The document discusses the concept of anonymity on the web, focusing particularly on onion routing and the Tor network, which aims to enhance user privacy by routing traffic through multiple relays. It explores the strengths and limitations of Tor, various types of attacks against it, and compares it with other anonymity services like I2P. Additionally, it provides practical insights into the setup of hidden services within Tor and the technical workings of the network's communication protocols.



![1.2 The Tor Network
Tor (The Onion Router) is a free, distributed and anonymous communication service that uses
an overlay network allowing people to improve their privacy and security by concealing the user’s
location and usage from anyone conducting network surveillance or traffic analysis over the Internet.
Tor was initially a research project of the United
States Naval Research Laboratory (NRL, 1995).
In 2003 the Tor network was deployed and the code
is released under the free and open MIT license.
At this initial stage, the network was formed by about
a dozen volunteer nodes (mostly in the US).
From this point onwards, further development and net-
work management has been handled by the Tor Project
Inc., a registered US non-profit organization composed
of the original developers and newcomers alike.
Nowadays, there are more than 7000 relays operational worldwide (with strong concentrations in
United States and Germany) [11] and more than 2.5 millions of relay users [12].
Practically speaking, Tor enables the user to route web traffic through several other computers in
the Tor network so that the other endpoint of the connection cannot trace the traffic back. So:
The more Tor users there are, the more protected your info.
3](https://image.slidesharecdn.com/1212666wsphw-170923233232/85/Anonymity-in-the-Web-based-on-Routing-Protocols-4-320.jpg)







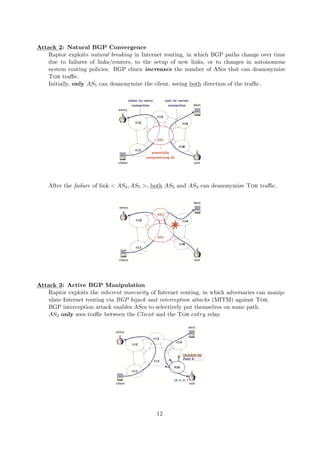






![The datasets returned the following results, with a ∼ 95% accuracy:
IP-Noise dataset: it consists of 76 HS-IP, 200 Client-IP, and 6593 noise circuits.
The circuits labeled with the class noise circuits consist of 954 HS-RP, 4514 Client-RP, and
3862 general browsing circuits.
RP-Noise dataset: it contains 200 Client- RP, 200 HS-RP, and 3862 noise circuits.
Figure 14: Number of instances of different circuit types.
At the end of the attack, we know if there is an hidden service in the network, as well as whether
there is an introduction point circuit or a rendezvous point one for each side (client or server).
After that, the website fingerprinting attack could be used against hidden services in order to
understand which HS they are analyzing.
The team used the WF against 50 sensitive HSs and 950 non-sensitive HSs, for a total of 1000 HS.
In Figure 15 there are the client classification result (left), with an accuracy over 80% and the
server one (right) (server offering the page), with an accuracy in a range from 80% to 96%.
The researchers suggest some potential defenses against the attack:
Figure 15: Client/Server Accuracy (TPR and FPR).
• Circuit Classification Defense: the attacks rely on special properties of the circuits used
for hidden service activities. The used features of the circuits are very identifiable: DoA,
number of outgoing/ingoing cells. So, first of all Tor should address the three features by
forcing all circuits to have similar lifetime, since Client IP and hidden service IP lasts either
a very short or very long time, and this is very identifying.
• Website Fingerprinting Defense: for WF attacks, defenses proposed by Wang et al. -
“Effective Attacks and Provable Defenses for Website Fingerprinting” [18] will be effective.
21](https://image.slidesharecdn.com/1212666wsphw-170923233232/85/Anonymity-in-the-Web-based-on-Routing-Protocols-22-320.jpg)
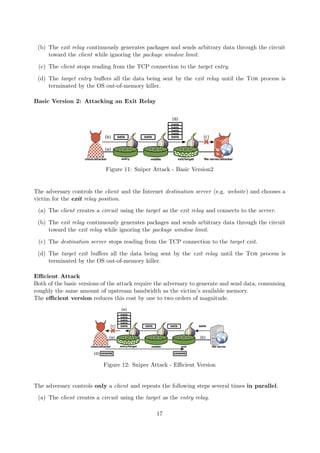
![1.5.5 Spoiled Onions: Exposing Malicious Tor Exit Relays
Spoiled Onion is a research project work between the PriSec group at Karlstad University in Sweden
and SBA Research in Austria about Tor exit relays.
Exit relays can see traffic in clear as it was sent by the Tor user; so, their role is particularly
sensitive compared to other Tor nodes (entry guards and middle relays), especially because traffic
does not have end-to-end encryption.
By design, exit relays act as a Man-In-The-Middle (MITM) in between a user and its destination.
This makes it possible for exit relay operators to run various MITM attacks such as Traffic
Sniffing, DNS Poisoning, and SSL-based attacks such as HTTPS MITM and Sslstrip.
An additional benefit for attackers is that exit relays can be set up quickly and anonymously, thus
making it very difficult to trace attacks back to their origin.
The project was focused on finding and counter-attacking people who run malicious exit relays
to tamper connections and or deanonymize users.
In order to do that, the research team developed:
Exit Map: a flexible and fast exit relay scanner which is able to detect several popular
MITM attacks.
HoneyConnector: a framework to detect sniffing Tor exit relays based on FTP and
IMAP fake connections.
Torbutton Patch: a patch for the Torbutton browser extension [1.5.2] which fetches
and compares X.509 Certificates over different Tor circuits, to detect MITM attacks
against HTTPS.
Using exitmap and HoneyConnector, the team monitored the Tor network over a period of mul-
tiple months in two independent studies. In total, they identified 65 exit relays that conducted
MITM attacks or reused sniffed credentials.
exitmap
Exitmap is a lightweight Python-based exit relay scanner. Its purpose is to create custom circuits
to exit relays that will be probed by modules, creating decoy connections to various destinations.
Figure 16: Design od exitmap
The goal is to cause exit relays to tamper
with the connections, revealing their ma-
licious intent and then being classified as
Spoiled Onions.
The tool runs on a single machine and re-
quires the Python library Stem, which imple-
ments the Tor control protocol used to initi-
ate and close circuits, attach streams and to
parse network consensus.
Once exitmap created a circuit with one of
the targeted exit relays, it invoked the de-
sired probing module which then proceeded
by establishing a connection to a decoy des-
tination. A stream of a probing module was
then attached to the respective circuit.
22](https://image.slidesharecdn.com/1212666wsphw-170923233232/85/Anonymity-in-the-Web-based-on-Routing-Protocols-23-320.jpg)






