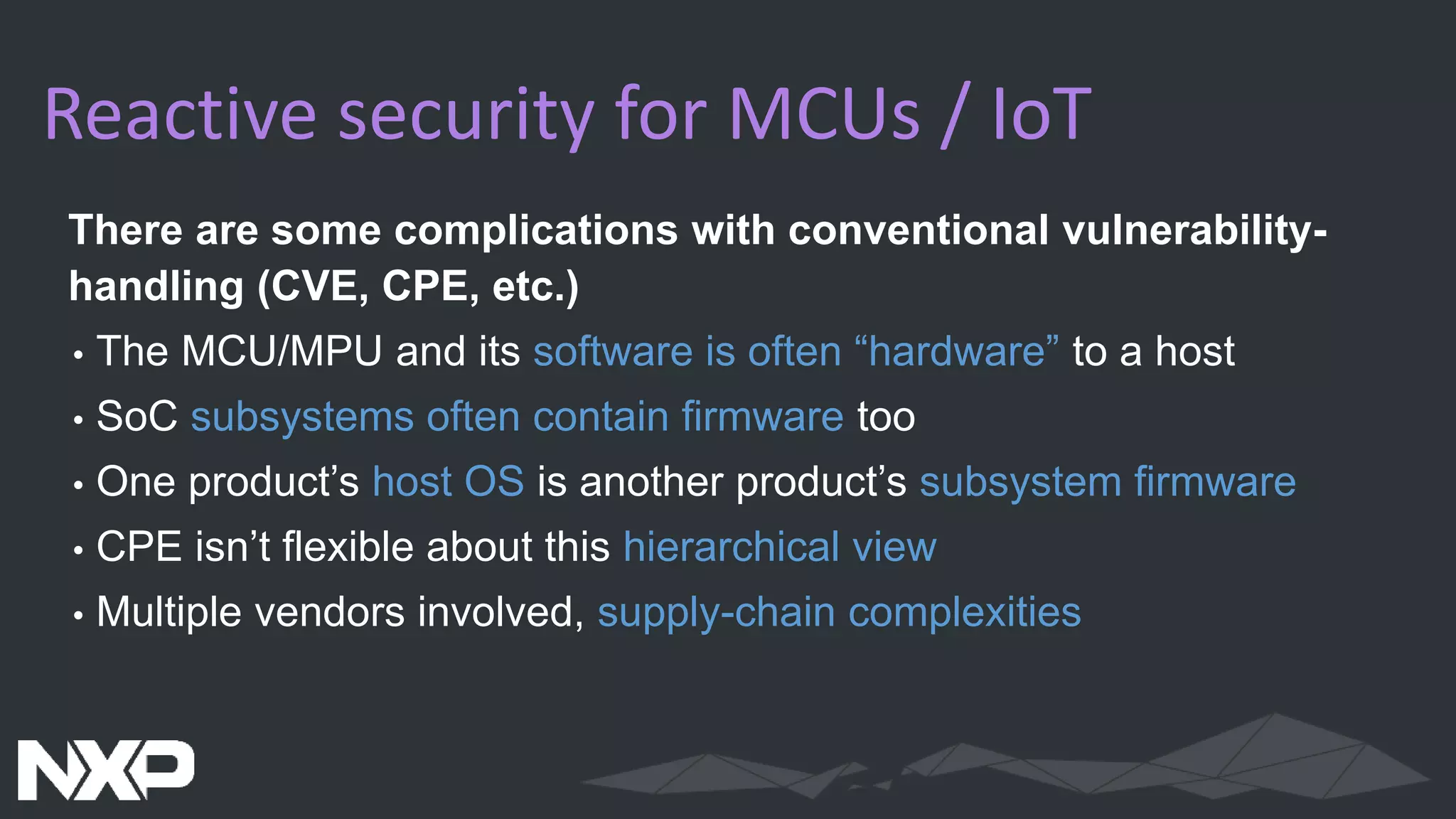
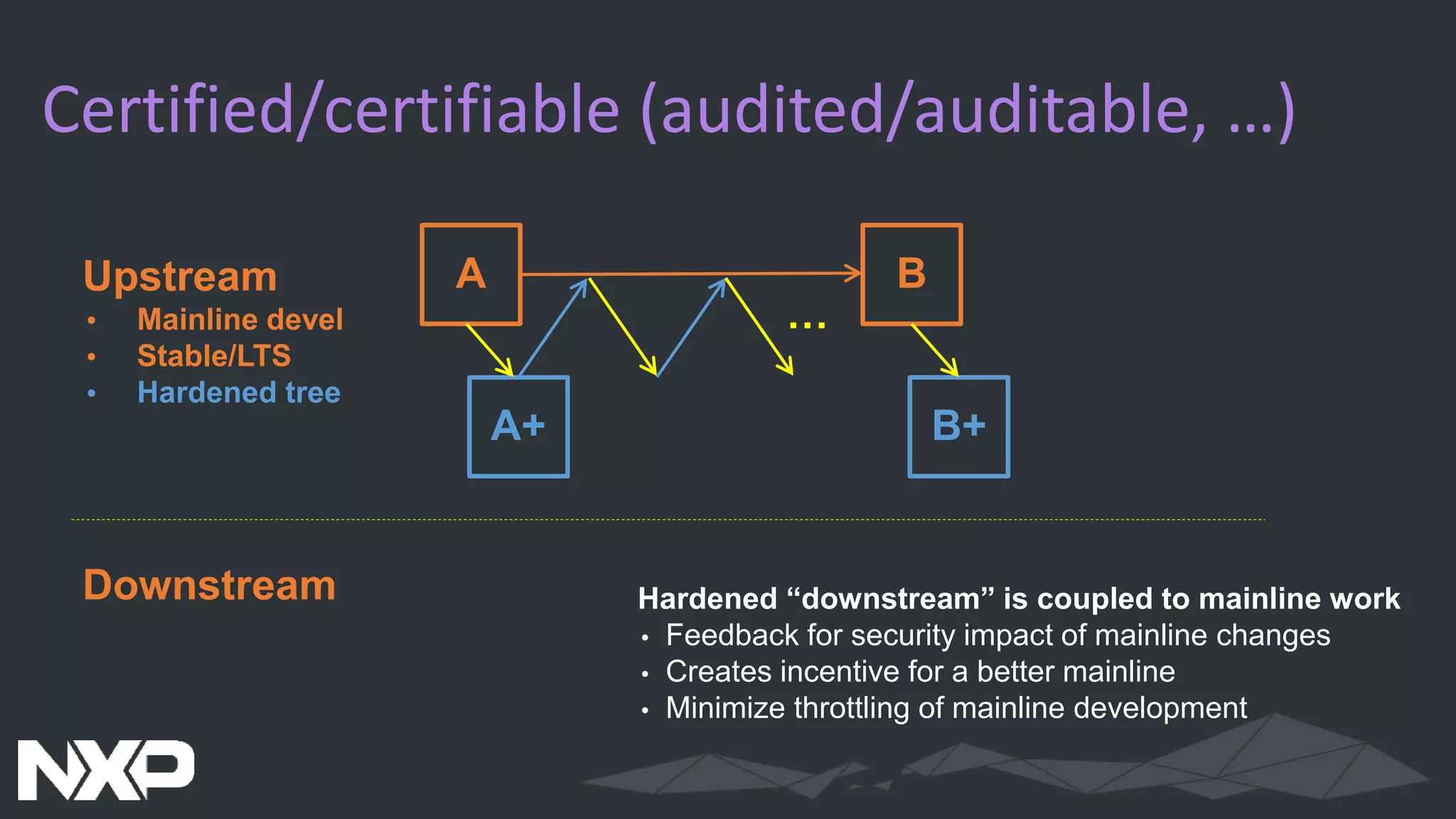
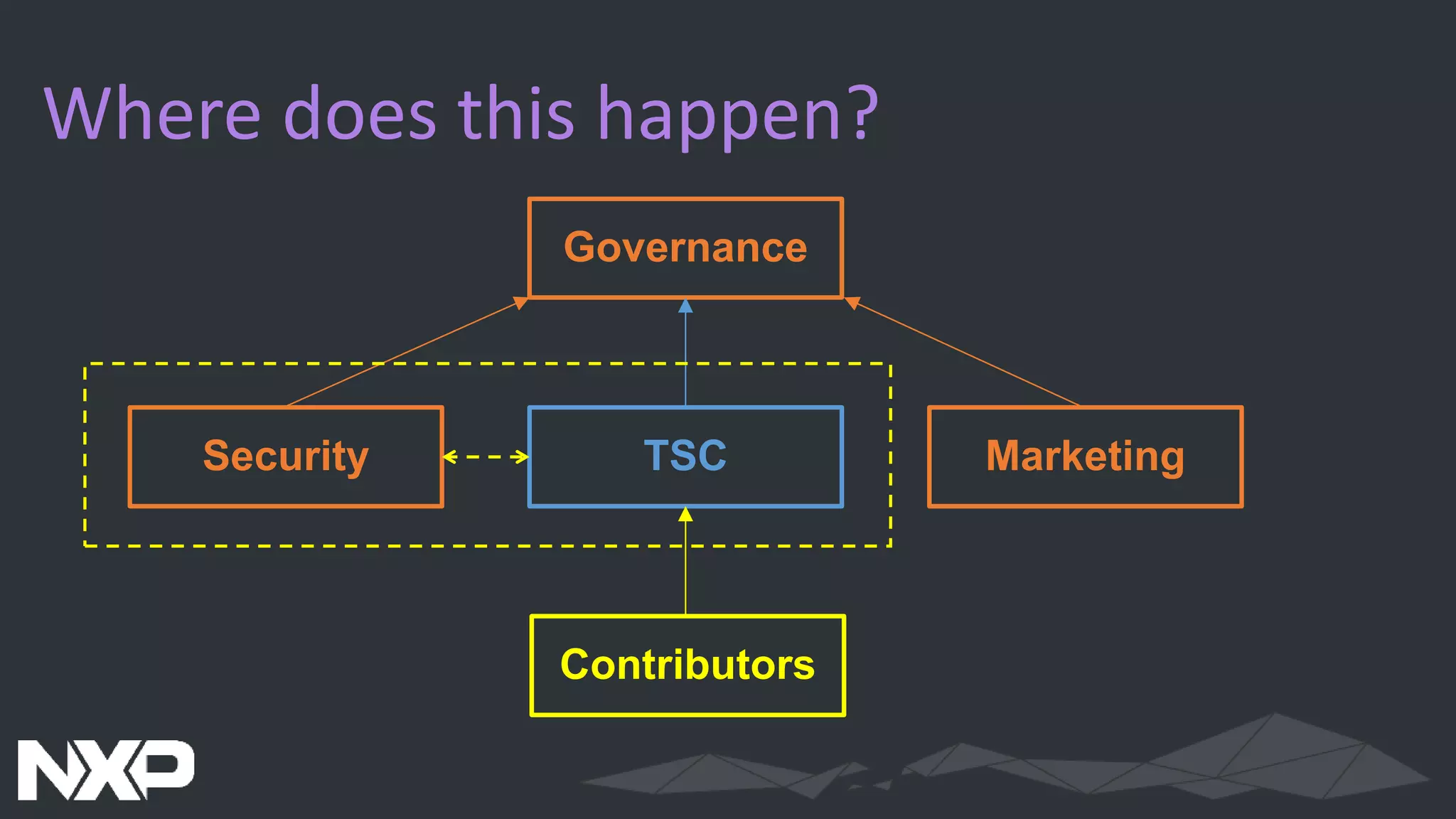
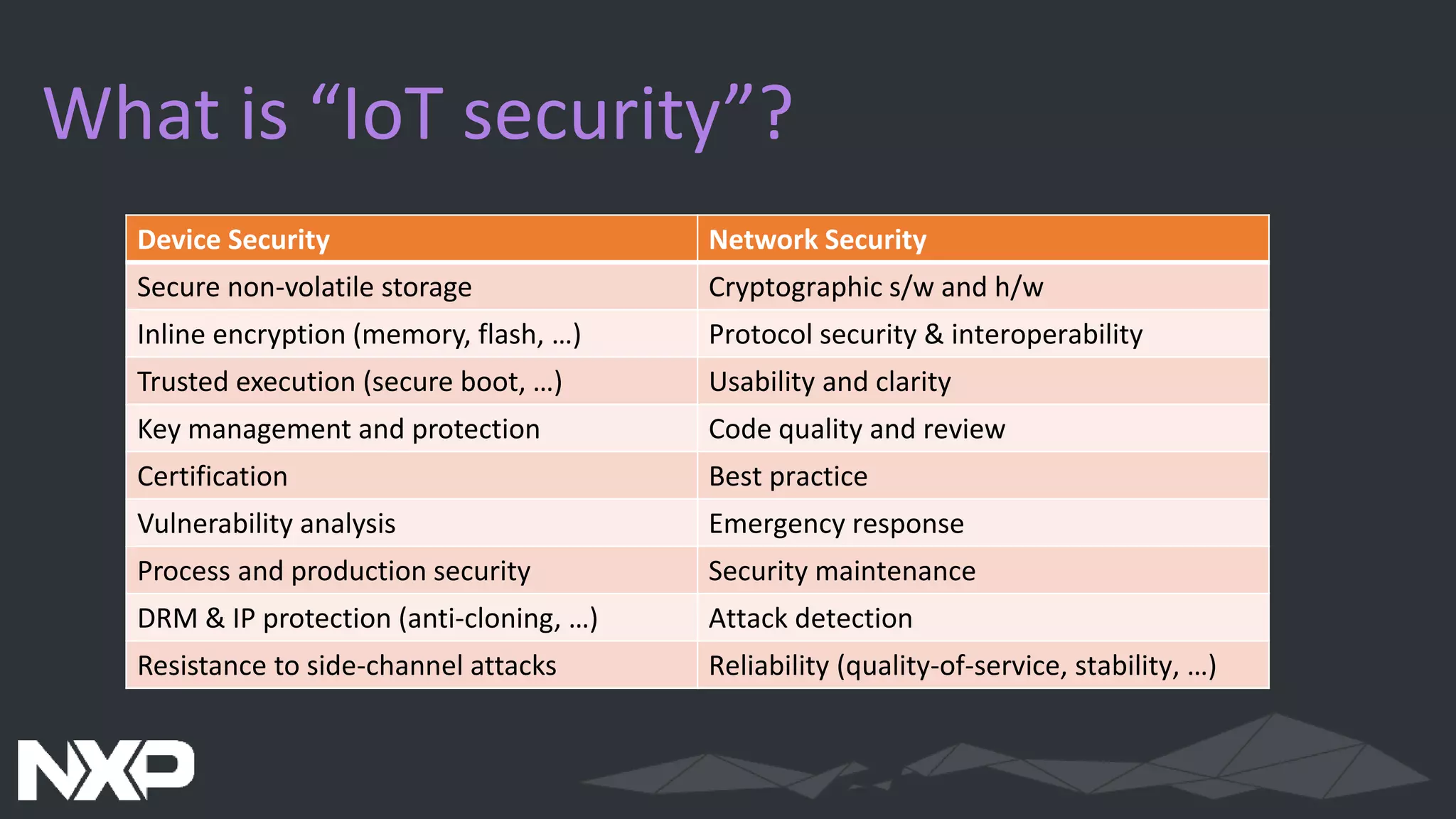
