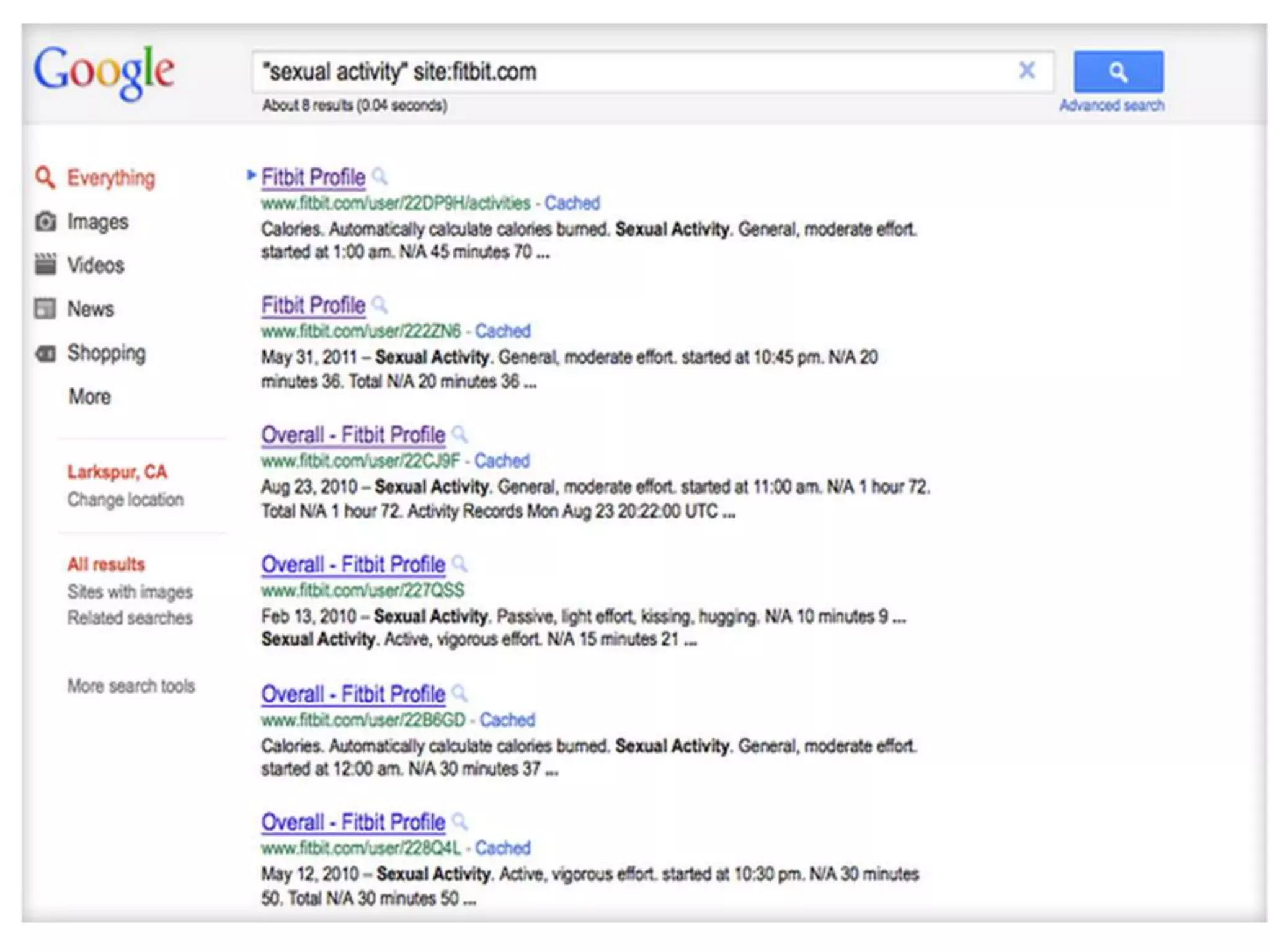
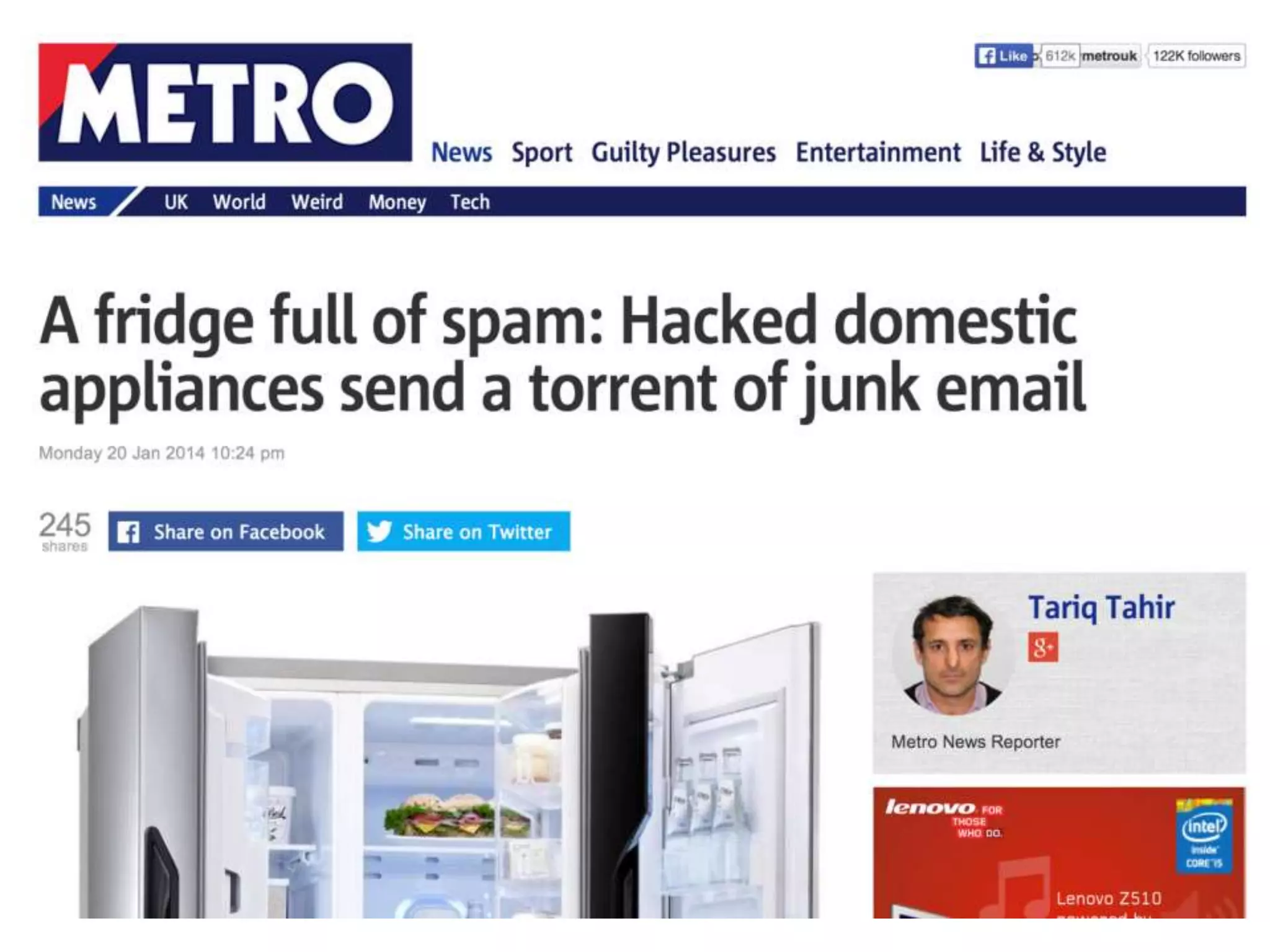
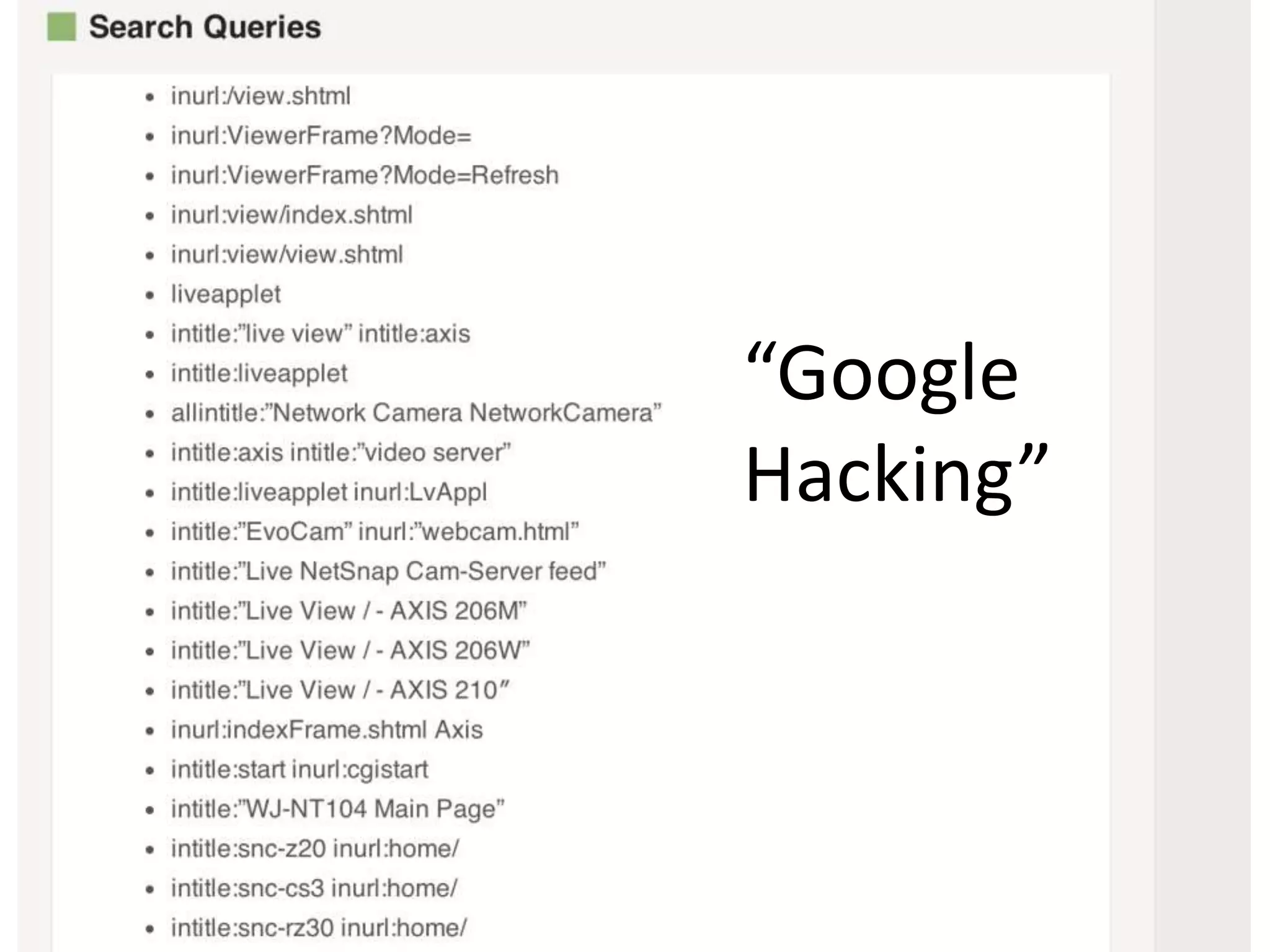
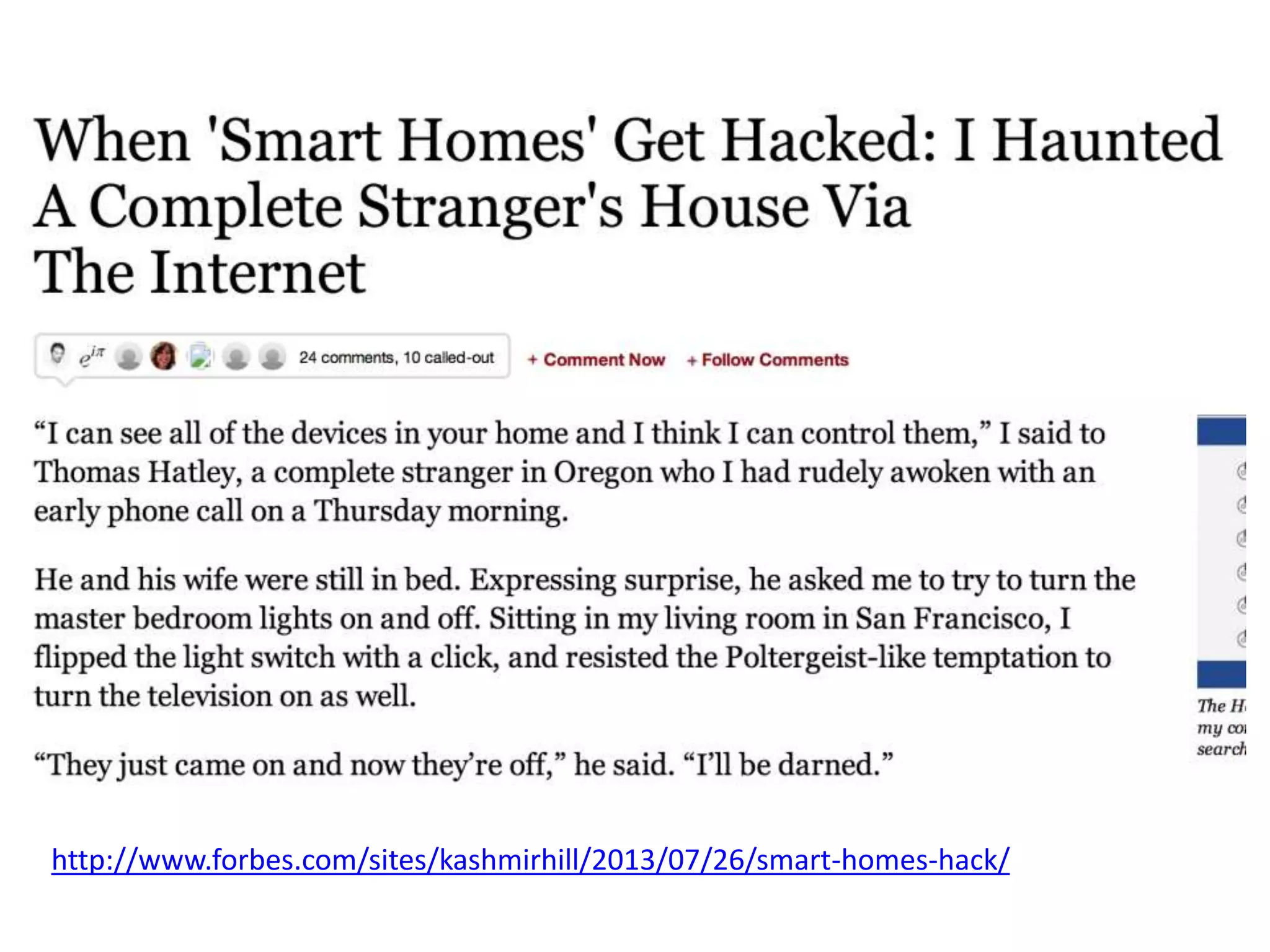
