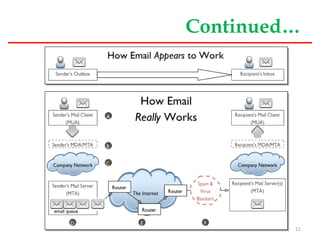
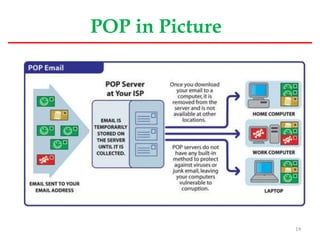
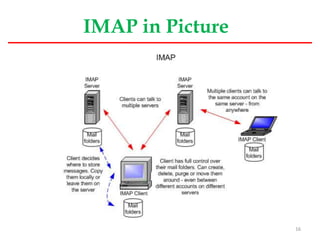
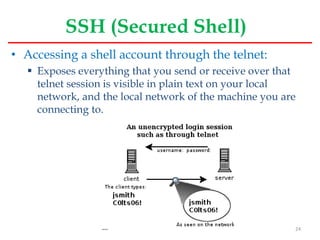
This document provides an overview of mail server basics from a Linux OS perspective. It discusses the main components of an email system including email clients, email servers, and POP and IMAP servers. It describes how email is sent and received, including the roles of SMTP, POP, and IMAP protocols. It also covers email administration tasks in Linux like configuring the hostname, timezone and hosts file. Remote administration tools like Webmin and secure remote access with SSH are also summarized.