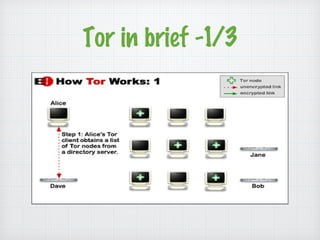
The document introduces Tor, a free software that provides anonymity online by defending against traffic analysis and network surveillance. It describes the structure and terminology of the Tor network, including various components like entry, exit, and relay nodes, as well as related projects such as Orbot and Stem. The author emphasizes the importance of online freedom and personal privacy while exploring the deep web.