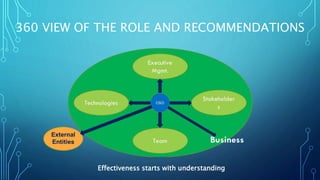
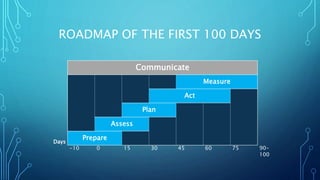
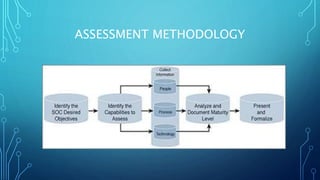
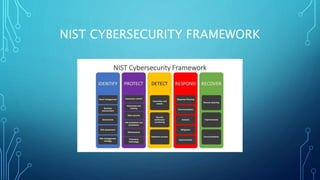
- The document outlines a roadmap for a CISO's first 100 days in a new role. It discusses assessing the organization's security posture, planning security strategy and goals, and taking initial actions like redefining teams. Key steps include preparing for day one, assessing people and processes, planning strategy and a 2-3 year roadmap, acting on projects and technology selection, and measuring program impact and providing executive reports. The roadmap is meant to help a new CISO gain insight, define a security vision, and show early progress and wins.