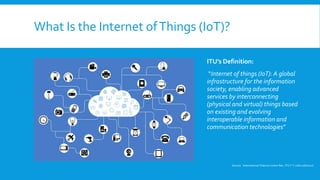
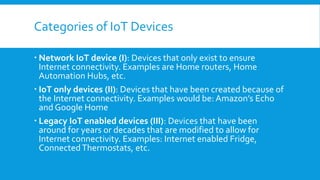
This document discusses Internet of Things (IoT) security. It defines IoT as interconnecting physical devices via communication technologies. It categorizes IoT devices and lists common technology vendors. It then describes why IoT devices are vulnerable in terms of cost, processing power, history of neglecting security, proprietary technologies, and inability to update. Examples of IoT attacks are also provided such as using webcams for DDoS attacks and hacking home routers and cars. The document concludes with recommended countermeasures like leveraging existing frameworks, segmentation, not relying on users, and building in automatic updates.