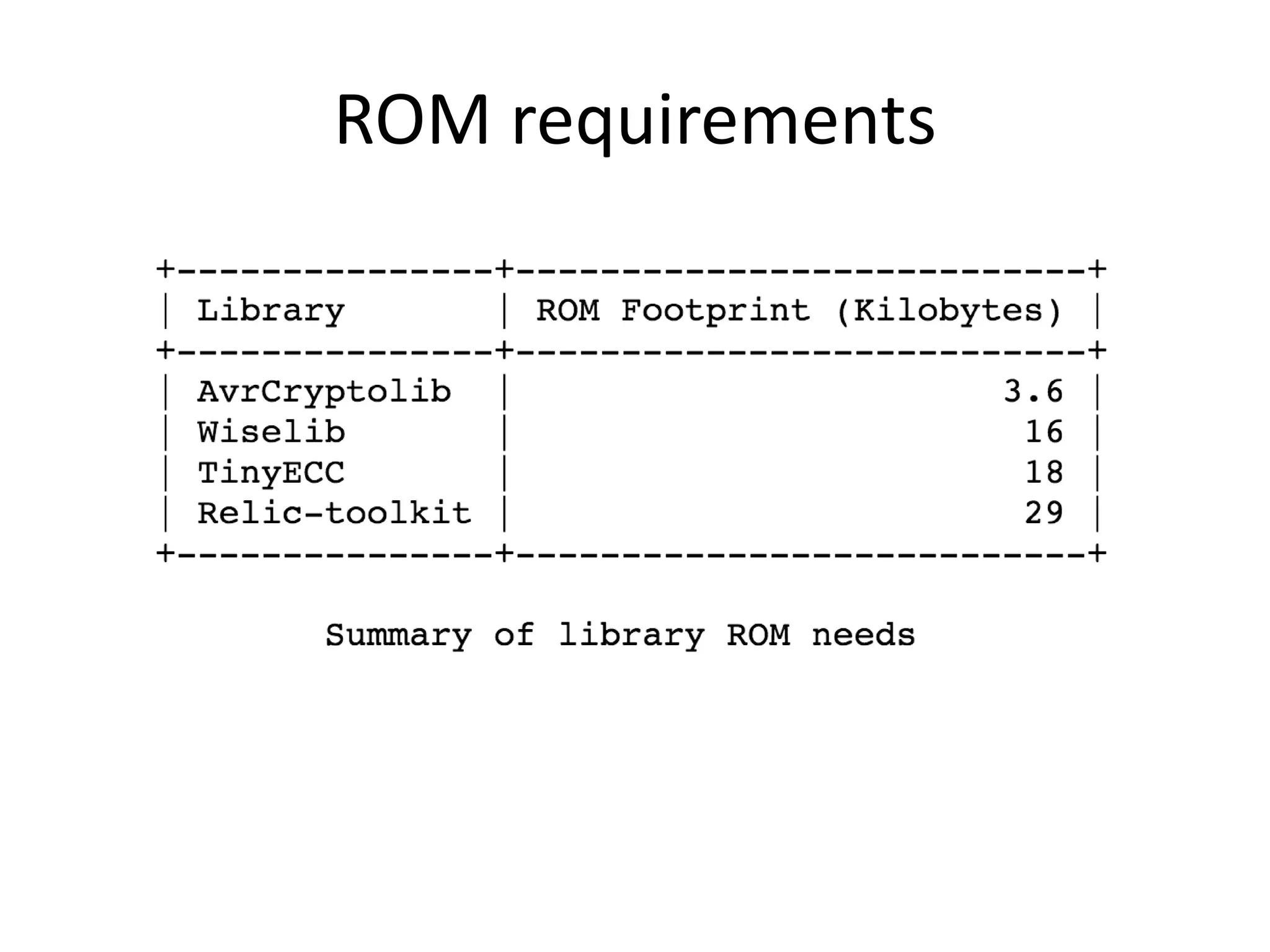
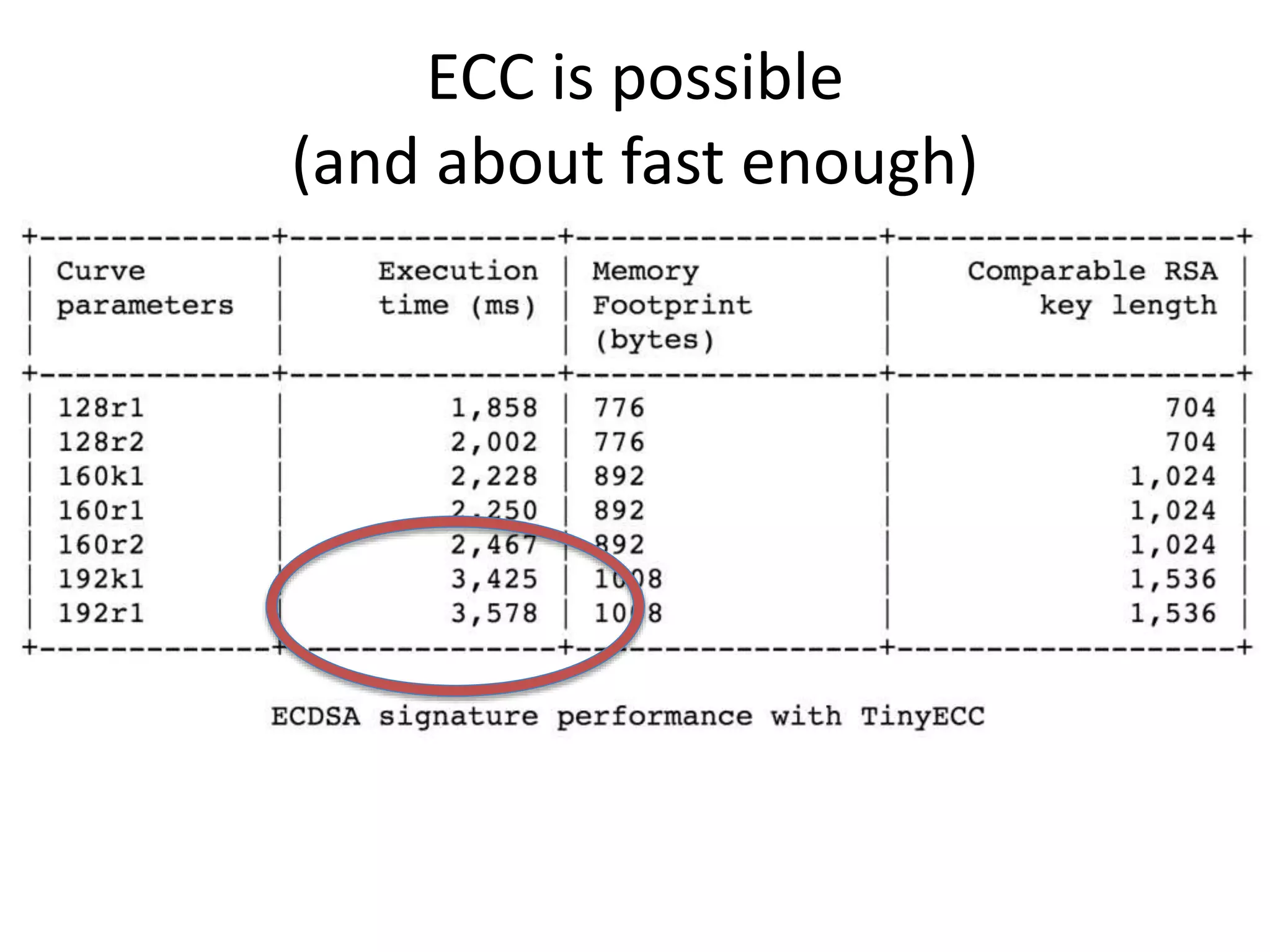
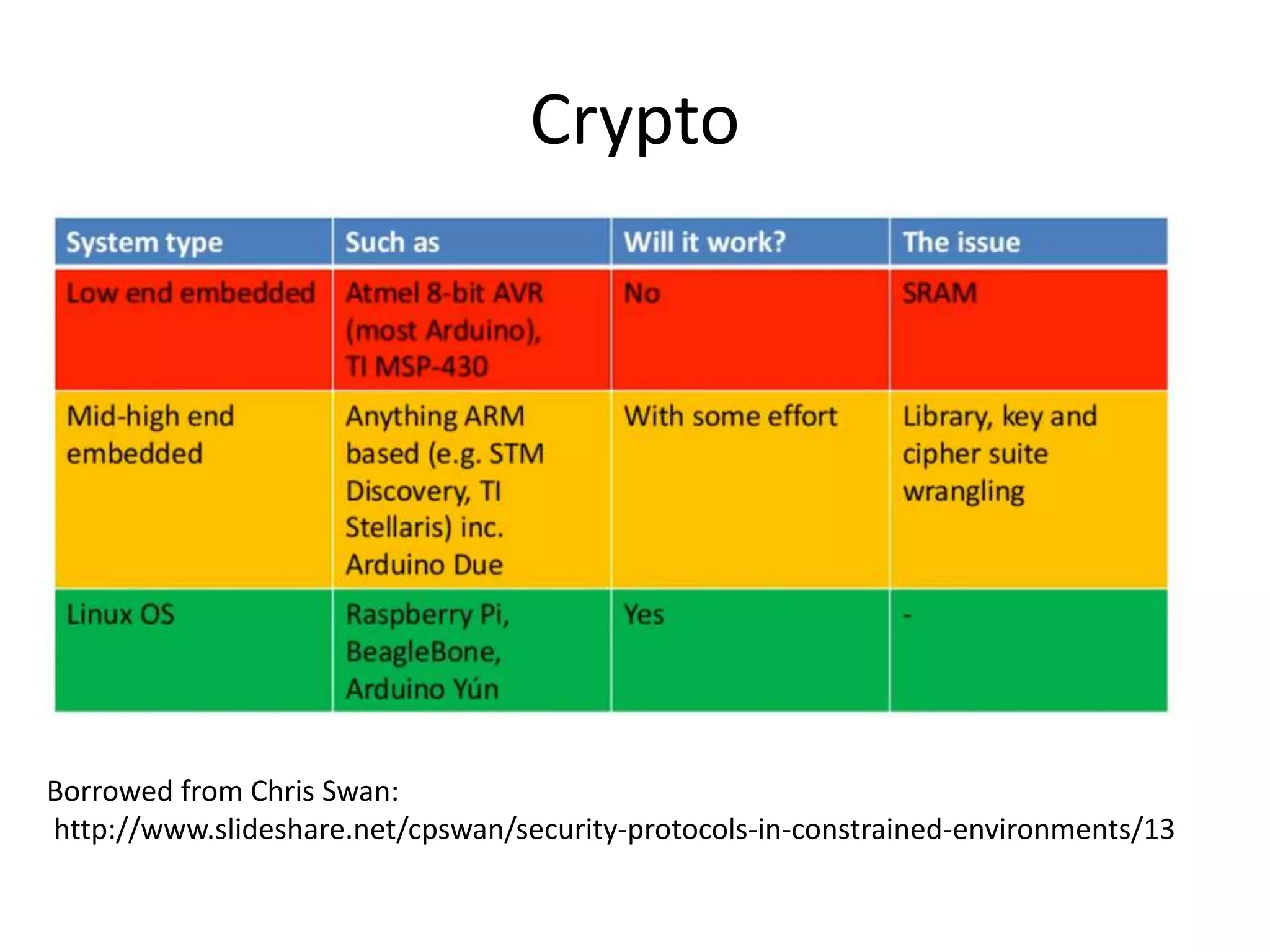
