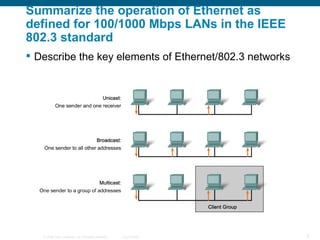
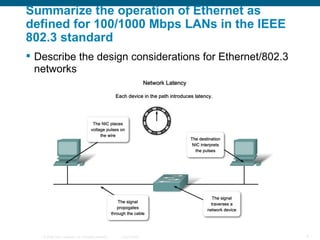
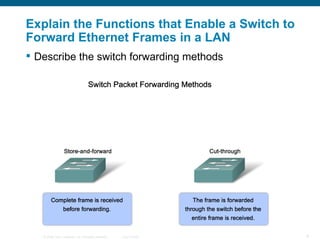
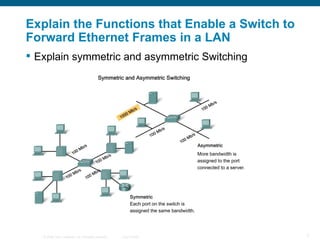
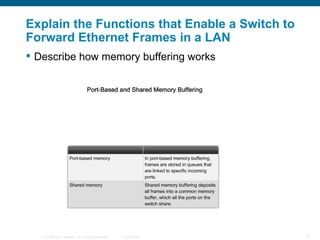
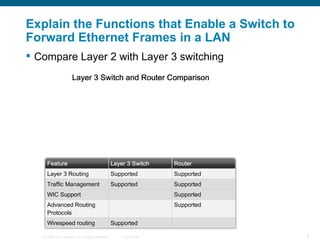
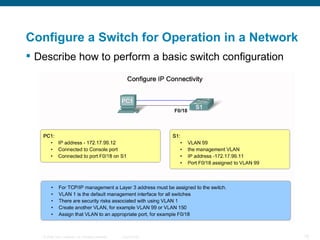
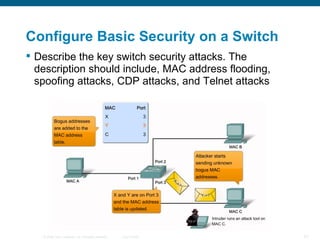
The document discusses configuring and securing a switch for use in a network. It describes summarizing Ethernet operations, switch forwarding methods, and configuring a switch through the Cisco IOS including security features like passwords, SSH, and port security. The objectives are to understand Ethernet, how switches forward frames, and configure a switch for a voice, video and data network with basic security.