![Encryption: in I2P there is a higher level of encryption because of the combination of
ElGamal/AES+SessionTags which is used by every pair of nodes in the tunnel (wrt. Tor
AES encryption only). This causes a big decrease in terms of transmission speed.
Circuits vs Unidirectional Tunnels: in I2P tunnels are unidirectional and every part
(sender and receiver) must build two tunnels, respectively for inbound and outbound traffic.
The response of a request does not come backward on the same tunnel, but it uses another
one created from the endpoint to the original sender.
So, the security is increased: the attacker can obtain only half of the information about
the request/response pattern (wrt. Tor bidirectional circuit).
But, this is also paid by a decrease of performances since each time a new tunnel must
be created for the response message.
Scalability: increasing the number of clients in the anonymous network, it directly influ-
ences both Tor and I2P. Although the anonymity set becomes larger and therefore stronger
anonymity is achieved, the network traffic increases and it may cause congestion.
In case of Tor, depending on the amount of new clients joining the network, sooner or later
there could be congestion problems such as latency increase and/or bandwidth decrease.
Moreover, increasing the amount of Tor Onion Routers also leads to the problem of
managing the growing directory: the effort to keep track of the whole network increases
since every OR should be able maintain a direct connection to each other OR in the network.
In case of I2P, new peers joining the network may also be used to build tunnels, assuming
they provide enough performance capability and bandwidth. Thus, in I2P congestion is not
likely to appear.
However, if a sufficient number of clients attempt to access services outside the I2P network,
further outproxies may have to be provided.
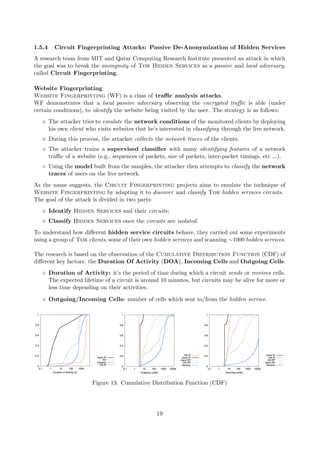
Network Distribution: in Tor, the network is not fully distributed since it’s based on
the concept of central directory servers. The information about relay nodes and hidden
services are provided by authorized directories (currently 9, 0.1% of total nodes)[11].
These Authority Routers keep track of changes in the network and distribute this infor-
mation, therefore if all of them would be compromised, anonymity would be endangered.
I2P instead is fully distributed: it’s based on a distributed architecture (Distributed
Hash Table) which eliminates the risks of single point of failure.
There is a file with some known nodes published on the I2P web page and a bootstrapping
operation is required to find a I2P peer which is able to join the network.
Once this router has been found, it can be queried for more known routers and each partici-
pating relay has to locally maintain a list of all known relays.
Figure 23: Tor Authority Routers.
32](https://image.slidesharecdn.com/1212666wsphw-170923233232/85/Anonymity-in-the-Web-based-on-Routing-Protocols-33-320.jpg)
![Performances: the latency and the bandwidth when accessing the public Internet with
either I2P or Tor was made in a comparison study of the University of Berlin (2011) [23].
The study revealed that while I2P was able to achieve better results when issuing simple
HTTP-GET-Requests, Tor provides clearly better results in terms of accessing whole web
pages and downloading files: in 50% of all cases, Tor was able to retrieve a whole web page
in ∼17 seconds, while I2P took ∼103.19 seconds.
In terms of download speed, Tor was able to deliver an average speed of 51.62 kB/s compared
to the 12.91 kB/s of I2P.
Visibility: Tor network has a greater visibility in the landscape of anonymizing networks.
It is largely used by governments, hackers and also common people that in many countries
try to elude censorship. Moreover, the documentation related to Tor is more detailed and
complete with respect to I2P and it is available in different languages.
Programming Language: Tor is developed using C, while I2P is based on Java.
33](https://image.slidesharecdn.com/1212666wsphw-170923233232/85/Anonymity-in-the-Web-based-on-Routing-Protocols-34-320.jpg)




