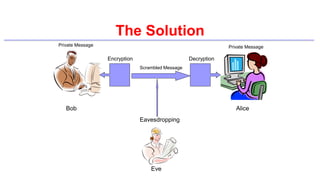
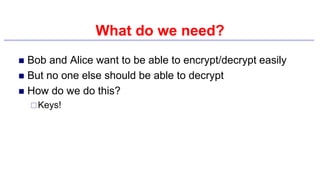
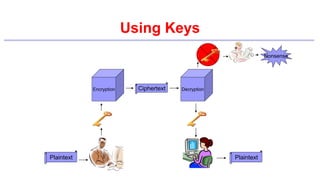
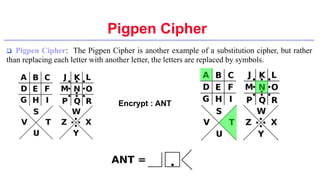
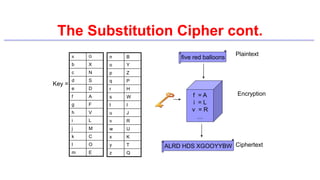
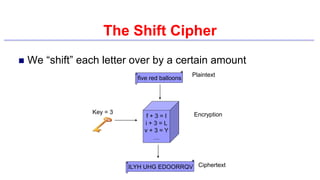
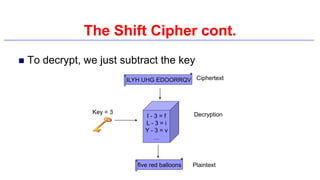
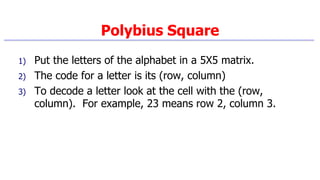
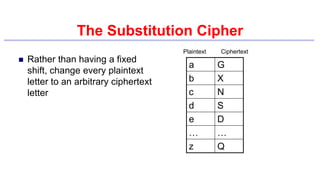
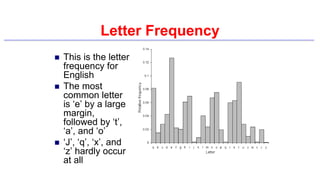
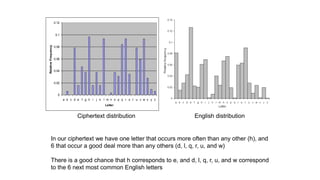
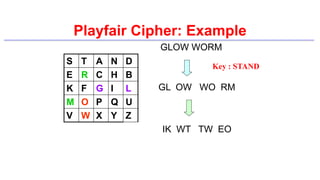
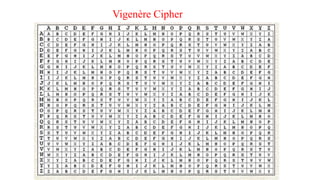
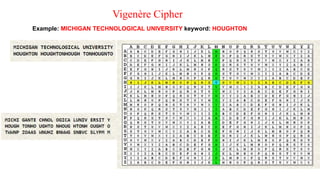
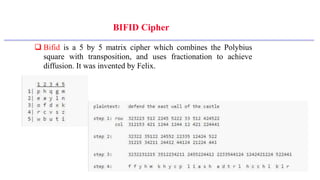
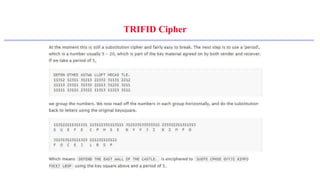
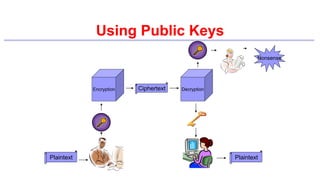
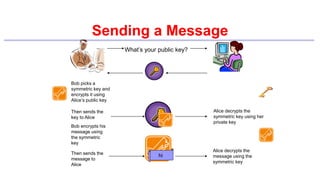
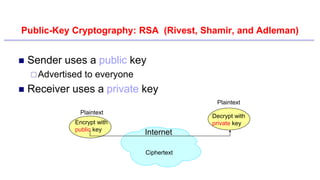
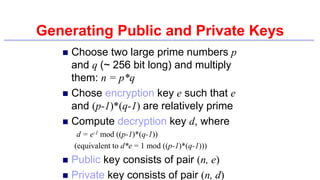
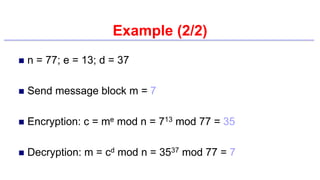
This document provides an introduction to classical ciphers and cryptography techniques. It discusses the components of information security - confidentiality, integrity and availability. It then covers various monoalphabetic and polygraphic substitution ciphers such as the Caesar, Atbash, Pigpen, Playfair and Vigenère ciphers. It also discusses transposition ciphers like the Rail Fence cipher and techniques for analyzing ciphertexts such as frequency analysis. Finally, it introduces bifid, trifid and four square ciphers. The document serves as a comprehensive overview of fundamental classical cryptography concepts.