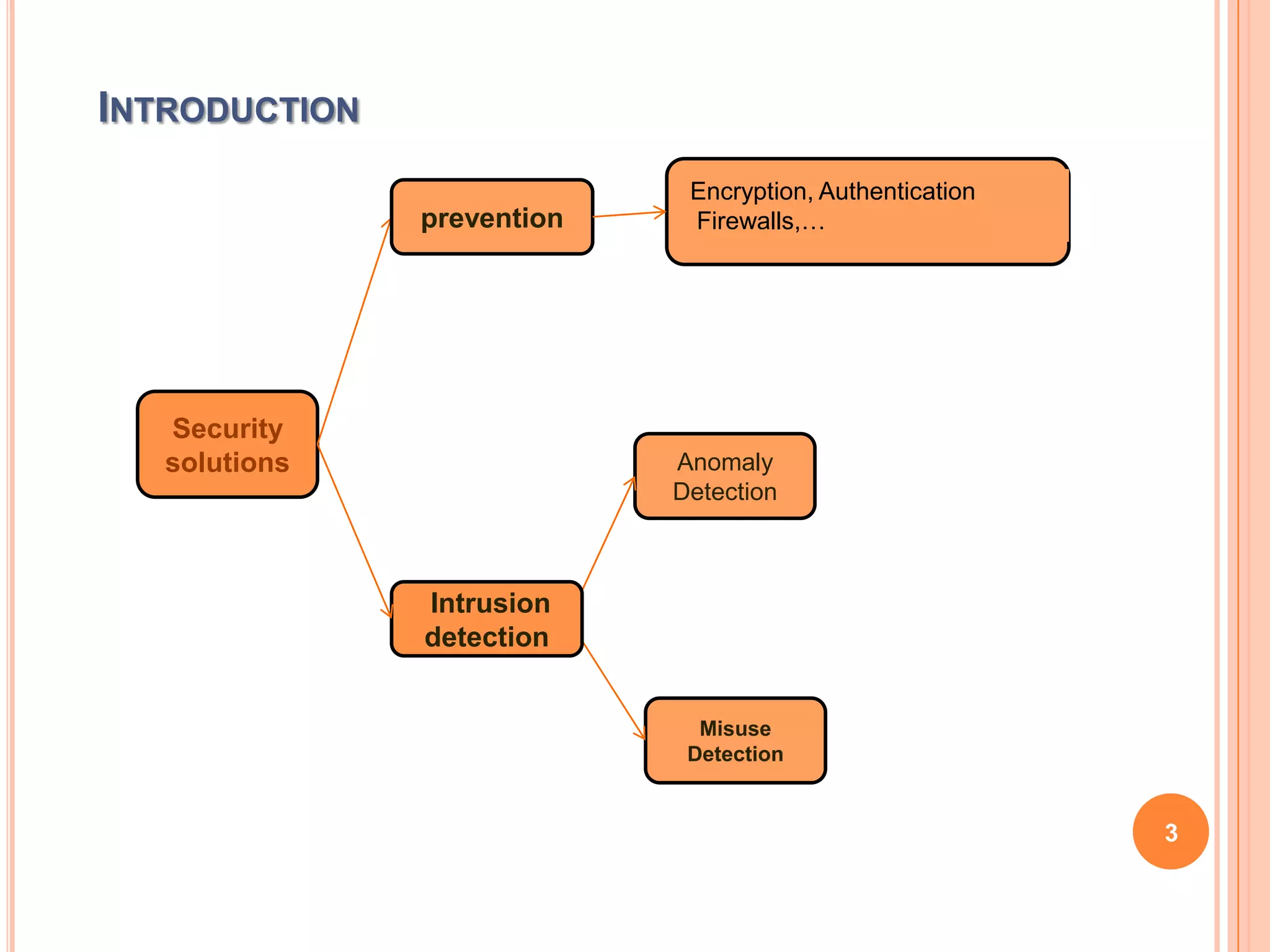
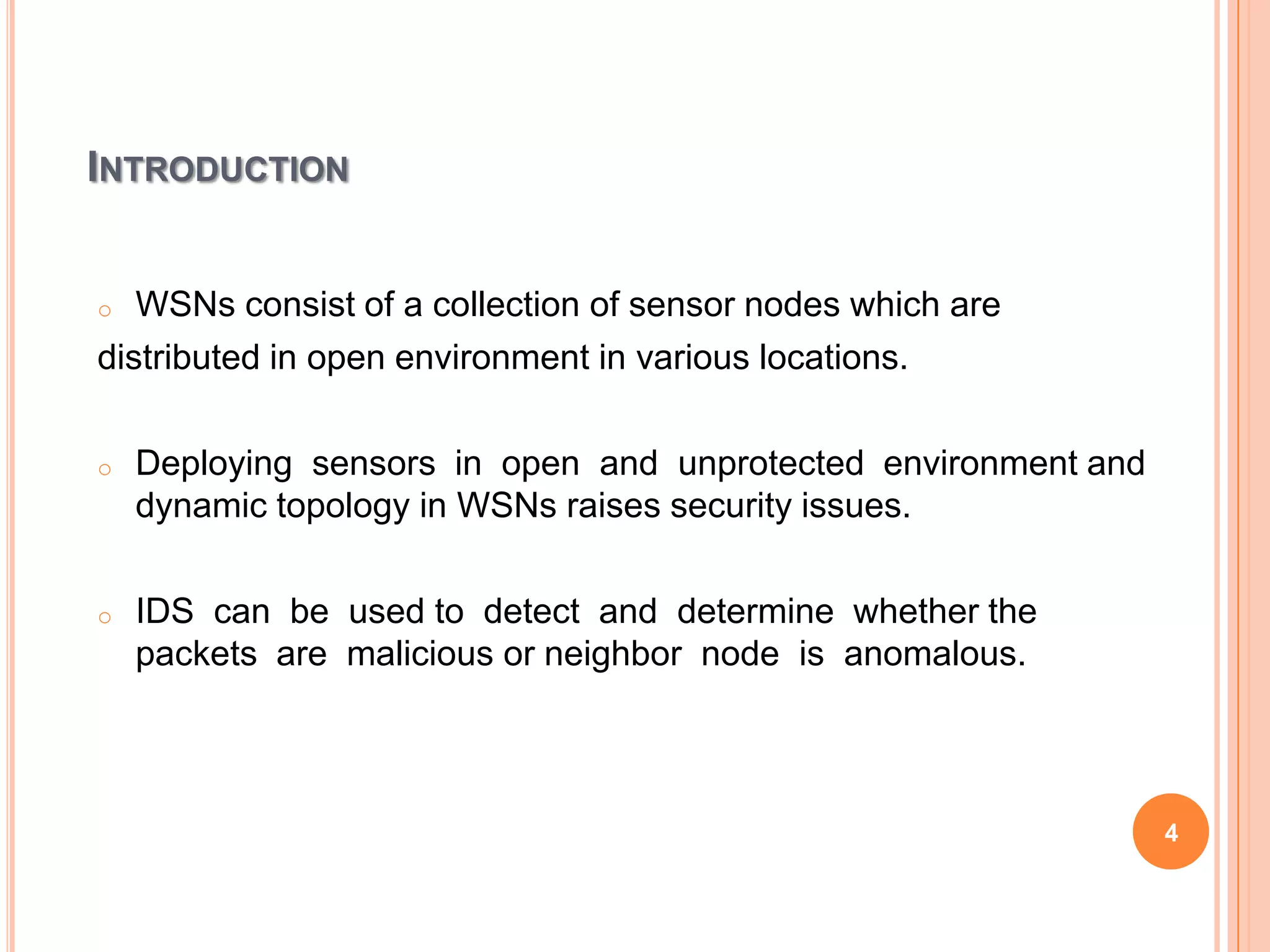
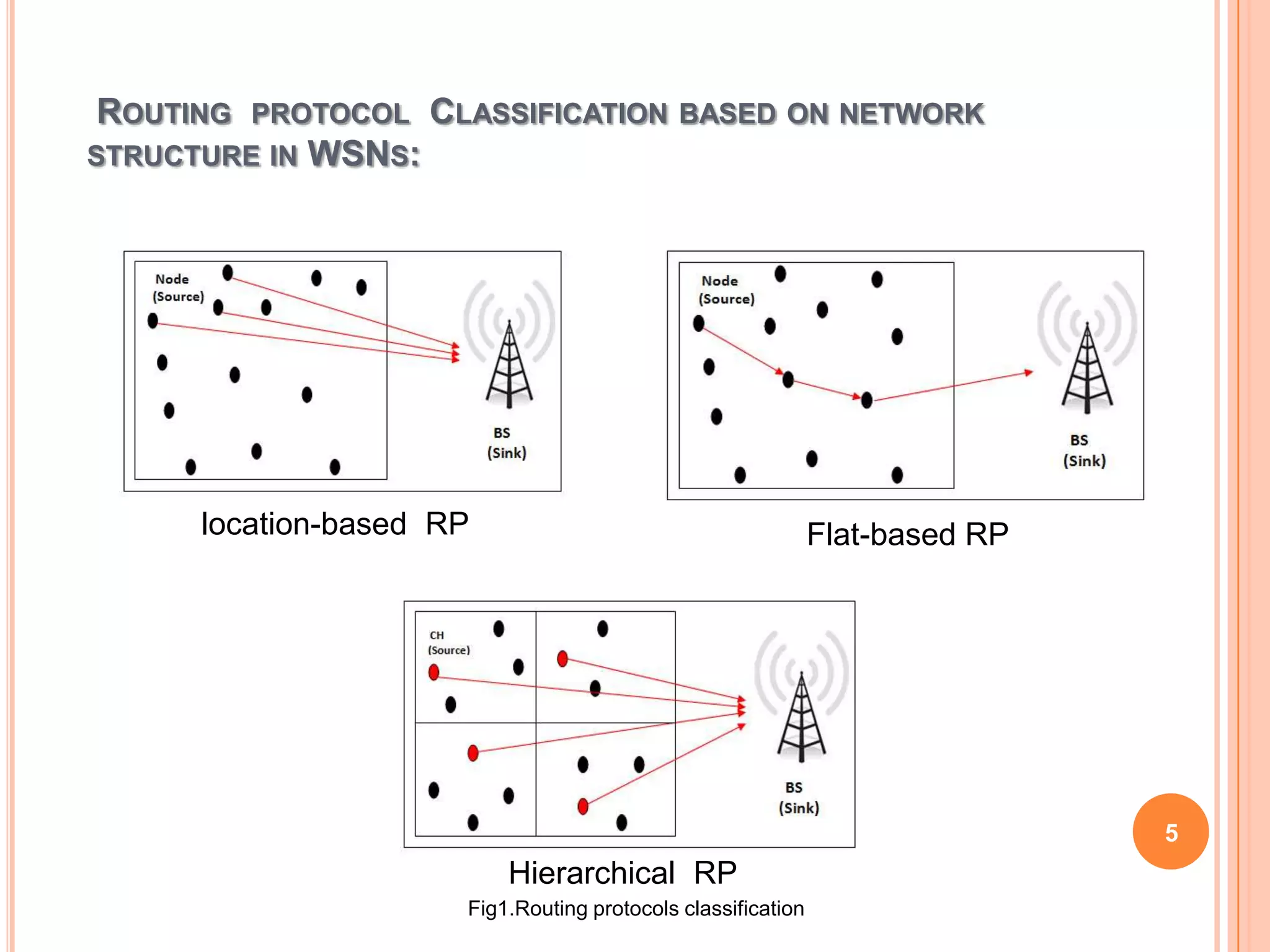
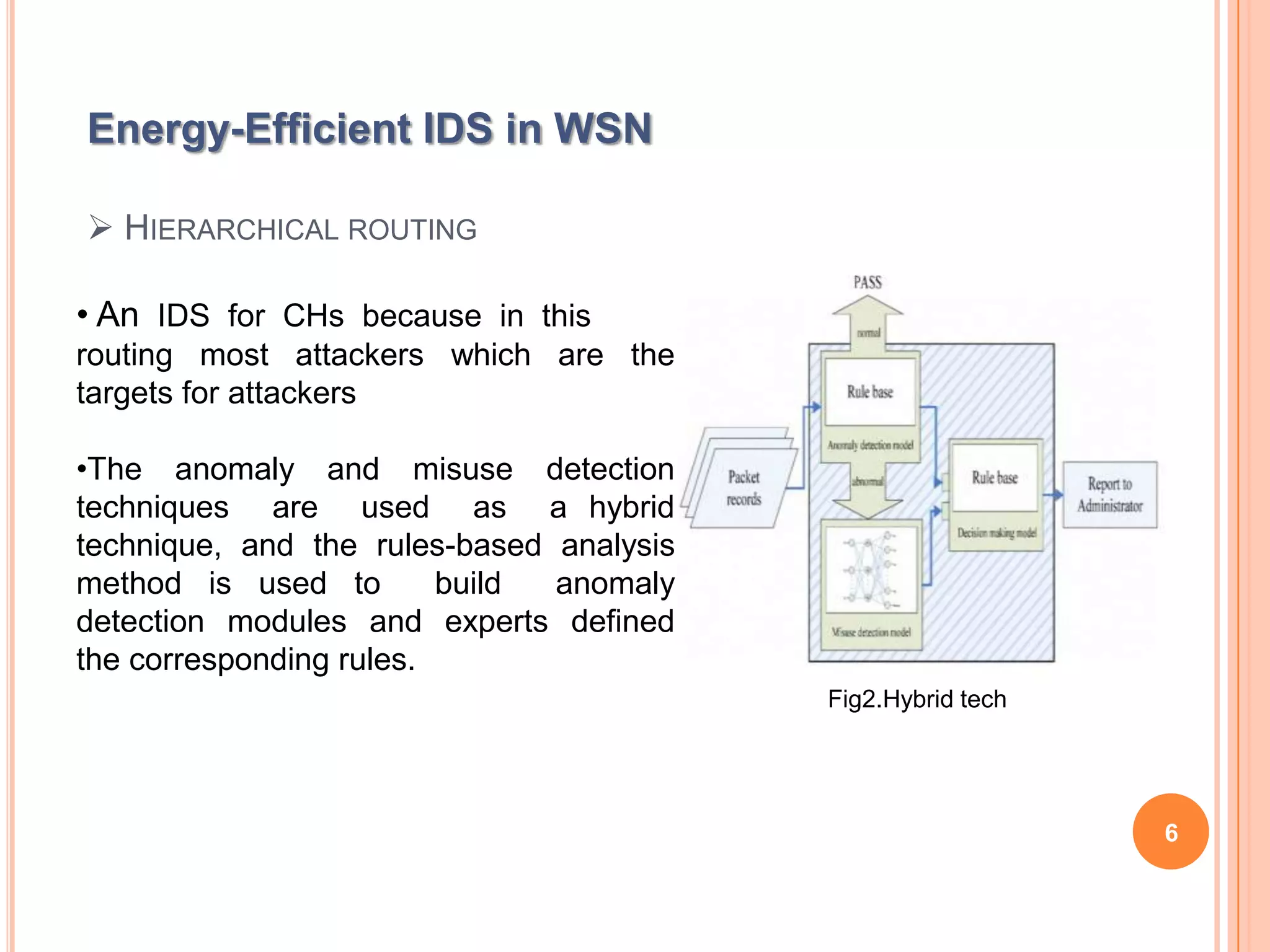
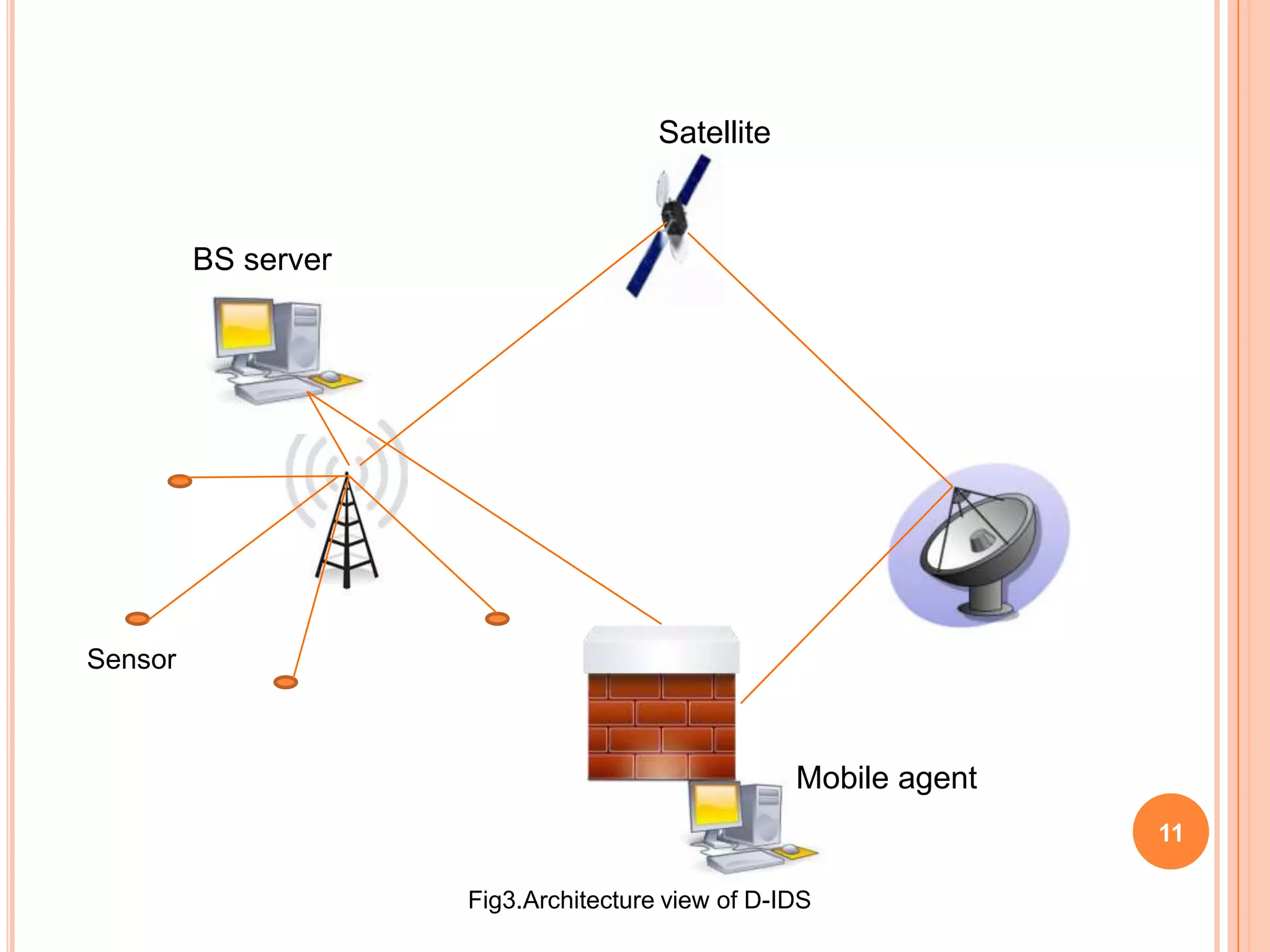
The document discusses energy-efficient intrusion detection techniques for wireless sensor networks. It summarizes routing protocols used in WSNs and proposes using hybrid anomaly and misuse detection at cluster heads in hierarchical routing to increase detection rates while reducing