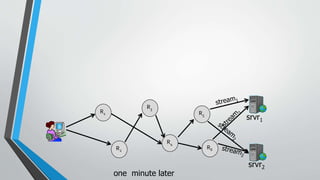
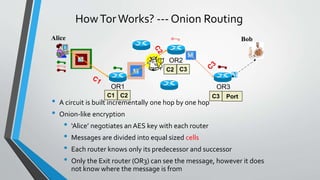
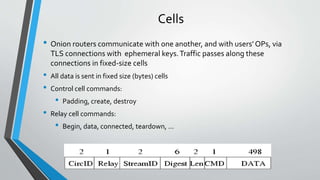
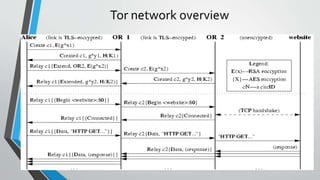
The document provides an overview of the Tor network, which aims to enable anonymous communication on the internet. It discusses why anonymity is needed, how the Tor network works using onion routing and circuits of routers to hide a user's location and identity, limitations of Tor including slow speeds and vulnerability of exit nodes, licit and illicit uses of Tor for privacy and censorship circumvention as well as illegal activities, and dangers of using Tor including surveillance risks. It concludes that research has made progress on anonymous communication and public interest in privacy tools like Tor is likely to increase.