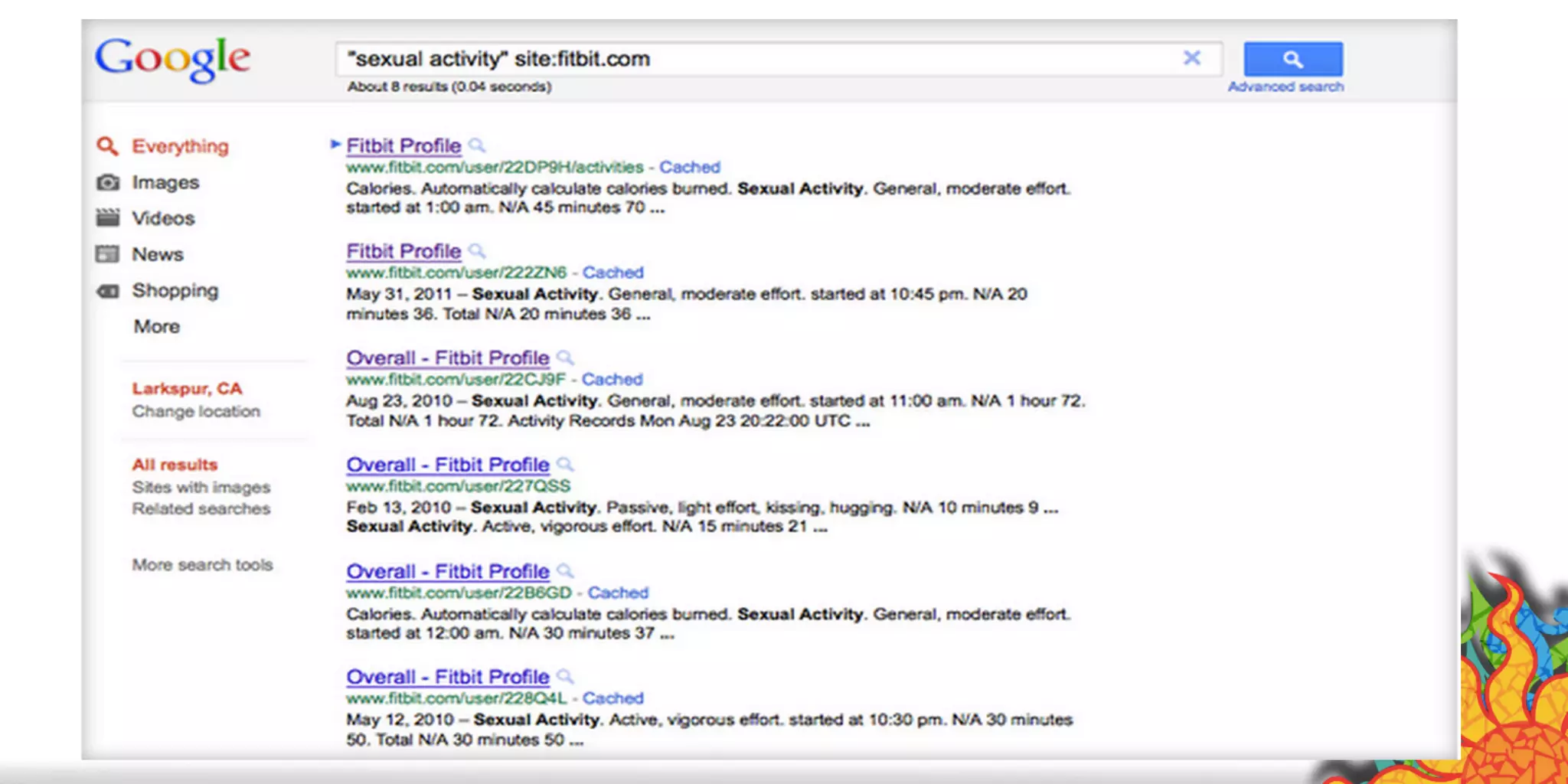
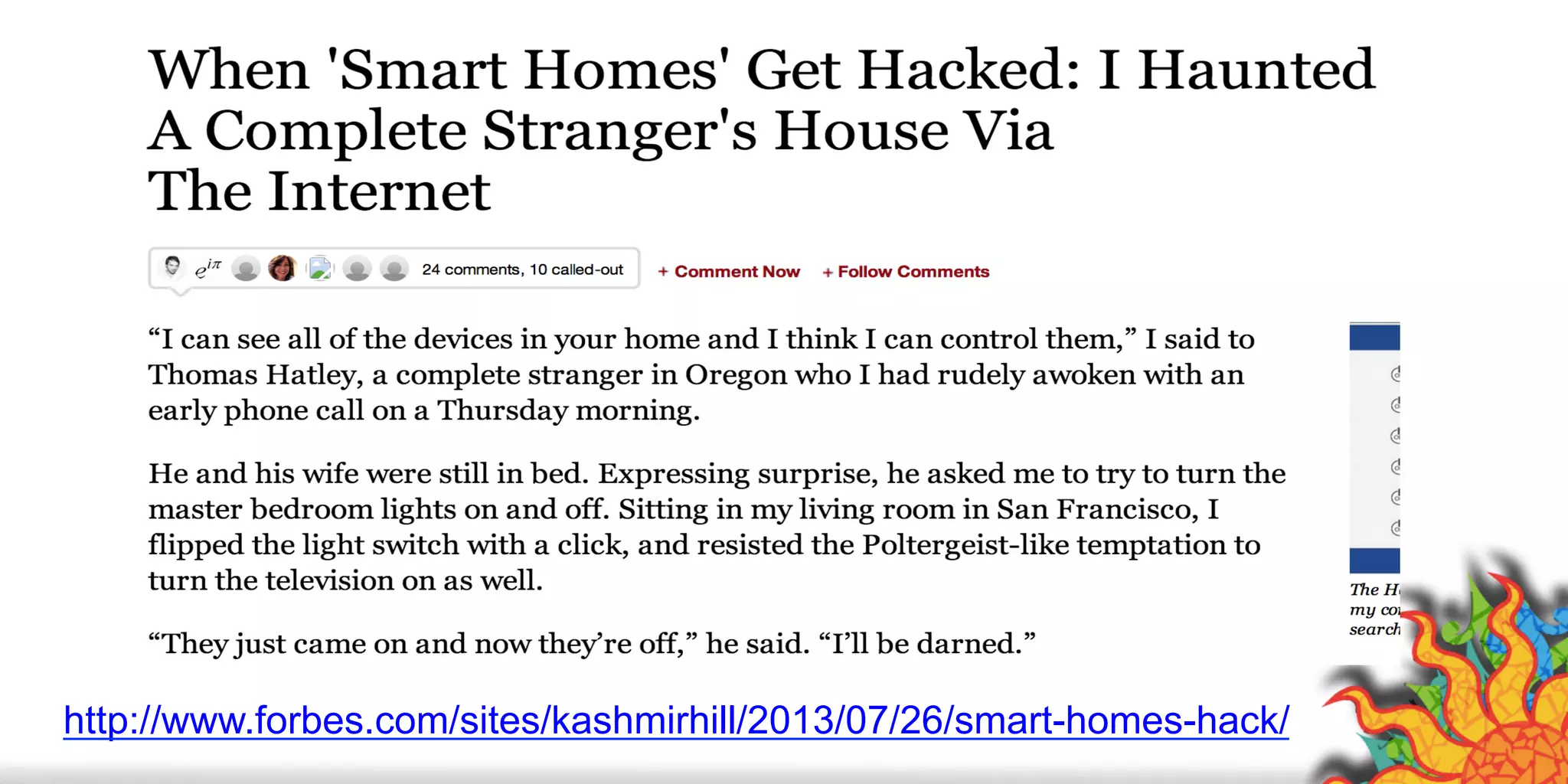
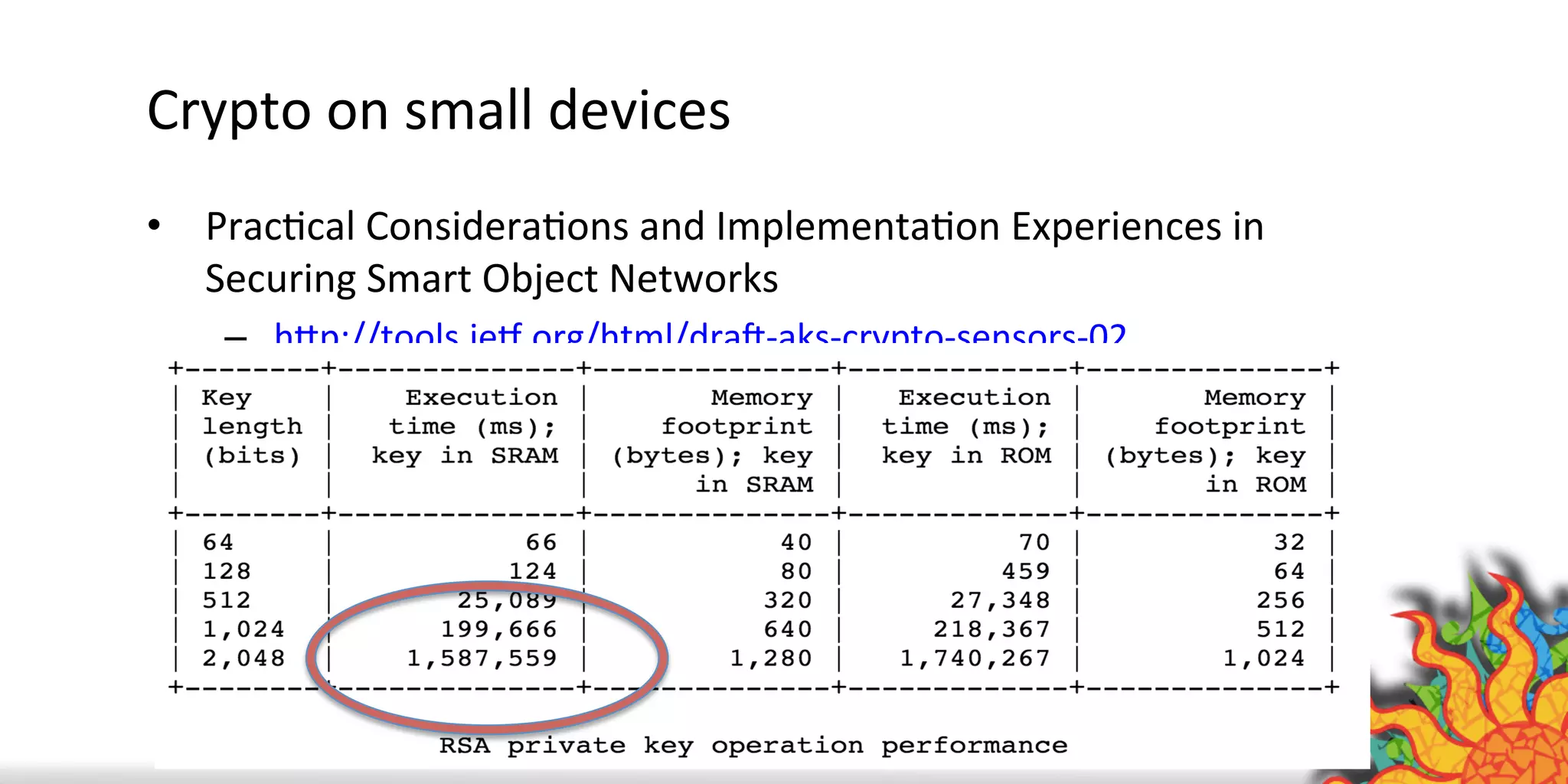
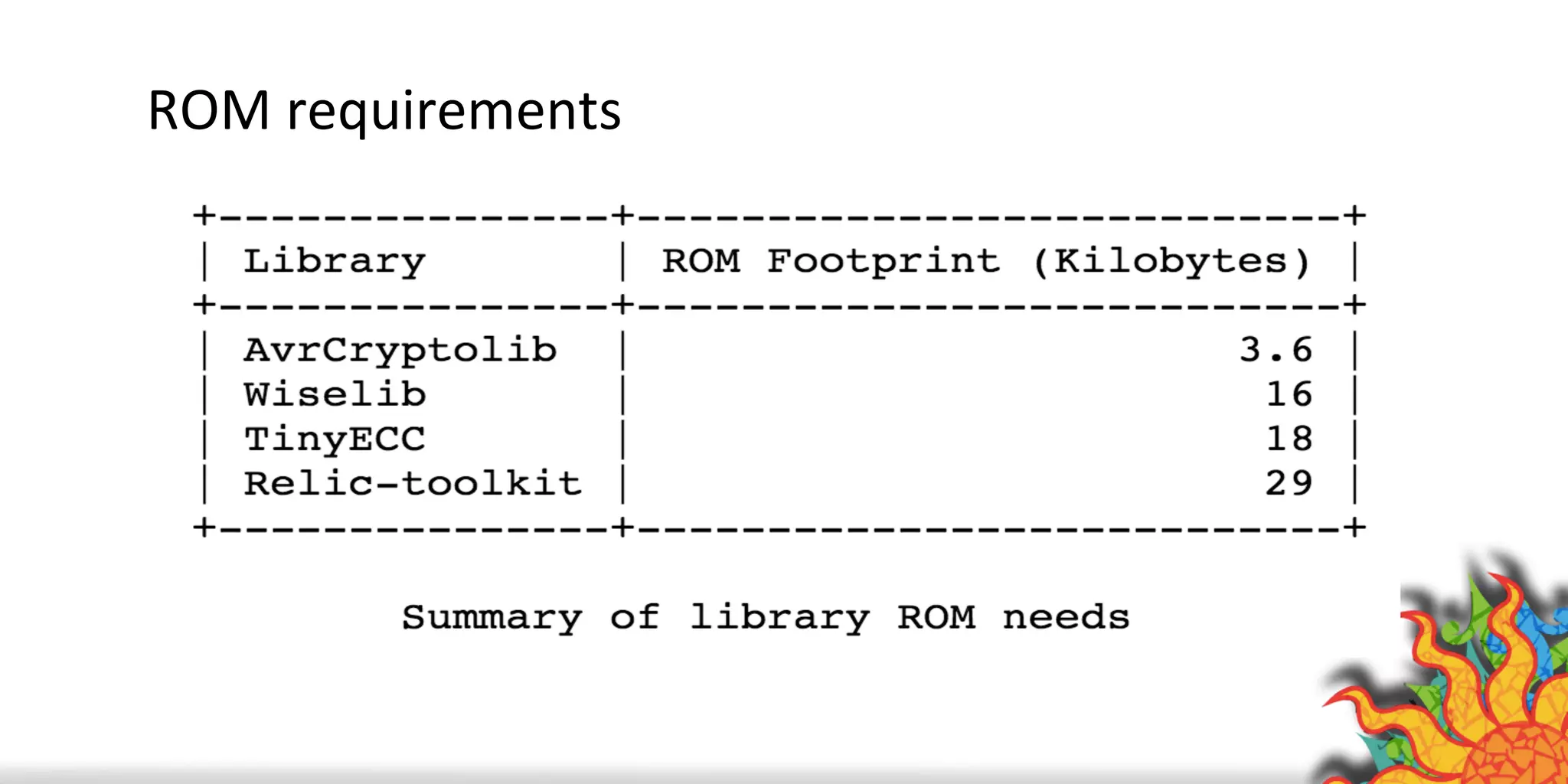
