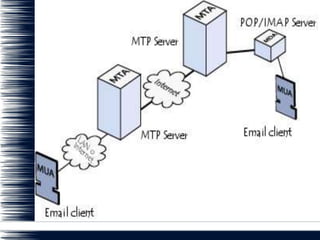
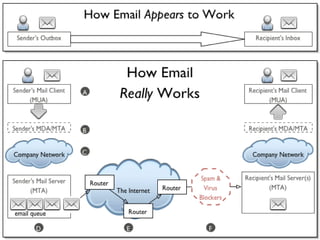
E-mail works by routing messages from server to server until it reaches the recipient's mail server. Messages are sent via SMTP servers called Mail Transport Agents (MTAs) and stored on the recipient's incoming mail server called a Mail Delivery Agent (MDA). Recipients then retrieve messages from the MDA using either POP3 or IMAP protocols. MTAs act like post offices that transport messages, while MDAs act like mailboxes that store messages until recipients access them. Retrieving mail requires a Mail User Agent like an email client or webmail interface.