![References
[1] F. D’Amore - Lecture of Web Security and Privacy (2017).
A simple introduction to Tor.
[2] R. Dingledine, N. Mathewson, P. Syverson.
Tor: The Second-Generation Onion Router.
https://svn.torproject.org/svn/projects/design-paper/tor-design.pdf
[3] A. Davidsson.
Tor: The Onion Routing network.
https://www.cert.se/2015/11/2015-11-20_Tor_-_the_Onion_Routing_Network.pdf
[4] D. McCoy, K. Bauer, D. Grunwald, T. Kohno, D. Sicker.
Shining Light in Dark Places: Understanding the Tor Network.
https://homes.cs.washington.edu/~yoshi/papers/Tor/PETS2008_37.pdf
[5] M.G. Reed, P.F. Syverson, D.M. Goldschlag.
Anonymous Connections and Onion Routing.
https://www.onion-router.net/Publications/JSAC-1998.pdf
[6] P. Syverson
Onion Routing - Brief Selected History.
https://www.onion-router.net/History.html
[7] K. Bauer, D. McCoy, D. Grunwald, T. Kohno, D. Sicker.
Low-Resource Routing Attacks Against Tor.
https://www.freehaven.net/anonbib/cache/bauer:wpes2007.pdf
[8] Wikipedia: Tor (Anonymity Network).
https://en.wikipedia.org/wiki/Tor_(anonymity_network)
[9] Wikipedia: Garlic Routing.
https://en.wikipedia.org/wiki/Garlic_routing
[10] Tor Project: The Onion Router website.
https://www.torproject.org/
[11] Tor Network Status web application.
https://torstatus.blutmagie.de/#AppServer
[12] Tor Network Metrics.
https://metrics.torproject.org/userstats-relay-country.html
[13] Y. Sun, A. Edmundson, L. Vanbever, O. Li
RAPTOR: Routing Attacks on Privacy in Tor.
https://www.cs.princeton.edu/~annee/pdf/usenixsec15.pdf
YouTube: https://www.youtube.com/watch?v=KsqnV_ItFFg
[14] T. Abbott, K. Lai, M. Lieberman, E. Price
Browser-Based Attacks on Tor
https://www.petsymposium.org/2007/papers/PET2007_preproc_Browser_based.pdf
41](https://image.slidesharecdn.com/1212666wsphw-170923233232/85/Anonymity-in-the-Web-based-on-Routing-Protocols-42-320.jpg)
![[15] R. Jansen, F. Tschorsch, A. Johnson, B. Scheuermann
The Sniper Attack: Anonymously Deanonymizing and Disabling the Tor Network
http://www.robgjansen.com/publications/sniper-ndss2014.pdf
[16] P. Winter, R. Kower, M. Mulazzani, M. Huber, S. Schrittwieser, S. Lindskog, E. Weippl
Spoiled Onions: Exposing Malicious Tor Exit Relays
https://www.cs.kau.se/philwint/spoiled_onions/pets2014.pdf
[17] A. Kwon, M. AlSabah, D. Lazar, M. Dacier, S. Devadas
Circuit Fingerprinting Attacks: Passive Deanonymization of Tor Hidden Services
https://www.usenix.org/system/files/conference/usenixsecurity15/
sec15-paper-kwon.pdf
[18] T. Wang, X. Cai, R. Nithyanand, R. Johnson, I. Goldberg
Effective Attacks and Provable Defenses for Website Fingerprinting
http://www.cypherpunks.ca/~iang/pubs/webfingerprint-usenix14.pdf
[19] The Invisible Internet Project
https://geti2p.net/id/docs/how/garlic-routing
[20] Infosec Institute: Introduction to Anonymizing Networks - Tor vs I2P.
http://resources.infosecinstitute.com/anonymizing-networks-tor-vs-i2p/#gref
[21] Wikipedia: Garlic Routing.
https://en.wikipedia.org/wiki/Garlic_routing
[22] B. Conrad, F. Shirazi.
A Survey on Tor and I2P.
http://i2p-projekt.i2p.re/_static/pdf/icimp_2014_1_40_30015.pdf
[23] M. Ehlert.
I2p usability vs. Tor usability a bandwidth and latency comparison.
http://userpage.fu-berlin.de/semu/docs/2011_seminar_ehlert_i2p.pdf
[24] Tor: Hidden Service Protocol.
https://www.torproject.org/docs/hidden-services.html.en
[25] Installing Tor on Debian/Ubuntu
https://www.torproject.org/docs/debian.html.en
42](https://image.slidesharecdn.com/1212666wsphw-170923233232/85/Anonymity-in-the-Web-based-on-Routing-Protocols-43-320.jpg)