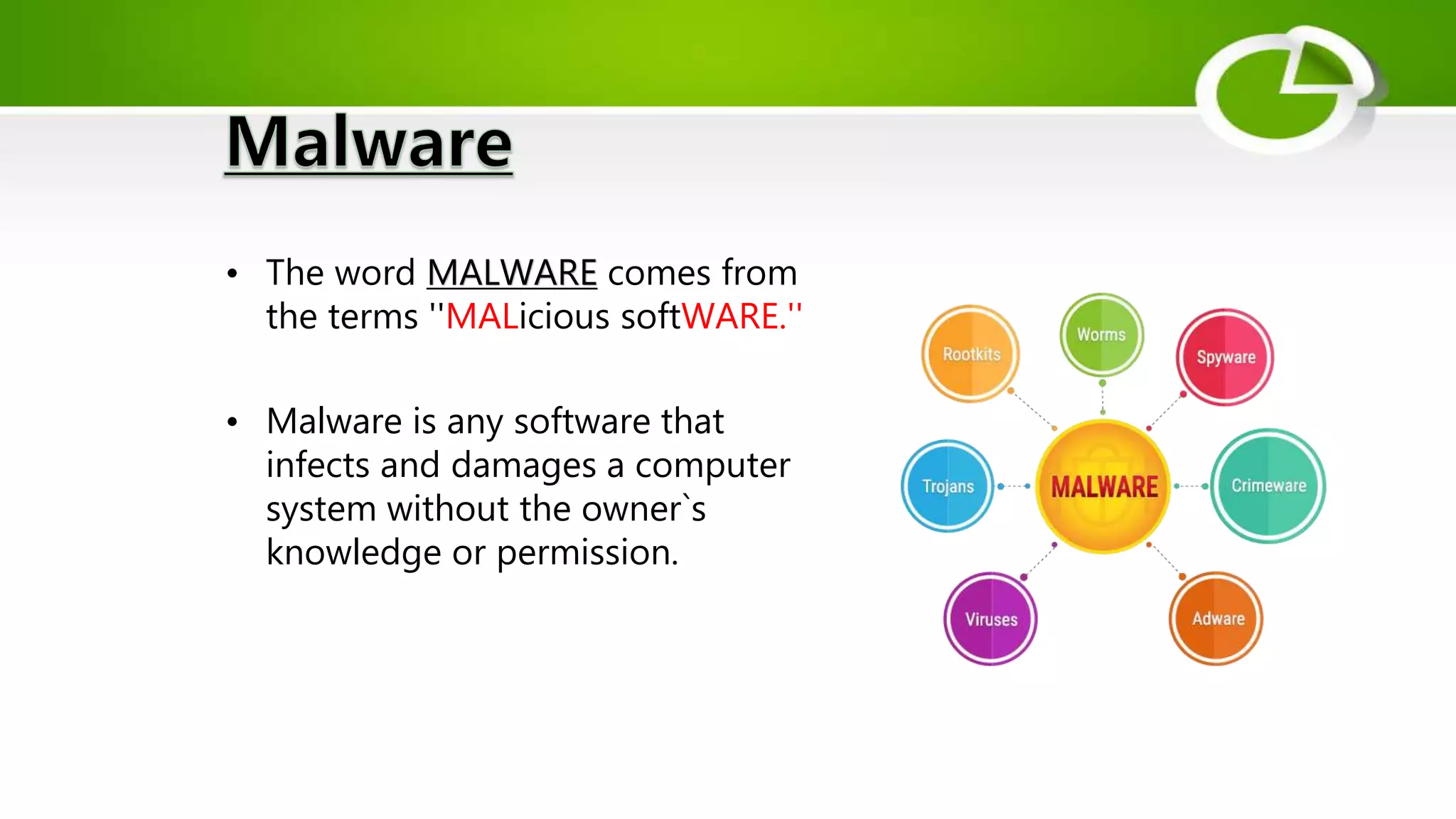
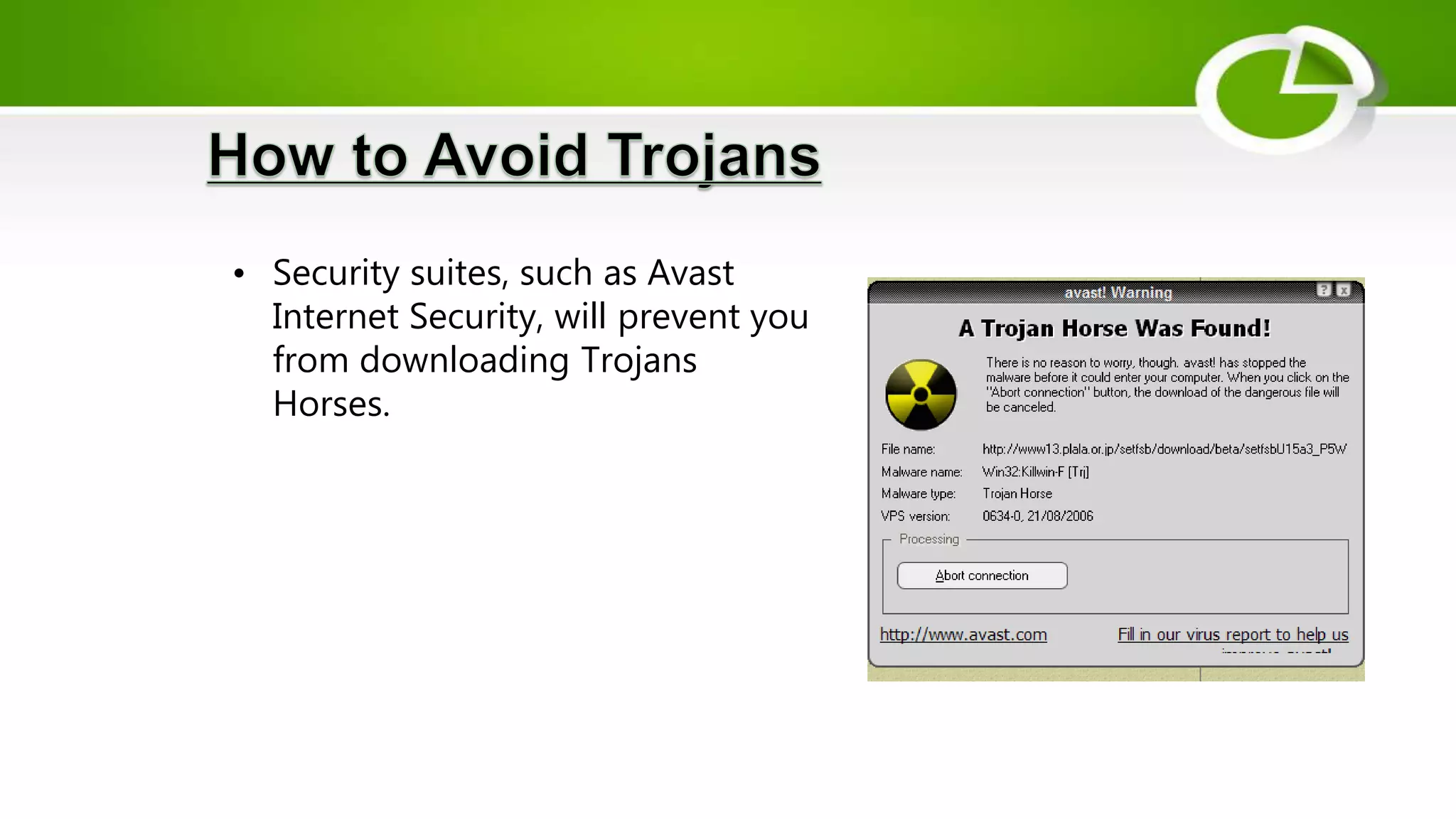
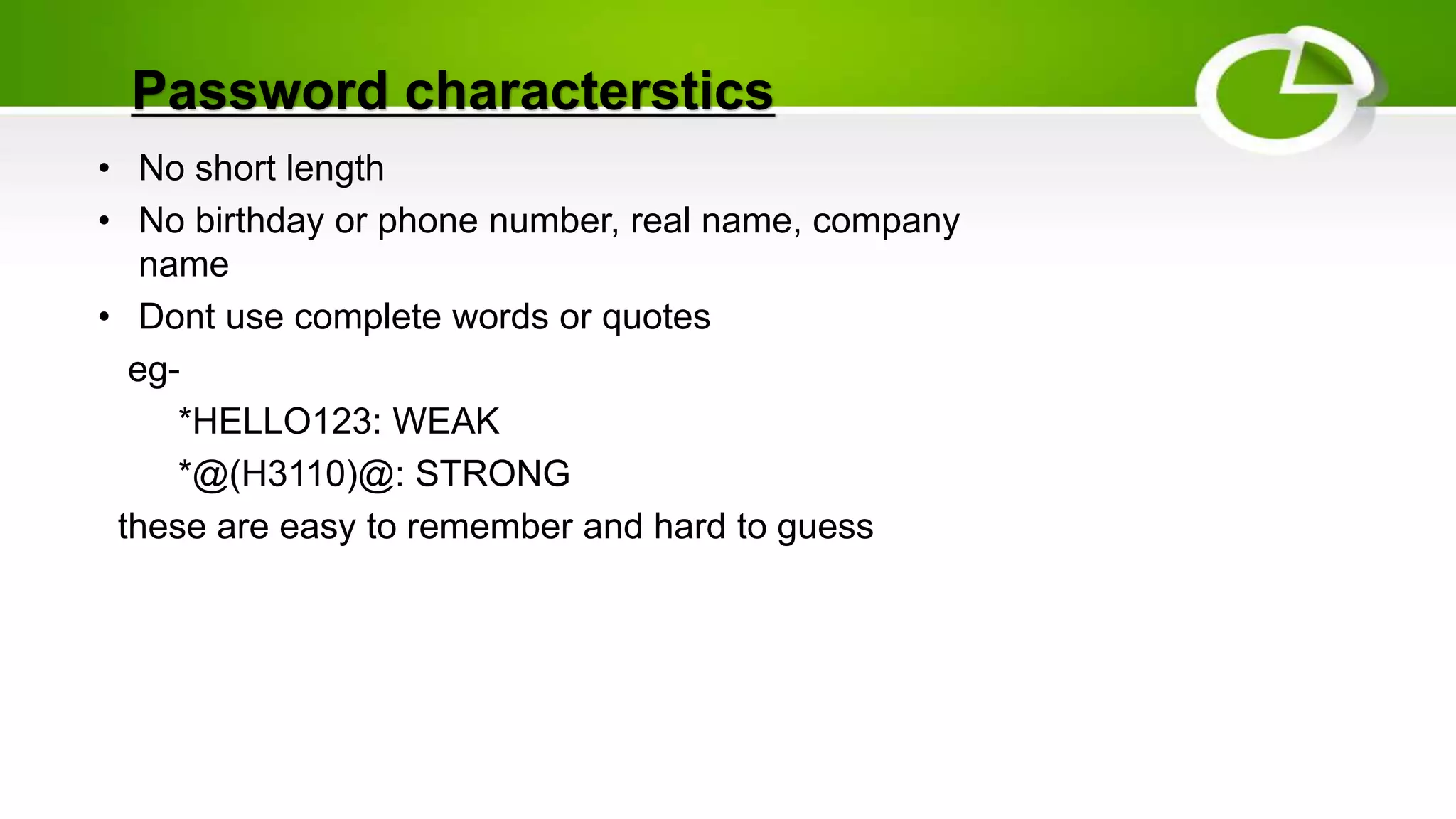
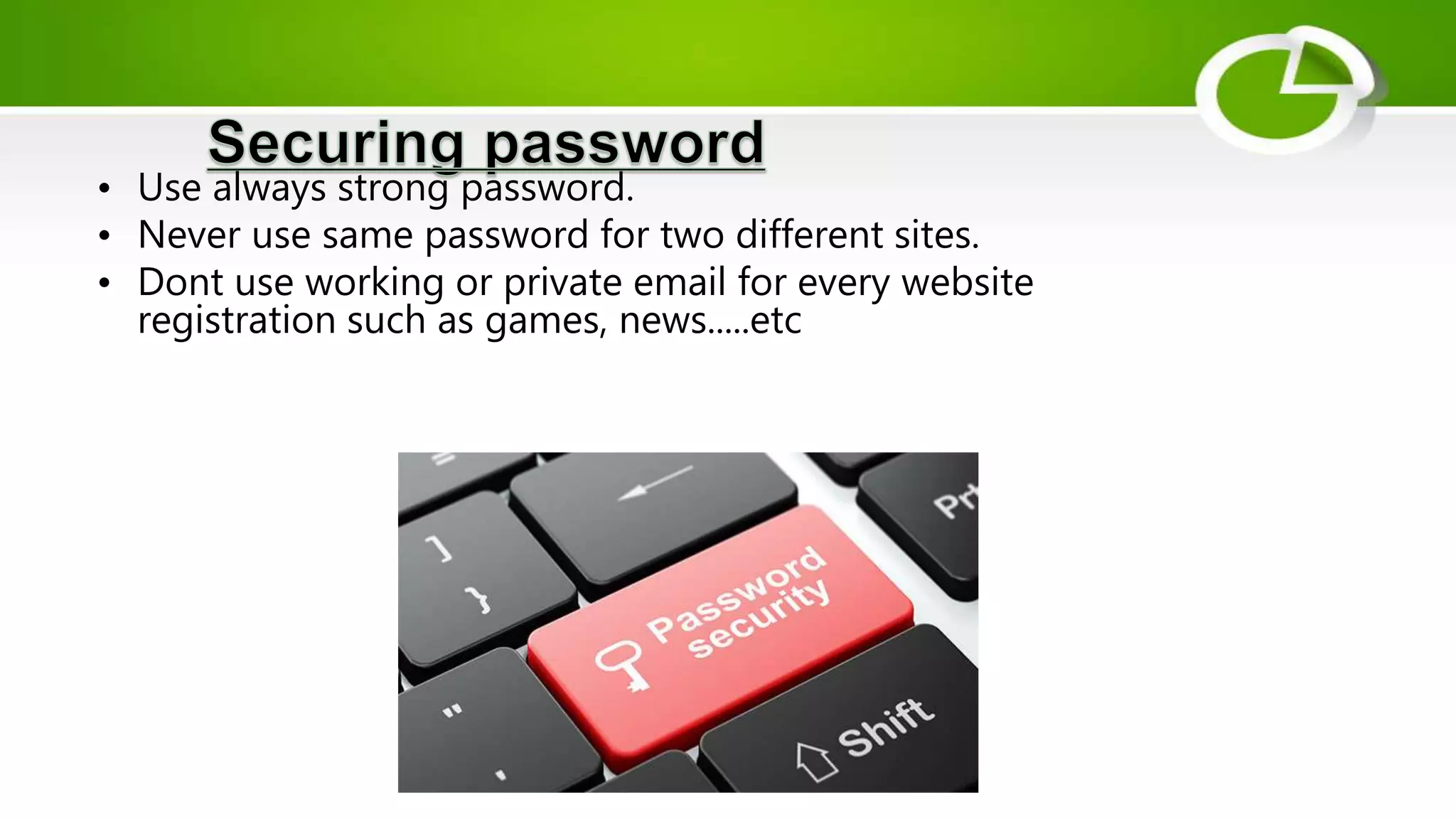
