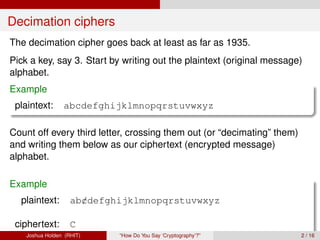
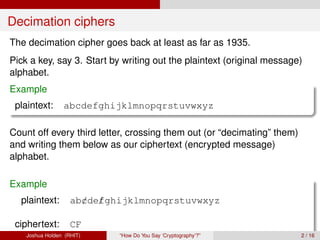
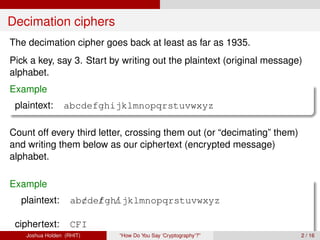
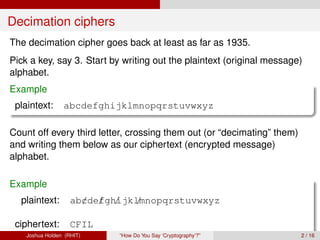
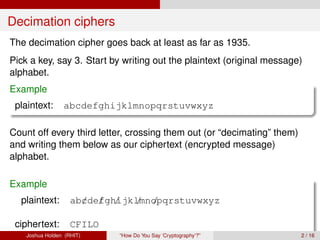
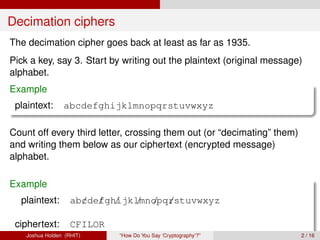
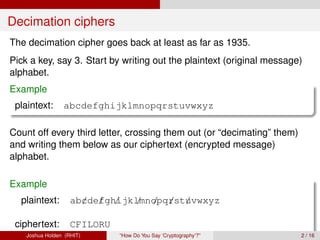
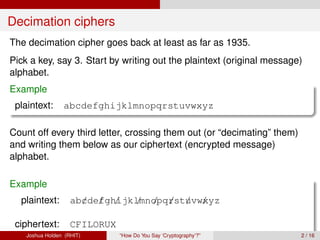
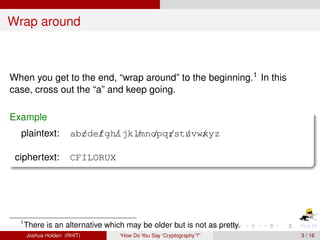
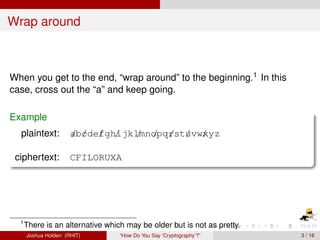
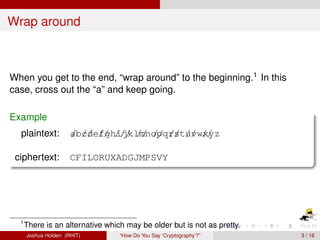
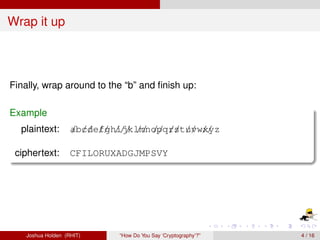
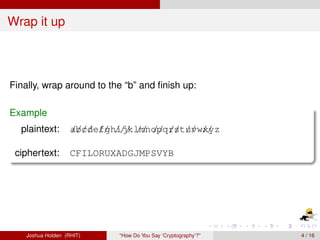
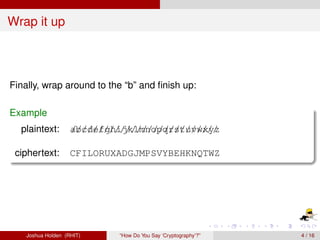
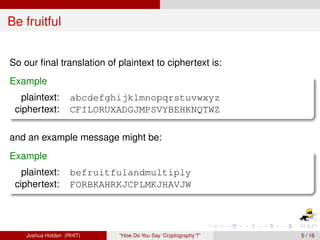
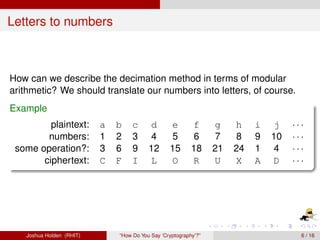
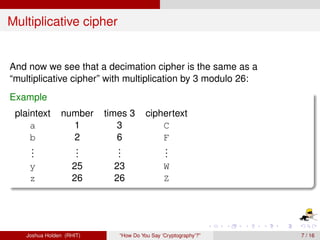
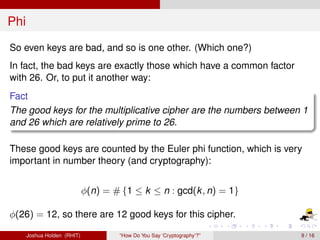
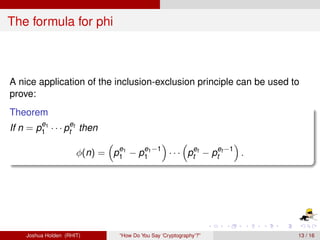
The document discusses decimation ciphers and how they relate to modular arithmetic. It explains that a decimation cipher is a type of multiplicative cipher where each letter is multiplied by a key modulo the number of letters in the alphabet. Only certain keys work well, namely those relatively prime to the alphabet size. The document explores this concept for different languages and their alphabets.