A Good Hash Function is Hard to Find, and Vice Versa
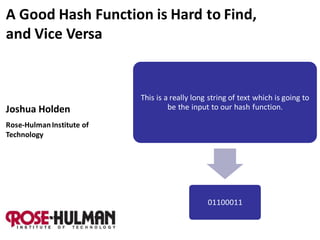
- 1. A Good Hash Function is Hard to Find, and Vice Versa This is a really long string of text which is going to Joshua Holden be the input to our hash function. Rose-Hulman Institute of Technology 01100011
- 2. A hash function is any function which takes an arbitrarily long string as input and gives a fixed-length output. Input: (“Message”) This is a really long string of text which is going to be the input to our hash function. Output: 01100011 (“Hash value”) 2
- 3. An example: Write the message in rows of five letters, convert to numbers, add down the columns modulo 26. Input: HELLO 07 04 11 11 14 (“Message”) MYNAM 12 24 13 00 12 EISAL 04 08 18 00 11 ICEXX 08 02 04 23 23 05 12 20 08 08 Output: F M U I I (“Hash value”) [Barr, Invitation to Cryptology] 3
- 4. A hash function is not: M h M an encoding. 4
- 5. A hash function is not: M h M M M M h h h an encoding. secret. 5
- 6. What is a hash function good for? Maybe to make sure a message hasn’t been altered. Alice Eve Bob Hi, Bob, this is Hi, Bob, this is Hi, Bob, this is Eve. Alice. Eve. 00011100 00011100 00110001, not 00011100 6
- 7. What is a hash function good for? Maybe to make sure a message hasn’t been altered. Hey! Alice Eve Bob Hi, Bob, this is Hi, Bob, this is Hi, Bob, this is Eve. Alice. Eve. 00011100 00011100 00110001, not 00011100 7
- 8. But of course, Eve could change the hash value as well as the message. ? Alice Eve Bob Hi, Bob, this is Hi, Bob, this is Hi, Bob, this is Eve. Alice. Eve. 00011100 00110001 Hash values by themselves only protect against 00110001 unintentional changes. 8
- 9. Alice could prevent this by “digitally signing” the hash value. Alice Eve Bob Hi, Bob, this is Hi, Bob, this is Hi, Bob, this is Eve. Alice. Eve. 00011100 00011100 Digitally signing a hash value is much more 00110001 efficient than signing a whole message! 9
- 10. What properties do we want a hash function to have? 1. It should be fast to compute. 10
- 11. What properties do we want a hash function to have? 1. It should be fast to compute. 2. It should distribute hash values evenly. M1 M2 M3 M4 M5 M6 h1 h2 h3 11
- 12. But for cryptographic purposes a hash function should also be “cryptographically secure”. M h 1. “One-way” a.k.a. “preimage-resistant” 12
- 13. But for cryptographic purposes a hash function should also be “cryptographically secure”. M h 1. “One-way” a.k.a. “preimage-resistant” M1 2. “Second-preimage resistant” M2 h 13
- 14. But for cryptographic purposes a hash function should also be “cryptographically secure”. M h 1. “One-way” a.k.a. “preimage-resistant” M1 2. “Second-preimage resistant” M2 h M1 h 3. “Collision-resistant” M2 14
- 15. One common way that real hash functions achieve these goals is with the Merkle-Damgård construction. [Wikipedia] IV = Initialization vector f = Compression function If the compression function is collision-resistant, then so is the hash function. 15
- 16. Some common hash functions that use the Merkle-Damgård construction: [Wikipedia] By Ronald Rivest: By NIST and the NSA: • MD4 (Message Digest • SHA (Secure Hash Algorithm) algorithm 4) • SHA-1 (slightly tweaked • MD5 (an improved version version of SHA) of MD4) • SHA-2 (significant revision of SHA-1) 16
- 17. The compression function of MD5 is fairly typical of all of these ciphers. 16 “steps” message word nonlinear function diffusion round constant feedforward permutation MD5 compression function One “step” of the function [Stallings, Cryptography and Network Security] 17
- 18. My goals for a new hash function: 1. Can be done without a computer in a class period. 18
- 19. My goals for a new hash function: 1. Can be done without a computer in a class period. 2. Reasonably secure. 19
- 20. My goals for a new hash function: 1. Can be done without a computer in a class period. 2. Reasonably secure. 3. Uses elements from “real” hash functions. 20
- 21. My goals for a new hash function: 1. Can be done without a computer in a class period. 2. Reasonably secure. 3. Uses elements from “real” hash functions. 4. “Optimized” for a four-function calculator. 21
- 22. Our first example doesn’t stack up too well. HELLO 07 04 11 11 14 MYNAM 12 24 13 00 12 EISAL 04 08 18 00 11 ICEXX 08 02 04 23 23 05 12 20 08 08 F M U I I 1. Can be done without a computer in a class period? Yes. 2. Reasonably secure? No The problem is that it’s too easy to work backwards from the hash to the preimage. 22
- 23. My first try: JHA (2000) hash = (7 x # of vowels – 3 x # of consonants + # of spaces 2) modulo 17 Hello my name is Alice (7 x 8 – 3 x 10 + 42) modulo 17 = 8 1. Can be done without a computer in a class period? Yes. 2. Reasonably secure? Not especially. Preimages are not that easy, but second preimages and collisions are. 23
- 24. My second try: JHA-1 (2010) hash = 5(7 x # of vowels – 3 x # of consonants + # of spaces2) modulo 17 Hello my name is Alice 5(7 x 8 – 3 x 10 + 42) modulo 17 = 9 1. Can be done without a computer in a class period? Yes. 2. Reasonably secure? A little better. Preimages are even harder, but second preimages and collisions are still not that hard. 24
- 25. My latest try: JHA-2 (2011), uses Merkle-Damgård. Convert letters to numbers, each block is one letter (two digits) Two-digit length of message IV = 76 No special finalization 25
- 26. JHA-2 compression function: A B New message block + Operations are modulo 100 diffusion* x7 permutation feedforward + *Thanks to Michael Pridal-LoPiccolo! 26
- 27. An example: H e l l o m y n a m e i s A l i c e 07 04 11 11 14 12 24 13 00 12 04 08 18 00 11 08 02 04 18 76 + 07 new block 83 x 7 81 18 + 76 feedforward 94 + 04 new block . . 27 .
- 28. An example: H e l l o m y n a m e 07 04 11 11 14 12 24 13 00 12 04 76 94 62 73 61 13 70 55 22 67 02 26 i s A l i c e 08 18 00 11 08 02 04 18 09 07 01 49 48 53 52 61 Hello, my name is Alice. Hello, my name 61 is Alice. 61 28
- 29. An example: H e l l o m y n a m e 07 04 11 11 14 12 24 13 00 12 04 76 94 62 73 61 13 70 55 22 67 02 26 i s A l i c e 08 18 00 11 08 02 04 18 Hi, 09 07 01 49 48 53 52 61 Alice! Hello, my name is Alice. Hello, my name 61 is Alice. 61 29
- 30. T h a n k s f o r 19 07 00 13 10 18 05 14 17 76 32 69 07 11 85 97 38 84 54 l i s t e n i n g 11 08 18 19 04 13 08 13 06 18 09 00 62 38 87 87 43 72 36 23 Bye! http://www.rose-hulman.edu/~holden 30
