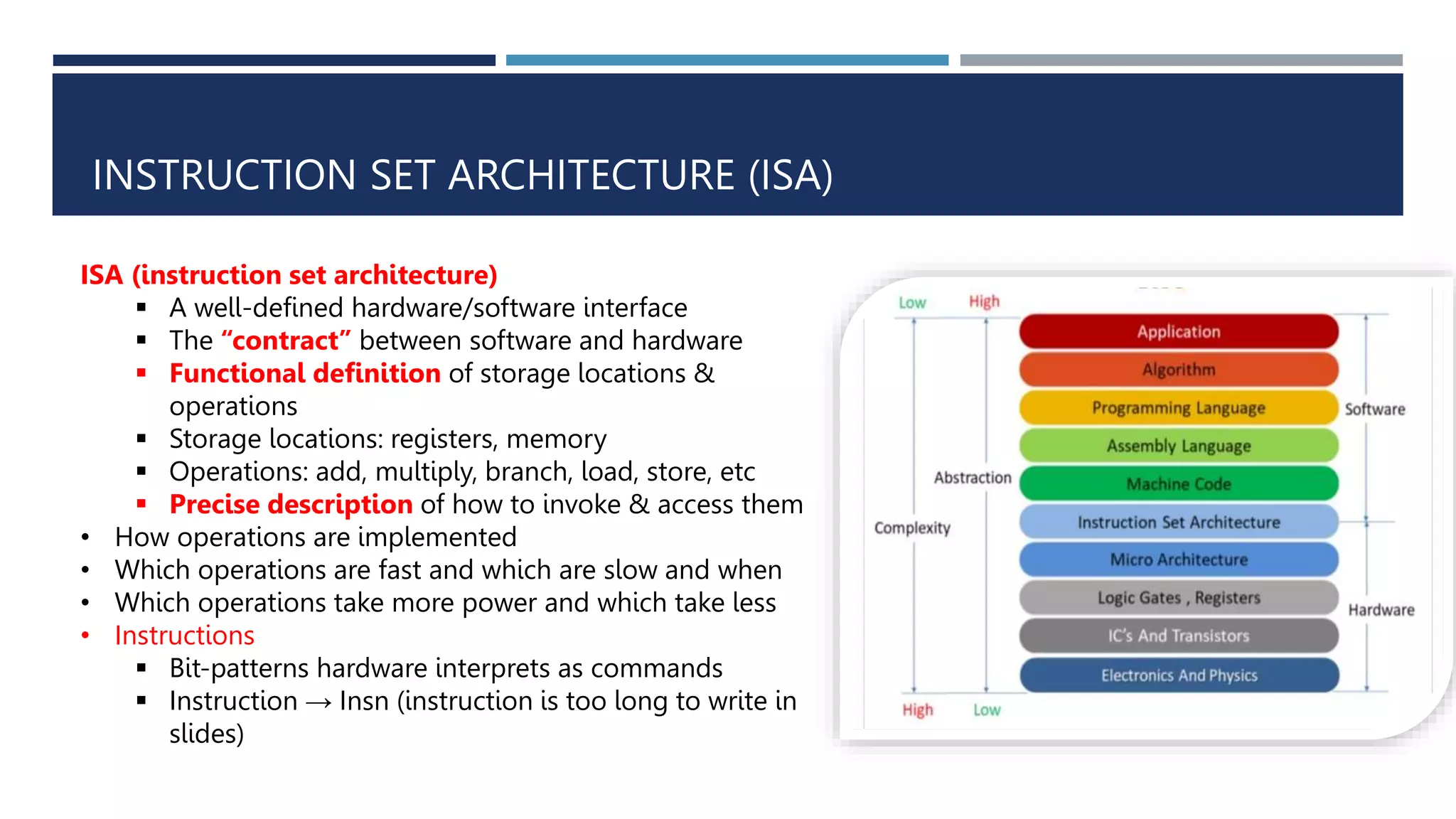
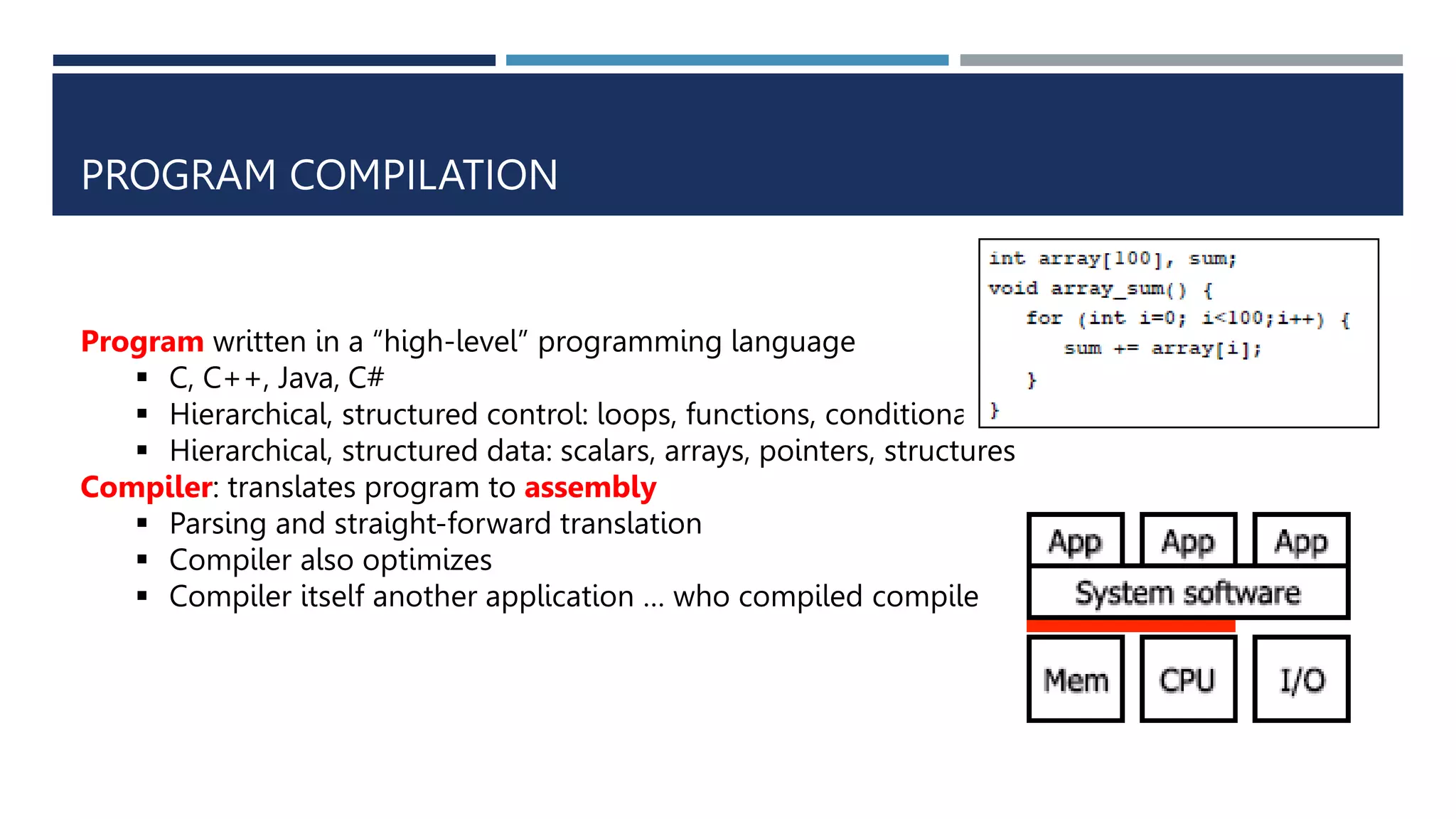
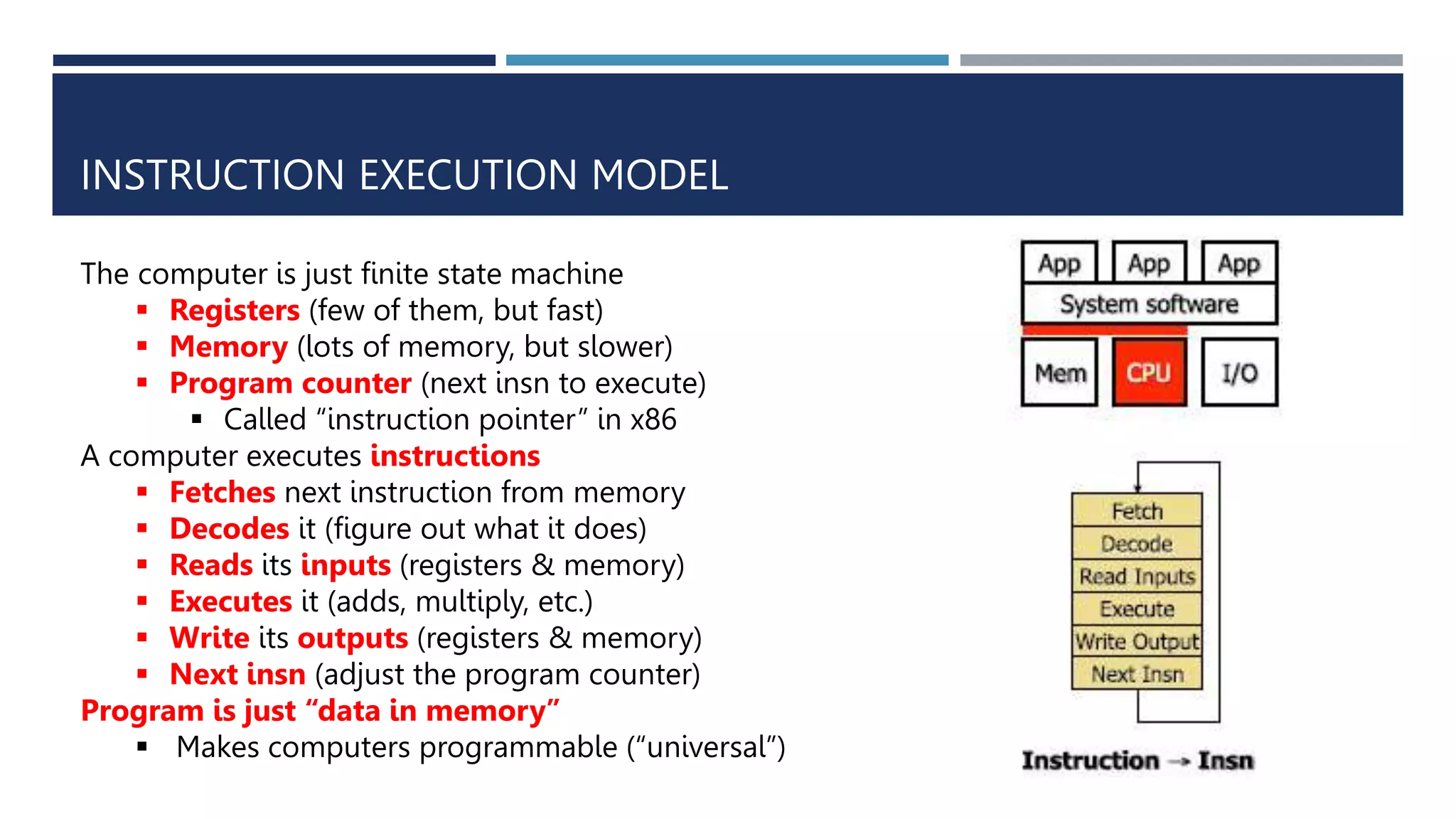
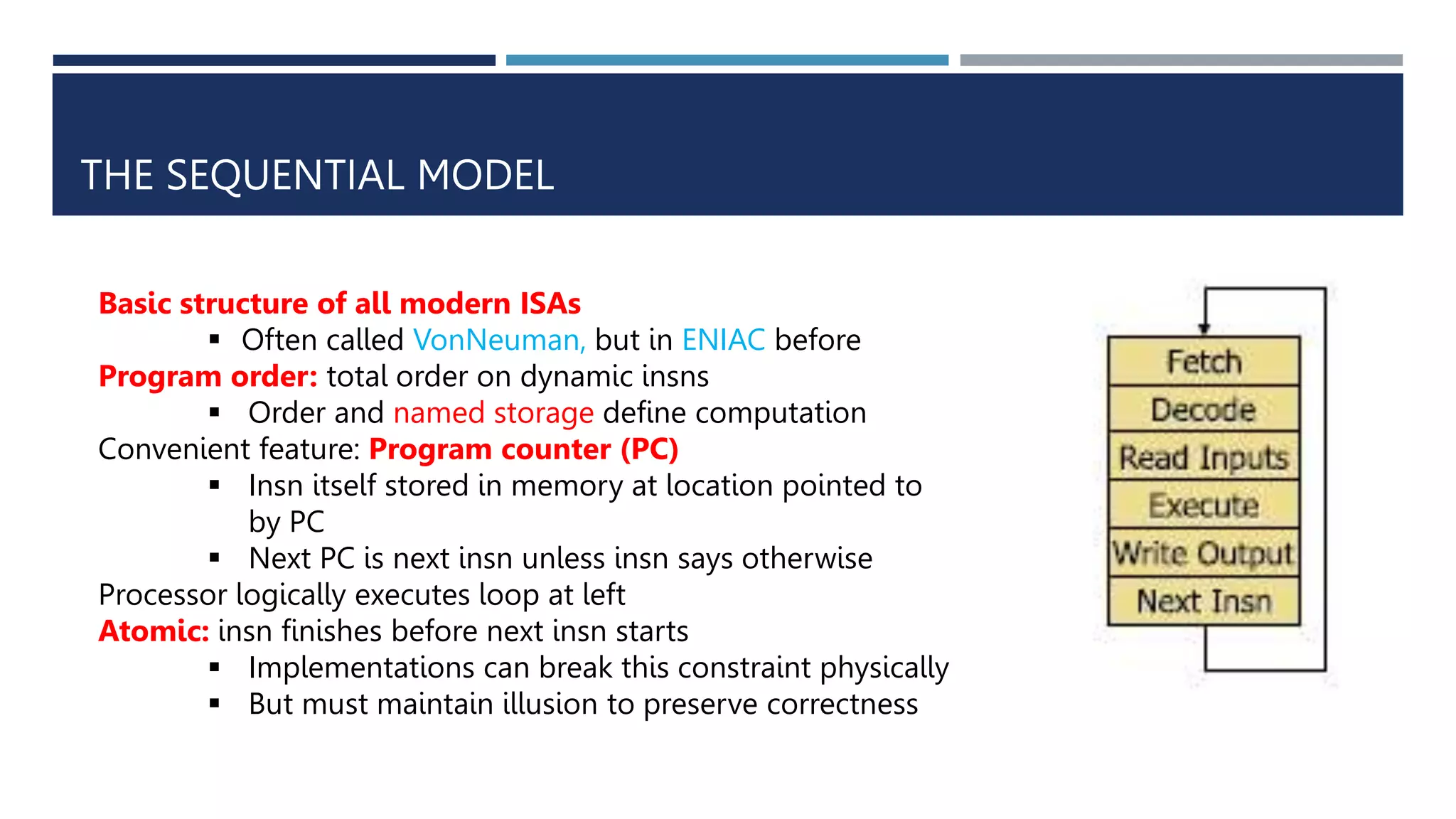
