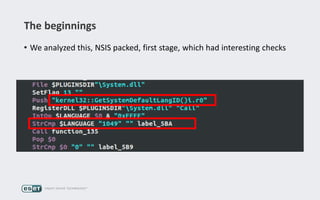
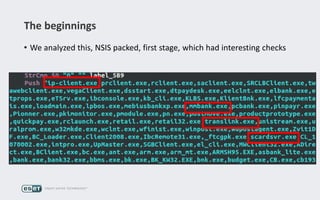
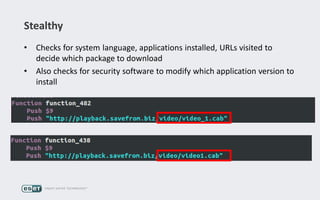
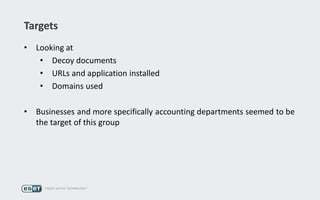
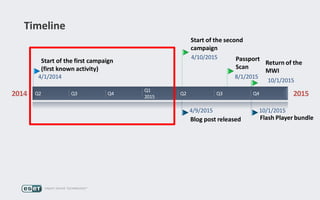
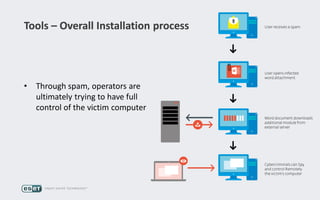
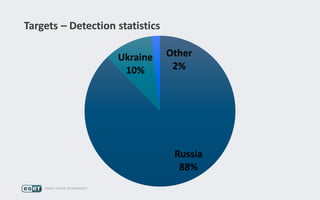
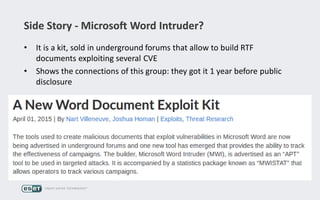
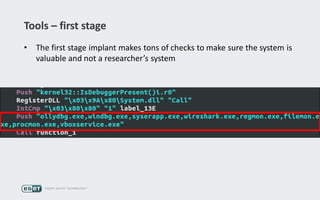
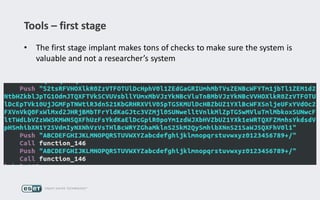
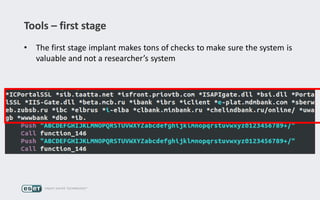
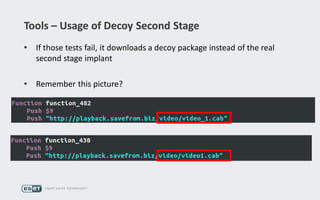
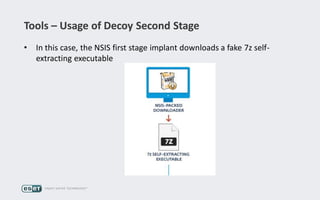
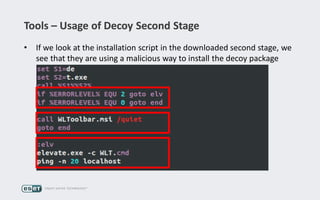
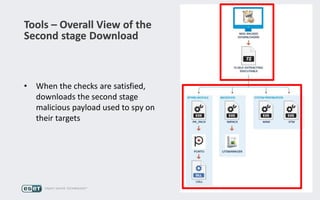
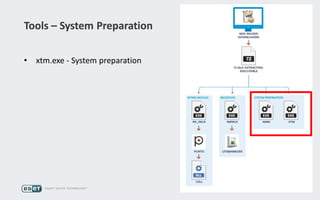
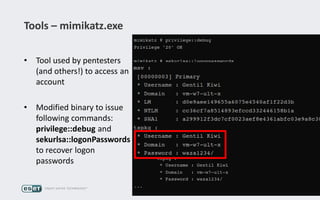
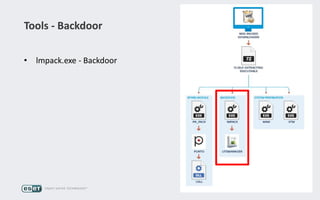
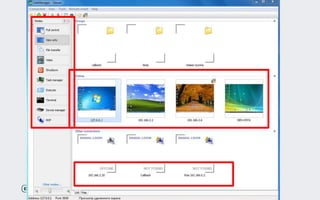
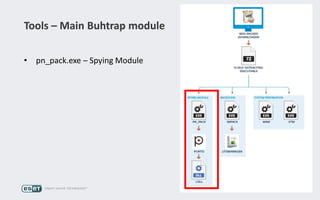
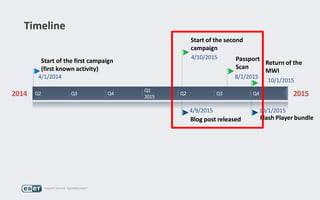
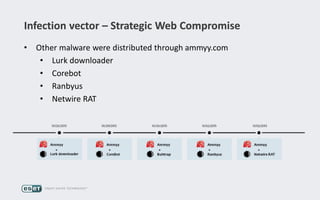
Operation Buhtrap is a financially motivated cybercrime campaign targeting banks and businesses in Russia, active since 2014. The group employs spearphishing and exploit kits to deploy malware and focuses on accounting departments, using tactics similar to espionage campaigns. Their operations involve a sophisticated use of decoy documents, valid certificates, and a structured team of malware coders and testers.