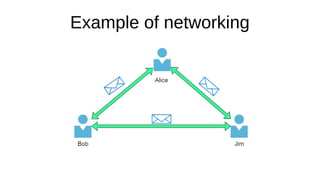
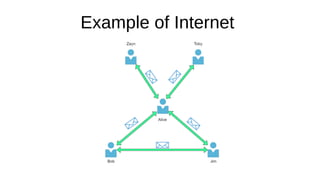
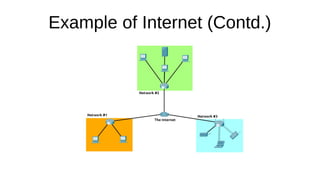
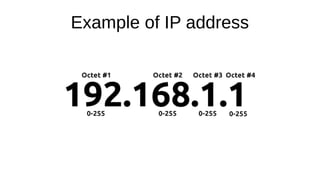
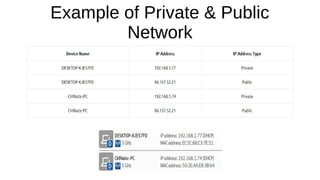
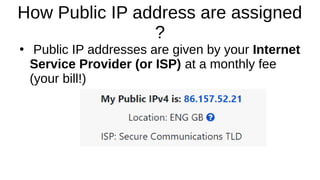
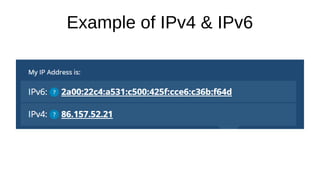
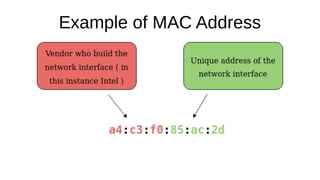
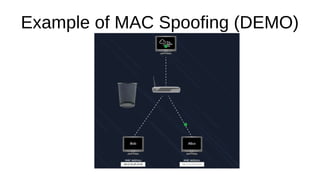
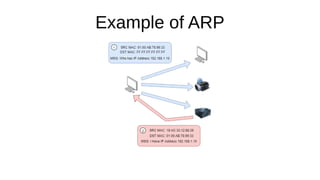
The document presents an introduction to networking fundamentals, covering key concepts such as networks, the internet, IP addresses, subnetting, and types of networks. It explains the role of IPv4 and IPv6 in addressing, the importance of MAC addresses, and networking protocols like ARP and DHCP. The session also introduces various networking tools and includes a question and answer segment.