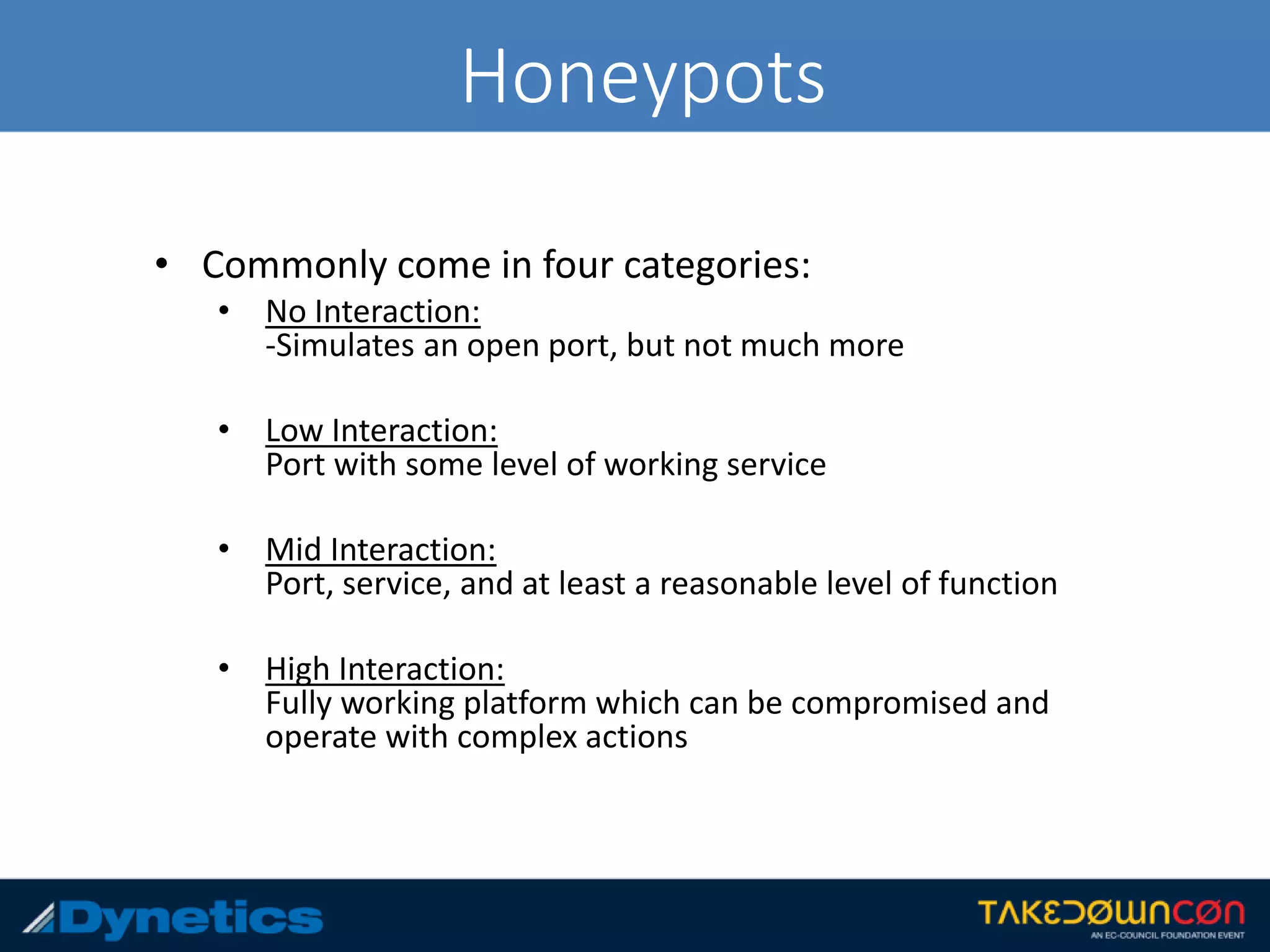
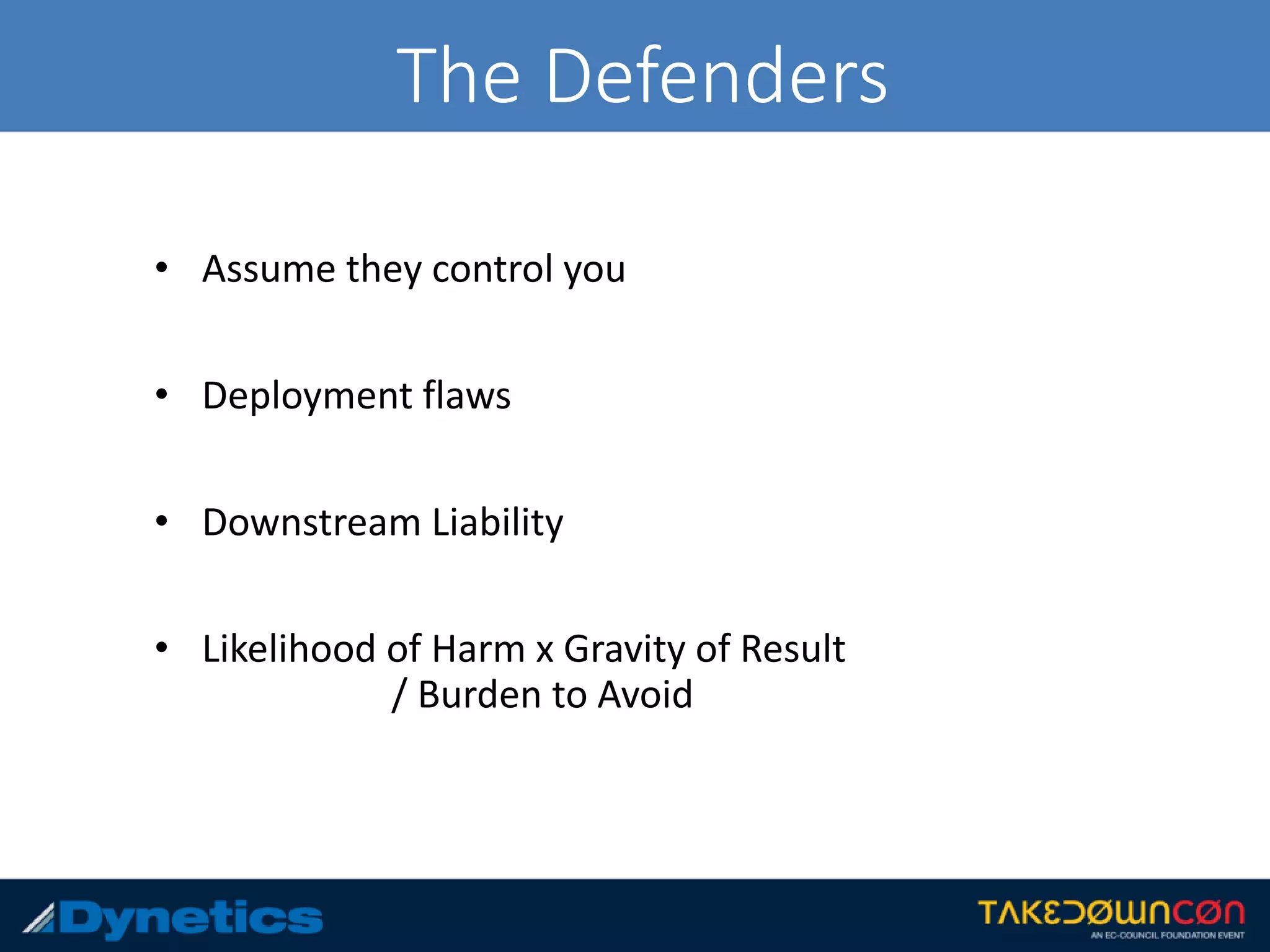
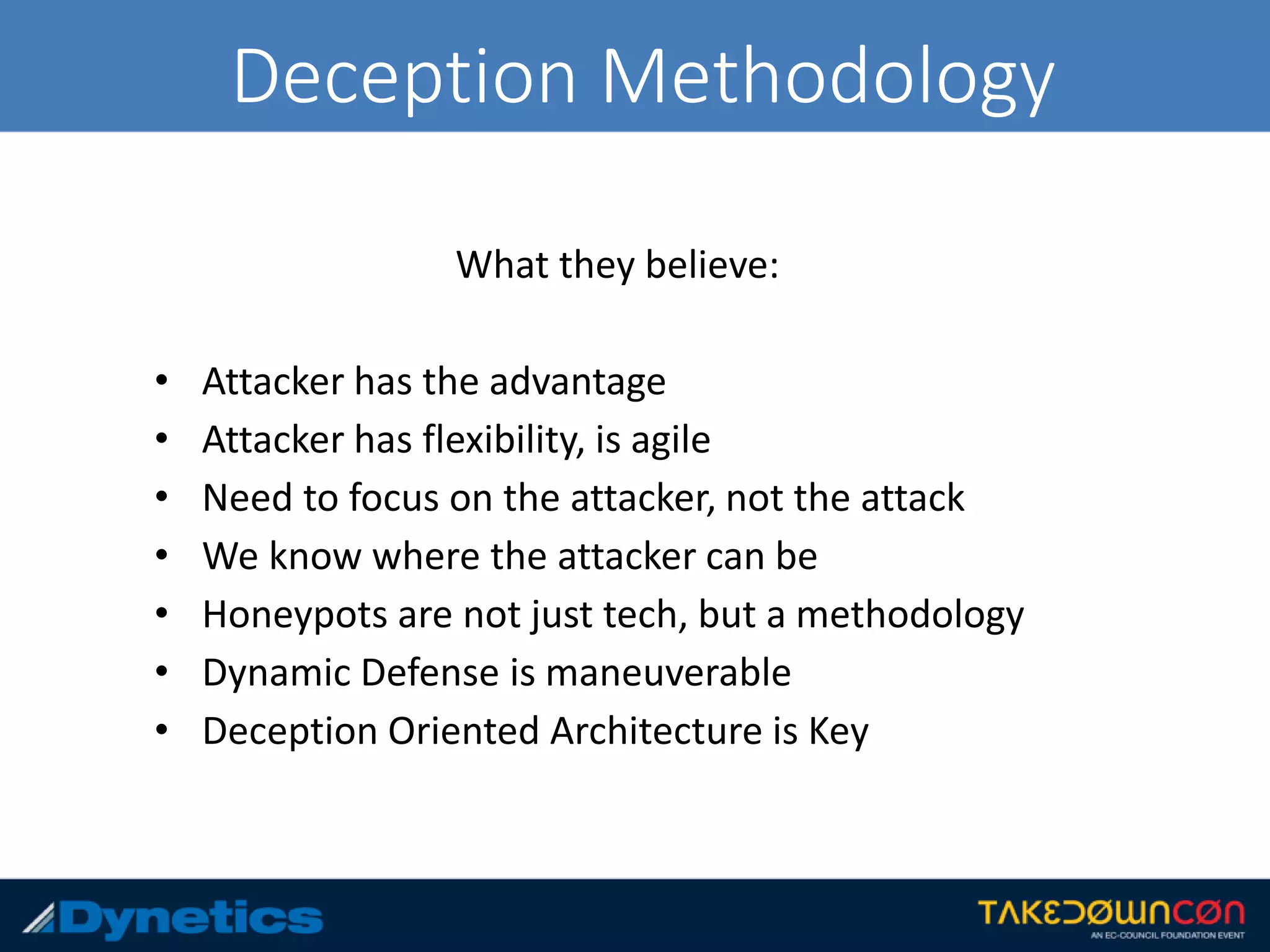
The document discusses the framework for Counter Honeypot Operations (CHOPs), which aims to establish effective techniques for engaging and defeating honeypots in cybersecurity. It emphasizes the importance of collaboration among security professionals to share strategies and skills against evolving deception methods used by attackers. CHOPs is still in early development, highlighting a need for a common methodology to enhance defense against honeypots and improve overall security strategies.