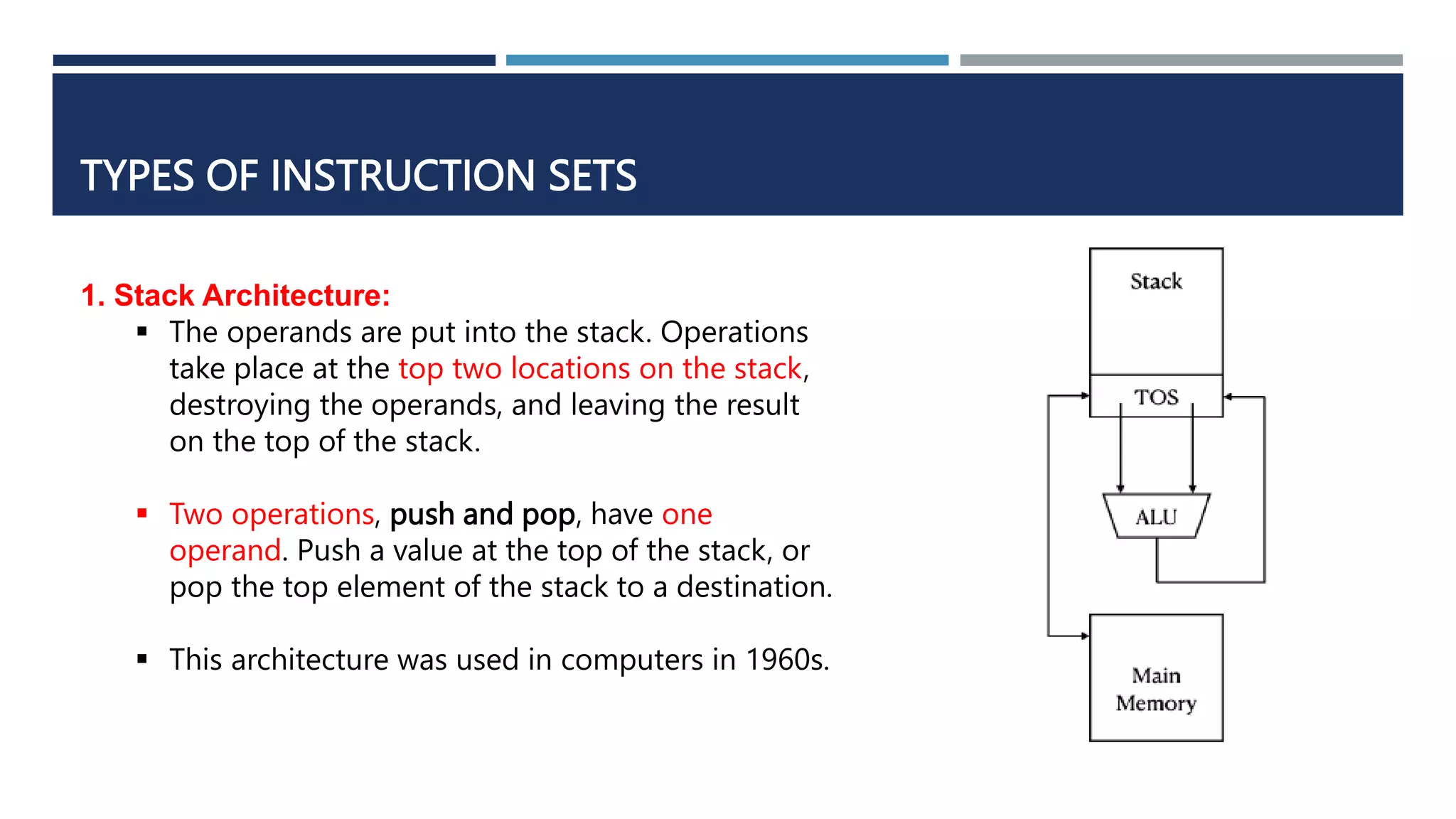
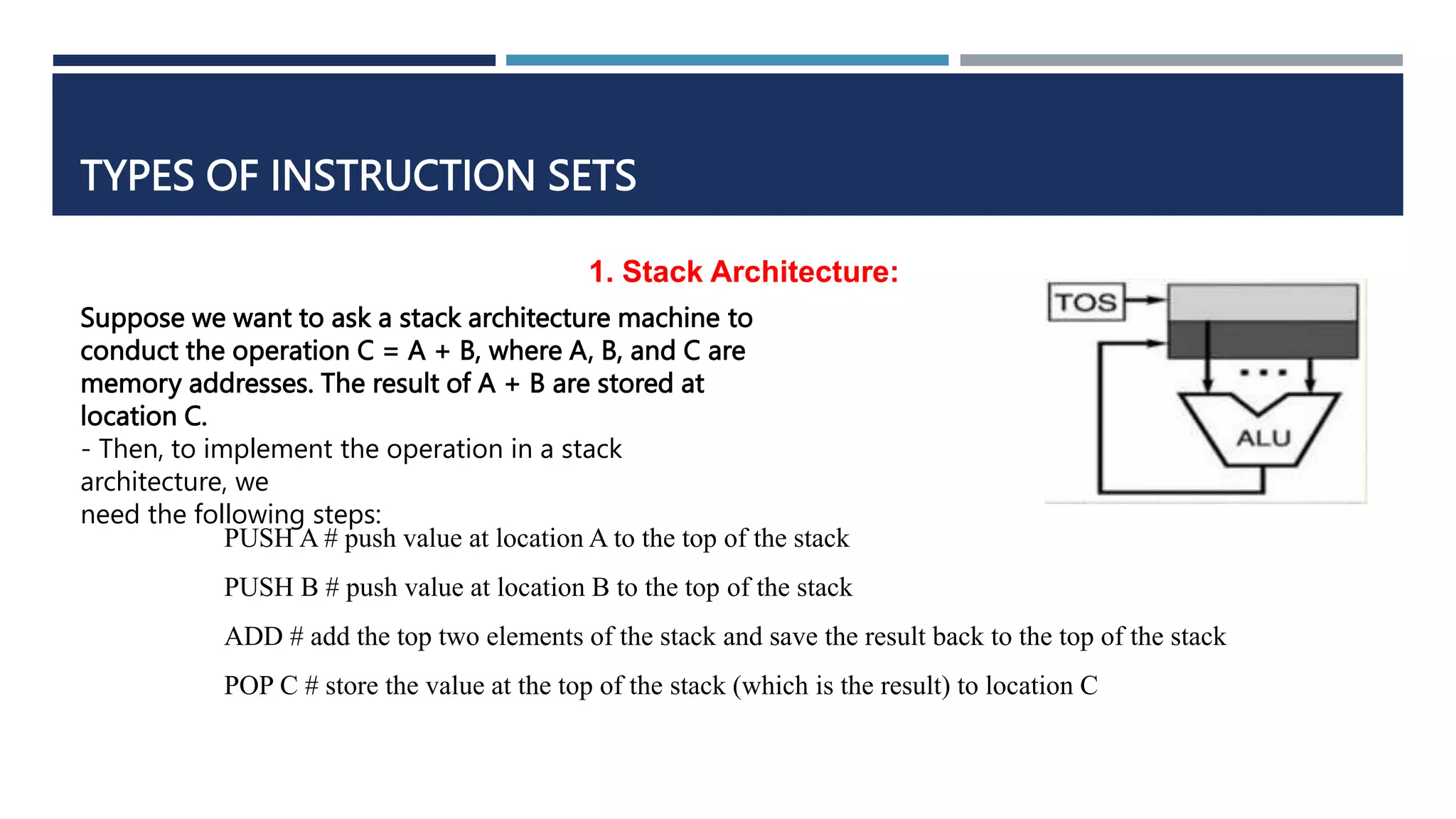
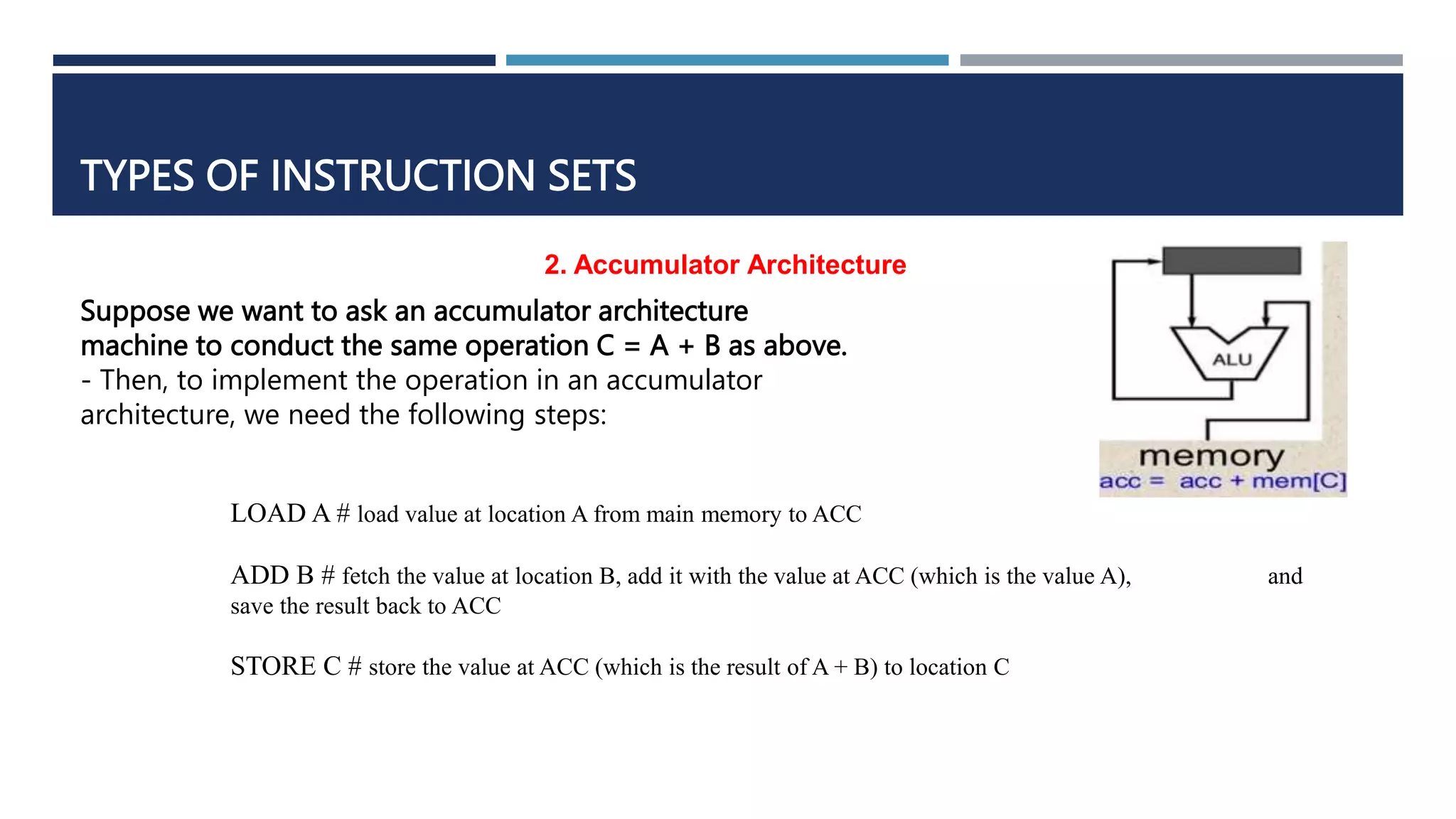