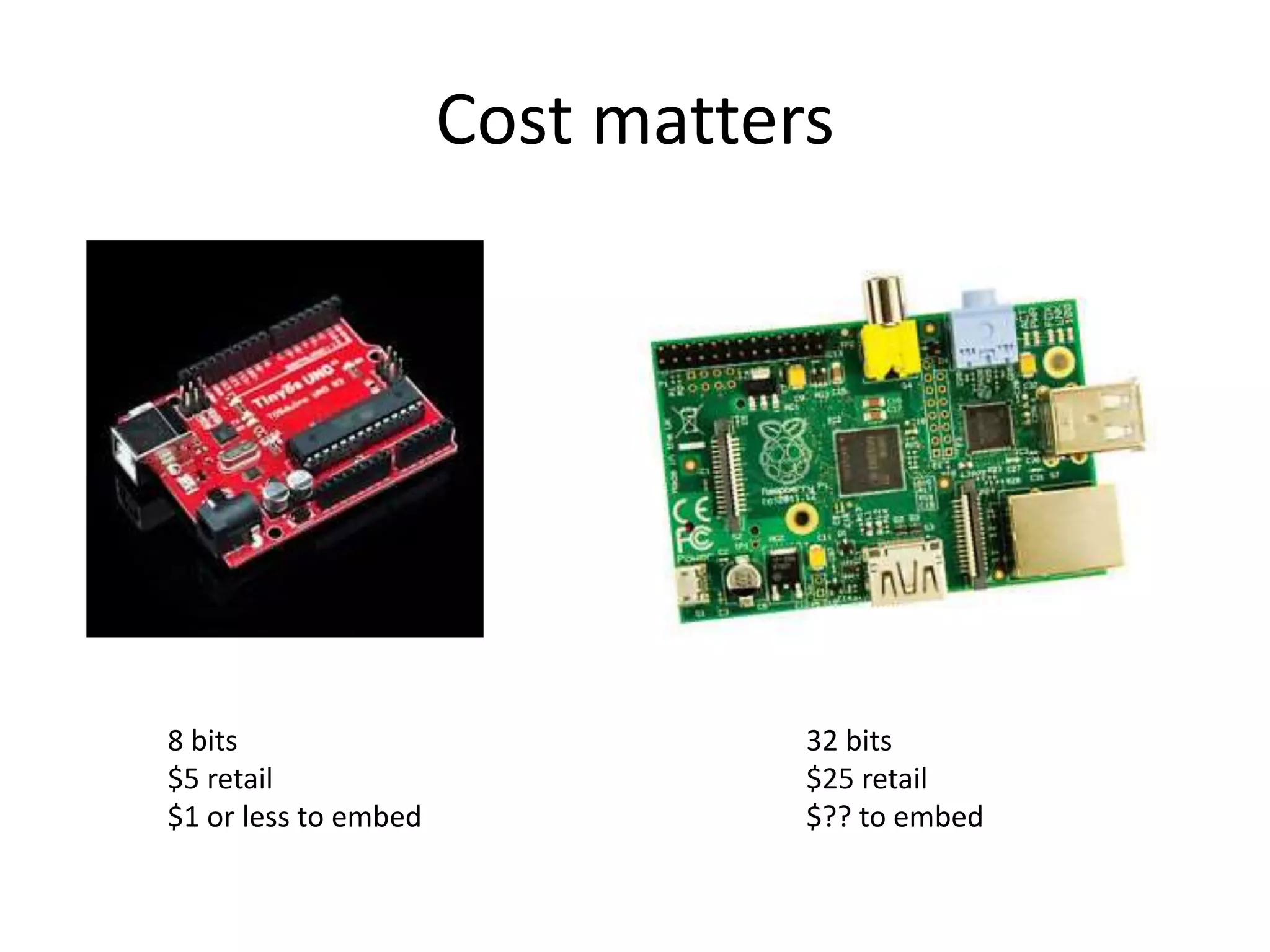
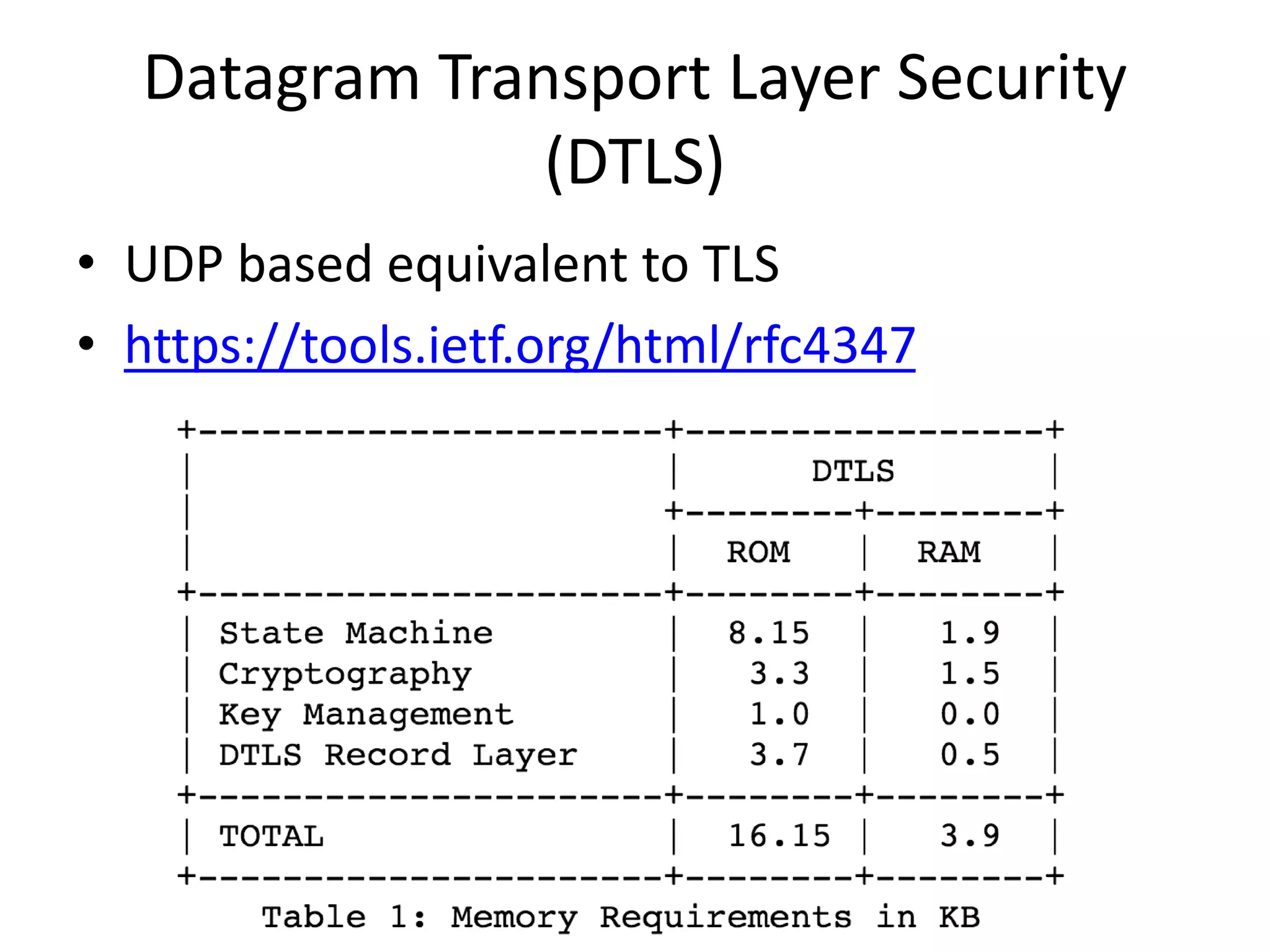
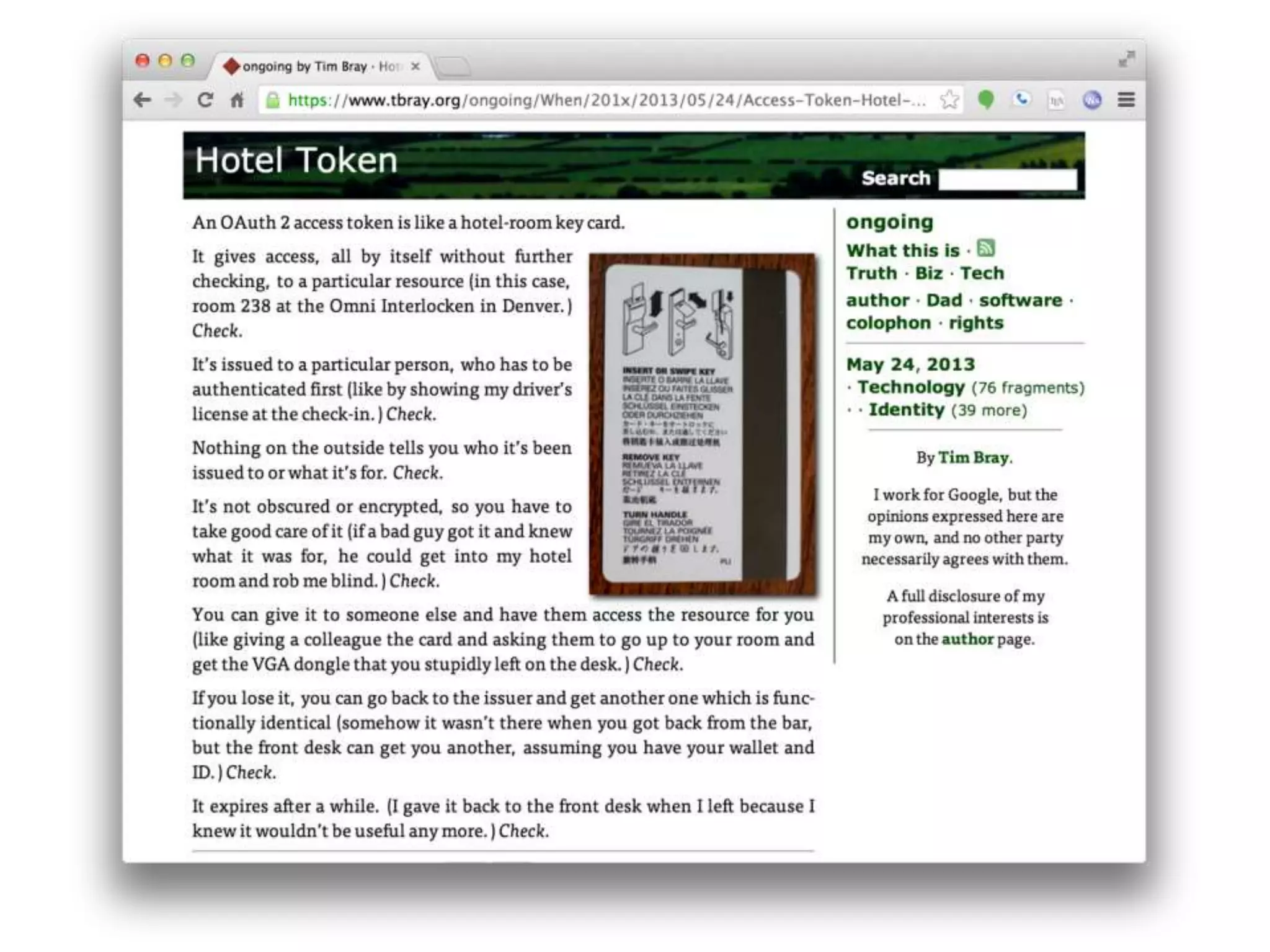
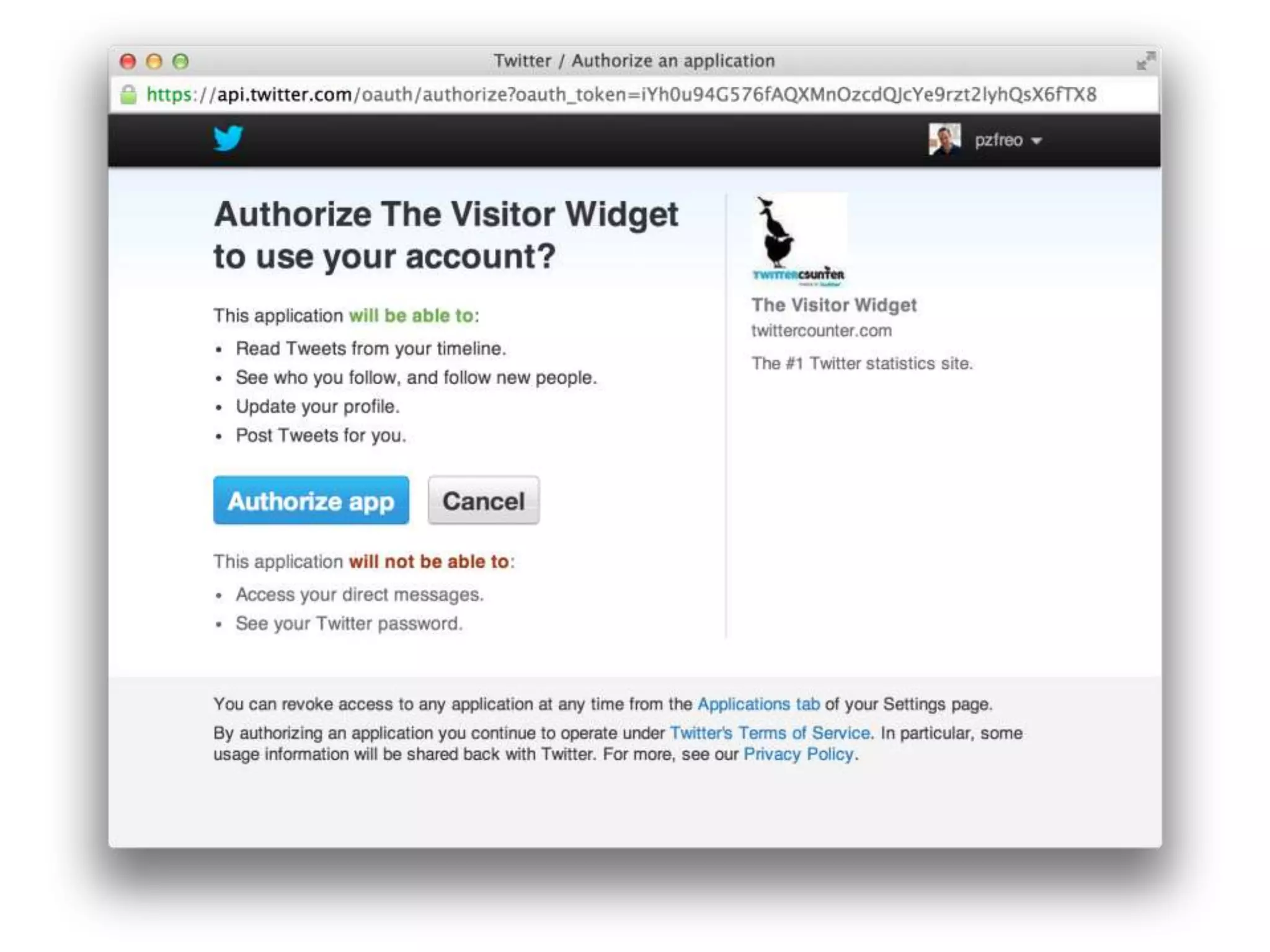
