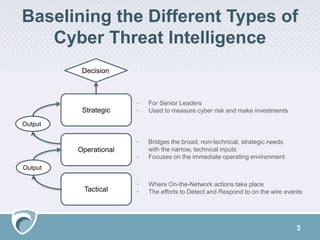
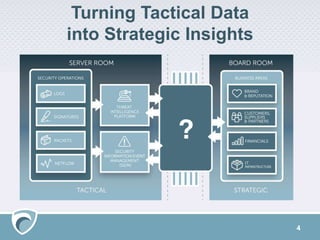



The document outlines a cyber threat intelligence solution presented by Adam Meyer, focusing on types of cyber threat intelligence: strategic for leaders and operational for immediate operations. It describes the Surfwatch Labs threat intelligence stack, which offers services like cyber risk management, fraud prevention, and brand protection through various data sources. The presentation also includes a Q&A section and resources for further engagement with Surfwatch Labs offerings.