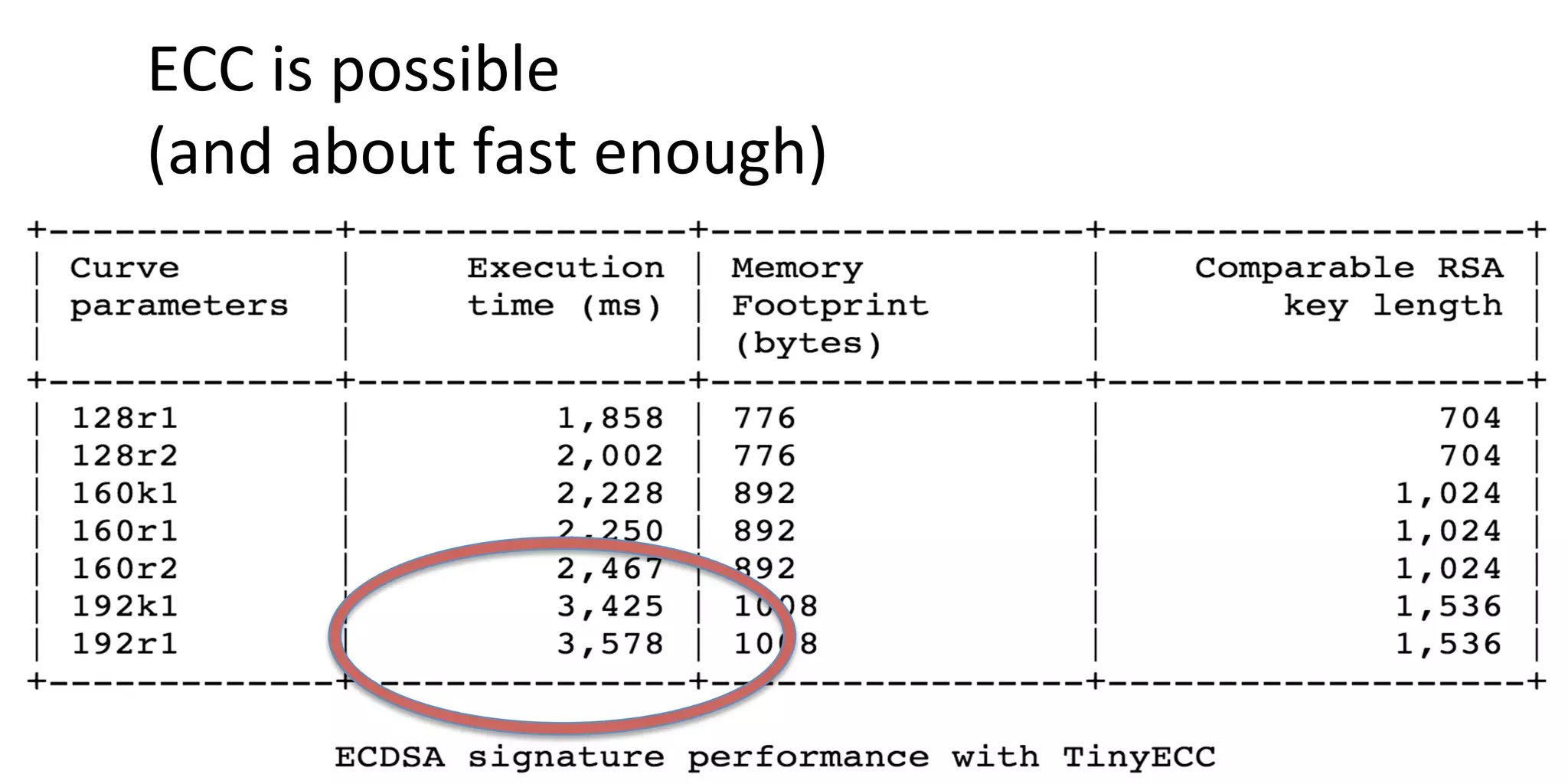
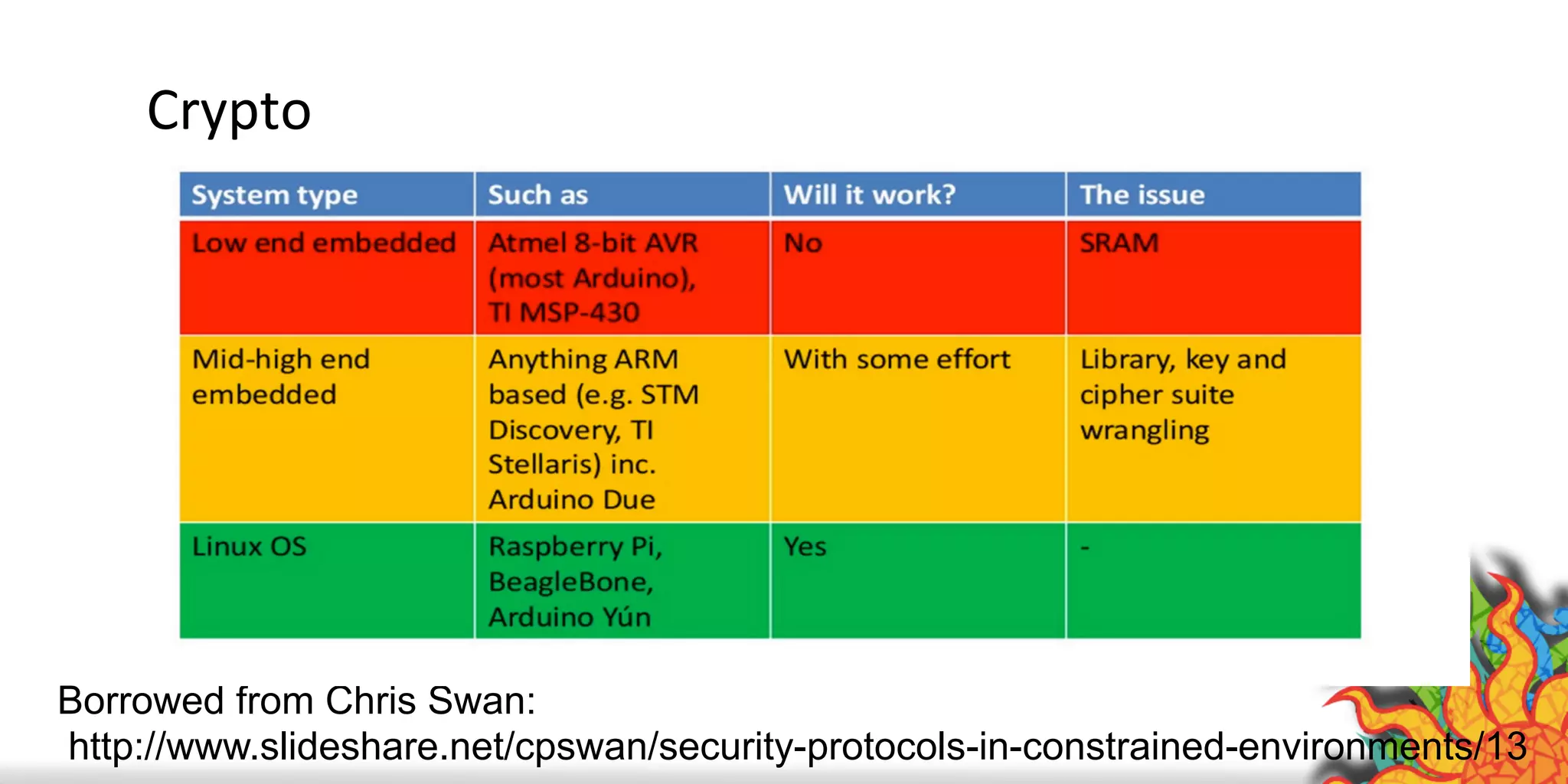
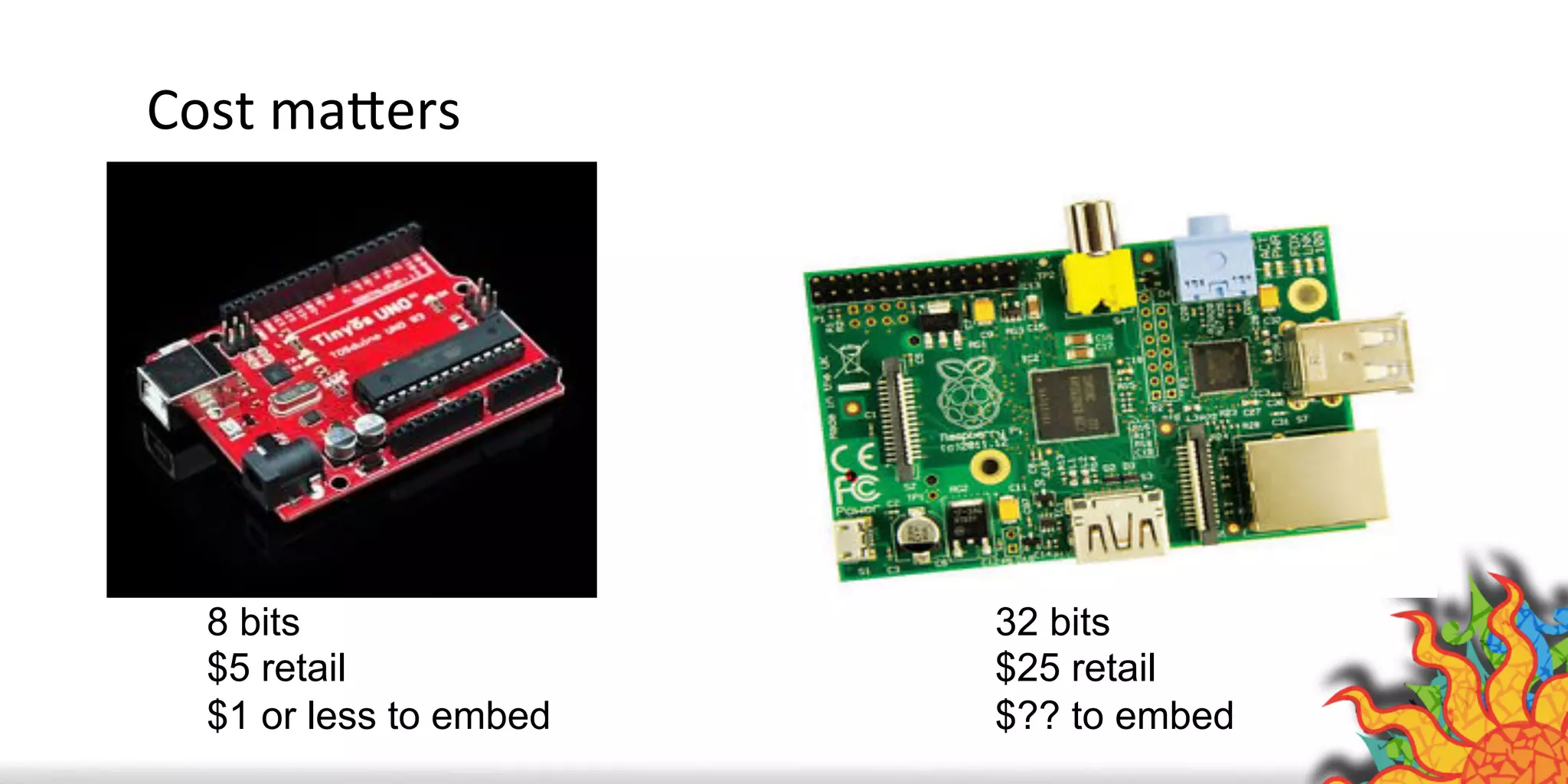