energy consumption. For flat-based routing, it suggests using statistical anomaly detection at each node. For location-based routing, it proposes detecting intrusions based on location and trust information to limit communication between distant nodes and the base station. Simulation results on real sensor network data show the approaches can effectively detect intrusions while preserving energy.






![REFERENCES
[1] C. F. García-Hernández, P. H. Ibargüengoytia-González, J. García-Hernández, and J. A. Pérez-Díaz (2007).
Wireless Sensor Networks and Applications: A Survey, in International Journal of Computer Science Issues
(IJCSI), 7(30):264-273.
[2] P. García-Teodoro, J. Díaz-Verdejo, G. Maciá-Fernández, and E. Vázquez (2009), Anomaly-based
Network Intrusion Detection: Techniques, Systems and Challenges. Computers & Security, 28(1–
2):18–28.
[3] A. Patcha and J-M. Park (2007), An Overview of Anomaly Detection Techniques: Existing Solutions
and Latest Technological Trends. Computer Networks, 51(12):3448–3470.
[4] Q. Wang, S. Wang and Z. Meng (2009), Applying an Intrusion Detection Algorithm to Wireless Sensor
Networks. In Procs. Second International Workshop on Knowledge Discovery and Data Mining (WKDD
2009), pp. 284–287.
[5] K.Q. Yan, S. C. Wang., S.S. Wang and C.W. Liu (2010), Hybrid Intrusion Detection System for
Enhancing the Security of a Cluster-based Wireless Sensor Network. In Proceedings of the Computer
Science and Information Technology (ICCSIT), July 2010, vol.1, pp.114-118.
[6] J. N. Al-Karaki and A. E. Kamal (2004), Routing Techniques in Wireless Sensor Networks: A Survey. IEEE
Wireless Communications, 11(6):6–28.
[7] L. J. G. Villalba, A. L. S. Orozco, A. T. Cabrera, and C. J. B. Abbas (2009), Routing Protocols in Wireless
Sensor Networks, Sensors, 9(11):8399–8421.
[8] D. Liu and Q. Dong (2007), Detecting misused keys in wireless sensor networks. In Procs. IPCCC 2007, April
2007, pp. 272 - 280.
