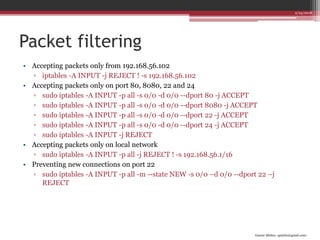
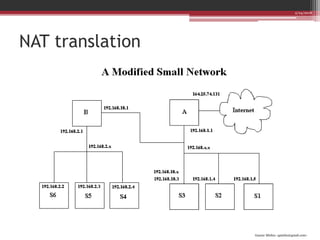
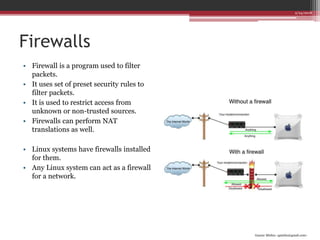
This document discusses Linux firewalls and IPtables. It explains that firewalls use a set of security rules to filter packets and restrict access. These rules are stored in IPtables. Each rule contains information like the protocol, source/destination addresses, and a target action of ACCEPT, DROP, etc. Examples are given of rules to accept packets from only one IP, from the local network, and to prevent new connections on port 22. The document also covers Network Address Translation (NAT) operations in IPtables, including SNAT to change the source address and DNAT to change the destination address when packets pass through the PREROUTING and POSTROUTING chains.


![Gaurav Mishra <gmishx@gmail.com>
Packet filtering
• Each rule in a chain contains following
parts:
▫ Protocol (-p)
TCP, UDP, ICMP or ALL
▫ Source address (-s)
ip address[/mask][port[:port]]
▫ Destination address (-d)
ip address[/mask][port[:port]]
▫ Network interface (-i)
name[+]
▫ Target (-j)
ACCEPT, DROP, REJECT, QUEUE,
RETURN
▫ State (-m)
NEW, ESTABLISHED, RELATED,
INVALID, RELATED+REPLY
2/24/2018](https://image.slidesharecdn.com/linux-3-180304060444/85/Firewall-and-IPtables-4-320.jpg)