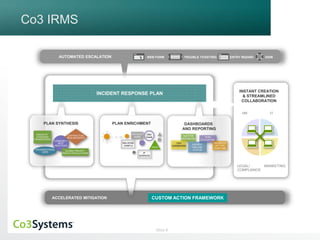
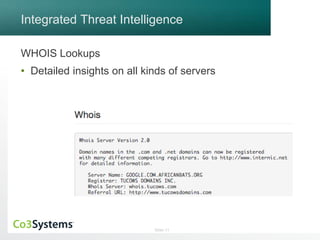
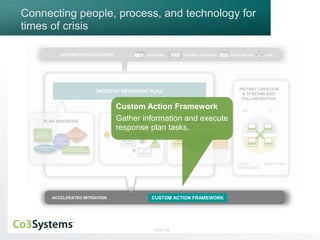
The webinar discusses Co3 Systems' incident response management software, highlighting its latest features including threat intelligence integration, easy customization, and streamlined collaboration across departments. Attendees can learn about real-time incident response planning, automated escalation processes, and the use of various dashboards for reporting and analysis. The session also emphasizes best practices for handling security incidents and improving organizational readiness.