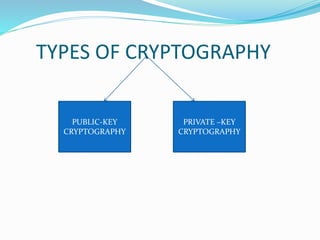
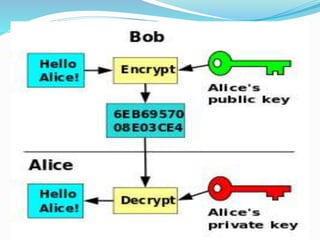
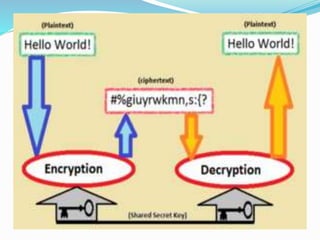
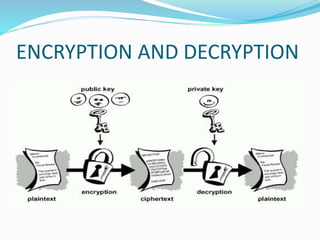
Sneha Chauhan presented on cyber crime and security techniques. The presentation discussed how the growth of the internet in India has led to new opportunities but also disadvantages like cyber crime. Several types of cyber crimes were defined, including hacking, denial of service attacks, and software piracy. The presentation provided safety tips to prevent cyber crime and outlined cyber security techniques such as using antivirus software, firewalls, and maintaining backups. It also discussed public key cryptography and private key cryptography.