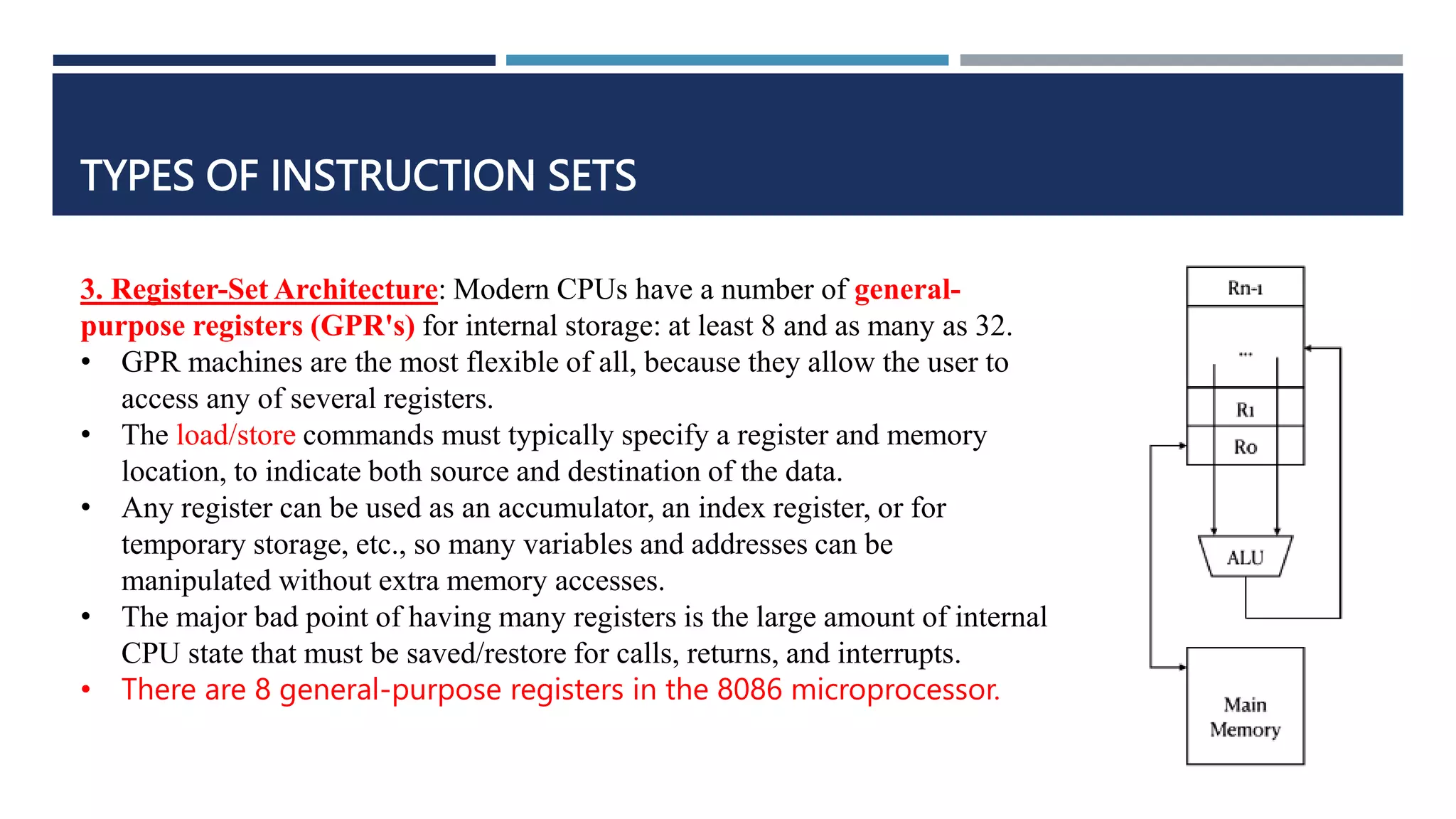
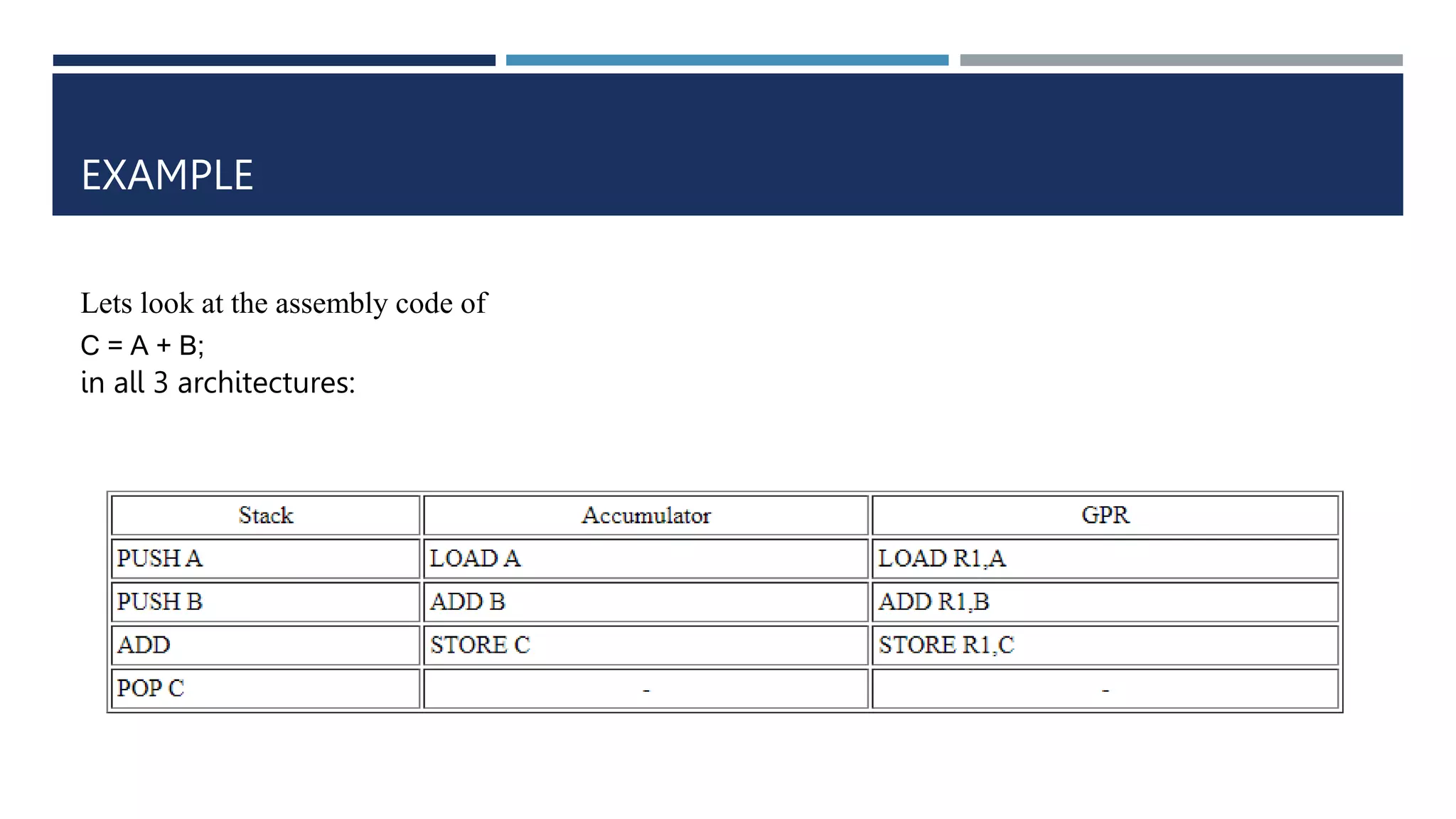
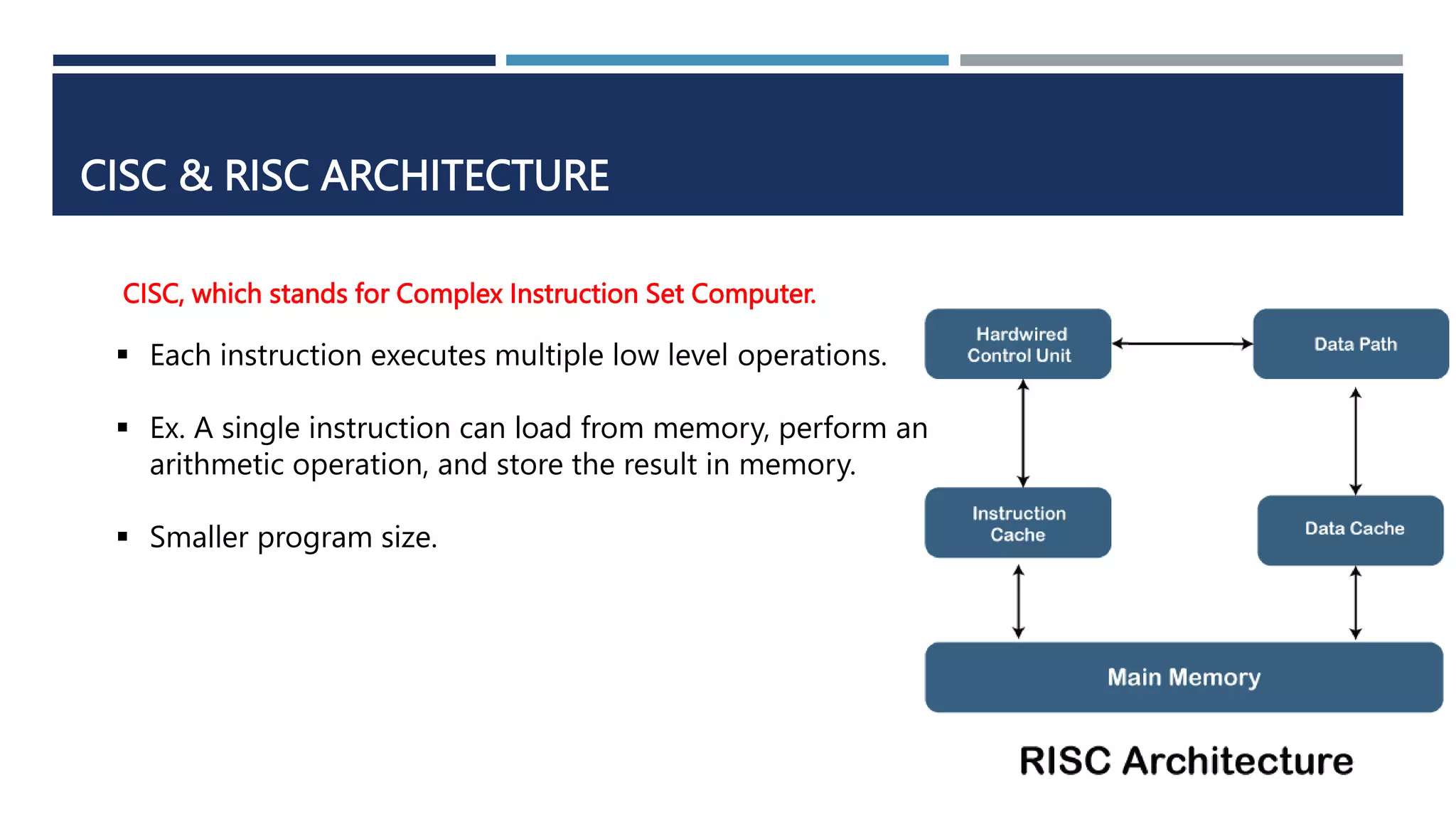
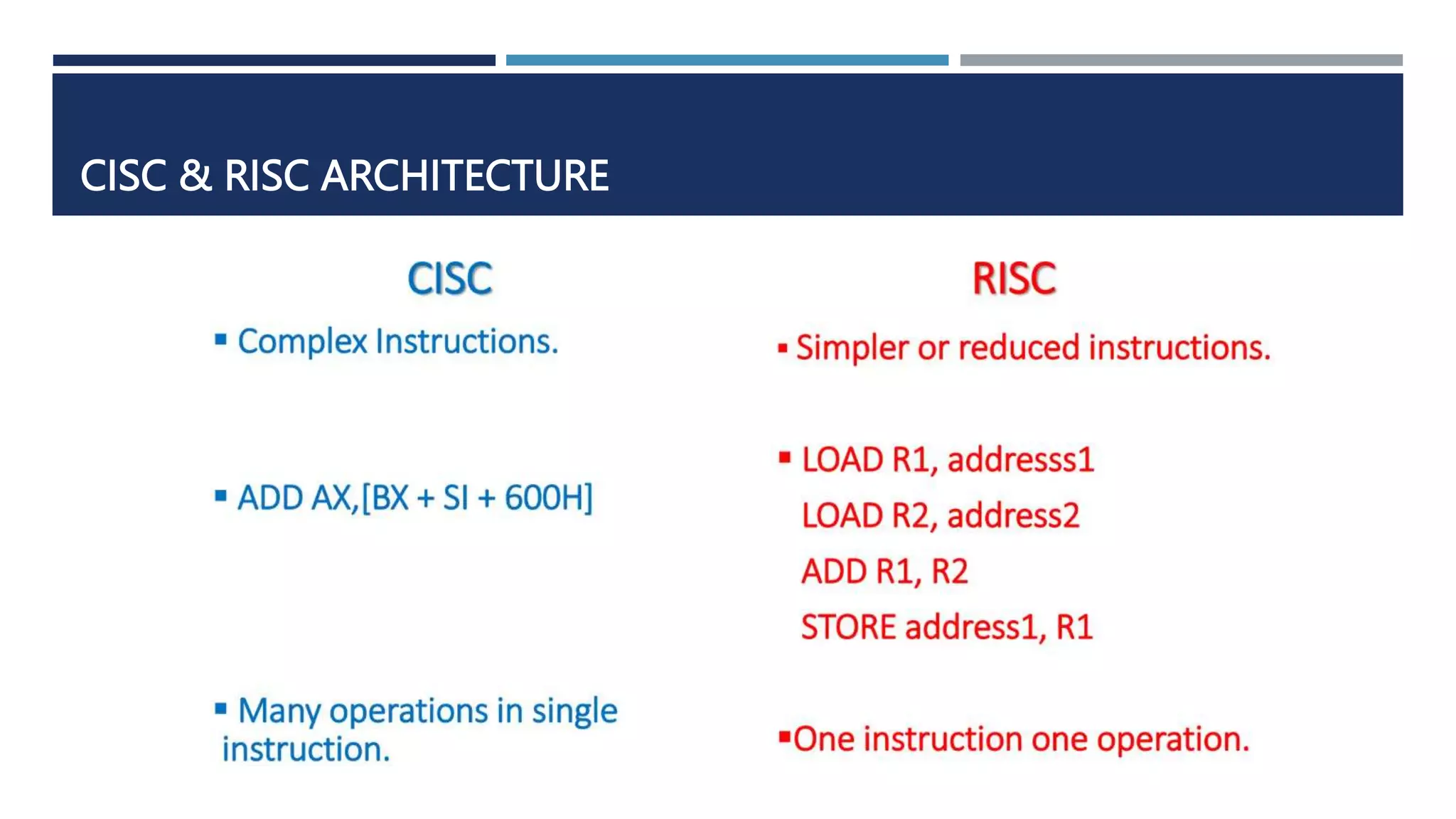