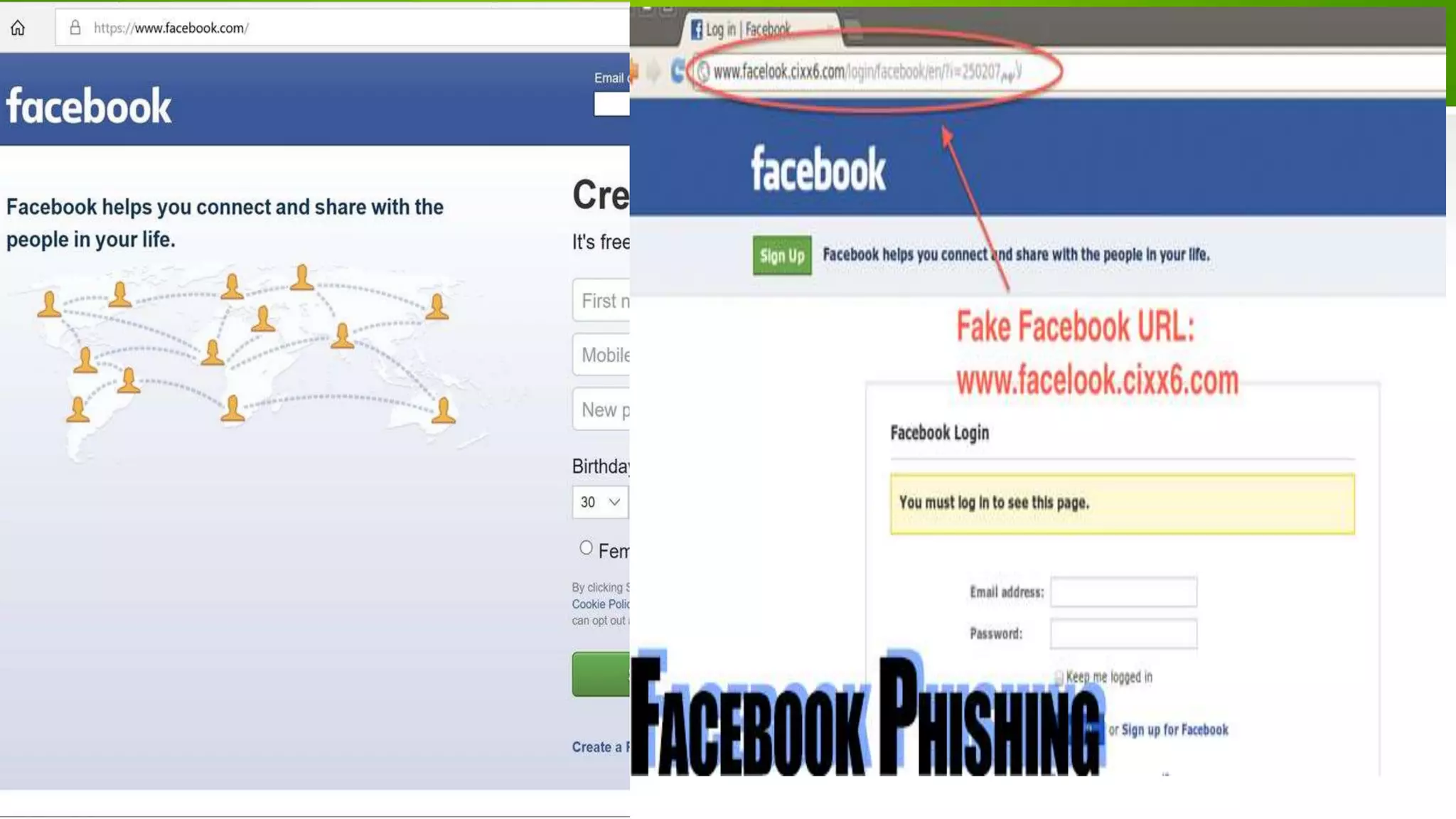
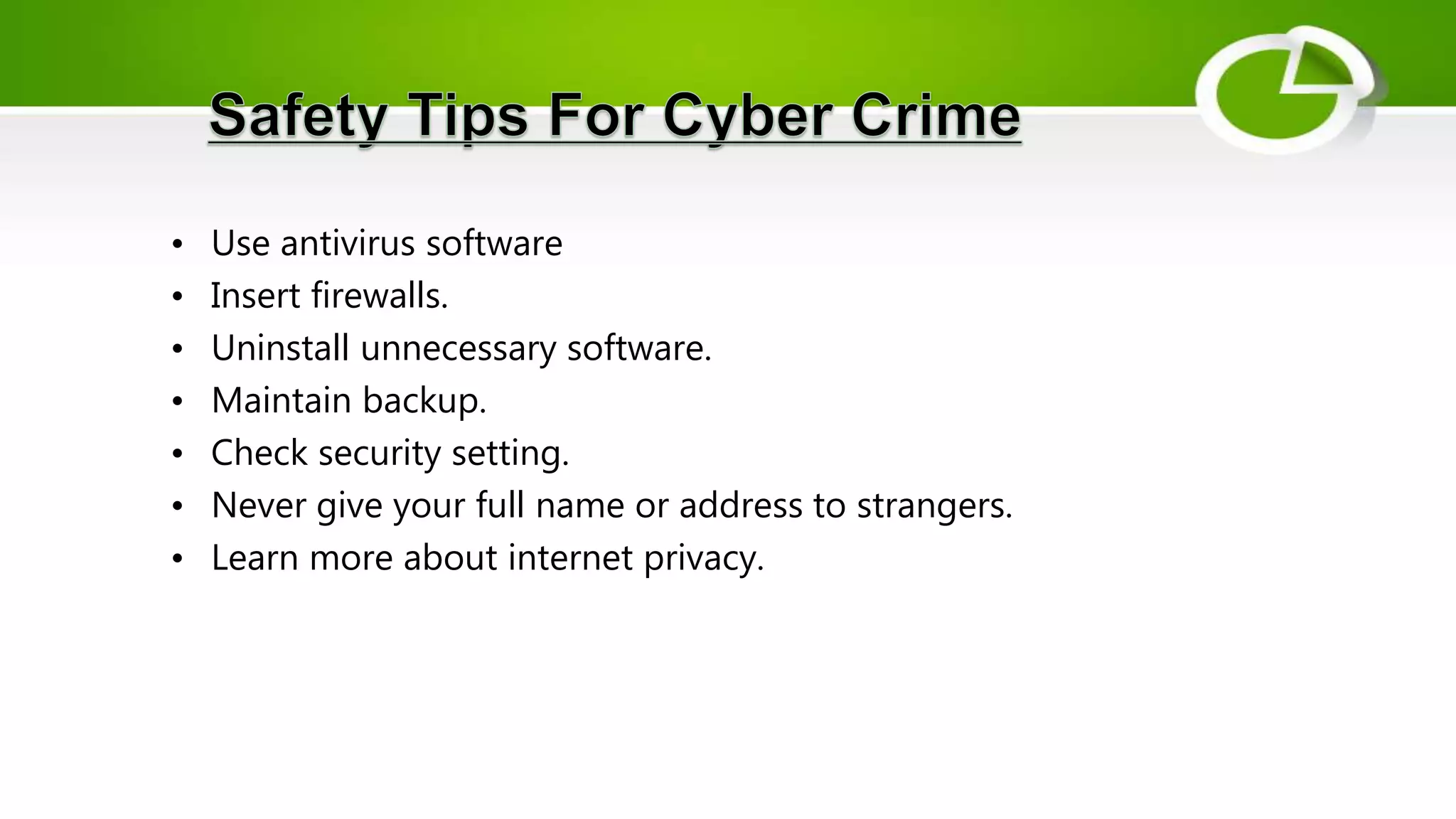
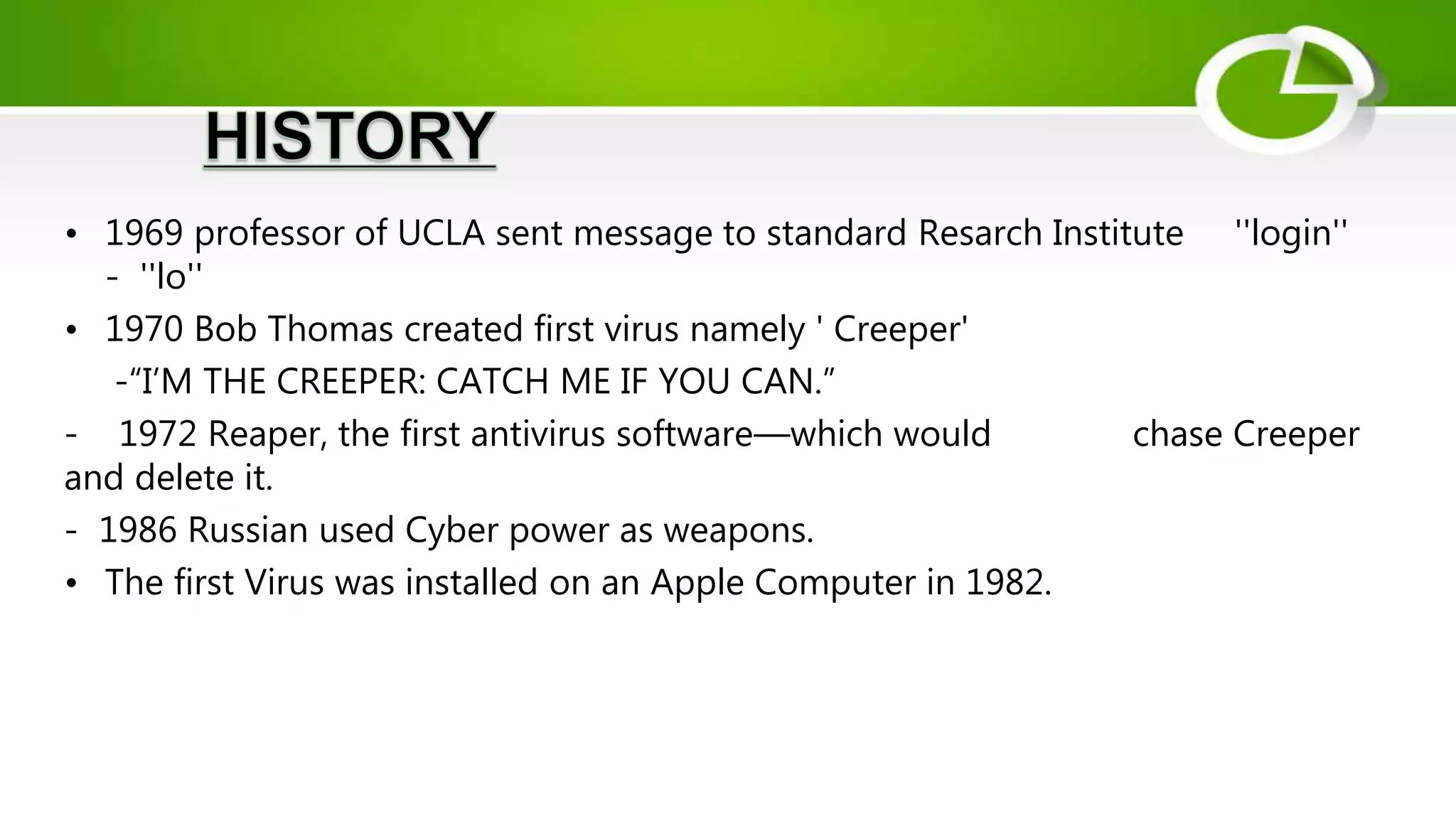
This document discusses cyber security and the need for it. It provides definitions of cyber security and cybercrime, explaining that cyber security aims to protect networks, devices, programs and data from unauthorized access or attacks through establishing rules and measures. It categorizes cybercrimes and discusses different types of cyber threats like viruses, hackers, malware and phishing. It also provides some cyber attack statistics and recommendations for maintaining cyber security like using antivirus software, firewalls, strong passwords and privacy settings.





![[ ]
CYBER
(Computer system,
network ,program or
data)
SECURITY
(System security,
network security
program or
data security)](https://image.slidesharecdn.com/mispptupdated-191111103627/75/CYBER-SECURITY-9-2048.jpg)