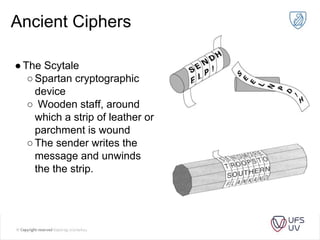
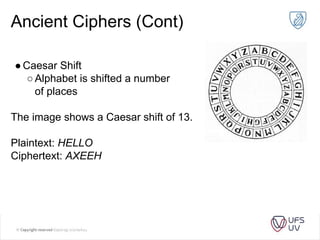
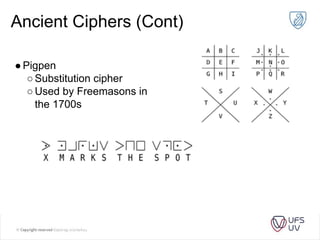
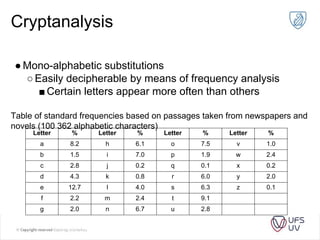
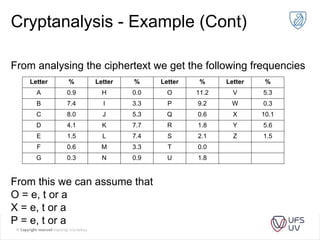
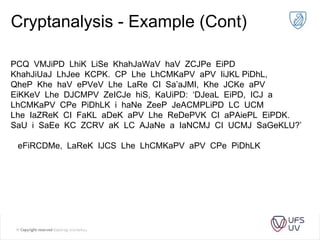
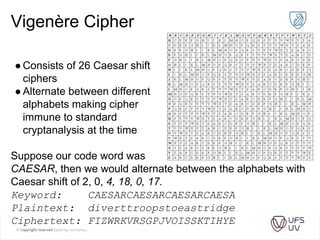
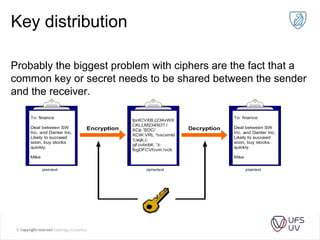
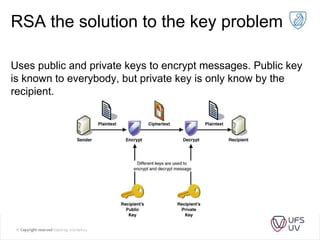
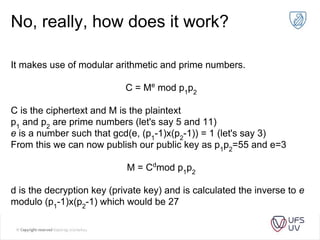
The document discusses various methods of cryptography throughout history including steganography, ancient ciphers like the Scytale and Caesar cipher, cryptanalysis techniques using frequency analysis, the Vigenère cipher, public key cryptography including RSA, and quantum key distribution. It provides examples to illustrate cryptanalysis and how RSA encryption and decryption works using modular arithmetic on prime numbers. Vulnerabilities of RSA are mentioned along with the promise of QKD for secure key exchange.