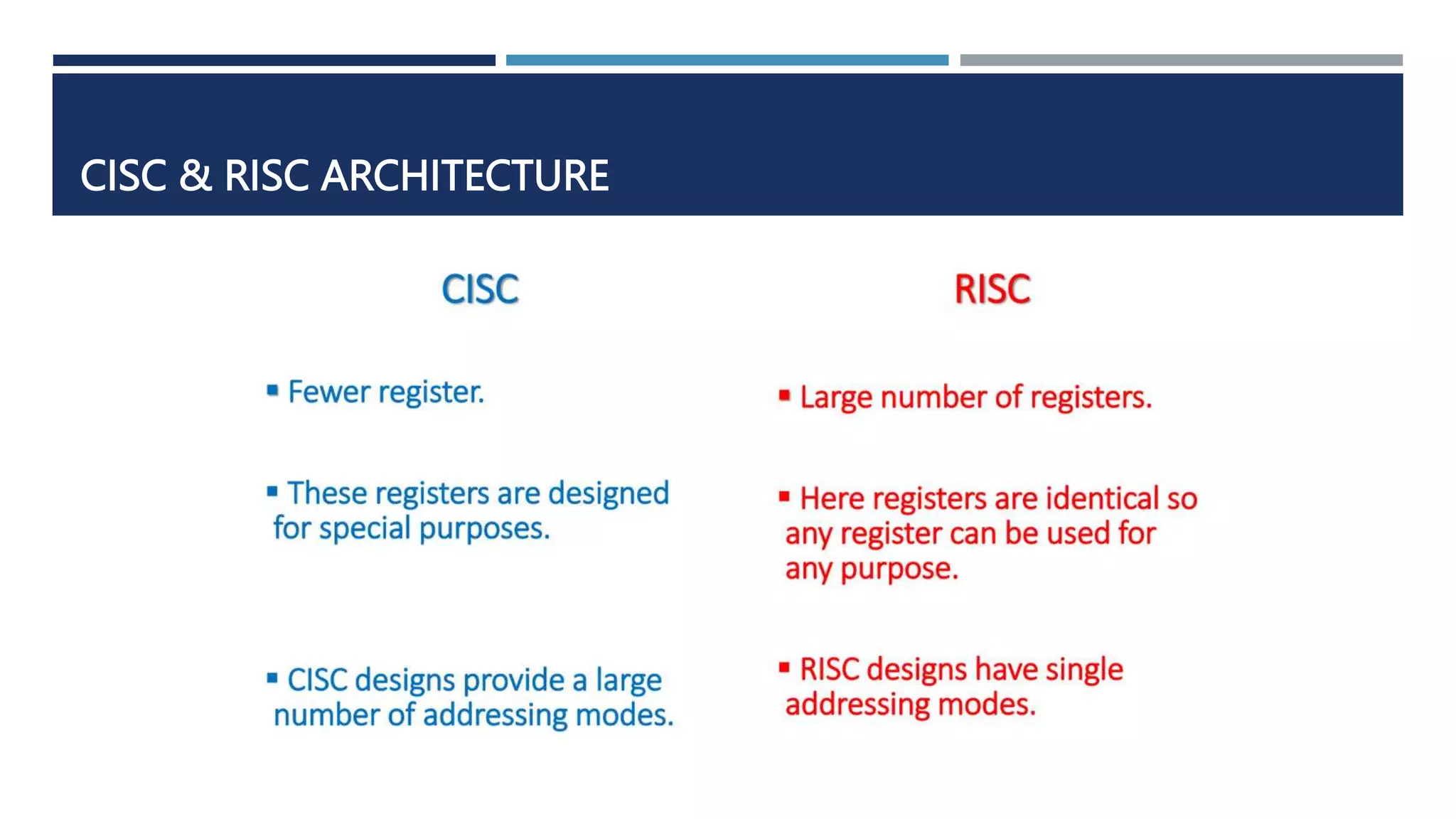
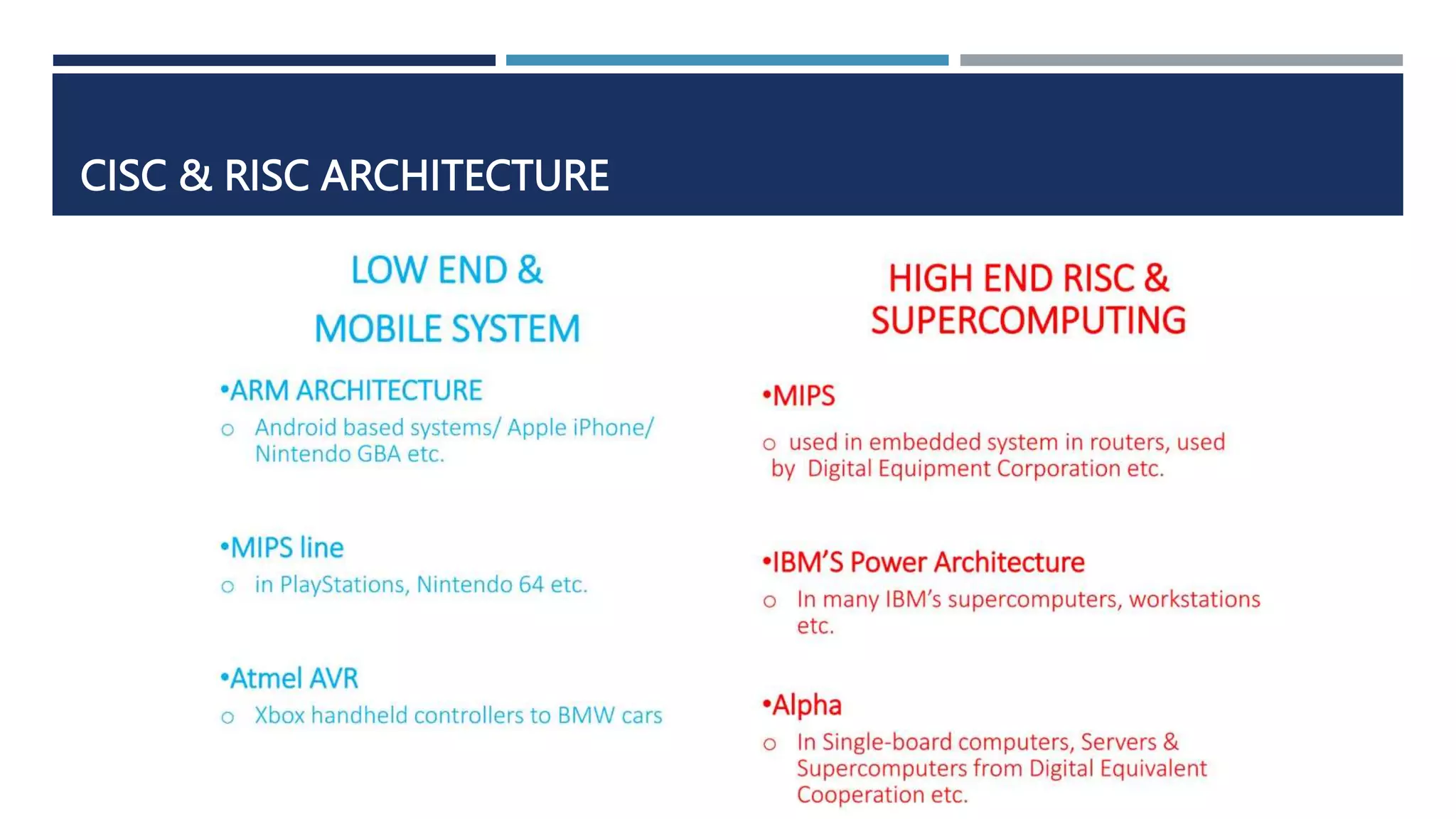
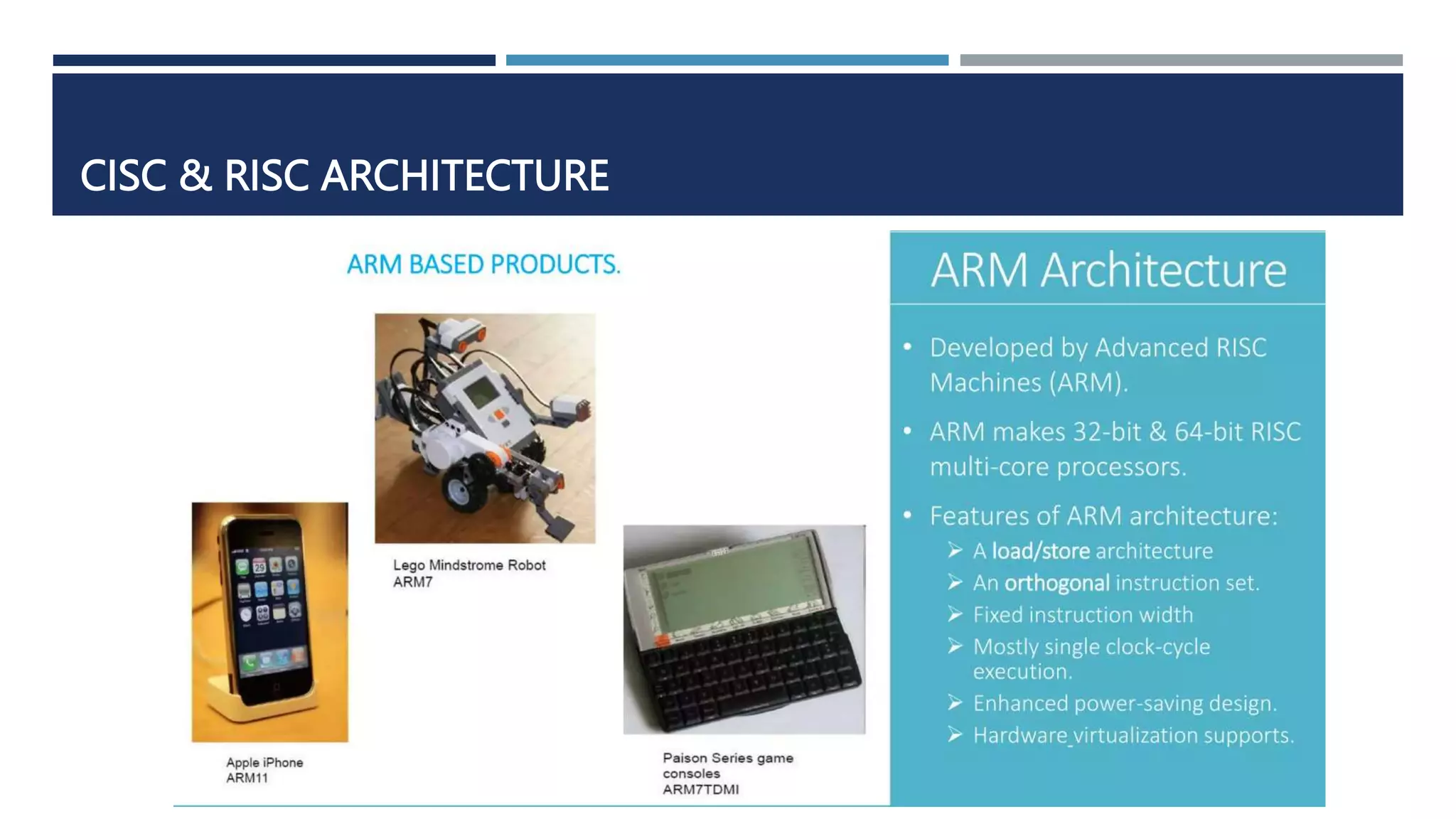
The document discusses instruction set architecture (ISA), which defines the interface between software and hardware. It describes ISA as specifying storage locations, operations, and how to invoke and access them. The document then compares ISA to human language and discusses program compilation. It outlines the basic instruction execution model of fetching, decoding, executing and writing instructions. The document also describes different types of instruction sets like stack, accumulator and register-set architectures. Finally, it contrasts complex instruction set computers (CISC) with reduced instruction set computers (RISC).