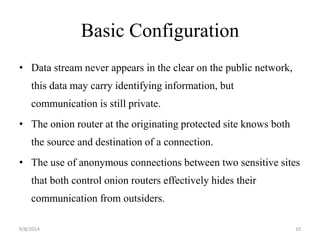
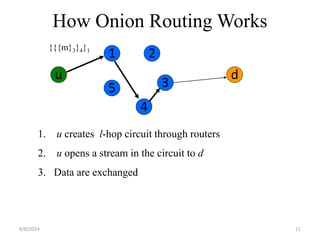
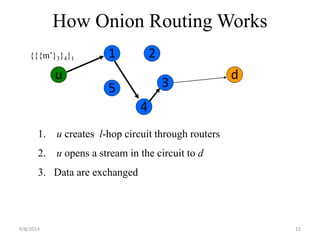
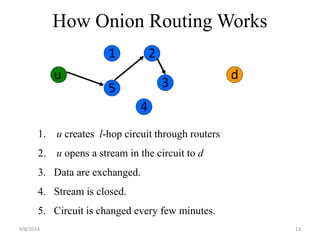
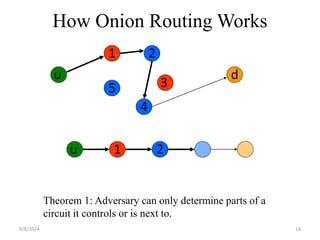
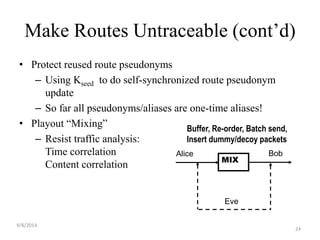
The document discusses a routing protocol called AASR for mobile ad hoc networks (MANETs) operating in adversarial environments. The objectives of AASR are to provide anonymity, location privacy, and defend against active attacks while maintaining throughput and reducing packet loss. It aims to achieve this through the use of group signatures, onion routing, and trapdoors to hide the identities of nodes and destinations of packets. The document reviews related work on onion routing, group signatures, and anonymous on-demand routing protocols. It also outlines some attacks on MANETs like location privacy attacks and discusses how the proposed framework uses techniques like trapdoors, asymmetric keys, and pseudonyms to make routing anonymous and untraceable.























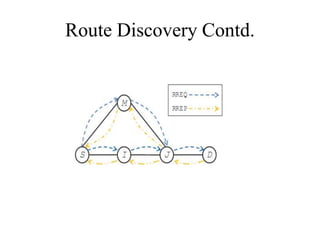



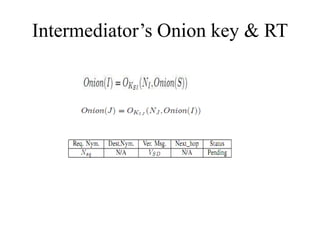
![Intermediate Node contd
• I tries to decrypt the part of VD with its own private key.
• In case of decryption failure, I understands that it is not the
destination of the RREQ.
• I will assemble and broadcast another RREQ packet in the
following format:
• I → ∗ : [RREQ,Nsq, VD, VSD,Onion(I)]GI−](https://image.slidesharecdn.com/firstreview-140908021145-phpapp02/85/AASR-Authenticated-Anonymous-Secure-Routing-for-MANETs-in-Adversarial-Environments-First-review-34-320.jpg)