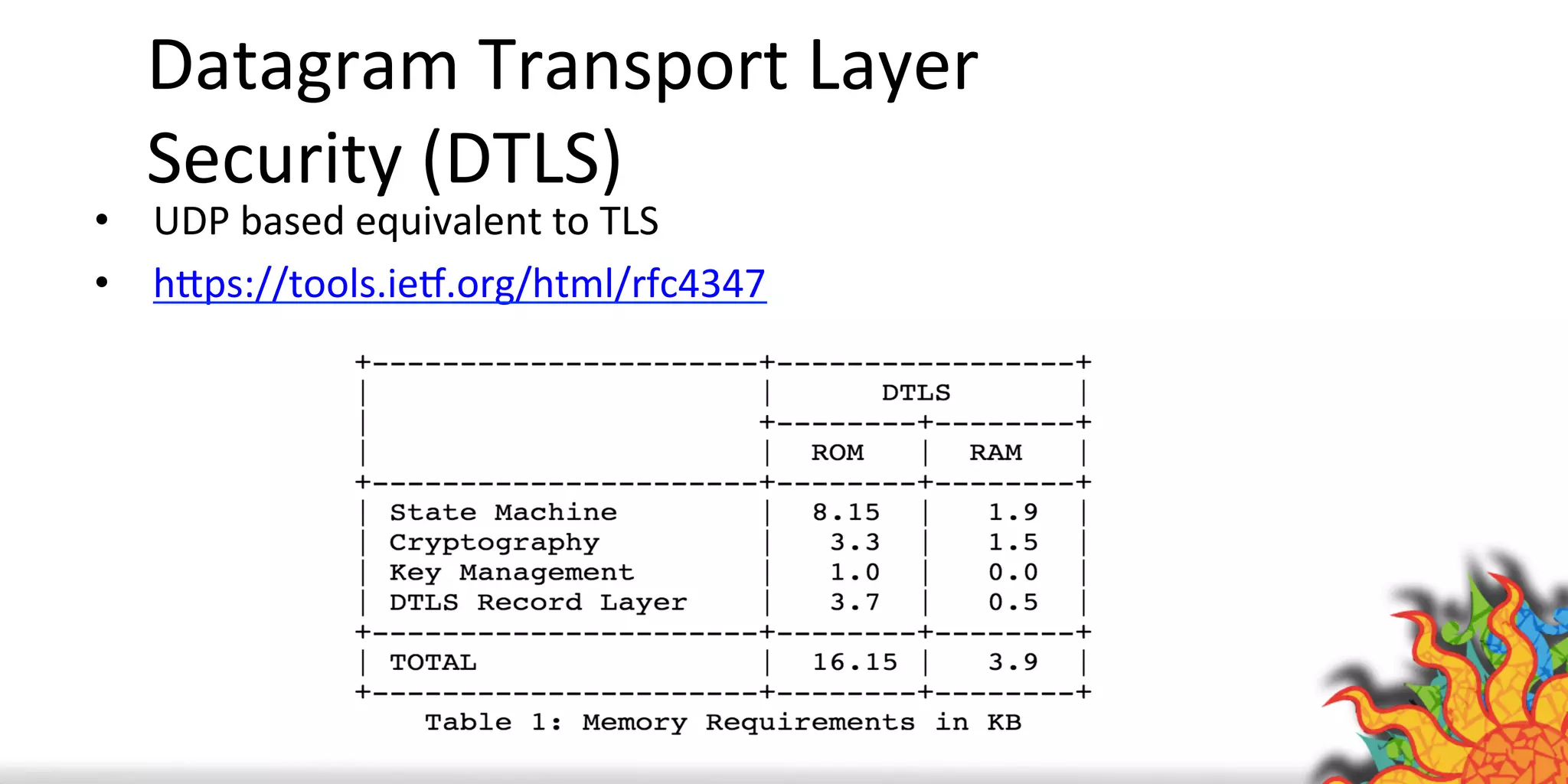
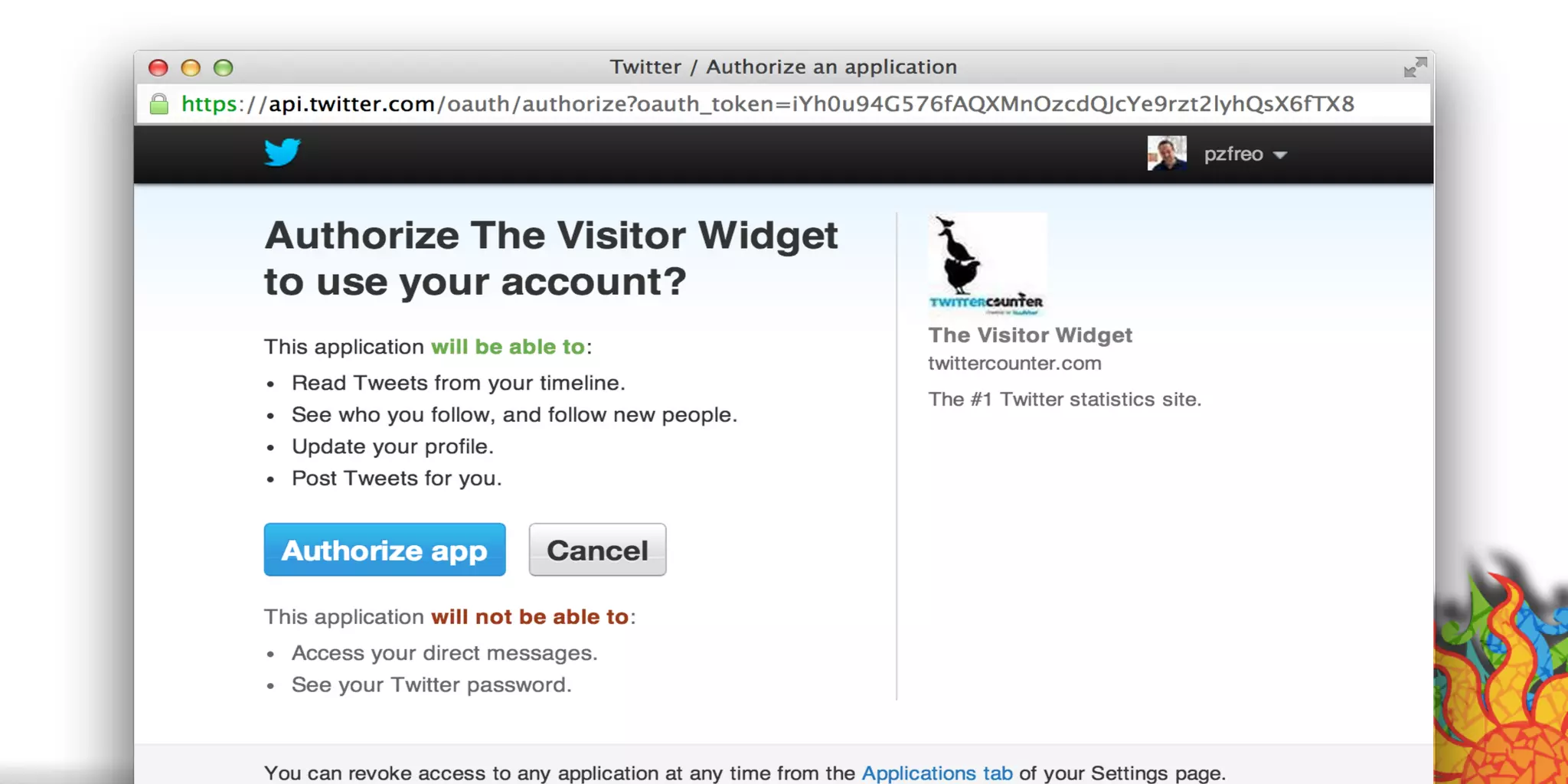
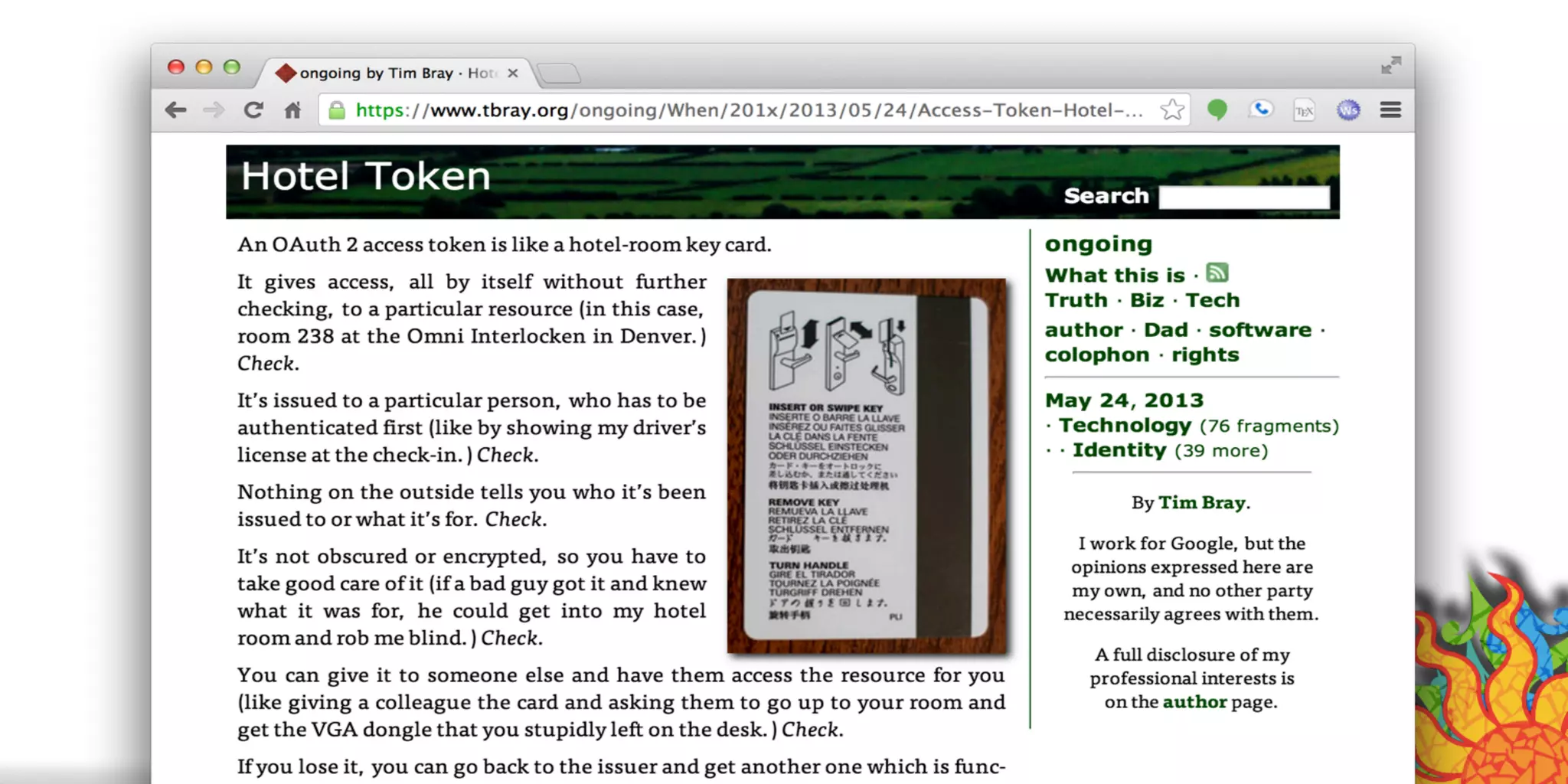
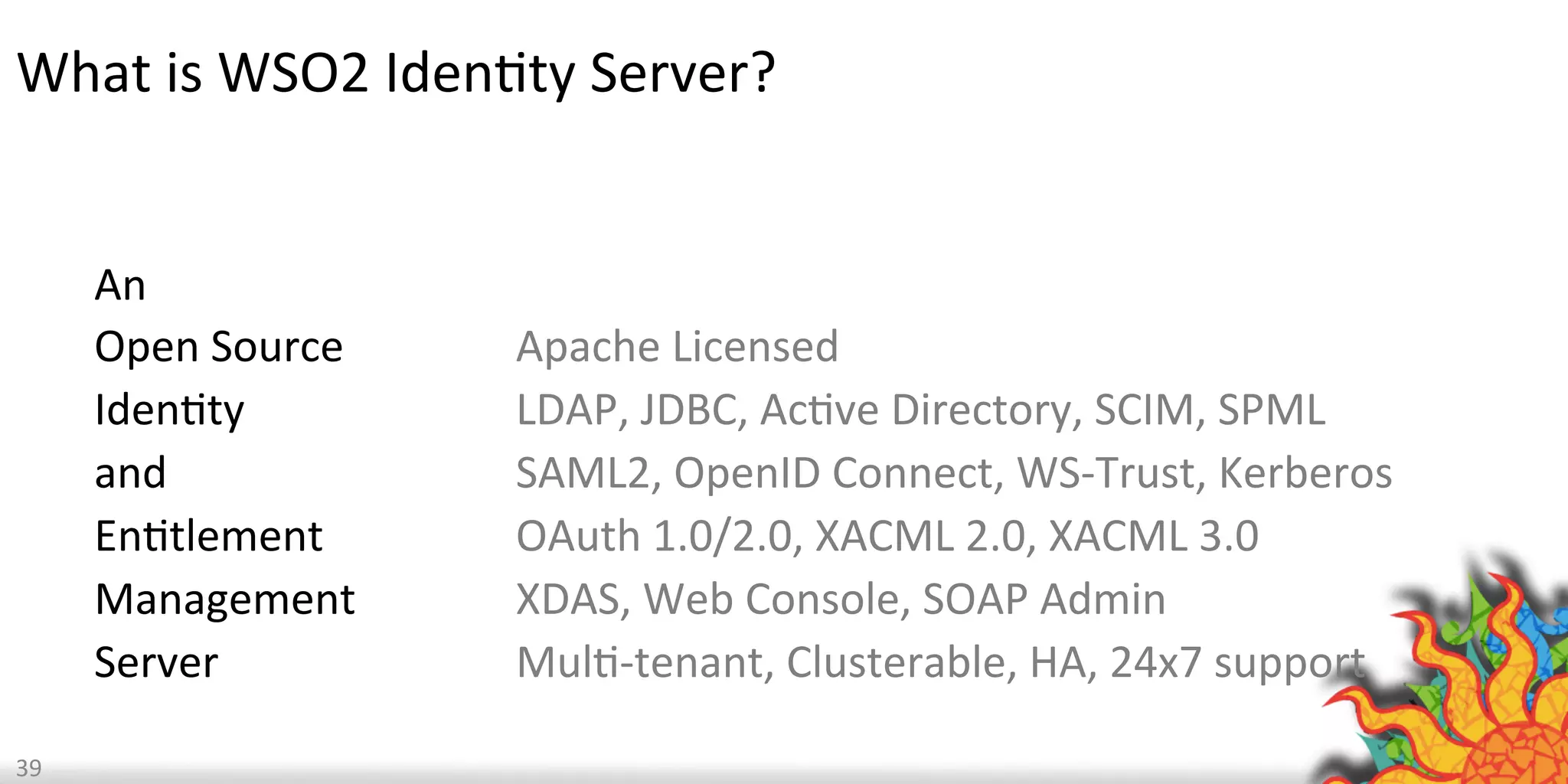