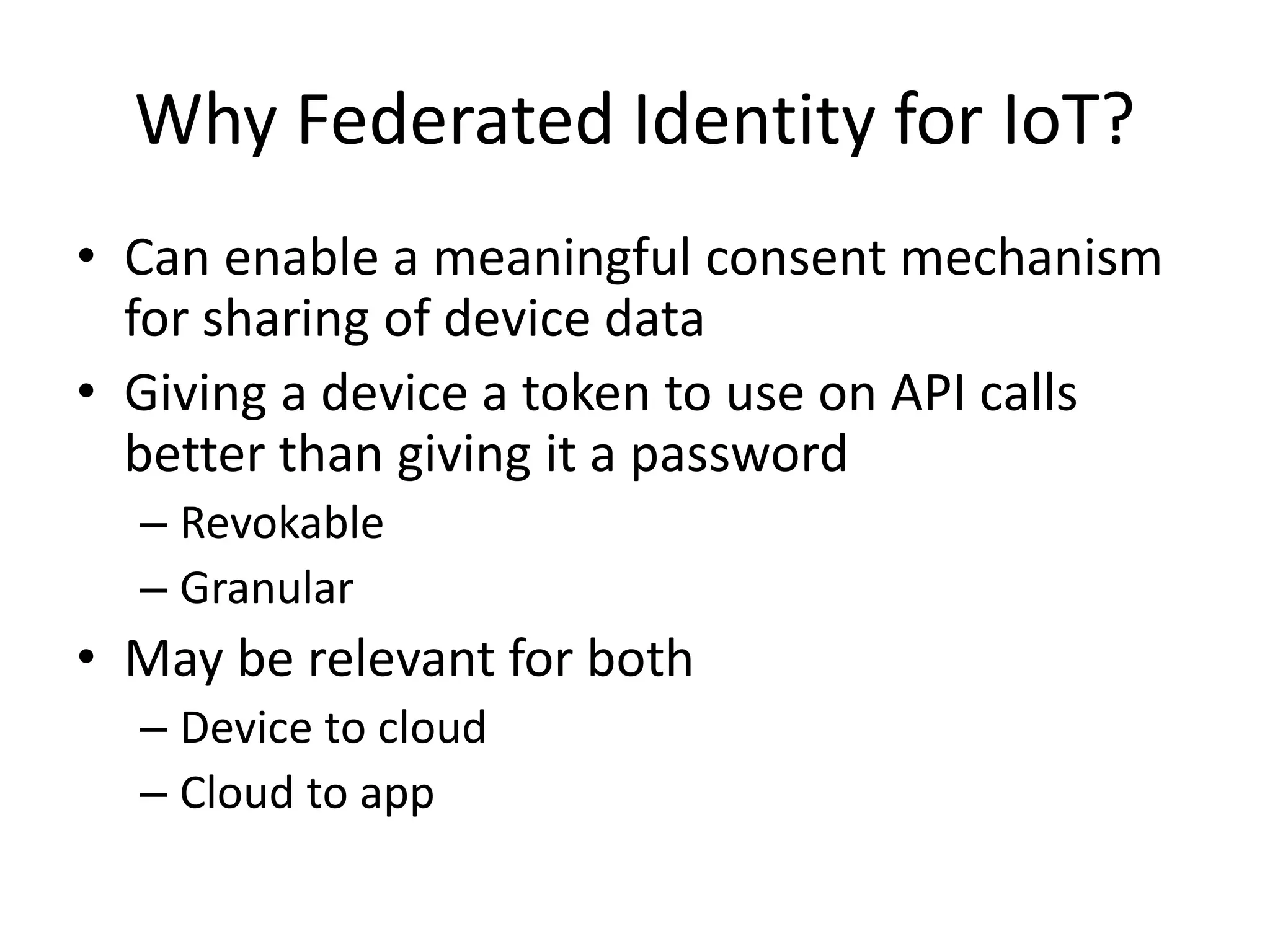
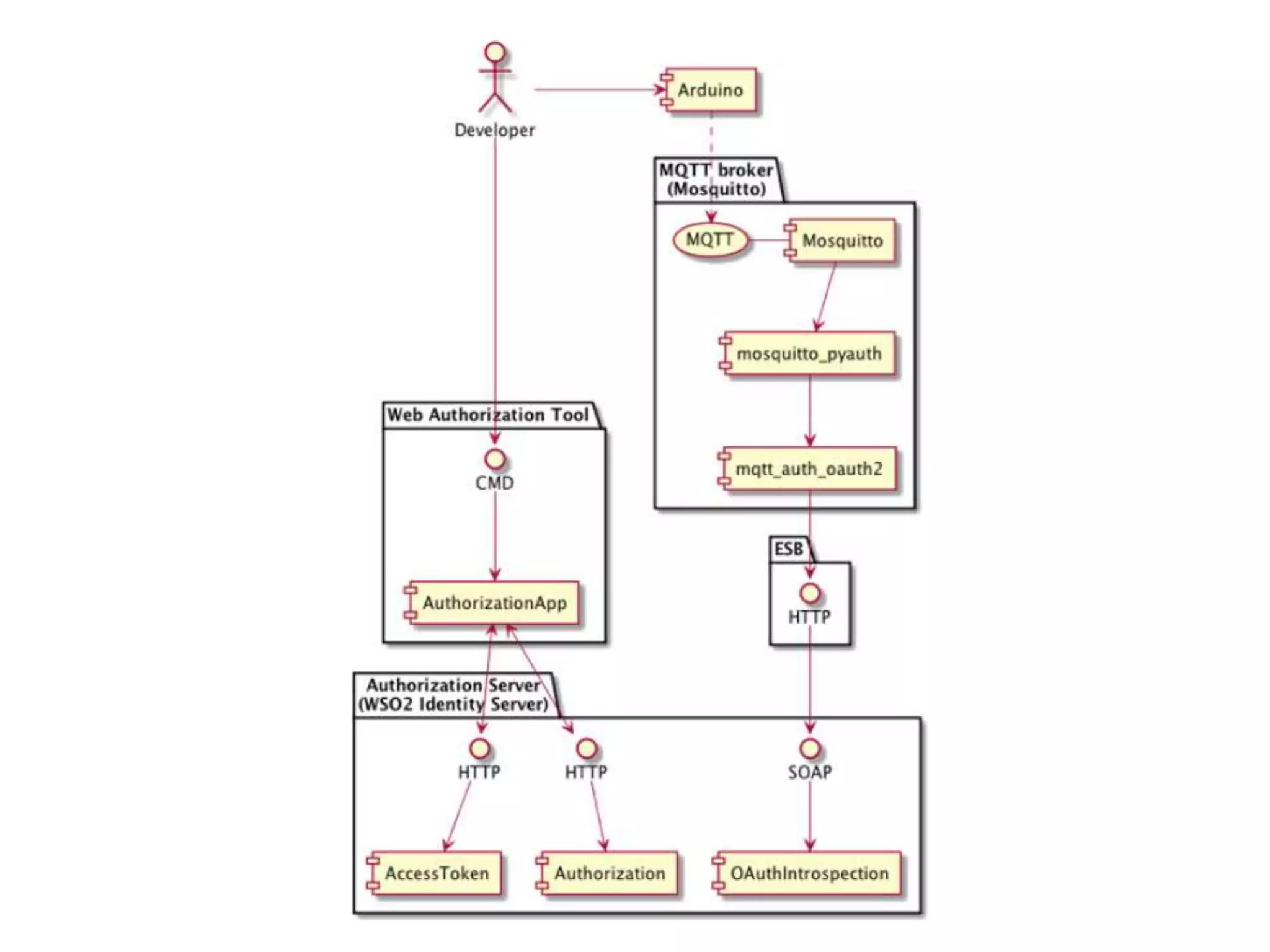
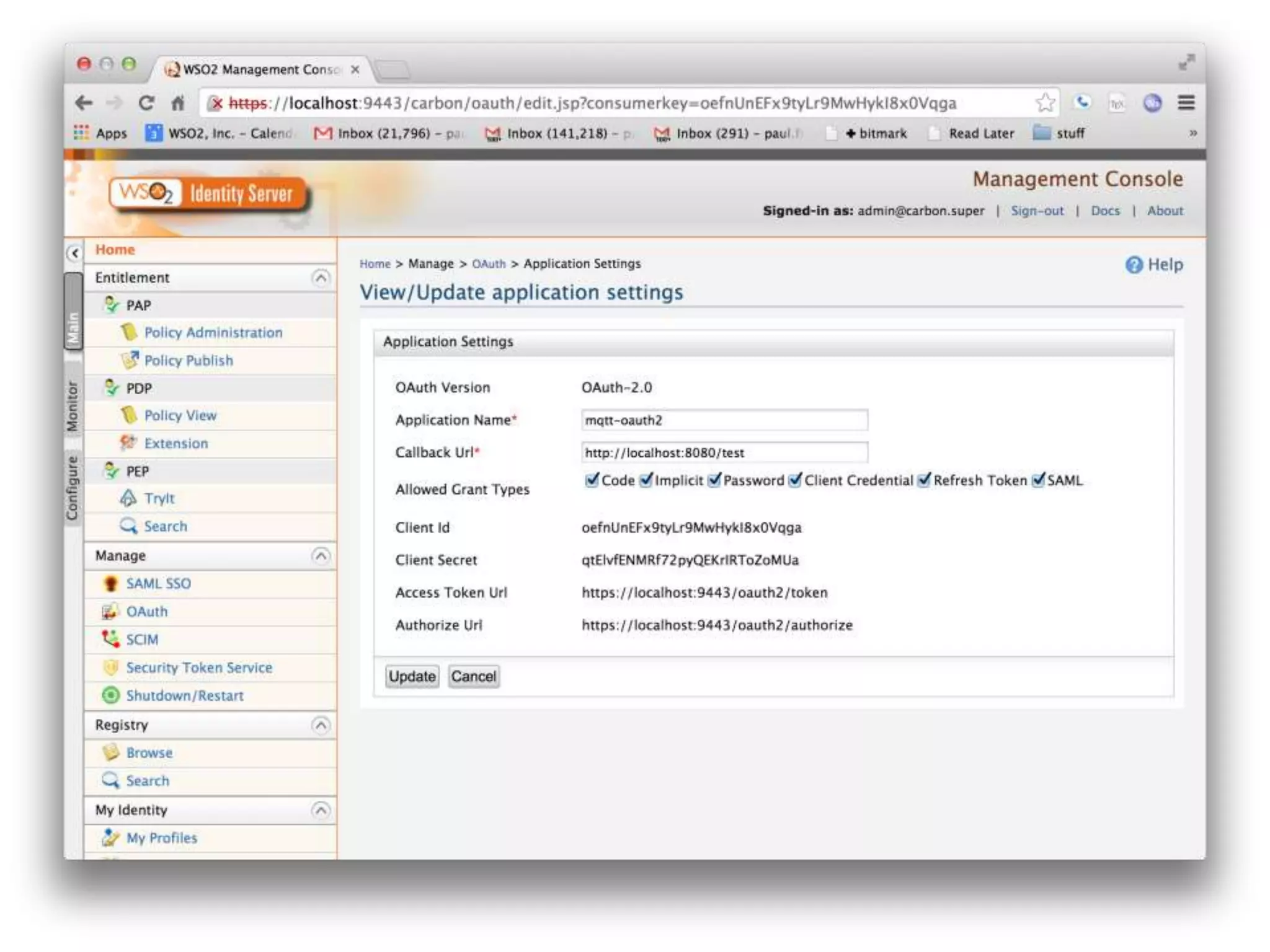
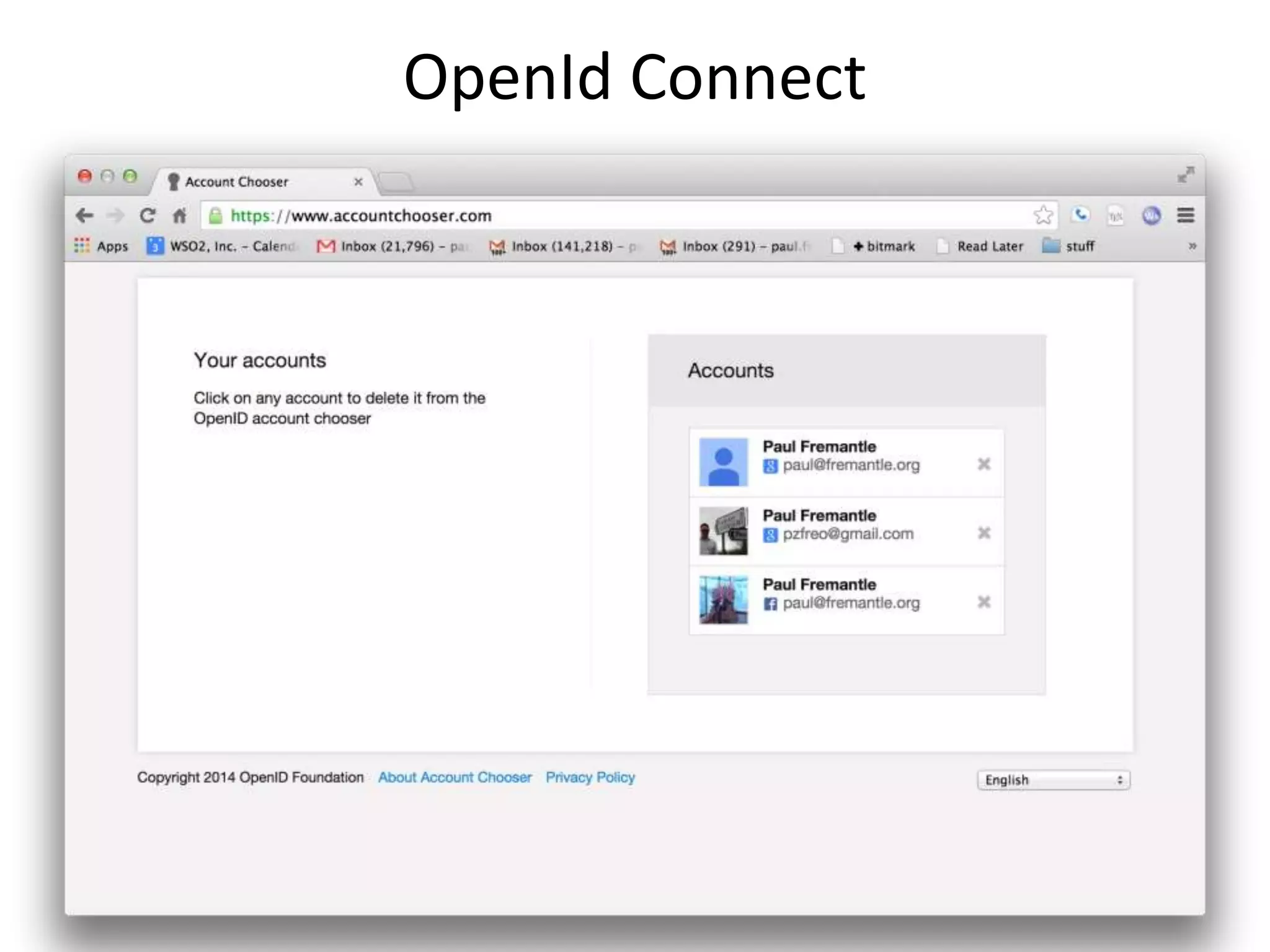
