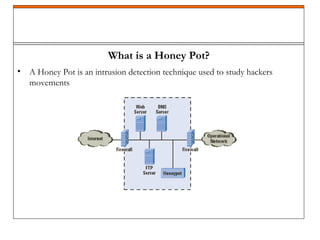
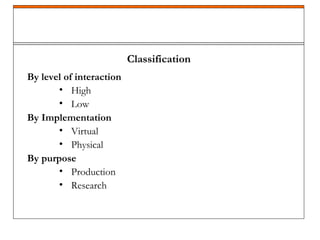
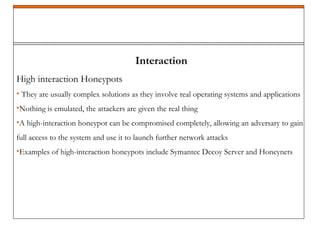
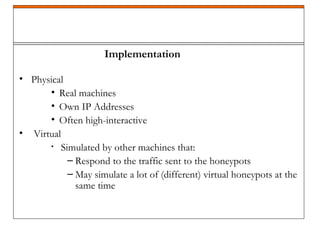
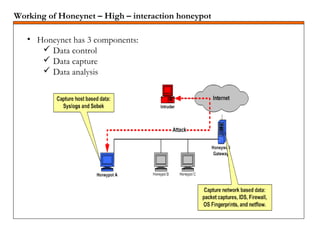
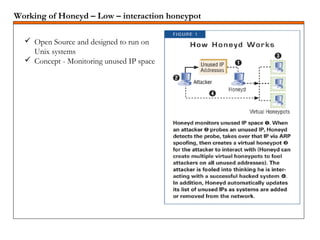
A honeypot is a security mechanism designed to detect and counter unauthorized access to information systems by simulating real system vulnerabilities. They can be classified into low-interaction and high-interaction types, serving various purposes like prevention, detection, or research. While honeypots are effective for studying hacker behavior and gathering data, they require careful implementation and maintenance due to associated risks.