[9] M-W. Park, J-M. Kim, Y-J. Han, and T-M. Chung (2008), A Misused Key Detection Mechanism for Hierarchical
Routings in Wireless Sensor Network. In Fourth International Conference on Networked Computing and
14
Advanced Information Management 2008 (NCM’08), pp. 47–52.](https://image.slidesharecdn.com/idspresentation-120904105505-phpapp01/75/Ids-presentation-14-2048.jpg)
![REFERENCES CONT…
[10] M. K. Watfa, and S. Commuri (2006), Energy-efficient Approaches to Coverage Holes Detection inWireless Sensor
Networks. In IEEE International Symposium on Intelligent Control, 4-6 Oct. 2006, Munich, Germany, pp. 131–136.
[11] C-F. Hsieh, Y-F. Huang, and R-C. Chen (2011), A Light-Weight Ranger Intrusion Detection System on Wireless Sensor
Networks. In 2011 Fifth International Conference on Genetic and Evolutionary Computing (ICGEC), pp. 49–52.
[12] L. Guorui, J. He, and Y. Fu (2008), Group-based Intrusion Detection System in Wireless Sensor Networks,
Computer Communications, 31(18):4324–4332.
[13] I. Onat and A. Miri (2005), An intrusion detection system for Wireless sensor networks, in Procs. IEEE International
Conference on Wireless And Mobile Computing, Networking and Communications (WiMob'2005), 22-24 Aug.
2005, pp. 253–259.
[14] S. Janakiraman, S. Rajasoundaran, and P. Narayanasamy (2012). The Model #x2014: Dynamic and Flexible Intrusion
Detection Protocol for
High Error Rate Wireless Sensor Networks Based on Data Flow. In 2012 International Conference on Computing,
Communication and
Applications (ICCCA), pp. 1 –6.
[15] M.A. Rassam, M.A. Maarof, and A. Zainal (2011). A Novel Intrusion Detection Framework for Wireless Sensor Networks.
In 2011 7th
International Conference on Information Assurance and Security (IAS), pp. 350 –353.
[16] T. Zahariadis, P. Trakadas, S. Maniatis, P. Karkazis, H. C. Leligou, and S. Voliotis (2009), Efficient Detection of Routing
Attacks in Wireless
Sensor Networks. In 16th International Conference on Systems, Signals and Image Processing (IWSSIP 2009), pp. 1–4.
[17] S. I. Eludiora, O. O. Abiona, A. O. Oluwatope, S. A. Bello, M.L. Sanni, D. O. Ayanda, C.E. Onime, E. R. Adagunodo, and L.O.
Kehind (2011), A Distributed Intrusion Detection Scheme for Wireless Sensor Networks, in Procs. IEEE
International Conference on Electro/Information Technology (EIT) 2011, pp.1-5.
15
[18] SmartDetect WSN Team (2010), SmartDetect: An Efficient WSN Implementation for Intrusion Detection in 2010
Second International Conference on Communication Systems and Networks (COMSNETS), pp. 1 –2.](https://image.slidesharecdn.com/idspresentation-120904105505-phpapp01/75/Ids-presentation-15-2048.jpg)
![REFERENCES CONT…
[19] M. Khan, G. Pandurangan, and V. S. Anil Kumar (2009). Distributed algorithms for constructing
approximate minimum spanning trees in wireless sensor networks, IEEE Transactions on Parallel
and Distributed Systems, 20:124–139, Jan. 2009.
[20] R. Subramanian, P.V. Kumar, S. Krishnan, B. Amrutur, J. Sebastian, M. Hegde, S.V.R. Anand (2009).
A low-complexity algorithm for intrusion detection in a pir-based wireless sensor network, in
International Conference Series on Intelligent Sensors, Sensor Networks and Information Processing.
[21] F. Ye, G. Zhong, S. Lu, and L. Zhang (2005). Gradient broadcast: a robust data delivery protocol
for large scale sensor networks, Wirel. Netw., 11(3):285–298.
[22] http://www.wsn-roup.org/comment/13#comment-13
[23] J. Yick, B. Mukherjee, and D. Ghosal (2008), Wireless Sensor Network Survey. Computer Networks , 52(12):
2292–2330.
[24] W. Seah and Y. K. Ta, (2010). Chapter 12: Routing Security Issues in Wireless Sensor Networks: Attacks
and Defenses, in Sustainable Wireless Sensor networks, pp. 279-308.
[25] Bc. L. Honus (2009). Design, Implementation and simulation of
intrusion detection system for wireless sensor networks, M.S. Thesis,
Masarykova Univerzita, Czech.
16](https://image.slidesharecdn.com/idspresentation-120904105505-phpapp01/75/Ids-presentation-16-2048.jpg)
