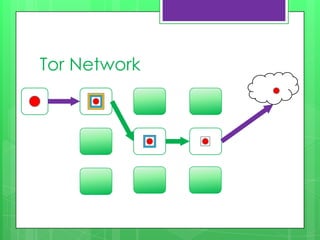
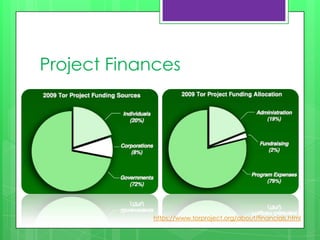
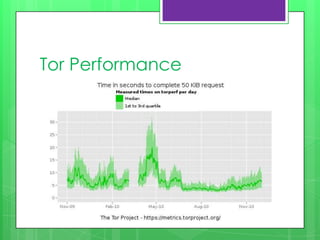
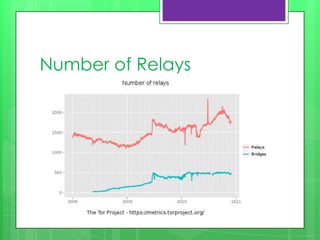
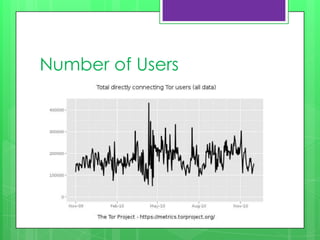
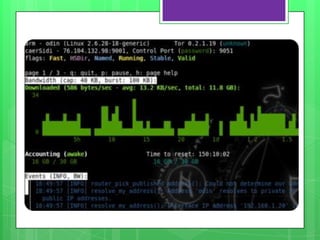
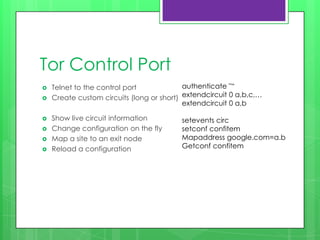
This document provides an overview of anonymity systems like Tor, I2P, and Freenet. It describes how Tor works by passing data through proxies to provide anonymity. It also discusses who uses Tor, such as whistleblowers and journalists seeking privacy. The document outlines the Tor project's finances and how it is funded by various organizations. It concludes by covering some attacks against Tor like traffic analysis and compromising relay nodes.