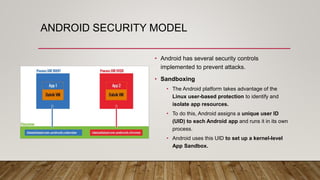
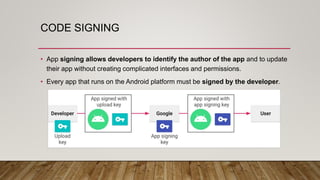
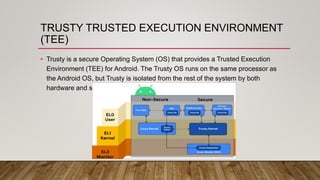
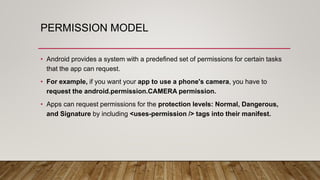
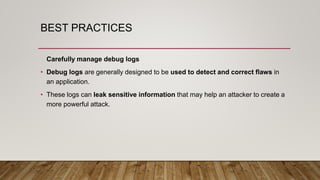
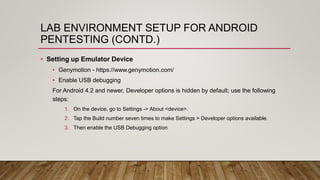
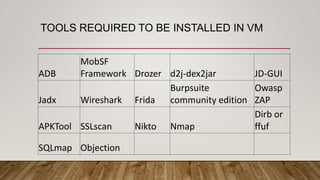
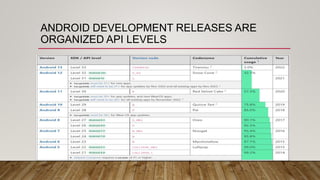
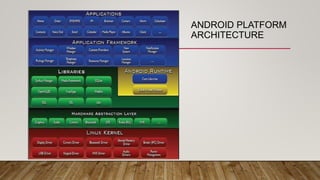
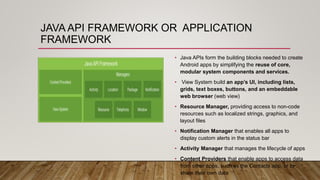
The document outlines an Android application penetration testing training session agenda, covering topics such as the basics of Android, OWASP's top 10 mobile vulnerabilities, and components of the Android framework. It also discusses the Android security model, including sandboxing, code signing, and permission models, along with best practices for secure app development. A lab environment setup for testing Android applications is presented, detailing tools and prerequisites necessary for effective penetration testing.












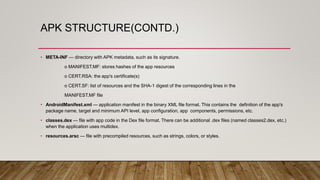
![APK STRUCTURE
• An APK file is a compressed package that contains
the following files and directories:
• assets — directory with application assets. (files
used within the Android app, such as XML files,
JavaScript files, and pictures)
• res — directory with all resources that are not
compiled into resources.arsc. These are all resources
except the files in res/values. This folder contains the
activity layouts.
• lib — directory with compiled native libraries used by
your app. Contains multiple directories —one for each
supported CPU architecture (ABI). [armeabi-v7a |
arm64-v8a | x86 | x86_64]](https://image.slidesharecdn.com/day1-androidpenetrationtesting-230119013848-c6213fa0/85/Android-Penetration-Testing-Day-1-19-320.jpg)