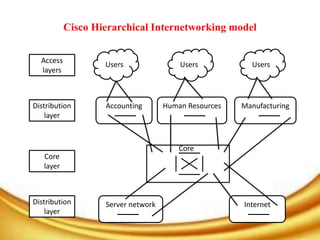
This document discusses considerations for designing a secure network. It emphasizes that network design should incorporate security from the beginning. Key aspects of design include separating assets by trust levels, using firewalls and other tools to monitor and secure multiple systems, and avoiding single points of failure to ensure availability. The Cisco hierarchical model is commonly used, with core, distribution, and access layers to efficiently move and aggregate traffic while controlling access. Performance, availability, and security should all be priorities in network planning.