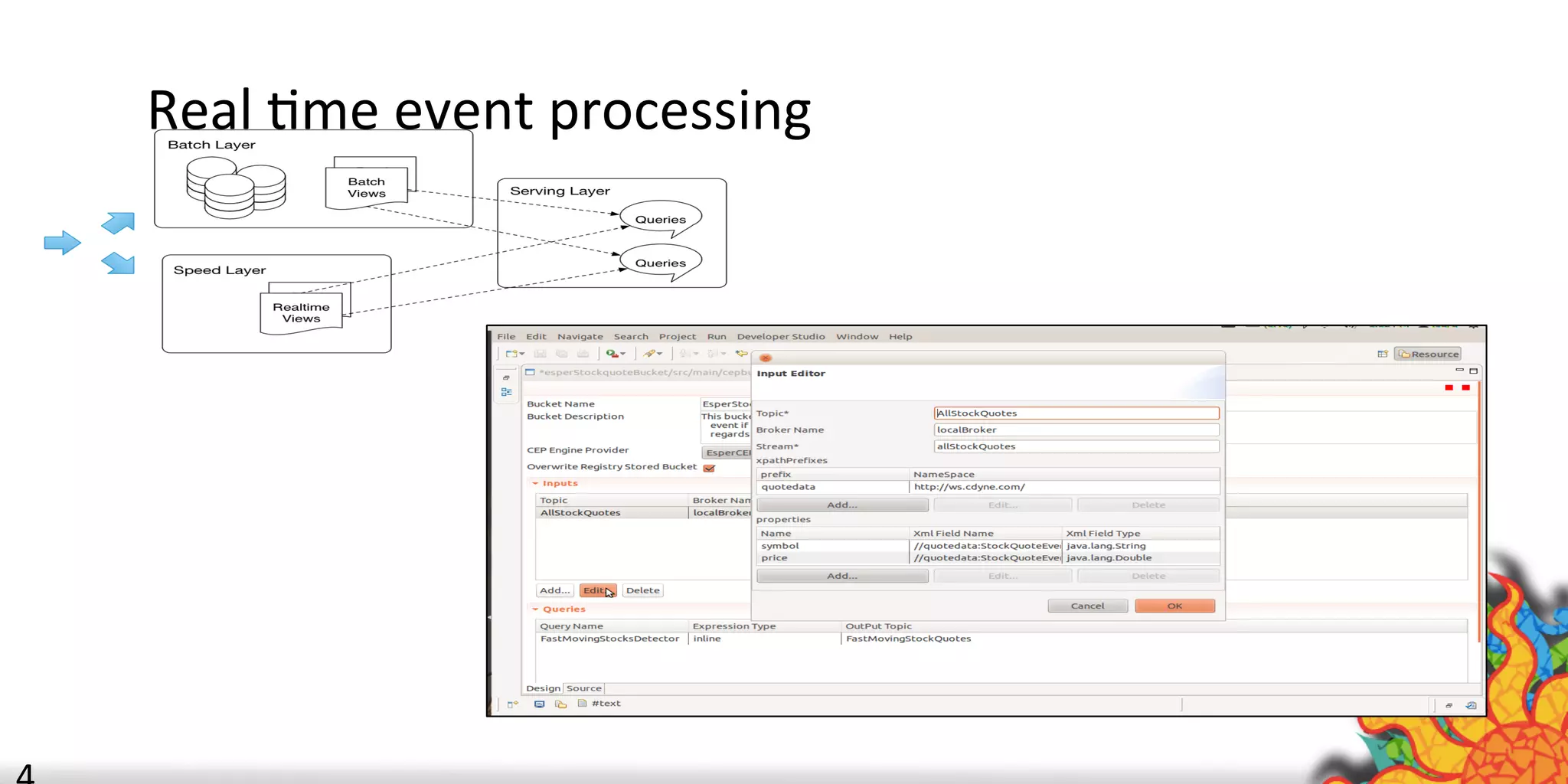
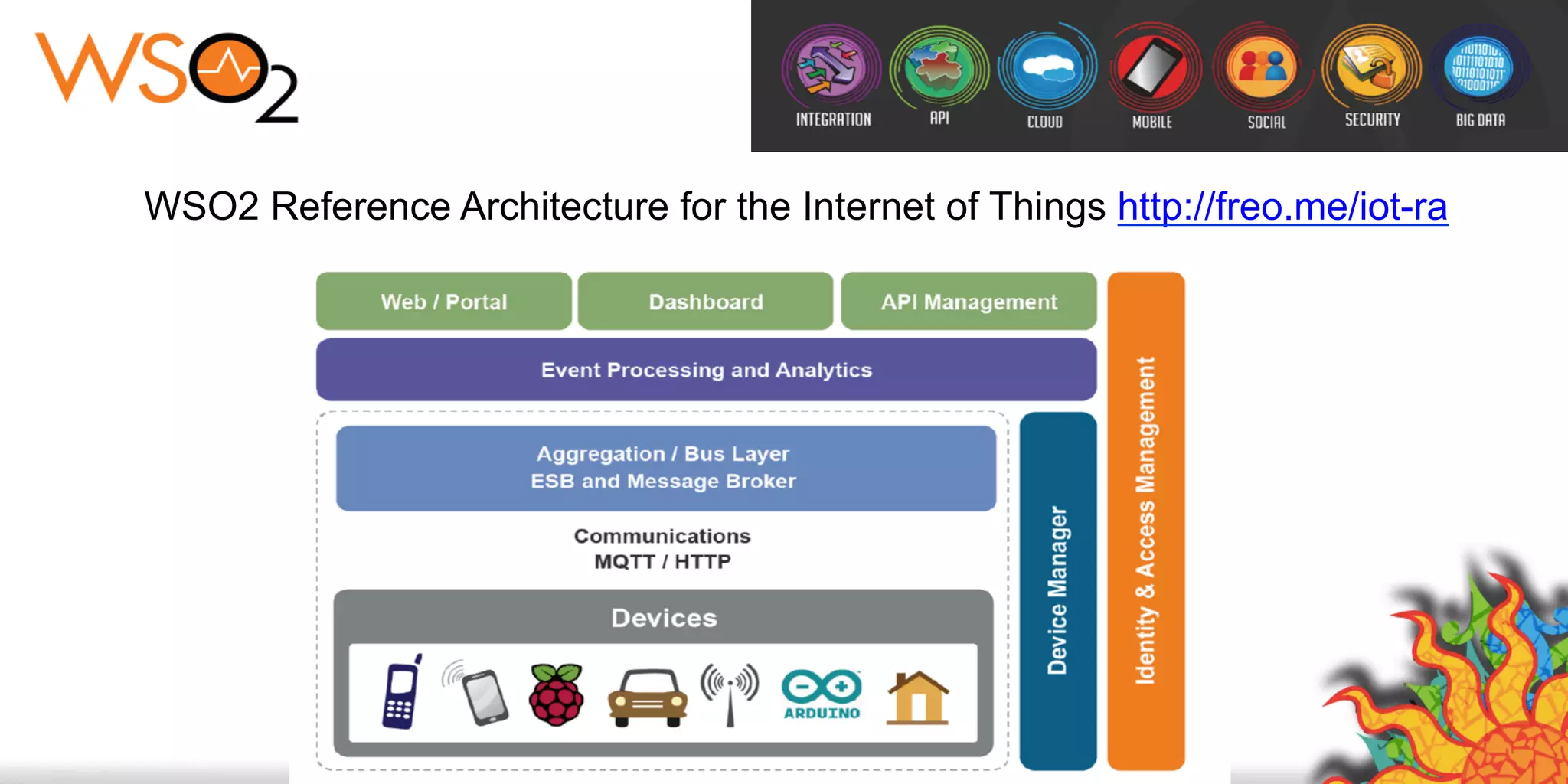
The document discusses security challenges for internet of things (IoT) devices. It outlines three rules for IoT security: don't be dumb, think about what's different from traditional internet security, and be smart. What's different about IoT includes the long lifespan of devices which makes updates difficult, limited capabilities of small devices, and highly personal user data. The document recommends not relying on security through obscurity and considering cryptography options that can work on small devices like ECC. It also discusses secure protocols and identity management through federated identity as an option for authentication and authorization with IoT devices.