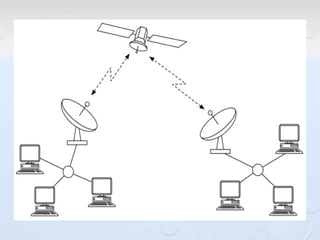
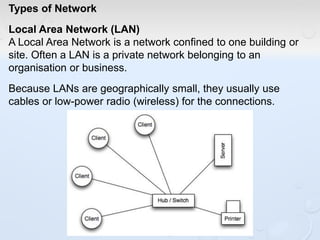
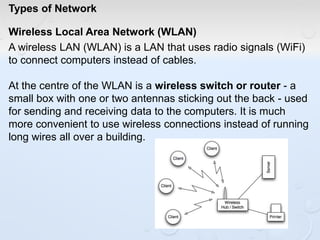
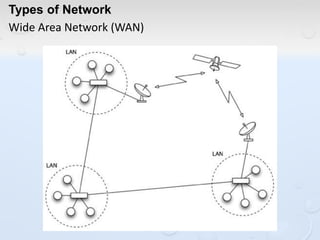
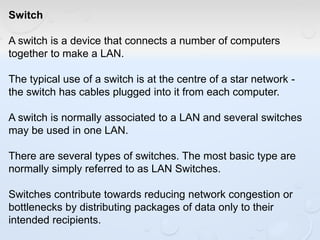
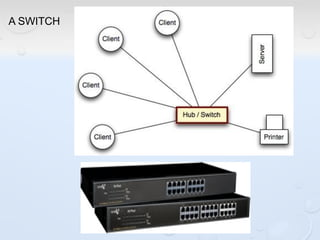
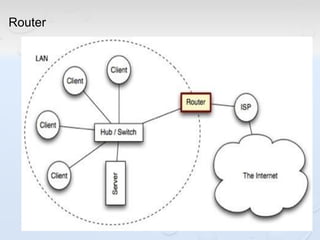
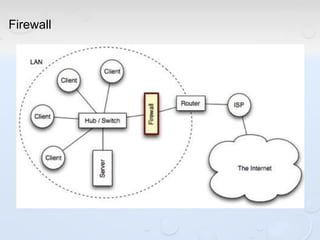
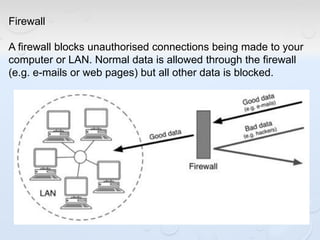
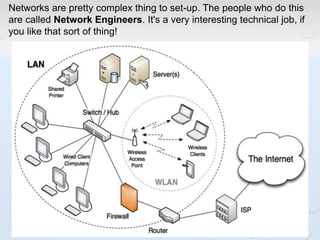
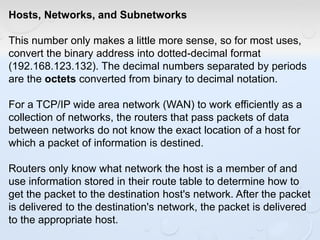
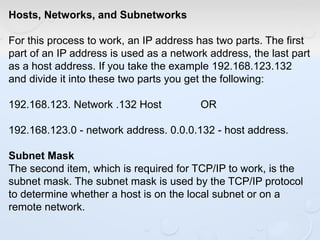
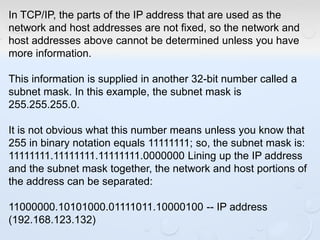
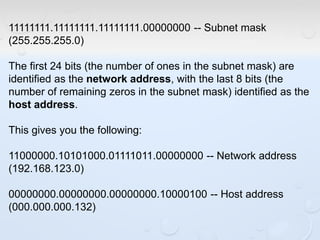
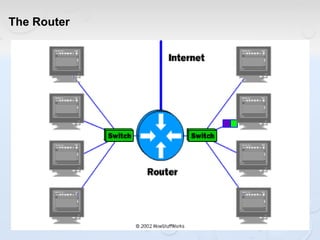
A network allows computers to share resources like files, printers and internet connections. It connects devices using cables, wireless or other connections. A network has servers that provide services to client computers. The internet is a global network that connects millions of devices using common protocols like TCP/IP. TCP/IP breaks data into packets that include the destination and source addresses. Networks require hardware like switches, routers and firewalls to function properly. IP addresses and subnet masks are used to identify devices and determine if they are local or remote.