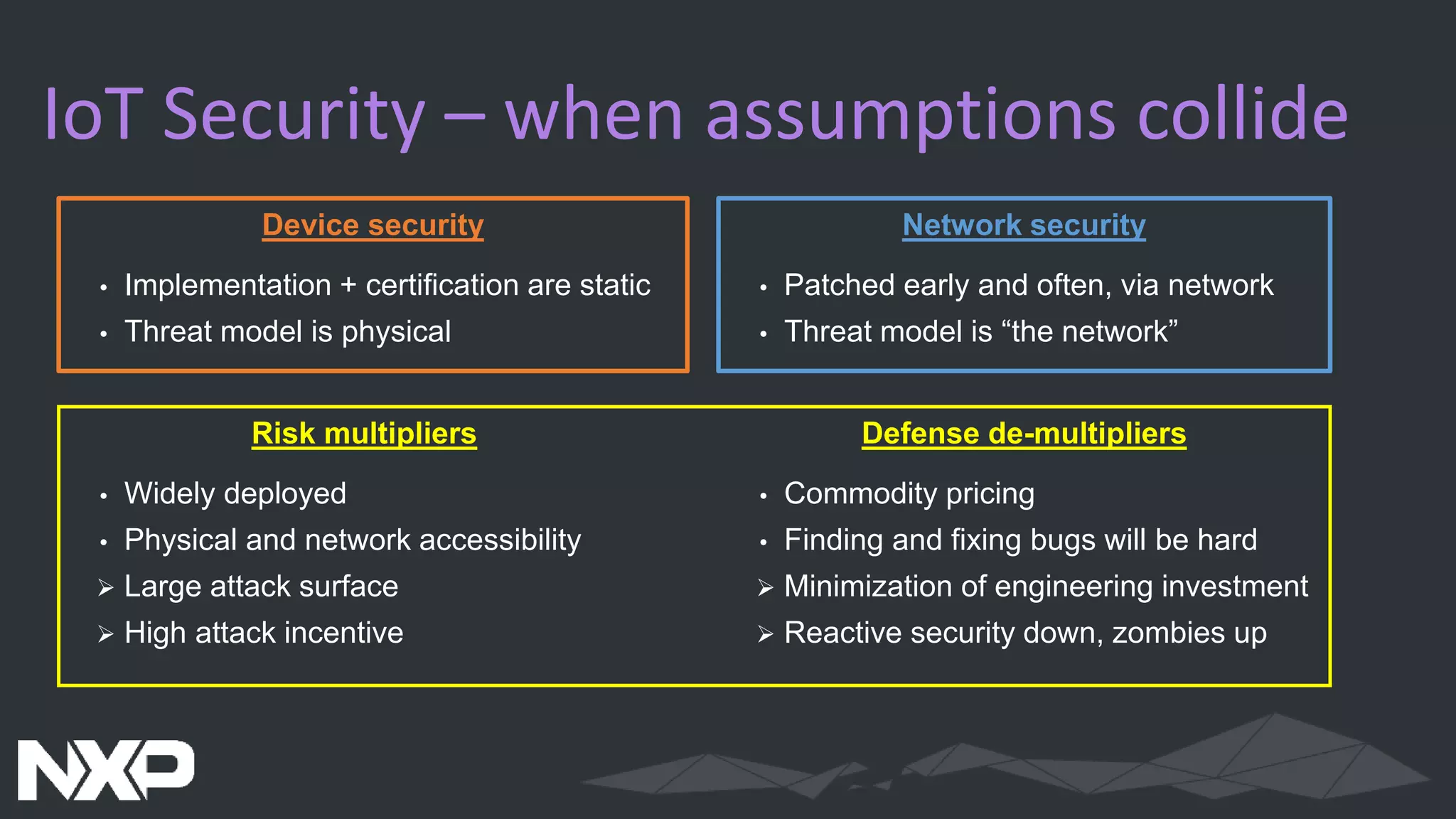
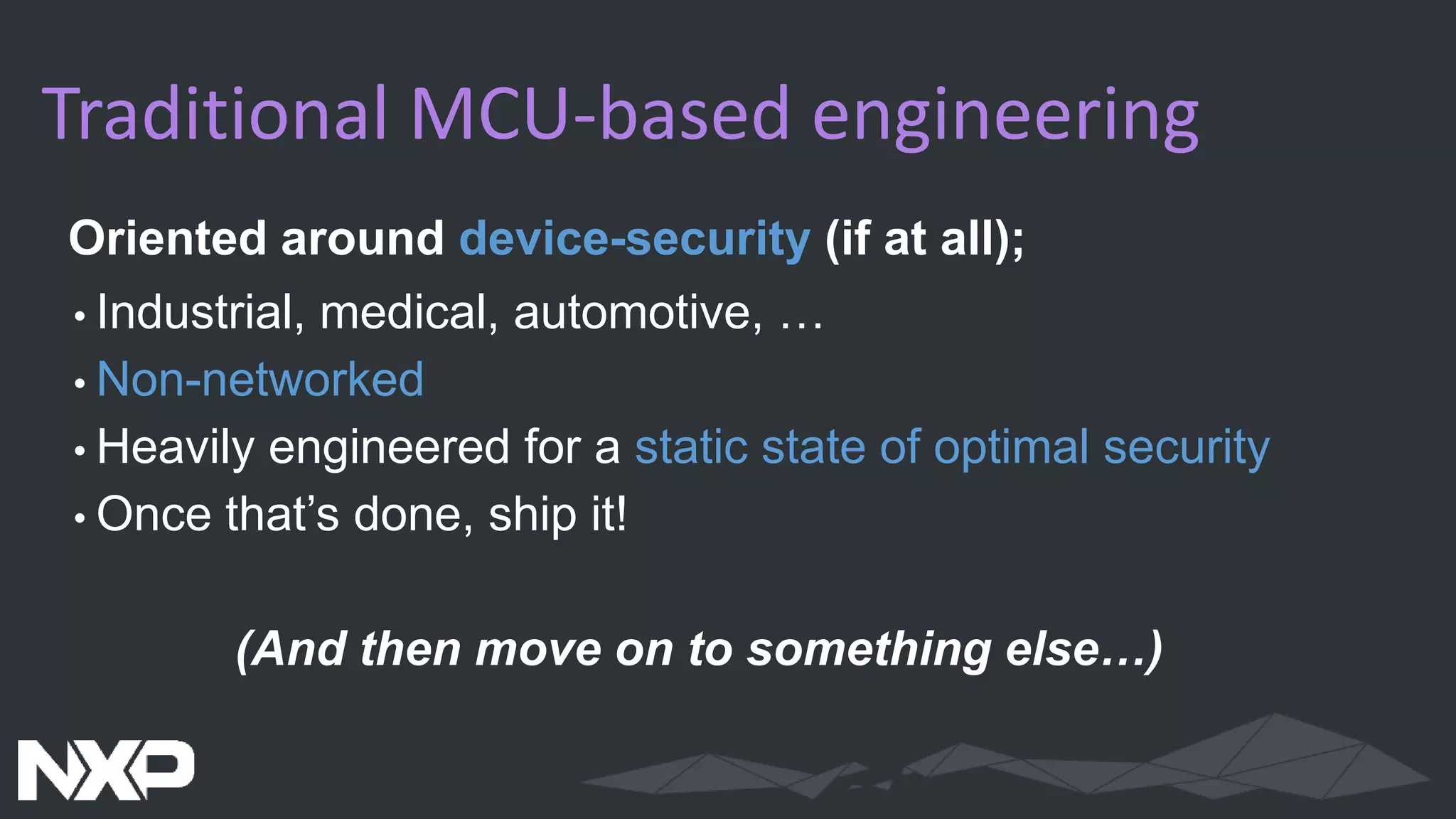
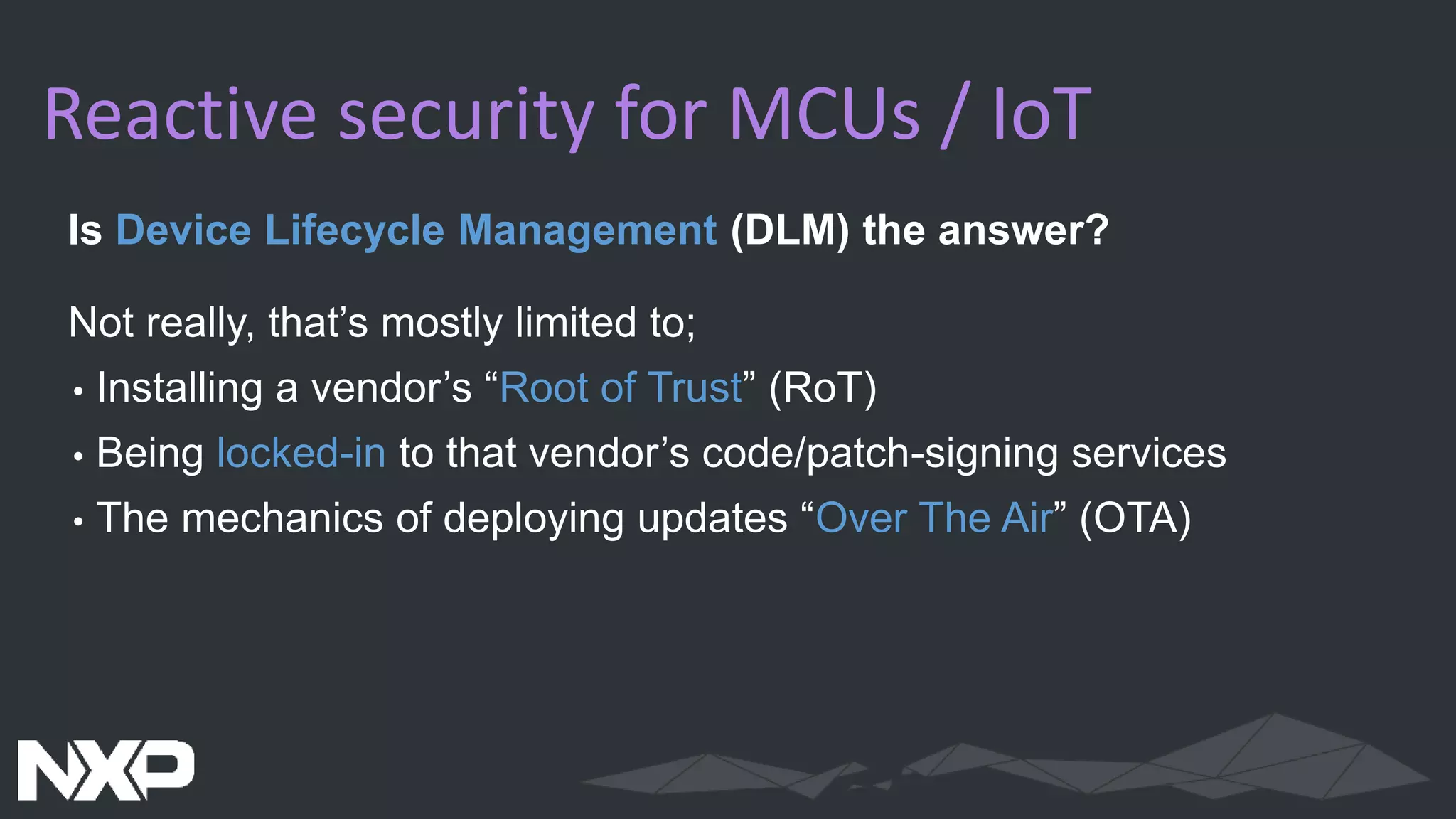
The document discusses IoT security in relation to the Zephyr project, highlighting the complexity and evolving nature of security in IoT devices and networks. It emphasizes the need for adaptable security measures, including lifecycle management and vulnerability handling, while advocating for best practices and certification processes. The document also outlines the role of Zephyr as an open-source RTOS aiming to maintain production-worthy security standards and respond effectively to emerging threats.














![Reactive security for MCUs / IoT
Reactive security is well-understood in traditional networked
computing;
• Servers
• High-end networking
• Smart-phones
• Desktops
• […]
Can we adopt the same methods?](https://image.slidesharecdn.com/linaroconnectlas2016-zephyr-160928170201/75/LAS16-300K2-Geoff-Thorpe-IoT-Zephyr-30-2048.jpg)