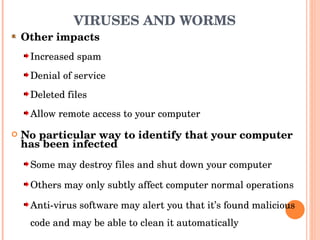
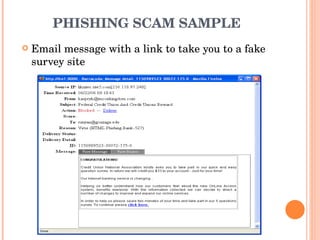
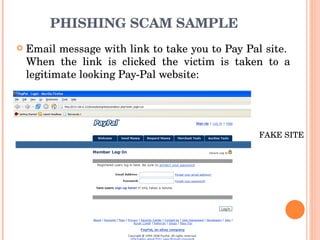
The document discusses email etiquette and security. It defines email and outlines its advantages like speedy communication. It emphasizes the importance of email etiquette for professionalism and avoiding misinterpretation. Some etiquette rules mentioned include being concise, using proper grammar, and not using all caps. Email security threats discussed include viruses, spam, and phishing. It provides examples of phishing scams and advises verifying identity before providing personal information. Measures to enhance email security include encryption, secure gateways, filtering, and compliance policies.