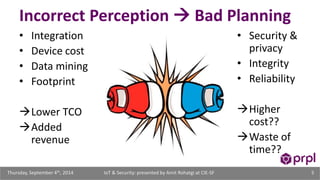
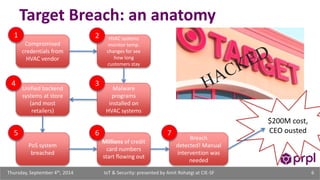
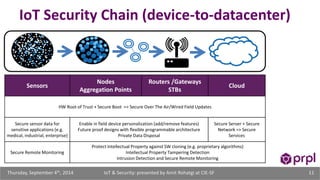
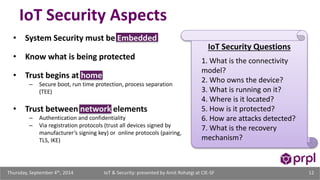
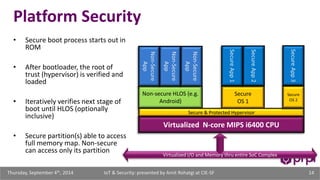
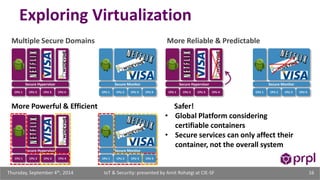
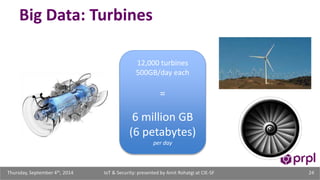
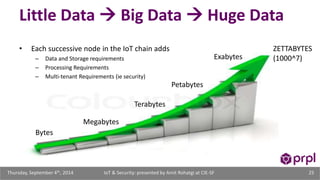
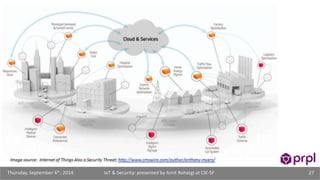
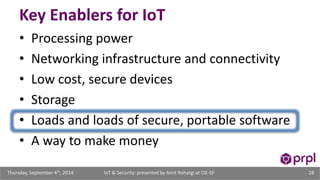
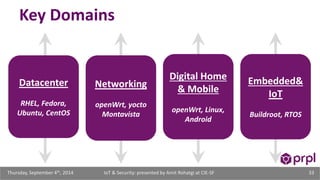
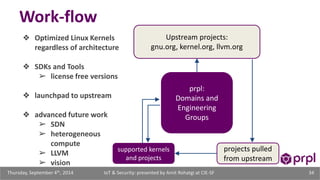
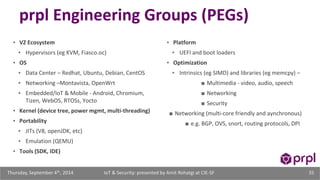
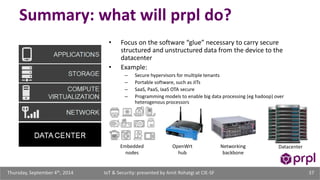
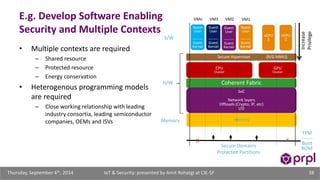
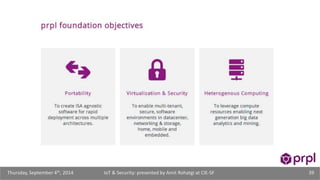
The document discusses the security challenges posed by the growing Internet of Things (IoT). It notes that consumer devices like refrigerators and TVs have already been hacked and used to send spam. The speaker discusses how incorrect perceptions of security and privacy risks could undermine planning for the IoT. Examples are given showing how compromised devices were used in the Target data breach to steal credit card numbers. The need for standardized security practices across the diverse array of IoT devices and systems is discussed.