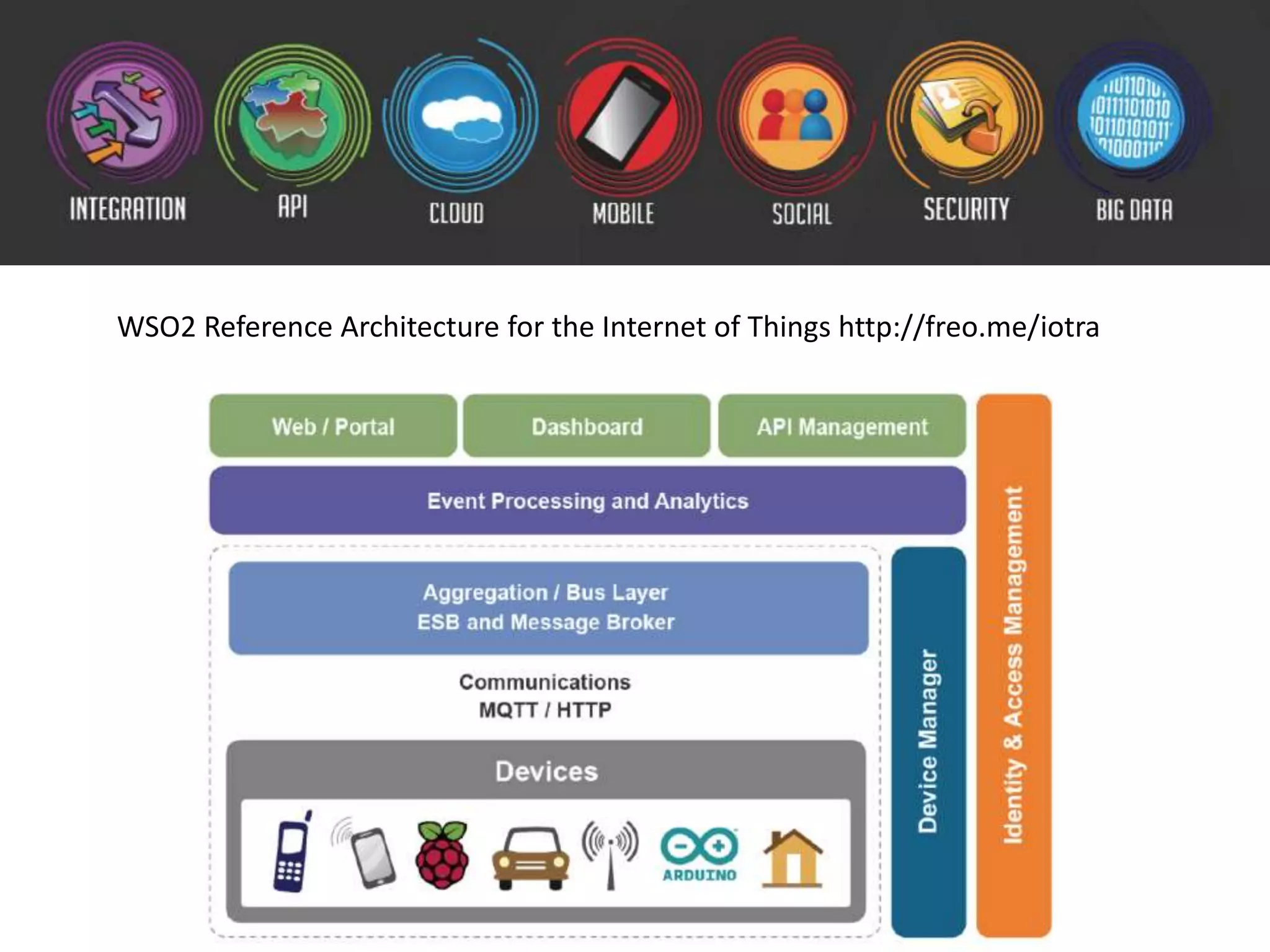
The document outlines key security challenges for Internet of Things (IoT) devices, emphasizing the importance of basic security practices and the unique vulnerabilities that IoT devices face due to their design and functionality. Recommendations include adhering to security best practices, using federated identity for device authentication, and considering the longevity and limitations of devices when implementing security measures. It advocates for community collaboration to enhance the security of future IoT devices by creating standards, libraries, and frameworks.