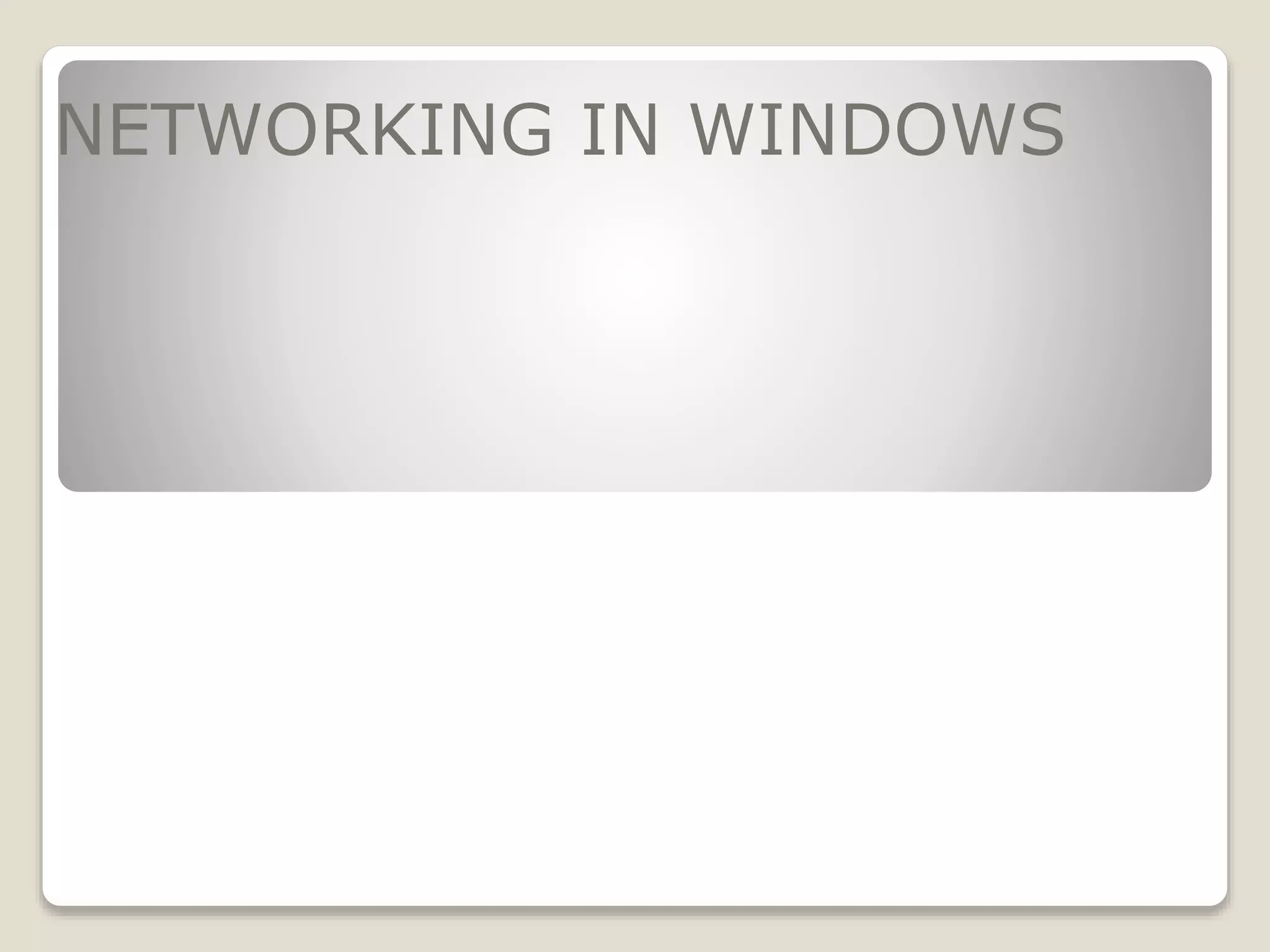
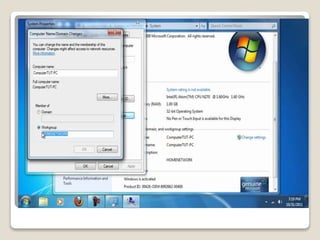
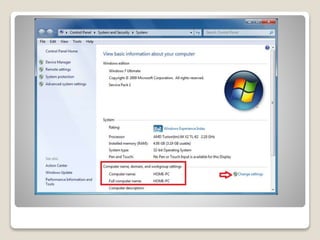
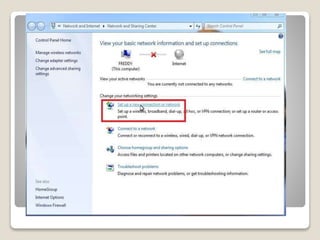
The document discusses networking concepts in Windows such as workgroups, computer names, user accounts, and sharing resources. It provides explanations of key terms and how to configure different sharing options in Windows like using the Public folder, mapping network drives, and sharing a local printer with the Homegroup. The document recommends using a wireless printer for a home network instead of sharing a local printer due to issues that can arise with permissions and speed when printing from another computer on the network.